- What Is WireGuard?
- What Is a VPN Tunnel?
- What Is a Business VPN? Understand Its Uses and Limitations
- What Is Network Segmentation?
- Ivanti VPN Vulnerability: What You Need to Know
-
Replacing Legacy VPN and NAC Solutions with a Next-Generation Network Security Client for Endpoints
- VPN Security: Are VPNs Safe and Secure?
- What Is SSTP (Secure Socket Tunneling Protocol)?
- What is Remote Access?
- What Is PPTP (Point-to-Point Tunneling Protocol)?
- What Is L2TP (Layer 2 Tunnel Protocol)?
- What Is IKE (Internet Key Exchange)? | IKE Meaning
- What Is an SSL VPN?
- What Is a Remote Access VPN?
- What Is a Cloud VPN?
-
Secure Remote Access | Protect Remote Employees from Cyberthreats
- IPsec vs. OpenVPN: What Are the Differences?
- What is Quality of Service?
- What is a Data Center?
- SSL VPN vs. IPSec: What Are the Differences?
- How to Set Up a Virtual Private Network (VPN)?
- How Does a VPN Work?
-
What Is the History of VPN?
- 1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
- 1980s: TCP/IP and the Public's Introduction to the Internet
- 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- 2010s: A Decade of Digital Transformation
- 2019–Present: The Response to Remote Work and Limitations of VPNs
- VPN History FAQs
- SoftEther vs. OpenVPN: What Are the Differences?
- What Are the Different Types of VPN?
- What Are the Different Types of VPN Protocols?
- VPN Alternatives for Remote Access
- VPC vs. VPN vs. VPS: What Are the Differences?
- What Is a Double VPN?
- What Is a Site-to-Site VPN?
-
What Is a VPN Concentrator?
- How Does a VPN Concentrator Work?
- Why Use a VPN Concentrator?
- VPN Concentrator Benefits
- VPN Concentrator Disadvantages
- VPN Concentrator Encryption Protocol Types
- VPN Concentrator vs. VPN Router
- VPN Concentrator vs. Site-to-Site VPN
- VPN Concentrator vs. IPsec Encryption
- VPN Concentrator vs. VPN Client
- VPN Concentrator FAQs
- What Is a VPN Gateway?
- What Is IKEv2 (Internet Key Exchange version 2)?
- What Is OpenVPN?
-
What Is SoftEther (Software Ethernet)?
- How Does the SoftEther VPN Protocol Work?
- What Is a SoftEther VPN?
- SoftEther VPN Architecture
- How Secure Is the SoftEther VPN Protocol?
- Pros and Cons of SoftEther
- How to Use SoftEther VPN
- Comparing SoftEther with Other Protocols
- The History of SoftEther
- Does SoftEther Work In Enterprise Environments?
- SoftEther FAQs
- WireGuard vs. OpenVPN | What Are the Differences?
What Is IPsec?
IPsec is a suite of protocols for securing IP network communications by authenticating and encrypting each IP packet of a communication session.
IPsec (Internet Protocol Security) includes protocols for establishing mutual authentication between agents at the beginning of a session and negotiating cryptographic keys to be used during the session. It is widely used in virtual private networks (VPNs), enabling secure data transmission over unsecured networks by creating encrypted tunnels between devices.
How Does IPsec Work?
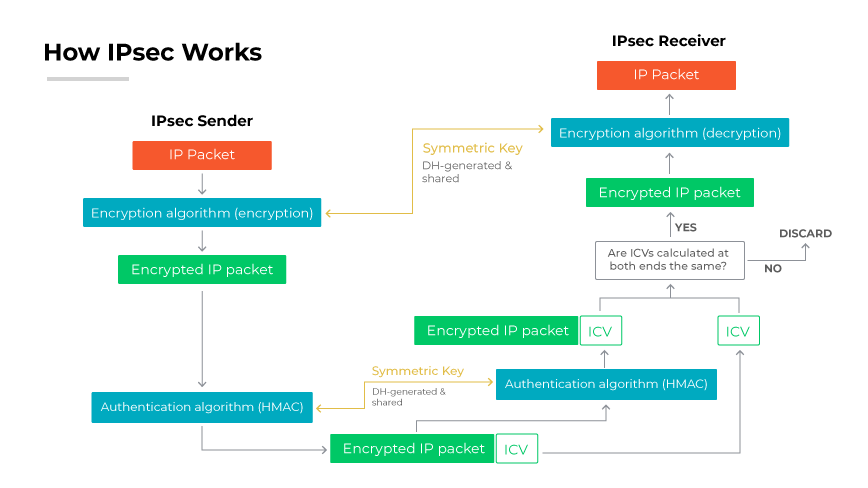
1. Security Association (SA) Establishment
Internet Protocol Security begins secure communication by creating a Security Association (SA) between devices. An SA is essentially a contract dictating the cryptographic keys and protocols to be applied for encryption and authentication. Establishing an SA is a crucial initial step, confirming that both parties concur on the security measures for their communication. This includes the use of Aggressive Mode, where pre-shared keys accelerate the establishment of the SA.
