- 1. How Does the SoftEther VPN Protocol Work?
- 2. What Is a SoftEther VPN?
- 3. SoftEther VPN Architecture
- 4. How Secure Is the SoftEther VPN Protocol?
- 5. Pros and Cons of SoftEther
- 6. How to Use SoftEther VPN
- 7. Comparing SoftEther with Other Protocols
- 8. The History of SoftEther
- 9. Does SoftEther Work In Enterprise Environments?
- 10. SoftEther FAQs
- How Does the SoftEther VPN Protocol Work?
- What Is a SoftEther VPN?
- SoftEther VPN Architecture
- How Secure Is the SoftEther VPN Protocol?
- Pros and Cons of SoftEther
- How to Use SoftEther VPN
- Comparing SoftEther with Other Protocols
- The History of SoftEther
- Does SoftEther Work In Enterprise Environments?
- SoftEther FAQs
What Is SoftEther (Software Ethernet)?
- How Does the SoftEther VPN Protocol Work?
- What Is a SoftEther VPN?
- SoftEther VPN Architecture
- How Secure Is the SoftEther VPN Protocol?
- Pros and Cons of SoftEther
- How to Use SoftEther VPN
- Comparing SoftEther with Other Protocols
- The History of SoftEther
- Does SoftEther Work In Enterprise Environments?
- SoftEther FAQs
SoftEther (Software Ethernet) is an open source VPN protocol that provides advanced encryption and secure communication channels for data transfer.
The SoftEther protocol ensures data integrity and confidentiality through strong encryption standards. Designed for speed and efficiency, it offers rapid data transmission and management ease. SoftEther's user friendly interface and support for multiple VPN protocols facilitate integration into diverse environments.
How Does the SoftEther VPN Protocol Work?
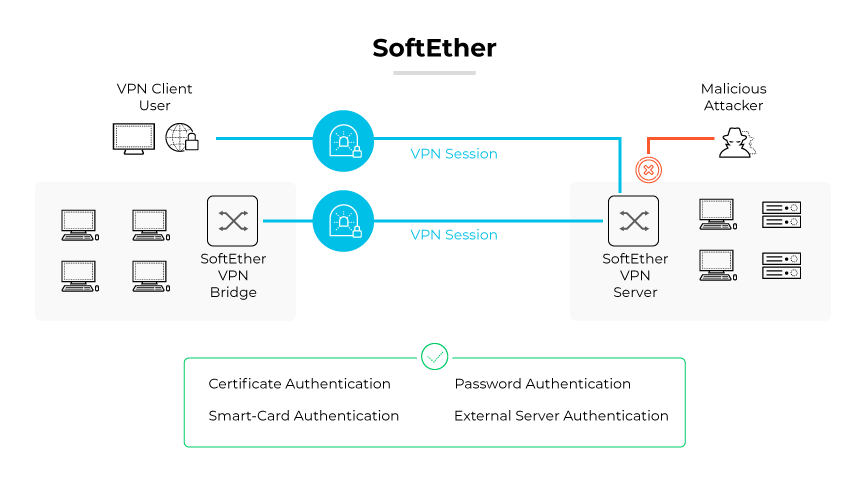
SoftEther VPN is a comprehensive VPN framework. It provides robust, secure client-to-server communications while facilitating rapid data transmission via its unique protocol. The multifaceted system incorporates both the SoftEther VPN Protocol, which ensures encrypted connections, and the SoftEther VPN Server, which supports a variety of VPN protocols.
The protocol establishes secure client-to-server links, ensuring data integrity and confidentiality through advanced encryption. The VPN Server acts as a versatile gateway, permitting the use of multiple protocols like IPSec and L2TP, which offers flexibility and broad compatibility.
A connection through SoftEther begins with a handshake between the SoftEther client and server, leading to authentication and the formation of an encrypted tunnel. The tunnel is the conduit for data. Encapsulation and AES-256 encryption protect the data from unauthorized access, while RSA-4096 bit keys prevent decryption, making VPN communications impenetrable to intrusions.
The protocol offers distinct security features, including deep packet inspection, dynamic DNS, and NAT traversal capabilities. These elements ward off threats like Man-in-the-Middle attacks. The implementation of dual-stack IPv4/IPv6 ensures future proofing and compliance with evolving internet protocols.
Ease of management is another critical aspect of the protocol. SoftEther provides a user friendly GUI for VPN Server and Bridge management. This simplifies the setup and administration of VPN connections for network administrators. A command line utility is also available, offering precise control for advanced users.
The SoftEther VPN Client supports a wide array of operating systems. The client is equipped with features like internet connection maintenance and voice guidance, making it accessible to users with varying levels of technical proficiency.
SoftEther's interoperability is notable. It supports connections from a range of devices and can integrate with other VPN technologies, ensuring a cohesive and secure network environment.
