- What Is WireGuard?
- What Is a VPN Tunnel?
- What Is a Business VPN? Understand Its Uses and Limitations
- What Is Network Segmentation?
- Ivanti VPN Vulnerability: What You Need to Know
-
Replacing Legacy VPN and NAC Solutions with a Next-Generation Network Security Client for Endpoints
- VPN Security: Are VPNs Safe and Secure?
- What Is SSTP (Secure Socket Tunneling Protocol)?
- What is Remote Access?
- What Is PPTP (Point-to-Point Tunneling Protocol)?
- What Is IPsec?
- What Is IKE (Internet Key Exchange)? | IKE Meaning
- What Is an SSL VPN?
- What Is a Remote Access VPN?
- What Is a Cloud VPN?
-
Secure Remote Access | Protect Remote Employees from Cyberthreats
- IPsec vs. OpenVPN: What Are the Differences?
- What is Quality of Service?
- What is a Data Center?
- SSL VPN vs. IPSec: What Are the Differences?
- How to Set Up a Virtual Private Network (VPN)?
- How Does a VPN Work?
-
What Is the History of VPN?
- 1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
- 1980s: TCP/IP and the Public's Introduction to the Internet
- 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- 2010s: A Decade of Digital Transformation
- 2019–Present: The Response to Remote Work and Limitations of VPNs
- VPN History FAQs
- SoftEther vs. OpenVPN: What Are the Differences?
- What Are the Different Types of VPN?
- What Are the Different Types of VPN Protocols?
- VPN Alternatives for Remote Access
- VPC vs. VPN vs. VPS: What Are the Differences?
- What Is a Double VPN?
- What Is a Site-to-Site VPN?
-
What Is a VPN Concentrator?
- How Does a VPN Concentrator Work?
- Why Use a VPN Concentrator?
- VPN Concentrator Benefits
- VPN Concentrator Disadvantages
- VPN Concentrator Encryption Protocol Types
- VPN Concentrator vs. VPN Router
- VPN Concentrator vs. Site-to-Site VPN
- VPN Concentrator vs. IPsec Encryption
- VPN Concentrator vs. VPN Client
- VPN Concentrator FAQs
- What Is a VPN Gateway?
- What Is IKEv2 (Internet Key Exchange version 2)?
- What Is OpenVPN?
-
What Is SoftEther (Software Ethernet)?
- How Does the SoftEther VPN Protocol Work?
- What Is a SoftEther VPN?
- SoftEther VPN Architecture
- How Secure Is the SoftEther VPN Protocol?
- Pros and Cons of SoftEther
- How to Use SoftEther VPN
- Comparing SoftEther with Other Protocols
- The History of SoftEther
- Does SoftEther Work In Enterprise Environments?
- SoftEther FAQs
- WireGuard vs. OpenVPN | What Are the Differences?
What Is L2TP (Layer 2 Tunnel Protocol)?
L2TP is a tunneling protocol, often used to support VPNs, which encapsulates data for secure transmission over public networks.
L2TP is often paired with IPsec because it does not encrypt data by itself. The combination of L2TP and IPsec ensures confidentiality, integrity, and authentication of the data packets transmitted through the VPN tunnel. The combination, known as L2TP/IPsec, is widely adopted for its enhanced security measures.
How Does L2TP Work?