2. Protocol Engagement
The SA uses two primary protocols: the Authentication Header (AH) and the Encapsulating Security Payload (ESP). AH is responsible for the integrity and authentication of data packets, confirming they have not been tampered with in transit. ESP encrypts the payload of the packet, concealing the data from potential interceptors. ESP provides the same integrity and authentication as AH.
3. Data Transmission
During data transmission, Internet Protocol Security encapsulates the original IP packet within an ESP or AH header, effectively securing the data within. The encapsulation process is the core of IPsec operation, ensuring the data payload remains confidential and integral from its point of origin to its destination.
4. Key Management and SA Termination
The security of IPsec is dynamic. It involves ongoing key management and the periodic re-negotiation of SAs to prevent security compromises. When the need for a secure connection ceases, the SA is terminated, effectively closing the secure tunnel. The termination process ensures secure channels do not remain active beyond the required span, mitigating the risk of unauthorized access.
IPsec Protocols
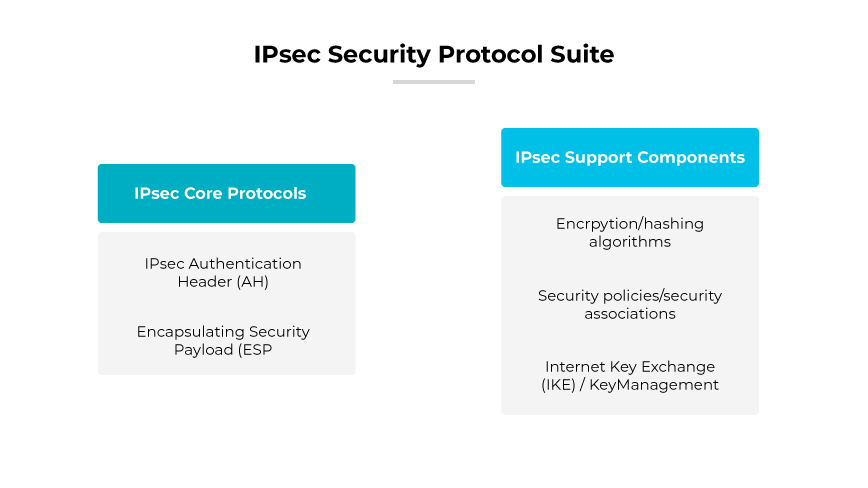
Internet Protocol Security includes a set of protocols for establishing mutual authentication between agents at the beginning of a session and negotiating cryptographic keys to be used during the session.
Internet Key Exchange (IKE)
IKE is crucial for the establishment and management of security associations (SA) within the IPsec protocol suite. It negotiates the cryptographic keys and specifies the necessary security parameters for the hosts. IKE operates in two phases. The first phase establishes the IKE SA. The second phase uses that SA to create the Internet Protocol Security SA for the actual secure data transfer.
Authentication Header (AH)
The AH protocol provides authentication for IP packets, ensuring the integrity and authenticity of transmitted data. AH encapsulates each packet, protecting the contents against tampering and modification during transit. However, it does not encrypt the data payload, which limits its usage scenarios.
Encapsulating Security Payload (ESP)
ESP offers both integrity and confidentiality by encrypting the data payload of IP packets. While it also provides authentication like AH, its main purpose is to protect the communications from eavesdropping. The IP header remains unencrypted, allowing for NAT traversal, but its integrity is not guaranteed by ESP itself.
Internet Security Association and Key Management Protocol (ISAKMP)
Part of the IKE, ISAKMP is responsible for establishing SAs and the cryptographic keys. This protocol facilitates dynamic key exchange and the negotiation of the security policy. ISAKMP operates through two phases. The first creates a secure channel (IKE SA) with pre-shared keys (PSK). The second phase uses the channel to establish IPsec SAs for data transfer.
IPsec Modes
Two distinct IPsec modes dictate how data is protected when sent across networks: Tunnel Mode and Transport Mode. Each mode serves unique scenarios and offers different security levels. Choosing between Tunnel and Transport Mode depends on the specific requirements of the network infrastructure and sensitivity of the data in transit. Both modes play pivotal roles in maintaining the security and integrity of data as it navigates through various networks to reach its intended destination.
