What Are the Different Types of VPN?
Types of VPN include:
- Site-to-site VPN
- Remote access VPN
- Cloud VPN
- SSL VPN
- Double VPN
Site-to-Site VPN
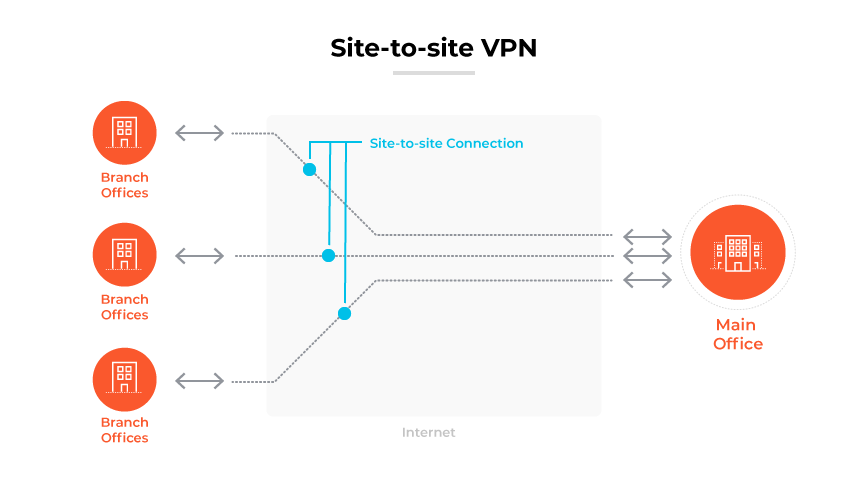
A site-to-site VPN establishes a link between two or more distinct networks, such as a company's main network and its satellite office networks. Many organizations adopt site-to-site VPNs to utilize internet pathways for confidential data rather than private MPLS channels.
Organizations with multiple branches spread across diverse regions often use site-to-site VPNs. Through this setup, businesses can safely integrate their central network with distant offices, enabling seamless communication and resource sharing as though they were one unified network. A site-to-site solution can be deployed as an extranet-based VPN when a company connects its network to the networks of its partners, suppliers, or customers.
Further reading: What Is a Site-to-Site VPN?
Remote Access VPN
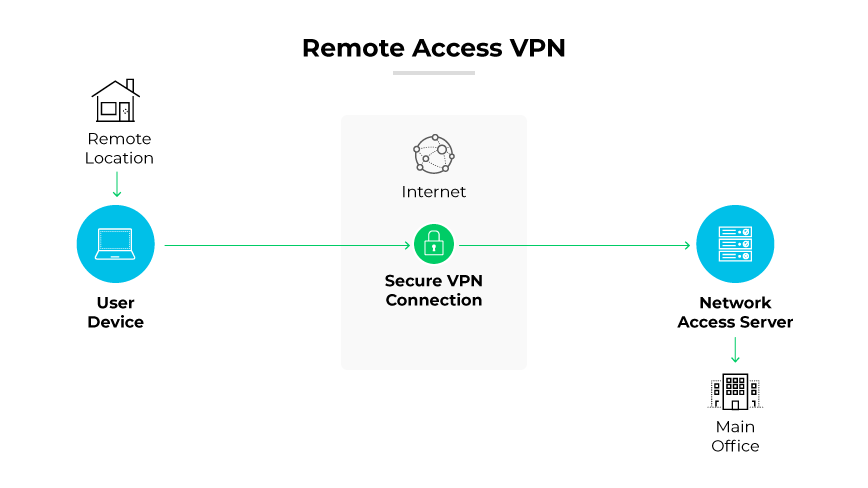
Remote access VPNs allow off-site users to securely connect to and utilize applications and information in the company's main data center, encrypting all user data transmitted and received.
The remote access VPN ensures security regardless of the user's public location by forming a virtually private connection using a tunnel between the enterprise's network and a distant user.
This is achieved by encrypting the data, rendering it indecipherable to potential interceptors. Users can interact with their company's network as if they were on-site, ensuring safe data transfer without the concern of external interference or data breaches.
Further reading: What Is a Remote Access VPN?