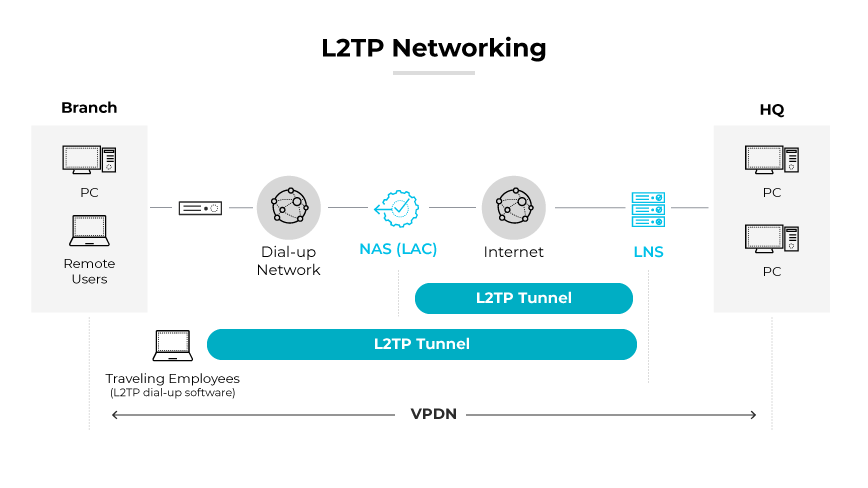
L2TP (Layer 2 Tunneling Protocol) works by encapsulating data packets within a tunnel over a network. Since the protocol does not inherently encrypt data, it relies on IPsec (Internet Protocol Security) for confidentiality, integrity, and authentication of the data packets traversing the tunnel.
The core of an L2TP implementation encompasses two components: the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS). The LAC functions at the originating point of the tunnel where it accepts connections from clients. It initiates the tunnel with an LNS, which is positioned at the endpoint of the network. The LNS acts as a bridge, connecting the secure tunnel to the target network or resources.
During the establishment of PPP sessions, L2TP assigns IP addresses provided by internet service providers (ISPs) to both the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS). This assignment is critical for the encapsulation and transmission of control packets through the secure tunnel.
The integration of Layer 2 Tunneling Protocol with Internet Protocol Security is crucial for creating a secure VPN connection. Internet Protocol Security ensures data packets transmitted through the L2TP tunnel are encrypted and secure. It uses sophisticated encryption methods such as 256-bit AES and protocols like the Internet Key Exchange (IKE) to establish mutual authentication and a secure connection between client and server.
How Secure Is L2TP?
Since Layer 2 Tunneling Protocol does not offer encryption by itself, its primary role is to create a tunnel for data to pass through securely. The security of the data within this tunnel relies entirely on IPsec. The combination provides a dual layer of protection by first creating a tunnel and then securing the data with encryption.
Data encapsulation by Layer 2 Tunneling Protocol allows for a private data flow over the internet. IPsec adds robust encryption to this encapsulated data, using cryptographic security services to protect communications between the user and the network. This includes data integrity, confidentiality, and authentication of origin, which are crucial for enterprise networks where sensitive data is in transit.
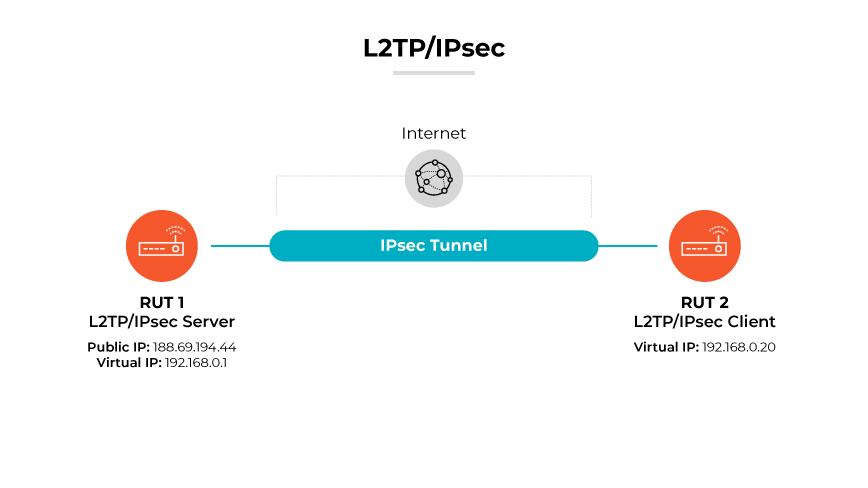
Internet Protocol Security works with Layer 2 Tunneling Protocol by establishing secure keys during the session, providing strong AES or 3DES encryption to ensure that no unauthorized interceptions can be made. The strength of an L2TP/IPsec VPN lies in its encryption and the secure passage it creates for data. Security protocols within L2TP/IPsec VPNs also safeguard the integrity of control packets, ensuring that PPP sessions remain confidential and unaltered during transit.
