What Is WireGuard?
WireGuard is a modern VPN protocol known for its simplicity and security.
WireGuard connects devices using state-of-the-art cryptography to establish secure connections, whether in routed or bridged configurations. It is designed to be easier to deploy and manage than other VPNs, offering a lightweight solution with fewer lines of code. This reduces its attack surface and simplifies auditing.
How Did the WireGuard Protocol Originate?
WireGuard originated as a revolutionary approach to virtual private networks (VPNs) with its development beginning in 2016. Jason A. Donenfeld, security researcher and developer, identified the complexities and performance issues in existing VPN protocols. Recognizing the need for a more efficient and secure system, he embarked on developing a new protocol. WireGuard was designed to streamline network tunneling with a focus on simplicity. The protocol aims to reduce the complexities and potential security vulnerabilities inherent in the predecessors' expansive codebases and multiple configuration options.
The WireGuard protocol was introduced to the public in 2017 at the Network and Distributed System Security Symposium (NDSS) and further detailed in a whitepaper by Donenfeld. The protocol’s architecture is characterized by a small, easily auditable codebase, a contrast to the tens of thousands of lines of code found in traditional VPN protocols. The minimalist design was chosen to ensure higher security and more straightforward maintenance. It emphasizes a fixed set of modern cryptographic primitives to avoid the risks associated with flexible encryption methods, enhancing both its security posture and performance capabilities.
How Does WireGuard Work?
WireGuard works by establishing secure network tunnels using a combination of modern cryptographic techniques. It uses a streamlined approach to VPN connections, prioritizing speed and security. Its efficiency is partly due to its reliance on a single cryptographic suite for all operations, which reduces the potential for misconfiguration and security vulnerabilities.
The foundation of the protocol’s security model is a set of robust cryptographic primitives. For encryption, it uses the ChaCha20 algorithm, paired with Poly1305 for message authentication. This combination is particularly effective on devices without hardware acceleration for cryptography. For key exchange, the protocol uses Curve25519, offering a secure method for establishing a shared secret over an insecure channel. BLAKE2s is used for hashing.
Its handshake mechanism is designed for minimal latency, involving a 1.5 Round Trip Time (1.5-RTT) process based on the Noise protocol framework. This handshake provides immediate session establishment and perfect forward secrecy. Past communication remains secure even if a key is compromised in the future
The protocol identifies network peers using static public keys, similar to SSH keys. These public keys double as a means of routing within the tunnel, a method known as cryptokey routing. This mechanism streamlines the process of determining packet destinations within the VPN tunnel, enhancing data transmission efficiency.
The protocol stands out for its minimalistic design. The entire protocol is implemented in less than 4,000 lines of code for the Linux kernel. This compact codebase facilitates easy auditing and contributes to the overall security by minimizing the attack surface. The straightforward nature and strong cryptographic foundation makes it an option for secure, high performance network tunneling.
How Secure Is WireGuard?
The protocol is designed to offer a high security while maintaining performance. Its minimalistic approach ensures that each part of the protocol contributes to a secure network tunnel, making it a suitable choice for enterprise environments that prioritize security without compromising on network efficiency.
WireGuard is an open source VPN protocol, which allows for transparent examination and auditing of its code by security experts and the community at large. The open development model fosters trust in its security processes and encourages ongoing improvements and widespread collaboration. The protocol's source code is freely available for anyone to review, contributing to its reputation as a trustworthy tool for secure network tunneling.
The protocol’s security is built on the principle of using the most modern, thoroughly vetted cryptographic protocols available. Its streamlined approach means there are fewer places where the code can be attacked, which inherently makes it more secure than more complex systems. The selection of cryptographic algorithms is fixed to avoid the pitfalls of cryptographic agility, which in other protocols can lead to insecure deployments due to the misconfiguration of cryptographic primitives.
The core of WireGuard's security is its use of state-of-the-art cryptography. ChaCha20 (encryption algorithm), Poly1305 (authentication), Curve25519 (key exchange), and BLAKE2s (hashing). These choices are recognized for their strength and performance, especially on devices that lack specialized cryptographic hardware. The protocol’s resistance to common attacks is bolstered by its default configuration which does not store any persistent user data, reducing exposure to data leaks.
The lean codebase allows for easier code auditing and reduces the potential for undiscovered vulnerabilities. Its design incorporates an avoidance strategy for unsolicited internet traffic, making it less susceptible to certain types of denial-of-service attacks.
