- 1. Why is firewall management important?
- 2. What are the main types of firewalls?
- 3. What are the key components of firewall management?
- 4. Who should be responsible for managing firewalls?
- 5. What are the main firewall management challenges?
- 6. Top 6 best practices for firewall management
- 7. How to choose the right firewall management system for your needs
- 8. Firewall management FAQs
- Why is firewall management important?
- What are the main types of firewalls?
- What are the key components of firewall management?
- Who should be responsible for managing firewalls?
- What are the main firewall management challenges?
- Top 6 best practices for firewall management
- How to choose the right firewall management system for your needs
- Firewall management FAQs
What Is Firewall Management?
- Why is firewall management important?
- What are the main types of firewalls?
- What are the key components of firewall management?
- Who should be responsible for managing firewalls?
- What are the main firewall management challenges?
- Top 6 best practices for firewall management
- How to choose the right firewall management system for your needs
- Firewall management FAQs
Firewall management is the process of configuring, monitoring, and maintaining firewalls to ensure they effectively protect a network.
It involves setting up rules to allow or block specific traffic, regularly auditing these rules, and monitoring logs to detect and respond to potential security incidents. Effective firewall management ensures vulnerabilities are addressed, threats are mitigated, and network operations remain secure and uninterrupted.
Why is firewall management important?
Firewall management is crucial for maintaining the security and integrity of a network.
Firewalls act as a barrier between internal networks and potential external threats. They filter traffic to prevent unauthorized access and cyberattacks. Proper firewall management ensures these protective measures are consistently effective and up-to-date.
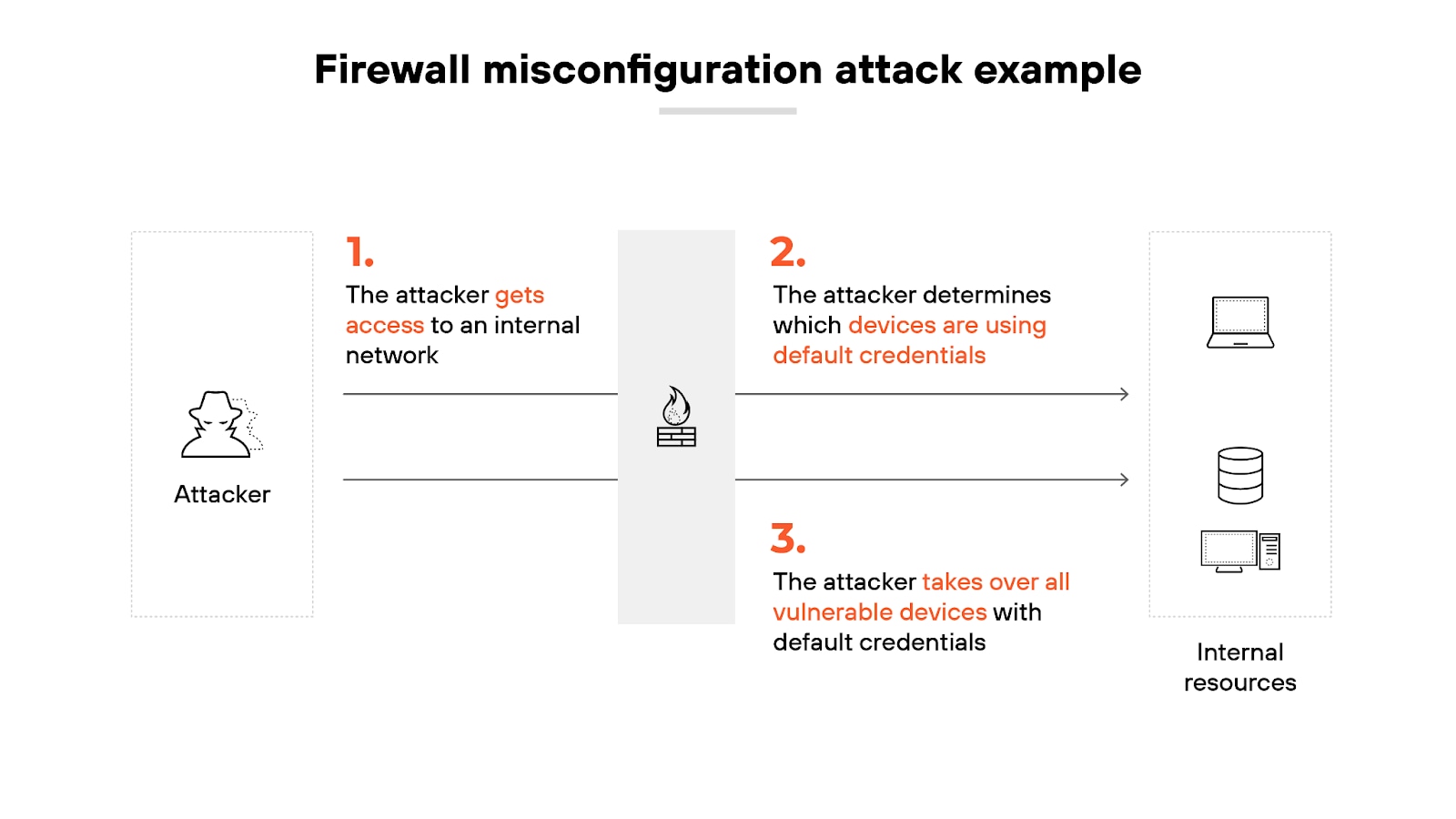
Without regular management, firewalls can become ineffective. Outdated rules and configurations may not address new threats, leaving networks vulnerable.
For example: Old or conflicting firewall rules can be exploited by attackers and compromise the entire system. Regular audits and updates are necessary to close these gaps and strengthen defenses.
Effective firewall management also optimizes network performance. By regularly reviewing and updating firewall rules, administrators can prevent bottlenecks and make sure data flow is smooth. Establishing a balance between security and performance helps maintain efficient operations without compromising protection.
Plus, firewall management is essential for compliance with industry standards and regulations. Standards like the payment card industry data security standard (PCI DSS) require strict firewall configurations to protect sensitive data. Regularly managing firewalls helps organizations adhere to these requirements and avoid potential legal and financial penalties.
What are the main types of firewalls?
Before we dive into the details of firewall management, it’s important to first establish the different types of firewalls available.
Here’s why:
Modern organizations use a broad range of firewall products for effective network security. In general, they all have the same objective: serve as the first line of defense by scrutinizing and controlling network traffic to thwart potential cyber threats.
However, every firewall uses a distinct process to achieve this goal.
Note: There are many types of firewalls, often categorized by system protected, form factor, network placement, and data filtering method. Organizations may require multiple firewall types for effective network security. Also, one firewall product can deliver multiple firewall types.
For the purposes of the topic of firewall management, we can break the main types of firewalls down as follows:
- Proxy firewalls
- Traditional firewalls
- Next-generation firewalls (NGFWs)
- Cloud firewalls
Let’s dive into the details of each.