Cloud VPN
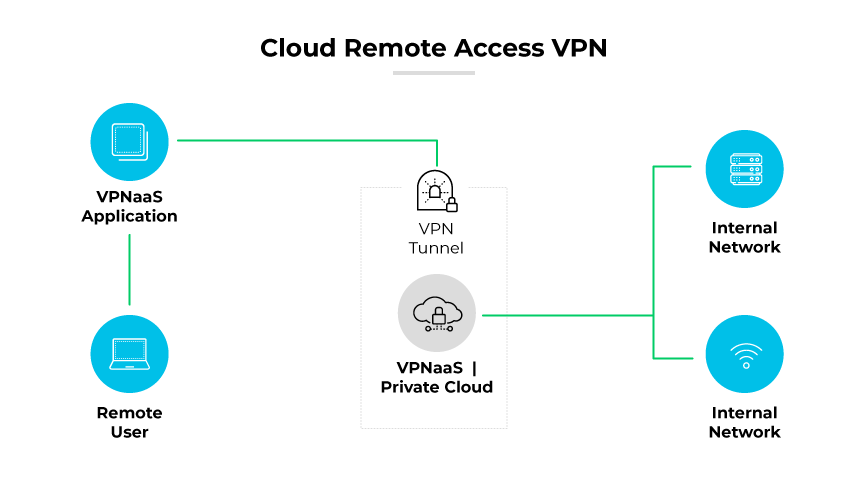
Cloud VPN, sometimes referred to as hosted VPN or VPN as a service (VPNaaS), is a VPN approach tailored for cloud environments. This VPN allows users to securely access a business's resources, data, and applications in the cloud through a web interface or a dedicated app on desktop or mobile.
Unlike conventional VPNs that necessitate specific infrastructure at the user's location, cloud VPNs integrate seamlessly into a company's cloud distribution framework. One significant benefit of cloud VPNs is rapid worldwide configuration and deployment.
Using a Cloud VPN enhances security compared to traditional VPNs and contributes to a more adaptable, nimble, and scalable cloud setup for businesses.
Further reading: What Is a Cloud VPN?
SSL VPN
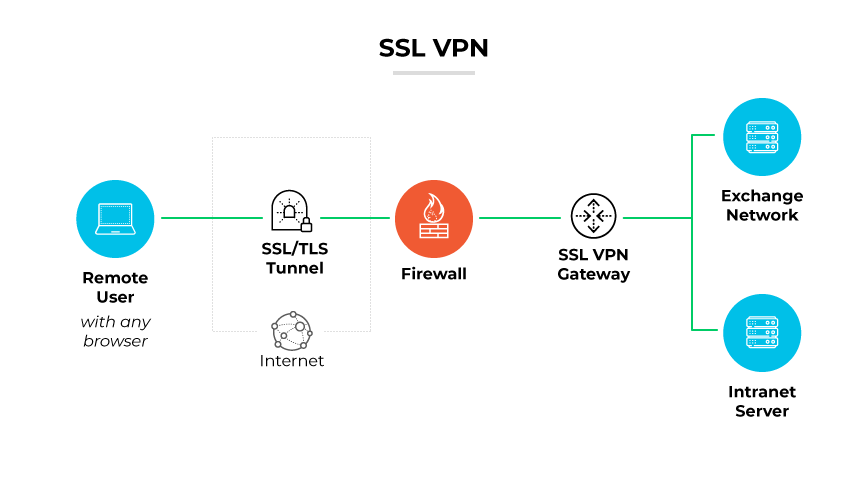
An SSL VPN, or Secure Sockets Layer virtual private network, allows remote users to connect to private networks in a secure manner. It employs the SSL security protocol, or its successor, the Transport Layer Security (TLS) security protocol, to ensure the encrypted transmission of data between the user's device and the VPN gateway. This encryption safeguards the integrity and confidentiality of data, ensuring that unauthorized entities cannot intercept or alter it.
Unlike some VPN solutions, an SSL VPN does not require specialized VPN client software on users' devices. Instead, it uses standard web browsers, making it more accessible and reducing the deployment complexity. All communications between the user's web browser and the VPN device are encrypted, making it safe for data transfer across potentially insecure networks.
There are two types of SSL VPNs:
SSL Portal VPN
In this model, users access a single webpage, or portal, which provides links to other private network resources. By visiting a specific website and entering credentials, users can initiate a secure SSL connection. This portal then grants access to designated applications or network services, as predefined by the organization.