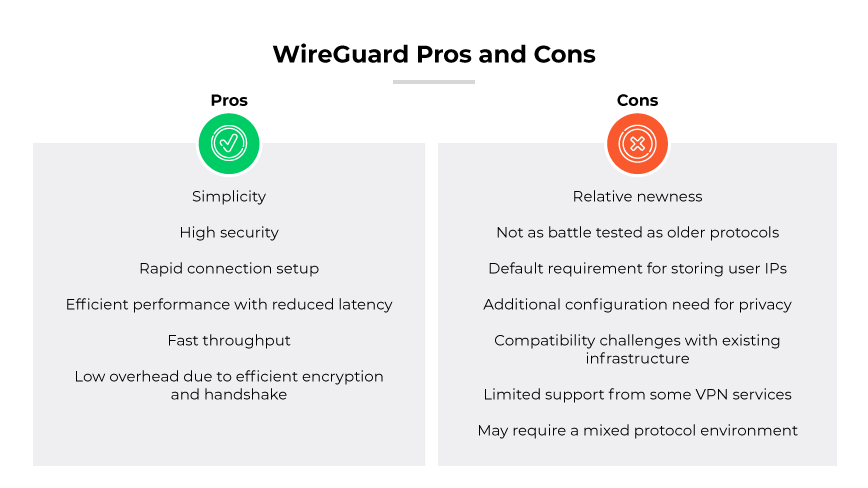
WireGuard Pros and Cons
| WireGuard Pros and Cons | |
|---|---|
| Pros | Cons |
|
|
WireGuard offers several advantages. Its most notable strength is its simplicity. It is also highly secure against various types of cyber threats. Its design allows for a rapid connection setup, which is beneficial for businesses with mobile workforces needing to maintain constant secure access to corporate resources.
Performance is another key benefit. The VPN protocol’s lean design means it operates with efficiency, reducing latency and providing faster throughput compared to traditional VPN protocols. This may be advantageous for enterprises that require the fast, secure transmission of large volumes of data across networks. The protocol has a lower overhead because of efficient encryption and handshake protocols.
On the downside, the protocol’s relative newness means has not endured as long as other protocols. While no major security flaws have been reported, its infancy means it has not been battle tested to the extent of older, more established protocols. As it matures and undergoes more rigorous testing, confidence in its robustness may increase. Another concern is privacy. By default, the protocol requires user IP address storage on the WireGuard server. This can be mitigated through additional configuration layers by the service provider.
Compatibility may also pose challenges. While the protocol supports a range of operating systems, integration with existing network infrastructure may require additional effort. Some VPN services may not yet support WireGuard or may only offer it on certain platforms. This could require a mixed protocol environment, which can complicate deployment and management.
WireGuard may be a potential option for enterprises looking for a modern VPN solution that balances security with performance. Its pros are noteworthy, offering a secure, fast, and efficient VPN experience. However, enterprises must consider the cons, including newness and the additional steps needed to ensure privacy and compatibility with existing systems. As with any technology choice, a careful assessment aligned with specific business requirements and security policies is essential.
WireGuard Use Cases
WireGuard, with its innovative design, presents itself as a candidate for various VPN related use cases within enterprise environments. One primary use case is establishing secure remote access for a workforce that is increasingly mobile. Enterprises can use the protocol to provide employees with secure access to corporate networks from any location. This is essential for maintaining business continuity and secure communications when employees are working from home or traveling.
Another application is creating secure site-to-site connections. For businesses that operate multiple geographically dispersed sites, the protocol offers a way to connect sites securely over the internet. By using the protocol to create VPN tunnels between sites, enterprises can ensure data transmitted across networks remains encrypted and inaccessible to unauthorized parties.
WireGuard may be well suited for deployment in environments where traditional VPN performance might lag, such as with IoT devices or scenarios where network performance is critical. Its lightweight nature allows it to run efficiently on a variety of hardware, from servers to small network appliances. The versatility makes it an option for securing the vast array of devices connected to the modern enterprise network.