What Is a SoftEther VPN?
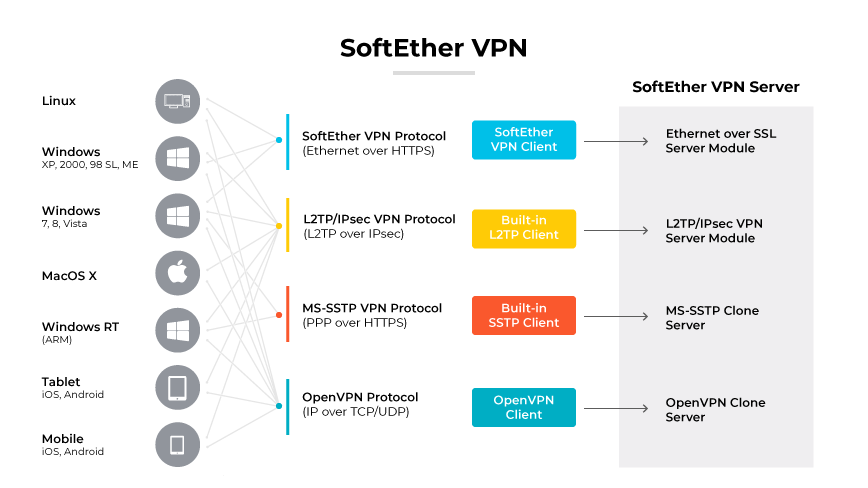
SoftEther VPN stands as a distinct, multifaceted VPN solution.
How Does SoftEther VPN Work?
Unlike the SoftEther protocol that underpins it, SoftEther VPN encompasses a complete VPN server and client software package, facilitating secure, flexible, and scalable networking solutions. It enables the deployment of both site-to-site and remote access VPNs with a variety of protocols such as SSL-VPN, L2TP/IPsec, and more, providing a versatile platform for secure communications and remote network management.
As an integrated VPN suite, SoftEther VPN is lauded for its ability to traverse complex network barriers while maintaining high throughput and stability.
SoftEther VPN Architecture
SoftEther VPN's architecture is distinct from traditional IPsec-based VPN systems, offering unique functionalities suited for enterprise networking. It uses software defined components including Virtual Hubs, which act as virtual ethernet switches. These virtual ethernet switches create isolated communication segments within a single VPN server. This contrasts with the fixed hardware dependency of traditional VPN systems, allowing separated traffic lanes for different user groups.
Each Virtual Hub maintains its forwarding database like a traditional ethernet switch, but it does so through software. The software based approach extends to Virtual Network Adapters and Virtual Layer-3 Switches, which emulate hardware devices and provide advanced routing capabilities, respectively. These virtual components support a flexible, modular network design.
In a Software Ethernet environment, network administrators can establish cascade connections between Virtual Hubs to seamlessly bridge separate network segments. This is a capability not typically found in IPsec systems. SoftEther's Local Bridge feature can connect these virtual segments to physical network interfaces, facilitating both site-to-site and remote access VPN configurations in a unified network topology.
SoftEther’s architecture is transparent to firewalls, proxies, and NATs, achieved through SSL VPN tunneling and NAT Traversal. This allows SoftEther VPNs to establish secure tunnels over HTTPS, usually using TCP/IP port 443. TCP/IP Port 443 is less likely to be blocked by firewalls because of its association with secure web traffic. SoftEther's advanced transmission mechanisms allow for multiple parallel SSL VPN tunnels, optimizing performance across slow or congested networks.
Software Ether’s ability to transmit VPN packets over ICMP or DNS can be beneficial for networks with stringent restrictions because it can facilitate VPN connections where traditional TCP or UDP packets are filtered. This versatility is exemplified by the SoftEther VPN Gate initiative, which uses SoftEther's architecture to provide a worldwide relay of VPN servers.
How Secure Is the SoftEther VPN Protocol?
The SoftEther VPN protocol is known for strong security measures. It utilizes OpenSSL, an open source library for SSL and TLS protocols. This ensures the encryption, decryption, and authentication processes are of a high standard. The protocol's ability to support an extensive range of encryption ciphers, including AES, RC4, DES, Triple-DES, SHA, and MDS, provides a solid foundation for safeguarding data.
SoftEther security is reflected in its diverse user authentication methods. These methods can enhance security by ensuring only authorized users can access the network. The protocol offers packet filtering and security policy options, instrumental in defending against harmful traffic and network assaults. These features collectively fortify the network's defense against sophisticated cyber threats.
The architecture of the SoftEther VPN protocol is designed to preempt security vulnerabilities. A comprehensive security audit conducted in the past highlighted potential weaknesses, but subsequent updates and patches have addressed these issues.
