What Is IKE (Internet Key Exchange)? | IKE Meaning
Internet Key Exchange (IKE) is a secure key management protocol for establishing secure, authenticated communication channels over IP networks.
IKE automates the negotiation and establishment of Security Associations (SAs) in IPsec for secure VPN connections. It ensures both parties in the communication use a common set of encryption and authentication methods, enabling the secure exchange of information. Acceptable methods can include encryption algorithms, authentication algorithms, Diffie-Hellman group, and pre-shared keys or RSA/DSA certificates.
How Does the IKE Protocol Work?
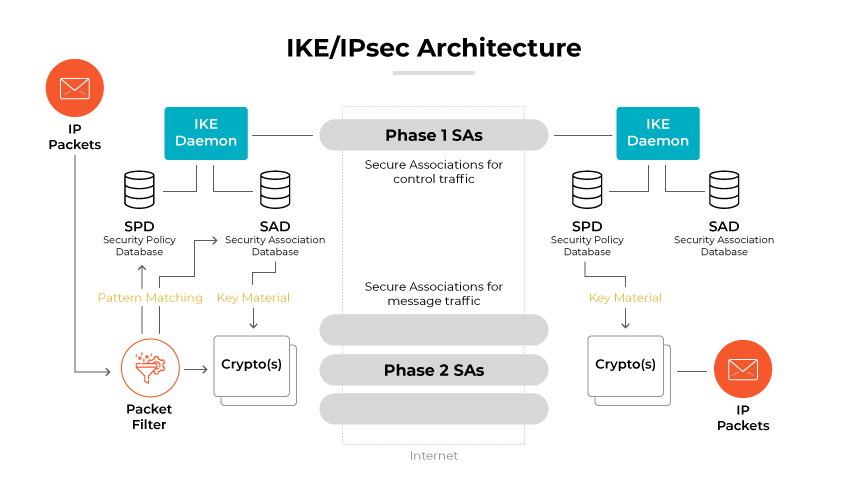
The IKE protocol provides continuous security assurance for communication over IP networks. It allows the dynamic establishment of encryption keys and the frequent change of those keys to maintain the security of communication channels.
In the enterprise context, where safeguarding data is paramount, Internet Key Exchange is the cornerstone of establishing Virtual Private Networks (VPNs) using IPsec. There are two main IKE phases that make the protocol work: Phase 1 and Phase 2.
IKE Phase 1
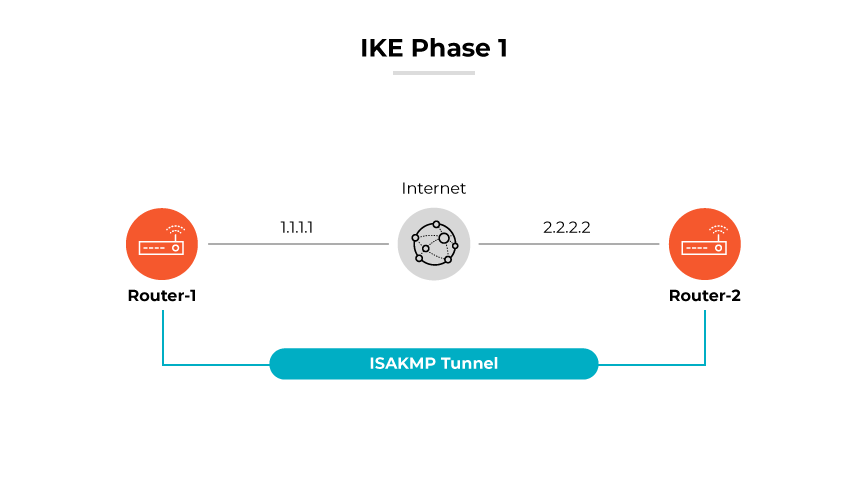
Phase 1 is about creating a trusted relationship and secure channel between two IKE peers. IKE negotiates the encryption and authentication methods that will secure communications. Communication can be authenticated using a pre-shared secret key, public key encryption, or a digital signature. The Diffie-Hellman key exchange algorithm is pivotal because it allows the two parties to establish a shared key over an unsecured channel without any prior exchange of secret keys. The chosen encryption algorithms and the strength of the keying material are critical in maintaining the confidentiality and integrity of the data.