Proxy firewalls
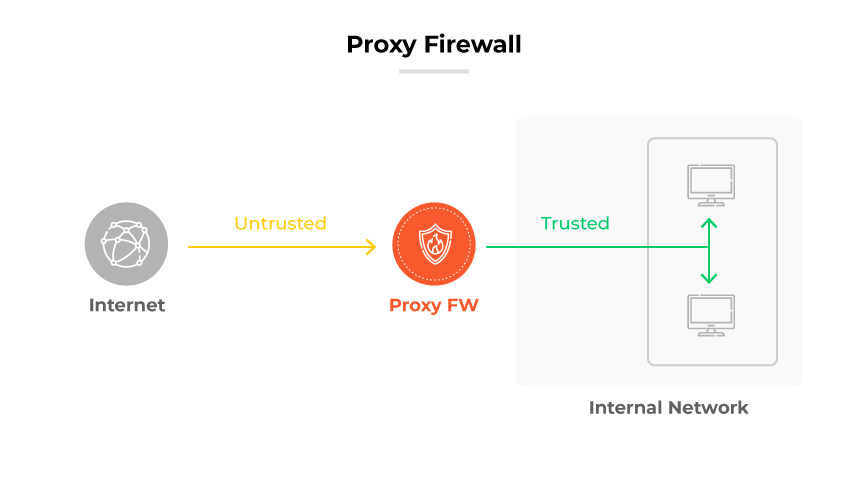
Proxy firewalls serve as intermediaries between internal users and external networks.
They work by intercepting and analyzing incoming and outgoing traffic at the application layer. Which means that instead of allowing direct connections, proxy firewalls process requests and responses on behalf of users.
As a result, they add an extra layer of security. And that prevents potential threats from directly reaching the internal network.
However, the process can introduce latency—making proxy firewalls slower compared to other firewall products.
Traditional firewalls
Traditional firewalls operate at the network or transport layer. They use predefined rules to control traffic flow based on IP addresses, port numbers, and protocols.
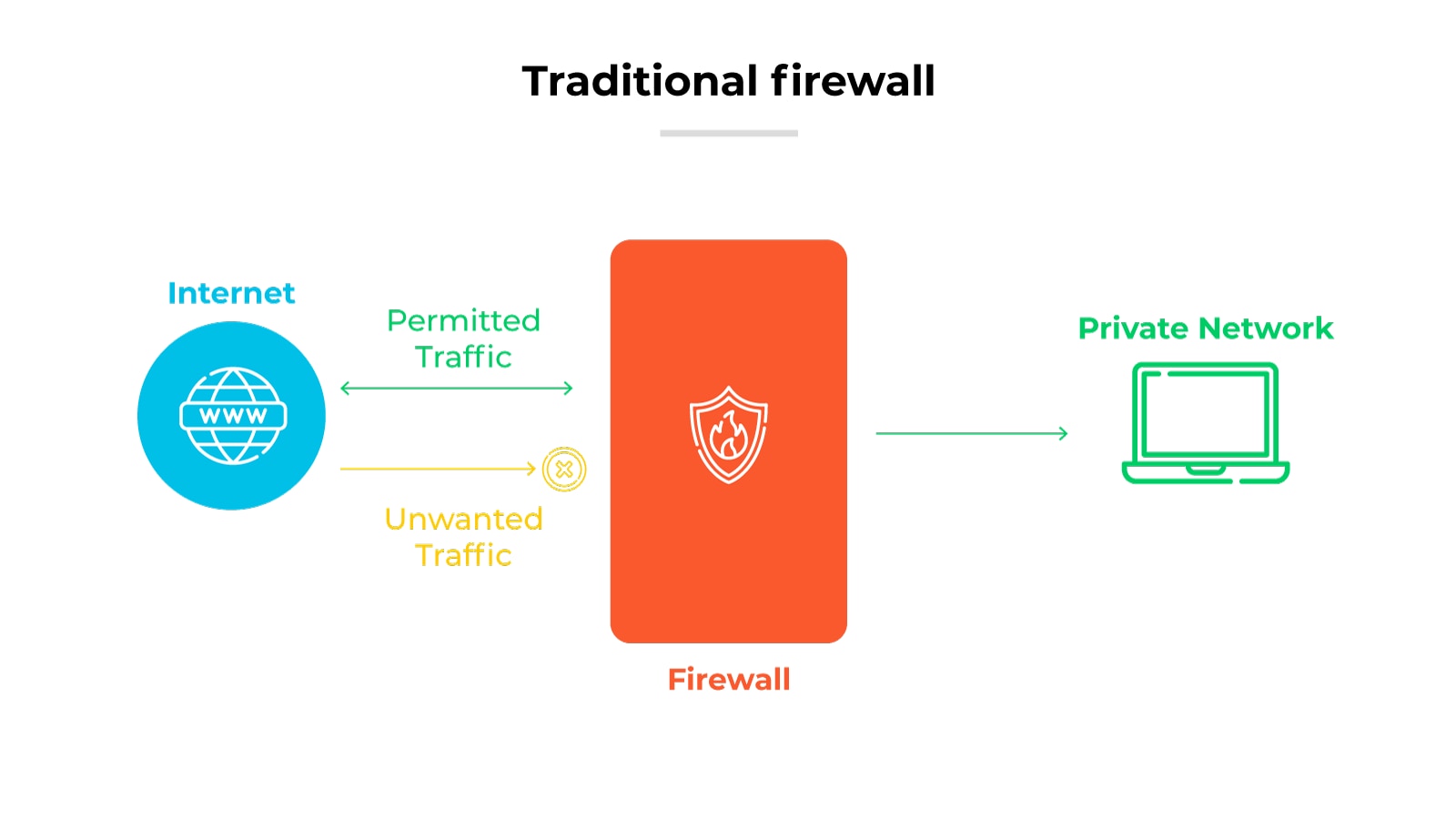
There are two main types of traditional firewalls: stateless and stateful.
Stateless firewalls, also known as packet filtering firewalls, inspect packets individually without considering past traffic patterns.

Stateful firewalls, also known as stateful inspection firewalls, maintain context about active connections, which allows more informed decision-making.
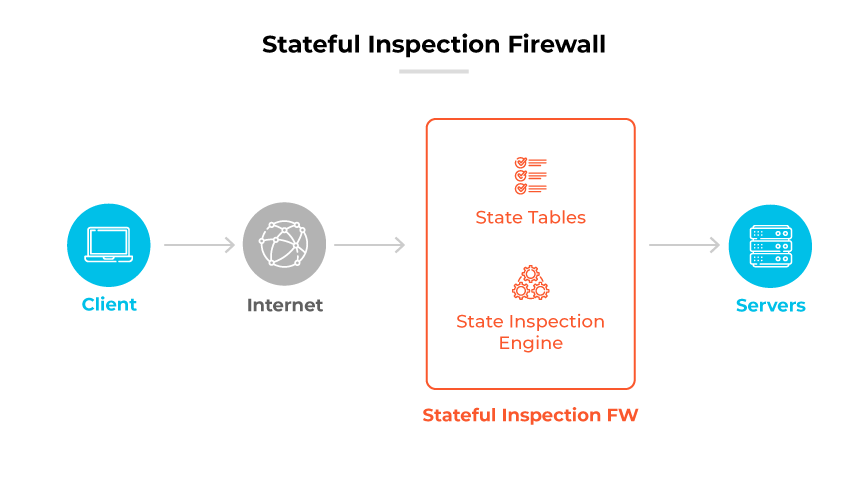
Traditional firewalls were historically common in many network security setups because they have a straightforward, relatively effective approach to filtering traffic.