Comparing WireGuard with Other VPN Protocols
WireGuard vs. OpenVPN
| OpenVPN vs. WireGuard | |
|---|---|
| OpenVPN | WireGuard |
|
- 600,000 lines of code - Often uses TCP - Uses AES-256 encryption - Better compatibility with older devices - Preferable for unstable connections - Highly configurable for complex environments |
- 4,000 lines of code - Primarily uses UDP protocol - Uses ChaCha20 for encryption - Faster performance with less overhead - Simplicity and speed ideal for businesses - Less configurable but efficient |
WireGuard's most significant advantage over OpenVPN is its lean codebase, with approximately 4,000 lines of code against OpenVPN's 600,000. This makes it more manageable for developers and auditors. The protocol is also faster than OpenVPN from a performance standpoint due to less computational overhead. Plus, it operates primarily on the UDP protocol, known for speed due to less rigorous handshake processes compared to TCP, which OpenVPN often uses. It is well suited for mobile devices due to its lightweight design and efficient use of system resources
In terms of encryption, WireGuard favors modern, high speed cryptographic primitives like ChaCha20 for encryption, whereas OpenVPN typically uses AES-256. While both are secure, the former's efficiency shines in environments where quick data transmission is critical. However, OpenVPN offers a broader compatibility with older devices and systems, and its use of TCP can make it a better choice for networks where stability and reliability over unstable connections are prioritized.
WireGuard's simplicity and speed make it appealing for businesses that need quick and secure connections. Still, OpenVPN's maturity in the market and its extensive configurability allow for a more customizable approach, which can be essential for complex enterprise environments.
WireGuard vs. IKEv2
| IKEv2 vs. WireGuard | |
|---|---|
| IKEv2 | WireGuard |
|
- Known for stability, especially when switching networks - Widely supported natively across various platforms - Flexible encryption method choices - Suitable for enterprises requiring legacy system support |
- Surpasses IKEv2 in speed and security with a modern cryptographic approach - Not as widely supported natively, but increasing in adoption - Uses a fixed set of secure cryptographic tools for reduced risk - Enhanced performance and simplicity for enterprise settings |
IKEv2 is known for stability, especially in changing network environments like switching from Wi-Fi to mobile data. It is also widely supported across various platforms natively, which can simplify deployment. WireGuard often surpasses IKEv2 in speed and security due to its modern cryptographic approach. On the other hand, it may not be natively supported across as many platforms.
IKEv2/IPsec's flexibility in encryption method choices can be a double edged sword. It provides options but can also complicate configuration and potentially introduce vulnerabilities if not properly managed. WireGuard's fixed set of secure cryptographic tools reduces this risk but at the cost of flexibility. For enterprises requiring legacy system support or specific encryption methods, IKEv2 may be more suitable.
The adoption of WireGuard in enterprise settings is often driven by its promise of enhanced performance and security. However, IKEv2 continues to hold a strong position, especially in established VPN solutions where change carries risk and complexity. Ultimately, the choice may come down to specific organizational needs and the value placed on speed and simplicity versus compatibility and proven stability.
WireGuard Setup
Configuration involves a few critical steps to establish a secure VPN connection. This process requires generating cryptographic keys, creating configuration files, and installing the necessary software.
Here is a general guide for configuring WireGuard clients within an enterprise network.
- To begin, you will need to install the WireGuard software on the client device. This software is available for various operating systems and can typically be found in the respective package repositories or app stores. Once installed, the next step is to generate the cryptographic keys. This can be done using the WireGuard interface on the command line or through the graphical interface, depending on the platform. These encryption keys are essential for the secure communication between the client and the WireGuard server.
- After key generation, you must create a client configuration file. This file includes the private key of the client, the public key of the server, the VPN server's endpoint (IP and port), and the allowed IP range that the client can use once connected. Configuration can often be done directly within the WireGuard application, or by editing a simple text file. The specific parameters will depend on the network setup and the desired security policies.
- Once the configuration file is ready, the client interface can be activated. On a command line interface, this is often done with a command like wg-quick up [interface], where [interface] is the name of the interface you've configured. For graphical users, this may involve simply toggling a connection on within the application.
- Finally, for the client to correctly route internet traffic through the VPN, you may need to adjust the network settings or firewall rules. This ensures that the desired traffic is securely tunneled.
It's worth noting that for an enterprise environment, automating deployment configurations can be achieved through various automation tools or by integrating with a network management solution. This streamlines the process and maintains consistency across the network.
Remember, the specific commands and steps can vary based on the operating system and network architecture. Always refer to the official WireGuard documentation and your enterprise's network policies when configuring clients.