IPsec Tunnel Mode
Tunnel Mode encapsulates the entire IP packet, including its header, within a new packet with a new header. This mode is akin to a protective envelope, ensuring the contents remain confidential and unaltered during their journey across public networks. It is most commonly used in gateway-to-gateway communications, where it safeguards internal network details by encrypting the entire original packet.
IPsec Transport Mode
Transport Mode secures only the payload of the IP packet, leaving the header untouched. This approach is less about hiding and more about protecting the integrity and confidentiality of the message within. Typically used for end-to-end communications, such as host-to-host interactions, it is less complex and allows devices on a network to verify the data's origin and ensure it has not been tampered with.
IPSec Ports
Internet Protocol Security utilizes designated ports as conduits for establishing and maintaining secure network communications. These ports are integral for the setup and continuation of secure sessions between devices within enterprise networks.
When setting up a secure channel, Internet Protocol Security primarily uses two ports: UDP port 500 for initiating connections and negotiating keys, and UDP port 4500 for situations where Network Address Translation (NAT) is involved.
These ports facilitate the Internet Key Exchange (IKE) process, which is vital for creating secure associations between communicating endpoints. Proper configuration of these ports on network gateways is essential to ensure the smooth operation of IPsec-based communications.
The Impact of IPsec on MSS and MTU
Internet Protocol Security implementation affects the Maximum Segment Size (MSS) and Maximum Transmission Unit (MTU) within a network. MSS refers to the largest segment of data an IP packet can carry, while MTU represents the largest size an IP packet can be (including headers and payloads). Internet Protocol Security introduces additional headers to packets, which requires a recalibration of these sizes to prevent issues such as fragmentation.
IPsec can add significant overhead to packets due to encapsulation headers, which reduces the effective MSS and can lead to fragmentation if the MTU is not adjusted. To maintain network efficiency, administrators may need to decrease the MSS or increase the MTU on devices to accommodate the extra headers that IPsec adds. This adjustment ensures data packets are transmitted without unnecessary fragmentation, maintaining the integrity and performance of enterprise network communications.
IPSec Pros and Cons
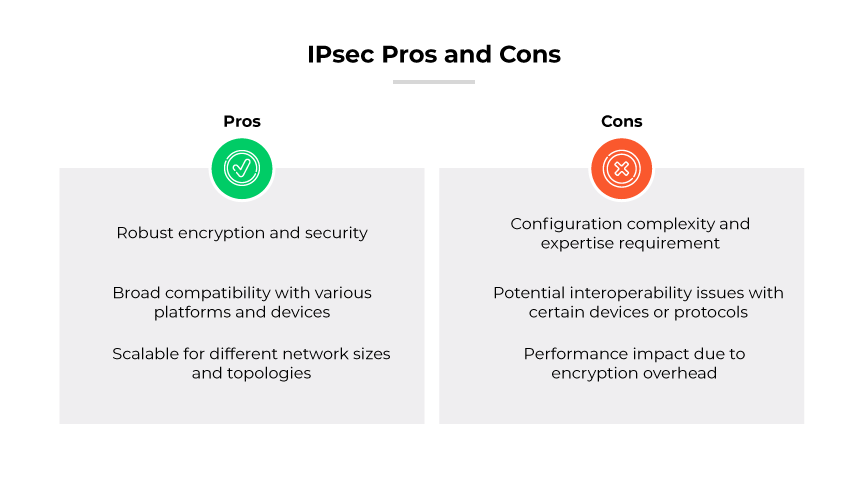
The advantages of IPsec are substantial in the context of enterprise network security. It offers robust cryptographic security, ensuring data remains confidential and unaltered during transmission. Its widespread adoption as an open standard facilitates broad compatibility across various hardware and software platforms. Versatility allows IPsec to secure a range of network configurations, from individual connections to complex enterprise environments. The scalability of Internet Protocol Security makes it suitable for businesses of all sizes, capable of growing alongside the expanding network needs.
IPsec deployment comes with challenges. The protocol's complexity can make it difficult to configure correctly, often requiring expertise that goes beyond basic networking skills. While Internet Protocol Security is broadly compatible, there can be interoperability issues with certain devices or other security protocols. The encryption and decryption process introduces computational overhead, which can affect network performance, particularly on high-traffic networks. Effective key management is critical, demanding diligent oversight to maintain the security of encrypted communications. IPsec is designed specifically for IP traffic; non-IP traffic requires additional measures for protection.
What Is an IPsec VPN?