Next-generation firewalls (NGFWs)
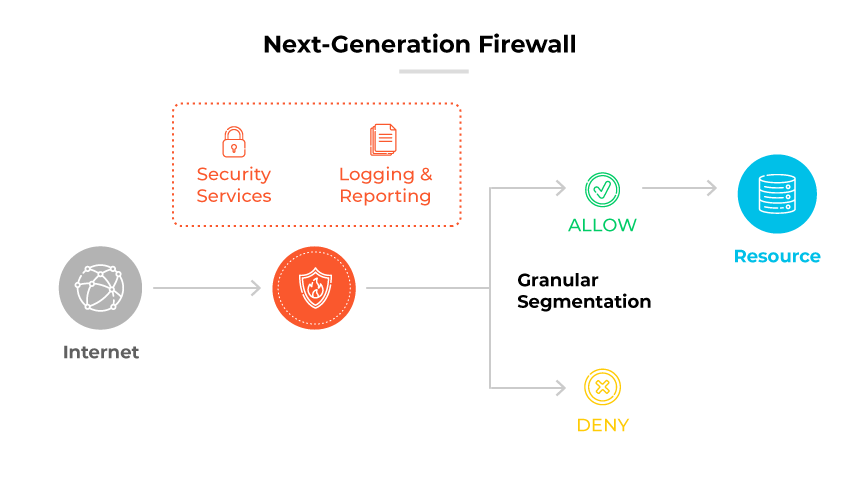
Next-generation firewalls (NGFW) build upon the capabilities of traditional firewalls by incorporating advanced features, including but not limited to:
- Deep packet inspection
- Intrusion prevention
- Application traffic analysis and control
- Cloud-sourced threat intelligence
- Advanced malware detection and prevention
NGFWs can identify and control applications regardless of port, protocol, or IP address used. They can also detect and block sophisticated threats like malware and exploits.
Cloud firewalls
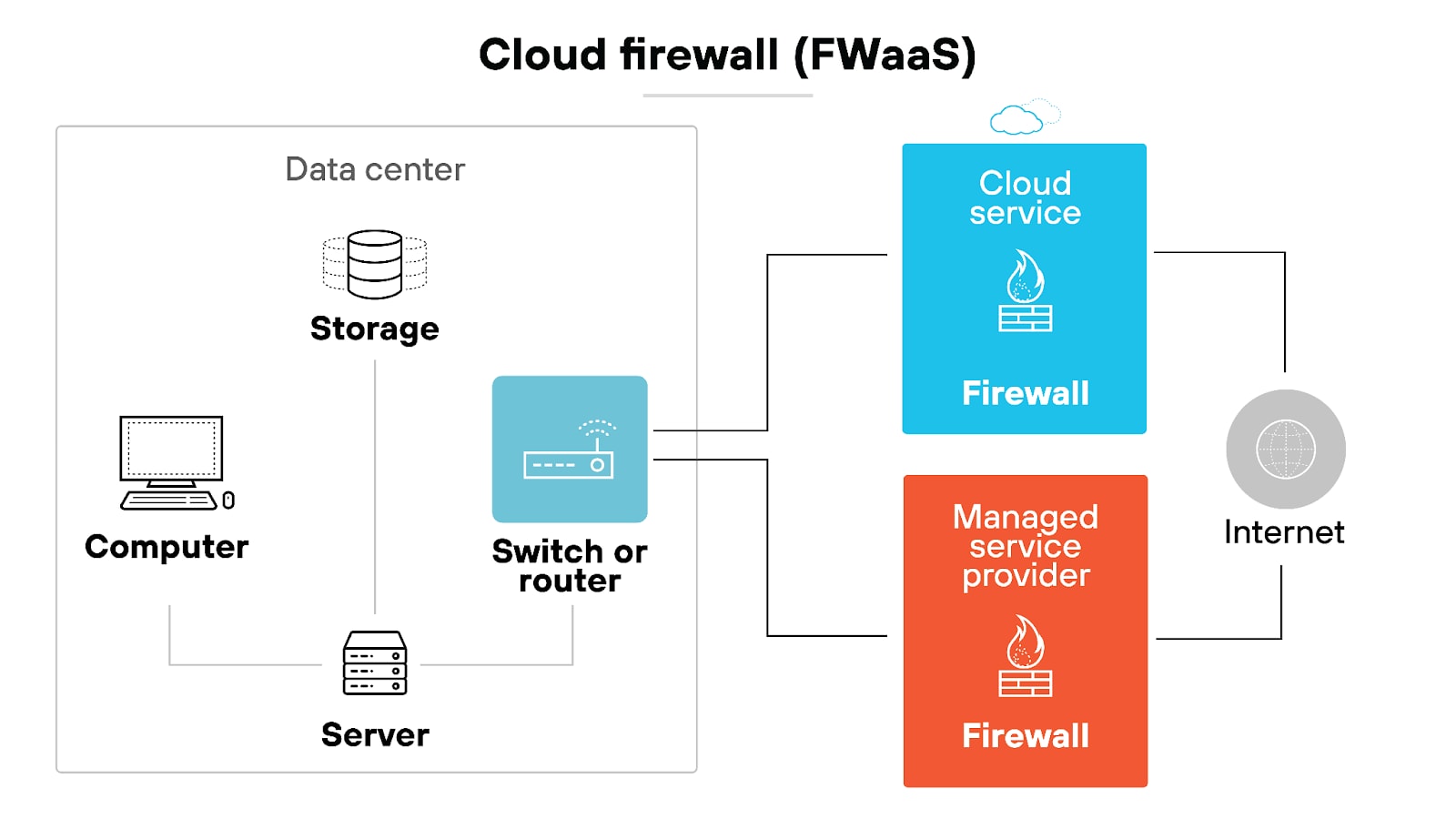
Cloud firewalls, also known as firewall-as-a-service (FWaaS), are a variation of software firewalls which protect cloud infrastructure and applications.
They offer similar functionalities to traditional and next-generation firewalls but are hosted in the cloud. Which makes them scalable and easy to deploy. Cloud firewalls are ideal for organizations with cloud-based environments.
They can also provide centralized security management to protect distributed network resources with consistent policies.
What are the key components of firewall management?
Firewall management is a multifaceted process that’s crucial for maintaining network security.
Effective firewall management involves:
- Policy control
- Configuration
- Rule management
- Change management
- Compliance
- Performance optimization
- Monitoring
- Automation
Each component plays a vital role in protecting against evolving threats.
Policy control
Policy control is the foundation of firewall management.
It involves defining the rules that determine which traffic is allowed or blocked. Rules are based on factors like source and destination IP addresses, port numbers, and protocols.
Like this:
Proper policy control ensures that the firewall enforces the organization's security policies, allowing legitimate traffic while blocking potential threats.
Firewall configuration
The initial setup of a firewall is critical.
Firewall configuration involves setting up rules and parameters that dictate how the firewall handles incoming and outgoing network traffic.