SSL Tunnel VPN
This variant is more comprehensive, enabling users to securely access multiple network services, not just those that are web-based. It establishes an encrypted tunnel under SSL, allowing for the secure access of various resources. To function optimally, SSL Tunnel VPN might require browsers equipped with additional applications, such as JavaScript or Flash.
Further reading: What Is a SSL VPN?
Double VPN
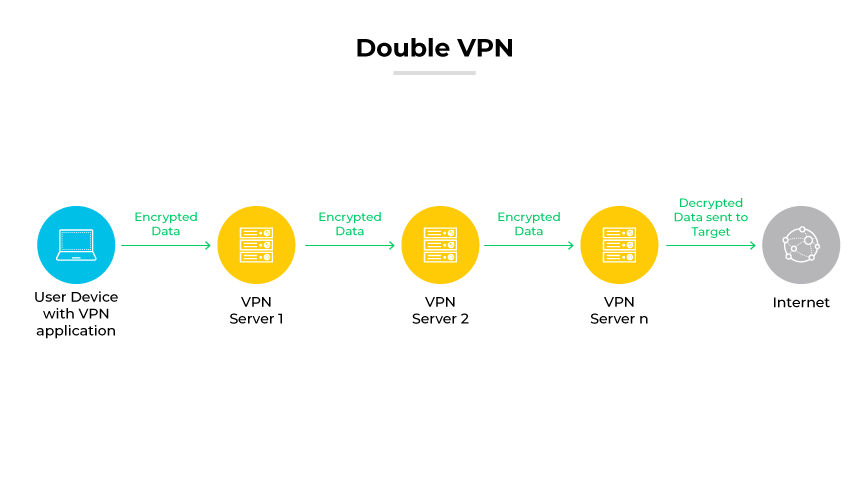
A double VPN is more of a configuration versus a type of VPN technology. This setup involves channeling user traffic through two sequential VPN servers, providing two layers of encryption. In standard VPN use, data flows from the user's device to a single VPN server and then to the destination online. Using a double VPN configuration, the user's data is first encrypted and sent to an initial VPN server. Then it's encrypted again and directed to a second VPN server before reaching its final online destination.
While the double VPN method heightens security by adding an extra layer of encryption, it can also lead to slower connection speeds. This slowdown is a result of the data passing through two separate servers and undergoing dual encryption processes. While beneficial for those seeking augmented security, it may not be ideal for all due to potential performance impacts.
Further reading: What Is a Double VPN?
How to Choose the Right VPN for Your Business
| VPN Type | Connection Type | Software Type | Use Cases |
|---|---|---|---|
| Remote Access VPN | User connects to a private network | Software installed on both a private device and the private network | Connecting to a private network from your home or personal location |
| Site-to-Site VPN | Private network connects to another private network | Software on both networks, users do not need apps | Creating a secure tunnel between two private networks |
| SSL VPN | Devices establish a secure remote access VPN connection with a web browser | Modern web browser or client applications that enable direct access to networks. There are two primary types: VPN portal and VPN tunnel | Enterprises use SSL VPNs to enable remote users to securely access organizational resources and to secure the internet sessions of users |
| Cloud Based Remote Access VPN | User connects to a company's applications, data, and files in the cloud | Accessible via a website or desktop/mobile application; No need for VPN infrastructure on user's end | Secure access to both the company’s cloud and data center-based applications and data |
| Double VPN | Use of two VPNs simultaneously, though practically challenging | Specialized software configuration or utility, but often results in conflicts | Enhanced security through multiple VPN layers, although challenging to implement properly |
The modern business landscape has seen a surge in remote work. Many companies now operate with distributed teams. This shift has increased the need for secure, remote access to company resources. Virtual private networks (VPNs) address this need. They provide encrypted connections between remote users and company networks.
However, choosing a VPN is more than simply selecting a product. It's a part of a larger network security strategy. Different VPNs cater to different business needs. Some are ideal for connecting branch offices, while others are designed for individual remote workers. Security features vary among VPN providers. Encryption strength, logging policies, and server locations are essential considerations. Businesses must assess their specific needs, research available options, and select a VPN that aligns with their overall security strategy.