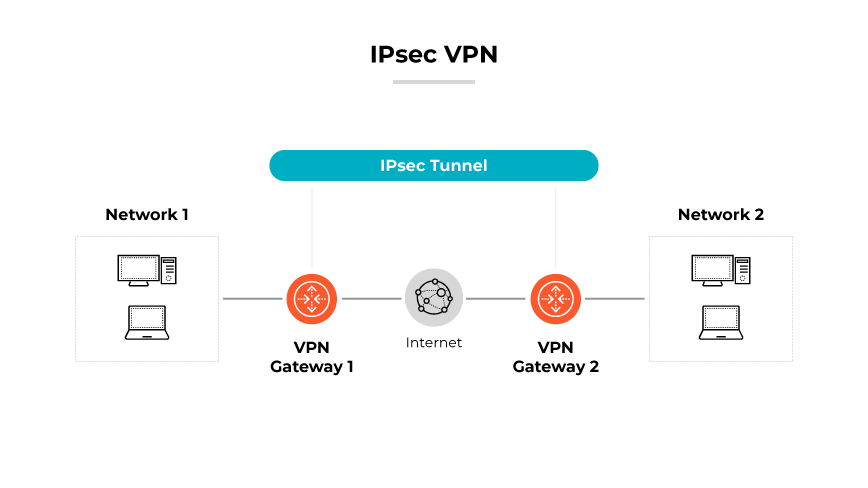
IPsec VPN secures IP communications by authenticating and encrypting each IP packet during transit. It is utilized within a business environment to establish a secure connection between remote users or sites over the internet, effectively maintaining confidentiality and integrity of data. This secure connection, or tunnel, allows employees to access corporate resources as if they were directly connected to the enterprise network.
An IPsec VPN offers the advantage of working at the network layer, providing end-to-end security for all data traveling through it. It is compatible with various hardware and software, making it a versatile solution for securely connecting disparate network segments over the internet.
IPsec vs. SSL VPN
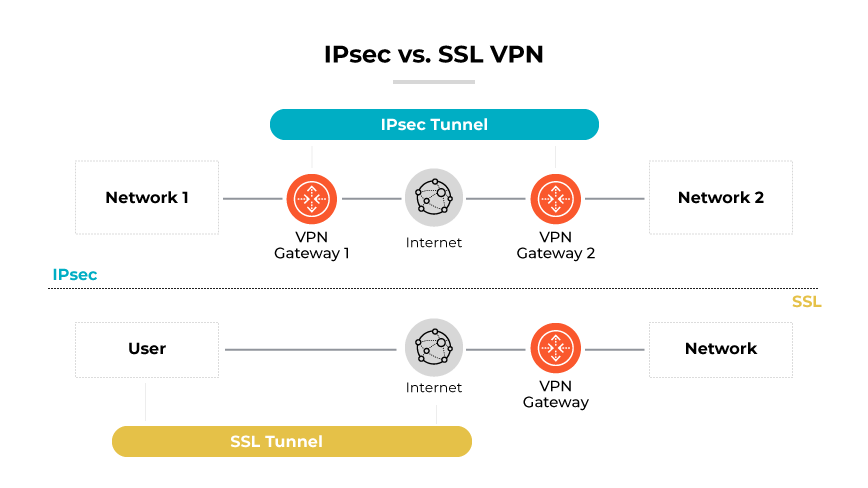
IPsec VPNs and SSL VPNs serve the same purpose of encrypting and securing communication over potentially insecure networks. However, they operate differently. IPsec VPNs encrypt at the network layer. They are ideal for connecting networks or devices with a high level of security, often requiring specialized client software to establish a connection.
SSL VPNs work at the application layer and provide secure access through a web browser without the need for specialized client software. Modern SSL VPNs primarily utilize TLS (Transport Layer Security) to secure HTTPS traffic. While TLS encryption secures the data exchange between a web browser and the server, it does not conceal ancillary information like IP addresses, physical location, browser, or operating system the host and connected sites are using. SSL VPNs are typically used for giving remote users access to specific applications or services within a corporate network. SSL VPNs offer flexibility and ease of use, but potentially less comprehensive security compared to IPsec VPNs.
History of IPsec
The origins of Internet Protocol Security can be traced back to the early 1970s with the development of encryption devices for ARPANET, the precursor to the modern internet. By the late 1980s, the National Security Agency (NSA) began sponsoring the development of security protocols for the internet, leading to early forms of network encryption. These efforts culminated in the work published by the National Institute of Standards and Technology (NIST), including the Security Protocol at Layer 3 (SP3), which evolved into the Network Layer Security Protocol (NLSP).
In the early 1990s, the US Naval Research Laboratory (NRL) played a pivotal role in developing and implementing IP encryption, contributing to the standards for what would become IPsec. Their work, supported by DARPA, led to the creation of the IP Security Working Group by the Internet Engineering Task Force (IETF) in 1992. This group's collaboration and workshops with various industry members resulted in the IPsec standards, providing the groundwork for the secure, authenticated, and encrypted transmission of IP packets that underpin today's secure internet communications.