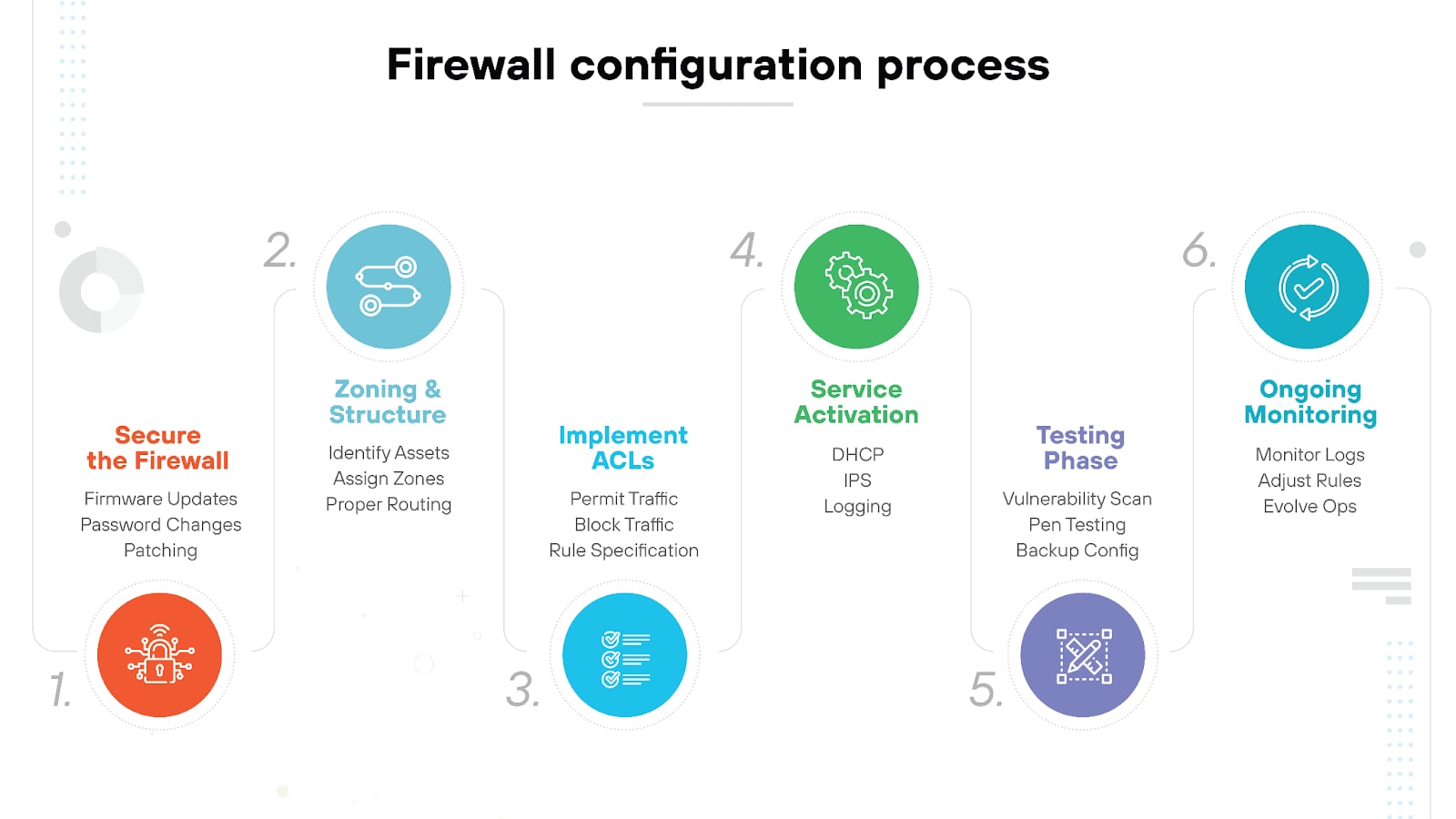
The firewall configuration process includes:
- Securing the firewall
- Designing firewall zones and IP address structure
- Implementing access control lists (ACLs)
- Activating additional services and logging
- Testing the configuration
- Ongoing monitoring and management
A properly configured firewall establishes a strong foundation for network security.
Firewall rule management
Managing firewall rules is an ongoing process:
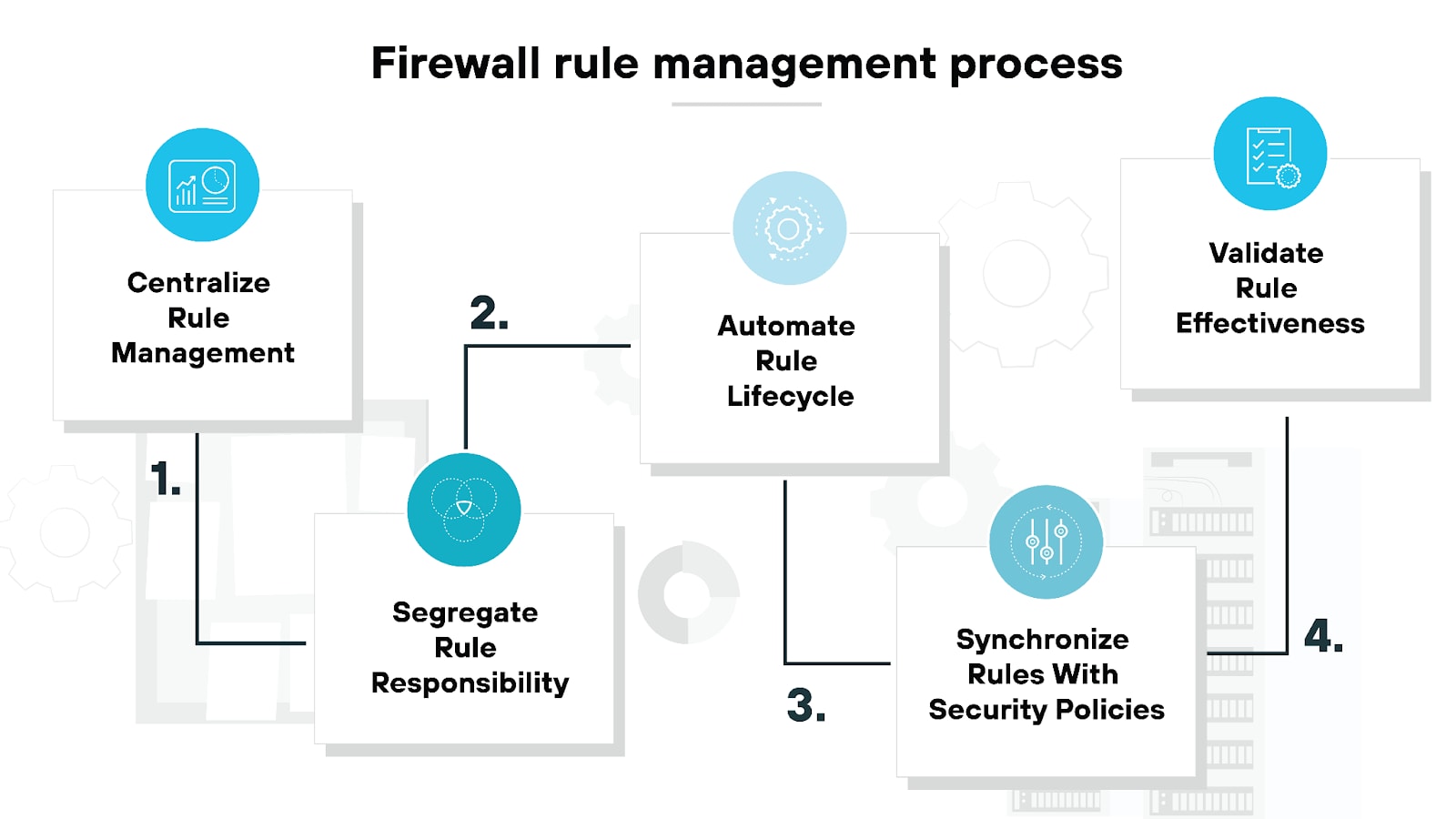
Firewall rule management involves identifying and removing outdated or redundant rules to streamline performance and enhance security.
Doing reviews and optimization activities regularly ensures firewall rules align with current security policies and effectively mitigate emerging threats.
Managing rules consistently also maintains optimal firewall performance.