The security of an L2TP/IPsec VPN can be compromised if the pre-shared keys are weak or if there are configuration errors. It is vital for network administrators to use strong, complex keys and maintain a precise configuration to uphold the VPN’s integrity. When correctly implemented, L2TP/IPsec remains a secure VPN protocol suitable for corporate use, facilitating safe and private communications across public networks.
L2TP Pros and Cons
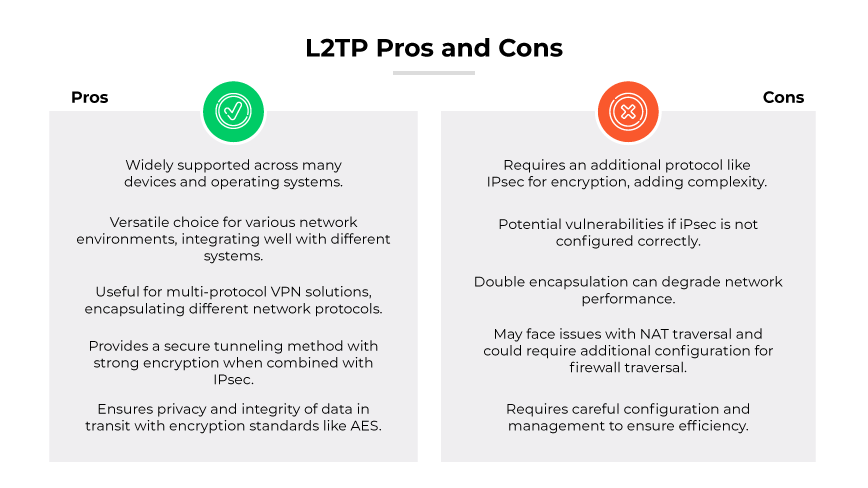
Layer 2 Tunneling Protocol (L2TP) has distinct advantages and disadvantages in the context of enterprise virtual private networks. The protocol is widely supported across many devices and operating systems, making it a versatile choice for integrating into a variety of network environments. Its ability to encapsulate different network protocols makes it useful for organizations that require a multi-protocol VPN solution. When combined with IPsec, it provides a secure tunneling method, leveraging strong encryption standards such as AES to ensure the privacy and integrity of data in transit.
On the downside, since Layer 2 Tunneling Protocol does not offer encryption by itself, it must rely on an additional protocol for securing VPN connections. This adds to the complexity of VPN setup and configuration. The reliance can introduce potential vulnerabilities if IPsec is not configured correctly. The double encapsulation process required by L2TP/IPsec introduces overhead that can degrade network performance. L2TP/IPsec traffic can face issues with NAT traversal and may require additional configuration to work seamlessly across firewalls.
While Layer 2 Tunneling Protocol is a generally stable, functional choice for creating VPNs when used with IPsec, it requires careful configuration and management to ensure secure and efficient operation.