Phase 1 has two distinct modes: Main Mode and Aggressive Mode. Main Mode offers identity protection and is more secure, taking six messages to complete the negotiation. Aggressive Mode is faster because it uses three messages but offers less security because it does not protect identities of negotiating parties.
IKE Phase 2
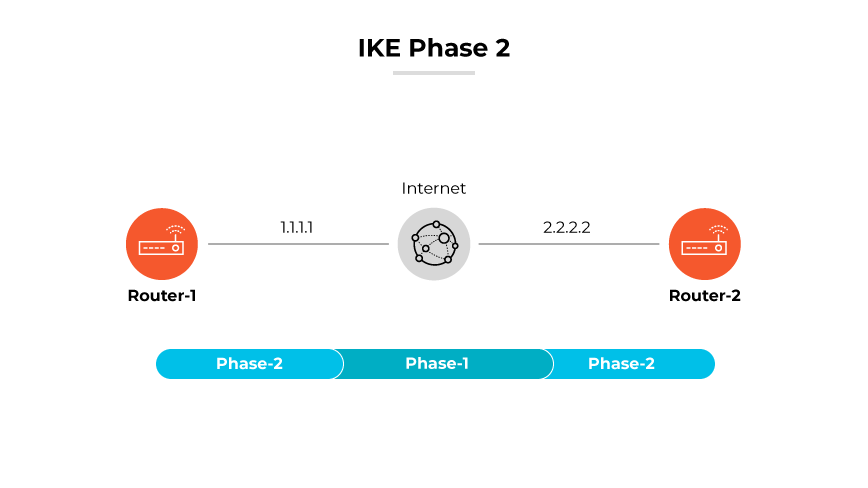
Phase 2 starts with setting up Security Associations (SAs) for IPsec. Detailed negotiations occur to decide the exact parameters for the IPsec tunnel, including encryption and hashing algorithms to secure the data. Phase 2 ensures data passing through the IPsec tunnel is encrypted and authenticated, adhering to the agreed security policies. Phase 2 always operates in Quick Mode, efficiently establishing IPsec SAs based on the foundation built in Phase 1.
An important feature that can be implemented in Phase 2 is Perfect Forward Secrecy (PFS). PFS ensures the keys for each communication session are not derived from a set of long-term keys, making it impossible to decrypt past sessions if long-term keys are compromised. Internet Key Exchange incorporates mechanisms for replay protection that authenticate the sequence of incoming IP packets. This defends against replay attacks, preventing hackers from intercepting and resending packets to disrupt communications or access systems without authorization.
During negotiation in Phase 2, proxy IDs are exchanged. These IDs represent the network traffic to be secured by the IPsec tunnel, ensuring only specified traffic is affected. A proxy ID contains a remote and local IP address prefix. Both peers must use matching proxy IDs, signifying that one peer's specified local IP address should correspond to the remote IP address set for the other peer.
The Phase 2 negotiation also determines whether to use Encapsulating Security Payload (ESP) or Authentication Header (AH) as the security protocol, each serving different security functions for data packets.
What Is IKEv2?
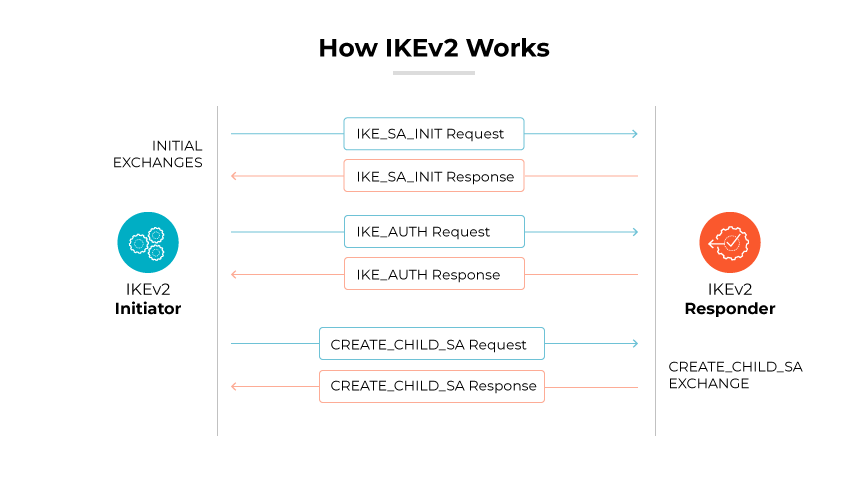
IKEv2, short for Internet Key Exchange version 2, is an updated tunneling protocol that was standardized in RFC 7296. It is designed to improve the efficiency and reliability of the original IKE protocol. As an essential component of IPsec VPN connections, IKEv2 simplifies the SA negotiation process, enhances security, and provides better support for changes in network connectivity.