Note: Policy control and rule management are related but distinct concepts in firewall management. Policy control defines the overarching rules for traffic flow based on security policies, while firewall rule management involves the ongoing maintenance and optimization of these rules to ensure effective performance and security.
Firewall change management
Firewalls have to be kept current with the latest patches and updates to address known vulnerabilities.
Change management involves regularly applying updates and patches to the firewall software:
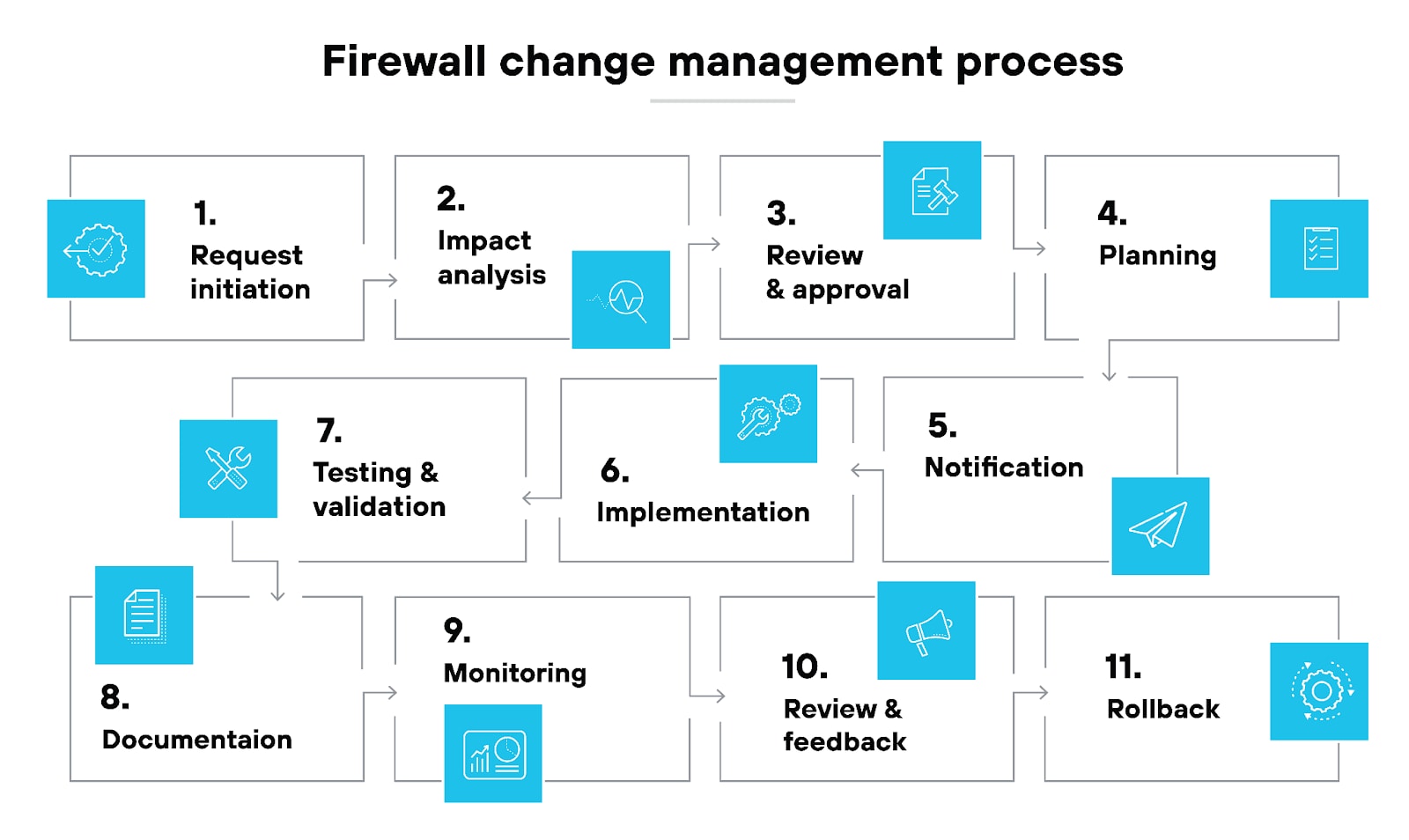
The process reduces security risks and keeps the firewall effective against any new exploits and threats.
Good change management majorly influences network security.
Ensuring firewall compliance
Adhering to industry-specific regulations and compliance standards are another pretty important part of managing firewalls.
Making sure firewall configurations and policies meet regulatory requirements helps organizations protect sensitive data. Not to mention avoid compliance violations.
Regular audits and reviews are necessary to maintain compliance and address any gaps in security practices.
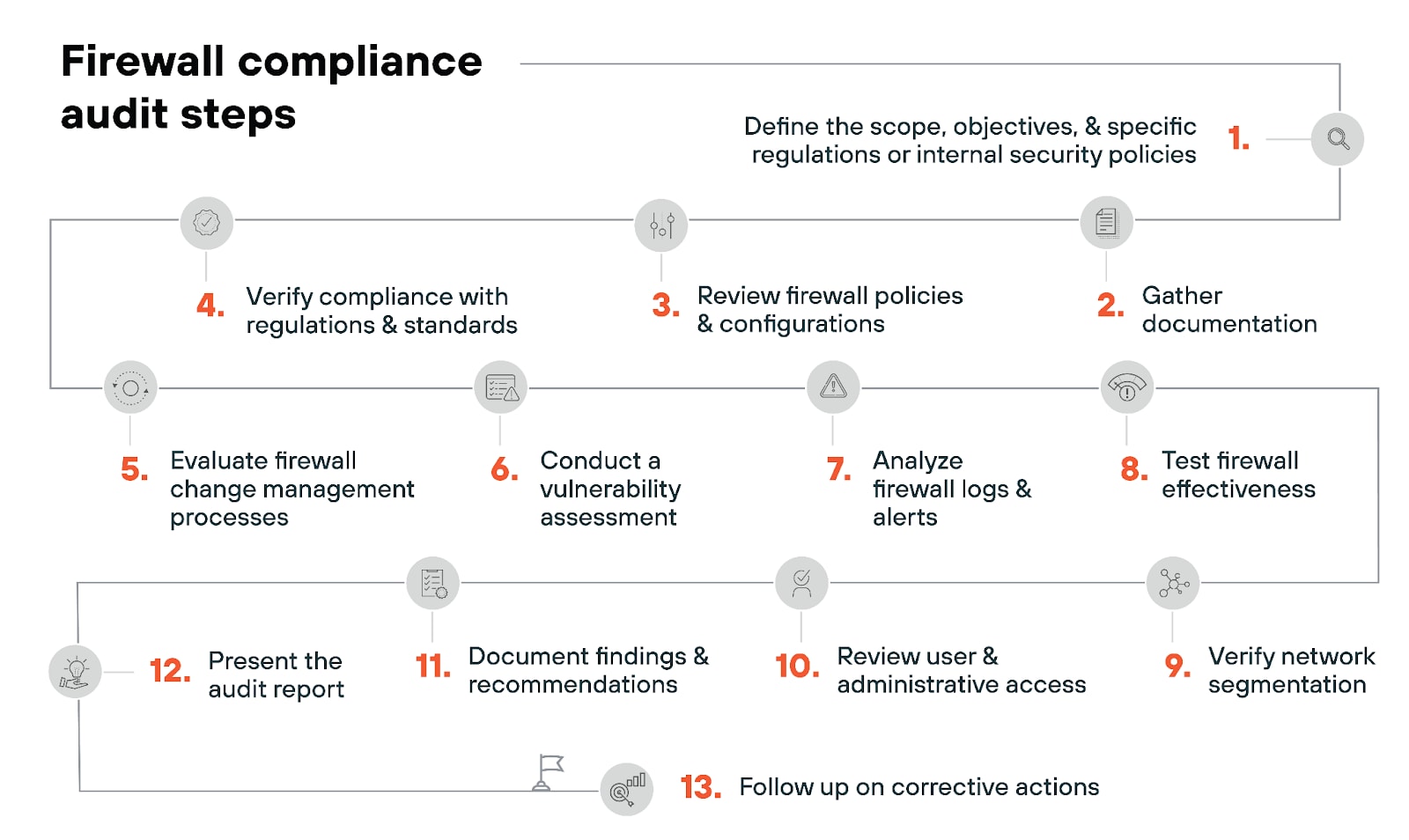
Firewall performance optimization
Firewall performance management focuses on ongoing maintenance and tuning so the firewall operates efficiently. Which includes troubleshooting any issues that may impact network security or throughput.