The protocol's inherent design prevents unauthorized data interception and tampering, maintaining the integrity of the data in transit.
Pros and Cons of SoftEther
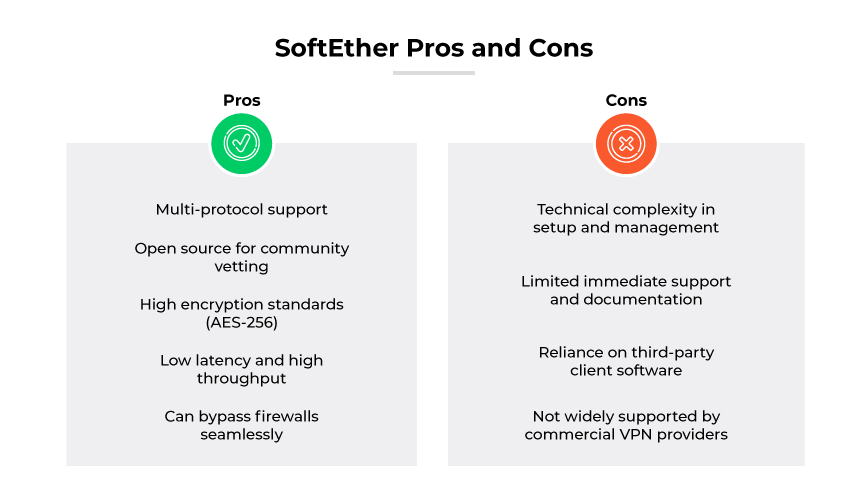
SoftEther offers a high degree of control and security but demands a level of technical acumen and resources to deploy and manage effectively. The protocol can be an effective VPN solution for organizations with very specific use cases, but for those seeking simplicity and broad support, other protocols may be more suitable.
Advantages of SoftEther
SoftEther is multi-protocol VPN software, so it can be a robust tool. Its open source nature allows for security vetting and enhancements by a global community of developers. This transparency is viewed by some as an advantage because it allows users to audit the open source software for potential vulnerabilities. It’s important to note that closed source proprietary VPN solutions are not consequently comparatively less secure.
Software Ethernet ensures data in transit remains secure from eavesdropping and unauthorized access through its support for strong encryption standards, including AES-256. Adherence to high encryption benchmarks can potentially fulfill strict data security policies mandated within corporate environments.
The protocol's performance is another advantage. Designed for speed, Software Ethernet minimizes latency and maximizes throughput, making it ideal for bandwidth intensive tasks. The open source software's ability to bypass firewall restrictions without detection allows for seamless remote access.
Disadvantages of SoftEther
The Software Ethernet protocol is not without its challenges. The setup and management of a SoftEther VPN can be complex, potentially requiring a steep learning curve. Unlike more widely adopted VPN solutions, it may lack the immediate support and documentation found with other protocols, leading to longer implementation times.
Another limitation is the reliance on third party applications for client software. Reliance on third party applications for client software may introduce additional points of failure or security concerns. Software Ethernet is not widely supported by commercial VPN service providers, so enterprises may find themselves with fewer options for quick deployment.
How to Use SoftEther VPN
SoftEther VPN is both free and open source, so it may be an option for organizations looking to deploy their own VPN servers. Despite not being widely available in many enterprise VPN solutions, it can be set up manually since it is open source.
When opting for a DIY VPN server using Software Ethernet, it is important to have the necessary technical expertise to ensure the VPN is configured securely and integrates with company network policies and infrastructure.
Here is a general guide on how to use SoftEther VPN:
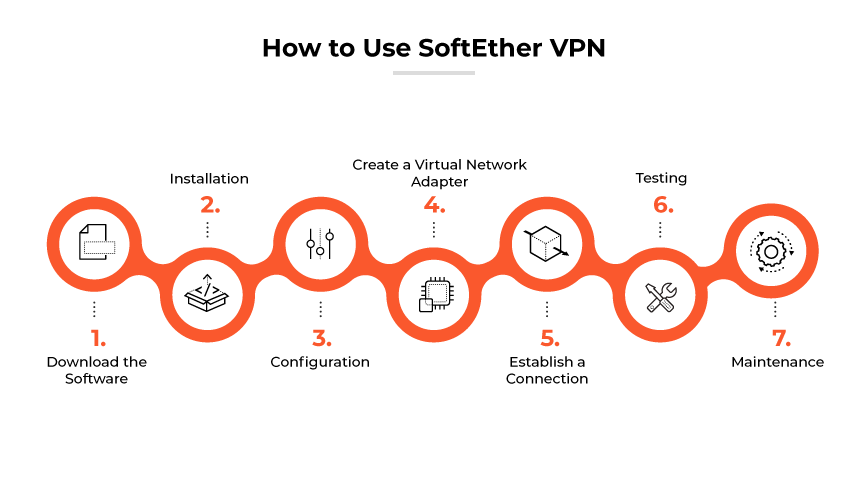
1. Download the Software
Begin by downloading the SoftEther VPN Server software. It is compatible with a variety of operating systems, so choose the version that matches your server's OS.