L2TP as a VPN
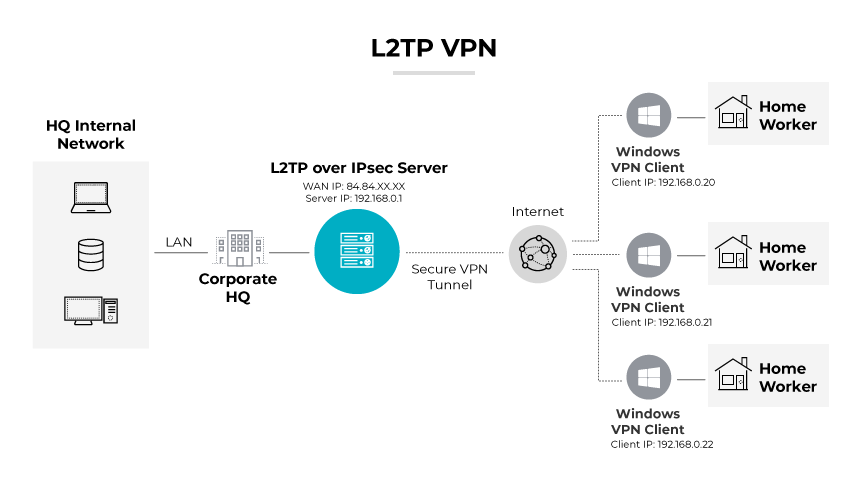
Layer 2 Tunneling Protocol is commonly used as a VPN protocol in the enterprise environment, particularly for establishing secure connections between remote users and the corporate network.
Layer 2 Tunneling Protocol creates a tunnel from the client to the VPN server, enabling the transport of data over the internet securely. IPsec further secures this tunnel by encrypting the data. This dual layer of protection is vital in preventing sensitive corporate data from being intercepted or tampered with during transmission.
The widespread support for L2TP/IPsec across various operating systems makes it an accessible option for businesses, ensuring consistent user experience and security across different devices and platforms.
What Is L2TP Passthrough?
L2TP Passthrough allows L2TP VPN traffic to cross through a firewall or NAT (Network Address Translation) device. When enabled, this function permits the establishment of L2TP connections initiated from a client inside a private network to a remote VPN server on the internet. The passthrough capability is crucial because NAT devices typically block VPN traffic by default due to security policies or the nature of the network protocol translation.
Enabling L2TP Passthrough is essential for businesses that employ remote access virtual private networks (VPNs). It ensures employees can securely connect to the company's network from outside the corporate firewall without being hindered by the NAT device.
Comparing L2TP with Other Protocols
The Layer 2 Tunneling Protocol serves as a middle ground in the VPN protocol landscape, combining features from Point to Point Tunneling Protocol (PPTP) and Layer 2 Forwarding Protocol (L2F). Its integration with IPsec encryption makes it a reliable choice for many enterprise environments. However, when compared to other protocols, each has its advantages and potential drawbacks depending on the specific needs of the network infrastructure.
L2TP vs. PPTP
Compared to Point to Point Tunneling Protocol, Layer 2 Tunneling Protocol represents a step forward in terms of security. While PPTP is known for its speed due to its lower encryption overhead, it is now largely obsolete due to significant security vulnerabilities.
L2TP's encapsulation feature, especially when paired with IPsec, offers a more secure tunnel, albeit with a slight decrease in speed due to the encryption process. L2TP/IPsec's enhanced security measures make it a better choice for enterprises that prioritize data protection over the marginal speed benefit offered by PPTP.
L2TP vs. IKEv2
IKEv2 is recognized for its stability, especially when switching networks (a common scenario for mobile devices), and it offers robust security in combination with IPsec. While L2TP/IPsec and IKEv2/IPsec are comparable in security, IKEv2 is generally favored for its ability to maintain VPN connections during network changes. For businesses with a mobile workforce, IKEv2/IPsec might be preferred over L2TP/IPsec for its resilience to changing network conditions.
L2TP vs. OpenVPN
OpenVPN is an open source protocol known for flexibility and strong security. It is more secure than Layer 2 Tunneling Protocol and is configurable to run on any port, allowing it to bypass firewalls more effectively. OpenVPN often outperforms L2TP in both speed and security, making it a potential choice for organizations requiring high levels of both. OpenVPN requires third party software to run, which may add complexity to deployment.
L2TP vs. SSTP
SSTP, another protocol developed by Microsoft, offers similar advantages to OpenVPN in terms of security due to its use of SSL/TLS. It excels at bypassing firewalls and is native to Windows environments, which might make it more convenient in certain enterprise settings. Compared to L2TP/IPsec, SSTP typically offers a higher level of security but might encounter speed issues on non-Windows devices due to the need for third party clients.