For example: Consider a scenario where a shadow anomaly occurs.
Let’s say you have two rules in your firewall rule set, like this:
Rule 1: Allow traffic from IP range 192.168.1.0/24 to any destination on port 80.
Rule 2: Deny traffic from IP 192.168.1.50 to any destination on port 80.
As you can see, Rule 1 is more general and allows traffic from the entire 192.168.1.0/24 network to any destination on port 80. But Rule 2 is specific to a single IP address within that range (192.168.1.50).
Which means that Rule 2 is shadowed by Rule 1 because Rule 1 allows traffic from the entire subnet, including 192.168.1.50, making the deny action of Rule 2 ineffective.
To resolve the shadow anomaly, Rule 2 should be placed before Rule 1 in the rule set. Firewall rules are typically processed in order, so the specific deny action would be applied before the general allow rule.
In other words, the correct order looks like this:
Rule 2: Deny traffic from IP 192.168.1.50 to any destination on port 80.
Rule 1: Allow traffic from IP range 192.168.1.0/24 to any destination on port 80.
This is an example of a critical task in firewall performance management: ensuring that rules are optimized for both security and efficiency.
By optimizing performance, organizations can maintain a stable, resilient network environment. And be sure the firewall doesn’t become a bottleneck.
Monitoring and reporting
Continuous monitoring and reporting are yet another essential element of maintaining a secure network and managing firewalls.
Analyzing firewall logs and activity gives network and security admins helpful insights into security trends and policy effectiveness.
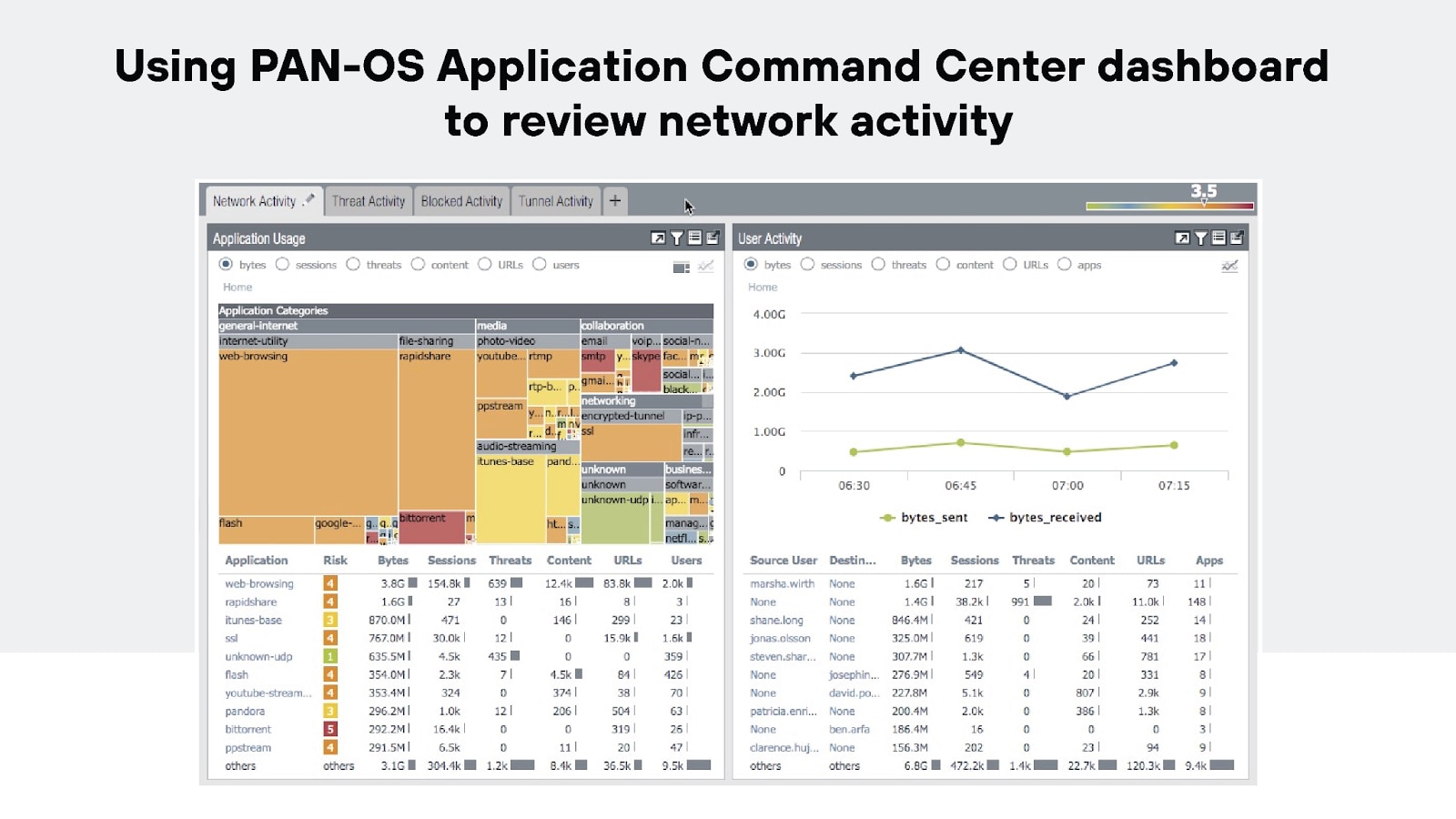
Plus, regular reports help identify any gaps in security and areas for improvement. This way, firewall management practices stay effective.
Automation
Automation can majorly improve the firewall management process.
Automation tools help analyze traffic patterns, suggest rule optimizations, and ensure consistency across multiple firewalls.