2. Installation
Install the VPN server software on your designated machine. The installation process might require familiarity with command line operations, especially if you are using a Linux based server.
3. Configuration
Once installed, configure the VPN server. Software Ethernet provides a management console that can be accessed via a web interface or command line. This console allows you to create virtual hubs, manage user authentication, and set up encryption and VPN connection settings.
4. Create a Virtual Network Adapter
For client machines that will connect to the VPN, install the SoftEther VPN Client and create a virtual network adapter. This will be used to interface with the VPN server.
5. Establish a Connection
With the server configured and the client installed, you can establish a connection. Input the server's address, decide on the encryption and authentication method, and if needed, input the required credentials.
6. Testing
After setting up the server and clients, test the connection for stability and security. Ensure the VPN tunnel is operational and data is being encrypted and transmitted securely.
7. Maintenance
Regularly update software and monitor the server for any unusual activities. Keeping the software updated is crucial for security and performance.
Comparing SoftEther with Other Protocols
IKEv2 | SoftEther
IKEv2 is stable, especially when switching networks. Stability makes it potentially useful for mobile users. IKEv2 quickly re-establishes a VPN connection without user intervention. Software Ethernet is not as seamless on mobile devices, but it provides a comparable level of security with more flexibility in configuration. It outshines IKEv2 with the ability to bypass strict firewalls using SSL VPN tunneling through HTTPS.
L2TP | SoftEther
L2TP is commonly paired with IPsec for added security, offering decent encryption. However, it is susceptible to firewall blocking and can be slower because of double encapsulation. SoftEther offers a more robust security posture with higher speeds and firewall traversal capabilities. Its adept use of AES-256 encryption and RSA-4096 bit keys positions it as a more secure alternative to L2TP/IPsec.
PPTP | SoftEther
PPTP is one of the oldest VPN protocols, known for speed but not security since it uses outdated encryption. Software Ethernet provides modern encryption techniques, making it more secure than PPTP.
IPsec | SoftEther
IPsec is a reliable choice for creating secure VPN tunnels, but it can be complex to set up and manage. SoftEther provides a similar level of security with a more user friendly approach. Software Ethernet’s architecture allows for higher throughput and better performance than traditional IPsec.
SSTP | SoftEther
SSTP, primarily used on Windows, offers strong security but is limited by its OS dependency. SoftEther transcends this limitation with multi-platform support and matches SSTP in terms of security. SoftEther's performance and ability to traverse firewalls give it an edge over SSTP for users seeking flexibility and robust security.
WireGuard | SoftEther
WireGuard is a newer option in the VPN protocol arena, offering a lightweight design and high speed connections. WireGuard provides strong security and ease of use, but it is still not as widely adopted as other protocols. Software Ethernet competes with WireGuard on speed and surpasses it in terms of security features, protocol flexibility, and legacy system support.
The History of SoftEther
SoftEther began as an academic endeavor and developed into an open source networking tool. Its story started in the University of Tsukuba, Japan, where it was initially created as a master's thesis research project in 2004. The SoftEther VPN project aimed to create a VPN solution that was both flexible and powerful, capable of traversing firewalls with ease.
As a protocol that supports SSL VPN, NAT traversal, and many other VPN technologies, Software Ethernet was designed to provide a versatile, secure VPN architecture. It was officially released to the public in 2014 after a decade of rigorous development and refinement. A growing community values the protocol’s open source nature, allowing for continuous improvement and peer review.
Does SoftEther Work In Enterprise Environments?
SoftEther is theoretically usable in enterprise settings. However, whether enterprise VPN solution providers allow for integration with the protocol may vary. All vendors offer proprietary VPN solutions which are typically designed to integrate with their own security ecosystems.
Businesses often choose such providers for a comprehensive security solution that includes VPN services. While Software Ethernet could technically be used in an enterprise environment, its integration depends on the IT infrastructure, security requirements, and whether the organization’s VPN strategy allows for the use of open source software.
A company would be more likely to use SoftEther for specific use cases where its features are especially beneficial, like creating an ad-hoc VPN bridge or connecting remote sites with specific needs. However, for unified threat management, policy enforcement, and global network coverage, enterprises may prefer the solutions offered by established VPN providers, which are backed by professional support and service level agreements (SLAs).
While the protocol provides interesting VPN capabilities, it should be noted that the vast majority of enterprise environments require additional features like advanced threat protection, monitoring, and seamless integration with existing network infrastructure. These features are provided by solutions like enterprise VPN platforms, SASE, SD-WAN, and ZTNA products.