Unlike its predecessor, IKEv2 simplifies the negotiation process by requiring fewer exchanges to establish a connection. It introduces a mechanism known as the IKE_SA_INIT, which combines the initial exchanges between parties to negotiate the security policies and methods. This is followed by the IKE_AUTH exchange, where both parties authenticate themselves and establish encrypted sessions. The process is designed to be less resource intensive, offering reduced bandwidth consumption and faster connection times.
IKEv2 also includes robust support for mobile connections. The protocol incorporates MOBIKE (Mobility and Multihoming Protocol), which allows users to change network points without dropping the VPN connection. MOBIKE is particularly beneficial for mobile device users. It also comes with built in NAT traversal, making it more reliable when crossing network boundaries. IKEv2 automatically detects when an IPsec tunnel becomes inactive and promptly re-establishes the connection, ensuring uninterrupted secure communication.
IKE Use Cases
Internet Key Exchange frequently serves as the foundational protocol for various secure network connections and services, including Virtual Private Networks (VPNs), Secure Shell (SSH) connections, Secure File Transfer Protocol (SFTP) sessions, and secure site-to-site connections.
The protocol is used in scenarios where data integrity, confidentiality, and authentication are critical, such as in the secure exchange of data between corporate offices over the internet. It is also used to ensure secure remote access for mobile and home based employees, allowing them to connect to enterprise resources securely.
Internet Key Exchange’s ability to dynamically manage SAs provides continuous protection against various threats, including man-in-the-middle, denial of service, and replay attacks. The dynamic aspect of the protocol is essential for maintaining long-term secure communication channels in evolving network architectures.
IKE Pros and Cons
Internet Key Exchange is very reliable, offering a consistent approach to encrypting data and authenticating communication sessions. Its scalability is especially beneficial for large-scale networks, as it can manage numerous simultaneous connections without a significant drop in performance.
Deploying IKE is not without challenges. The protocol's complexity can be a barrier to implementation, requiring specialized knowledge in encryption and authentication methods. The intricacy makes IKE resource intensive, often requiring investment in both hardware and expertise. The protocol’s limited compatibility with some older and non-standard devices can hinder integration into existing network infrastructures. This limitation can lead to challenges in maintaining a unified security posture across all devices within a corporate network.
IKE Vulnerabilities
Internet Key Exchange, while robust, is not immune to vulnerabilities. One such vulnerability is the potential for offline dictionary attacks, where attackers use precomputed hashes to guess low-entropy passwords. IKE can be susceptible to man-in-the-middle (MITM) attacks that may attempt to downgrade the encryption strength. Replay attacks pose a threat, where attackers intercept and resend packets to disrupt the communication flow or gain unauthorized access.
Another concern is key reuse, potentially allowing attackers who have compromised a key to decrypt other sessions. Proper key management is essential to avoiding this. The implementation of protocols like Perfect Forward Secrecy (PFS) can be helpful, ensuring that each session has a unique encryption key.
To protect against vulnerabilities, enterprises should employ strong, high entropy passwords that are resistant to brute force attempts. Firewalls and updated security software form the first line of defense against MITM and other network based attacks. Regular updates to the protocol and related security software can protect against known exploits.
Implementing two-factor authentication is also helpful, adding an additional verification step that must be completed before granting access to a system. Network segmentation can reduce the attack surface by isolating critical systems and applying strict access controls. Employing anti-replay measures like sequence numbers or timestamps in configurations can prevent the successful execution of replay attacks.
By adhering to these best practices, enterprises can fortify their use of Internet Key Exchange against common exploits. It is crucial to stay vigilant and regularly review and update security practices to counteract potential vulnerabilities associated with IKE.