For example:
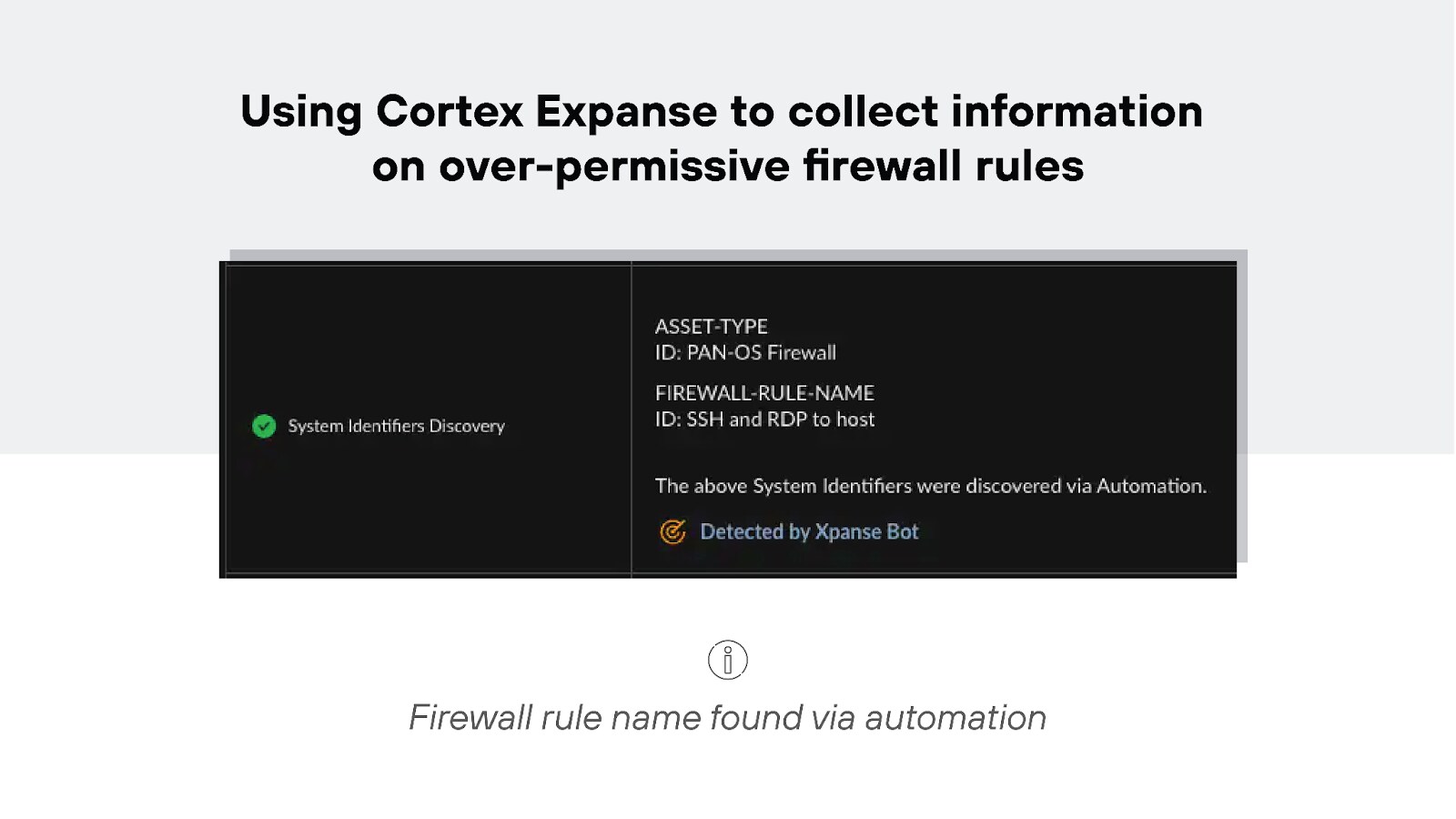
It also reduces the risk of human error and makes managing complex firewall environments a lot more efficient.
Further reading:
- What Is Firewall Configuration? | How to Configure a Firewall
- How to Troubleshoot a Firewall | Firewall Issues & Solutions
Who should be responsible for managing firewalls?
Managing firewalls is a key part of keeping the network secure. Needless to say, deciding who should handle the job is important to make sure firewalls are set up, maintained, and monitored properly.
So, who should manage firewalls and why does it matter?
Doing firewall management right requires a team effort. One that involves various roles within the organization.
The IT and network security team are the main players. They should be handling configuration, monitoring, and responding to incidents.
For organizations who don’t have the in-house expertise needed for effective firewall management: Outsourcing to managed security service providers (MSSPs) is an option. MSSPs bring specialized knowledge and 24/7 monitoring capabilities. If your IT and network security staff are limited, going with this option will allow the resources you do have to focus on core business activities.
Also:
While IT security teams and network admins handle the day-to-day activities, it’s worth mentioning that other roles often have a vested interest firewall management:
- Compliance officers are sometimes involved in verifying that firewall configurations and policies meet regulatory standards. Although compliance officers aren’t part of the daily technical tasks, they do work with network and security personnel to conduct regular audits and reviews.
- Executive leadership might be a part of setting the strategic direction for the organization’s security posture. They also allocate resources. Executive influence is usually focused on making sure firewall management procedure aligns with business objectives and risk management strategies.
What are the main firewall management challenges?
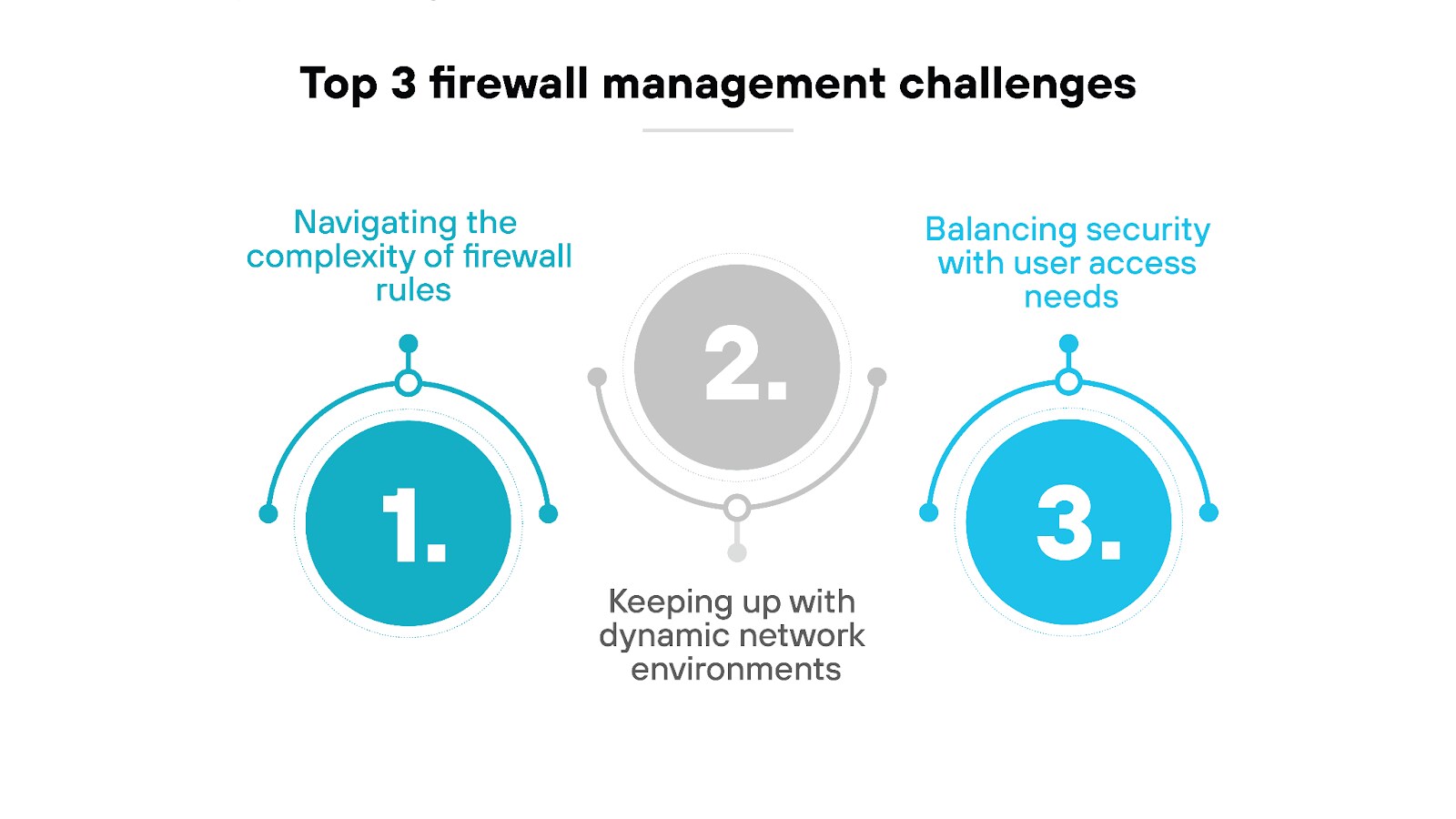
As with all network security activities, managing firewalls does come with several challenges, though none that can’t be overcome. Most network admins would agree that firewall rules, changes, and user access are the quintessential obstacles that come along with staying on top of firewalls.
Navigating the complexity of firewall rules
One of the biggest challenges in firewall management is dealing with the complexity of rules.
Firewalls often have hundreds or thousands of rules. And managing them can become overwhelming.
Not to mention, over time, rules can become outdated, redundant, or conflict with each other.
Optimizing firewall rules involves regular reviews to ensure they’re effective, up-to-date, and don’t introduce unnecessary complexity.
Keeping up with dynamic network environments
Modern networks are super dynamic. Traffic patterns, applications, and user behaviors change frequently. Which means firewalls have to adapt in real time.
Firewalls have to be configured to accommodate changes—and without compromising security. So, network and security personnel have to monitor and adjust firewall rules constantly to make sure they’re working with current network conditions.
Balancing security with user access needs
Dealing with user access is one of the biggest challenges when it comes to firewall management.
That’s because firewalls have to control access for both internal and remote users. And that includes those with privileged access.
The core issue here is really about balancing security with accessibility. Firewalls have to allow legitimate users to work without unnecessary hindrance. At the same time, they need to block unauthorized access.
Implementing multi-factor authentication and role-based access control helps keep a balance. Monitoring user activities regularly also makes it easier to stay on top of access.
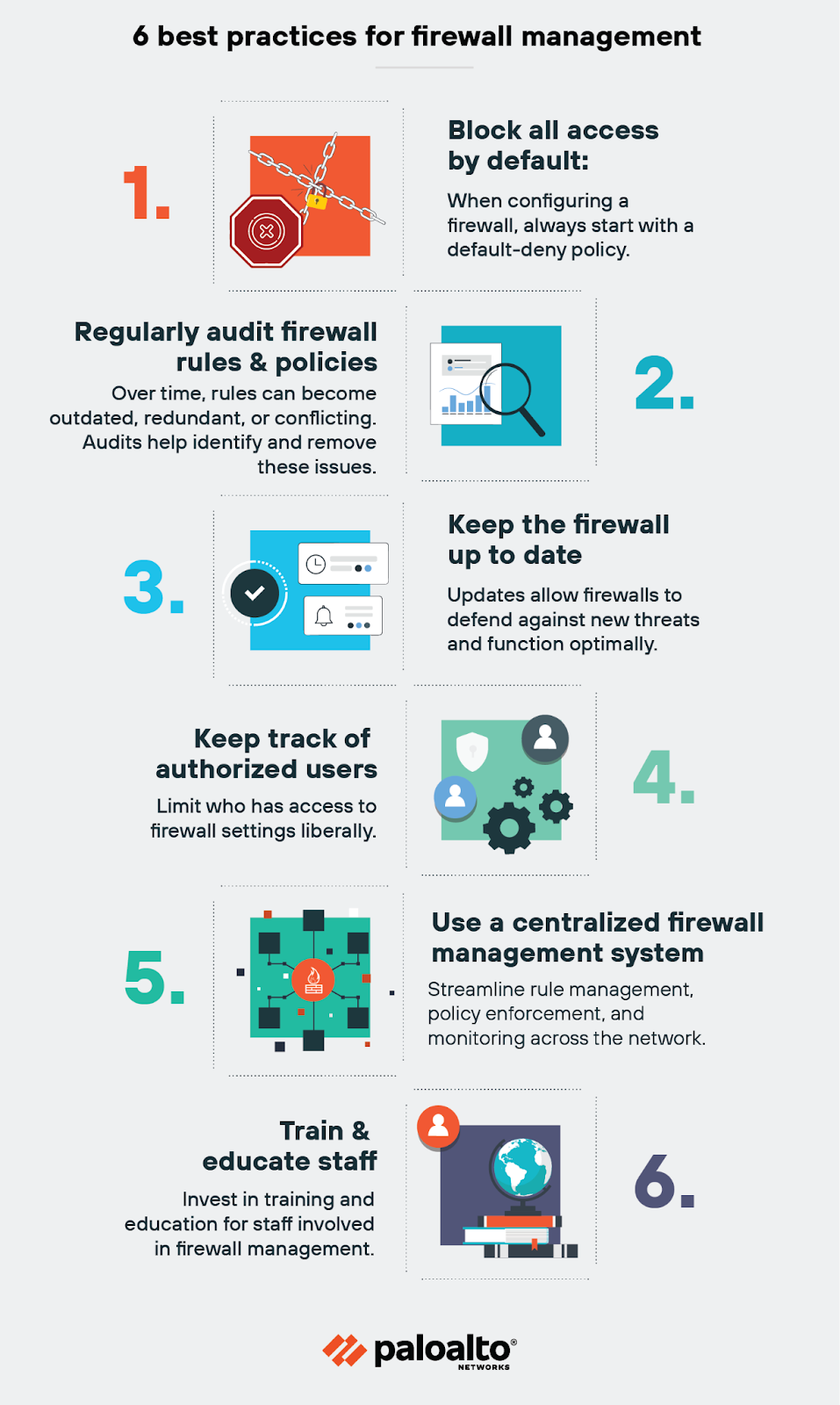
Top 6 best practices for firewall management
Let's explore the top best practices for managing firewalls.
These tactics help protect against external threats, minimize internal security risks, and ensure that the network remains secure and compliant with regulatory requirements.
Remember: firewall management is an ongoing process.
1. Block all access by default
When configuring a firewall, always start with a default-deny policy. Which means blocking all incoming and outgoing traffic—unless explicitly allowed by other rules.
This will reduce the risk of unauthorized access by only permitting traffic that meets specific security criteria.
2. Regularly audit firewall rules and policies
Conducting regular audits of firewall rules and policies is essential.
As discussed, over time, rules can become outdated, redundant, or conflicting. Audits help identify and remove these issues. This way, the firewall remains efficient and secure.
Reviewing logs and monitoring changes are fundamental parts of the process.
Auditing is really about refining and optimizing firewall settings on an ongoing basis.
3. Keep the firewall up to date
Keep firewall software and firmware up to date at all times. No exceptions.
Vendors frequently release updates that address vulnerabilities, add new features, and improve performance. Stay on top of them. Updates allow firewalls to defend against new threats and function optimally.
Tip: Automate firewall software and firmware updates where possible to streamline this process.
4. Keep track of authorized users
Limit who has access to firewall settings liberally. Monitor always.
Only senior network admins or designated security personnel should have the ability to modify firewall configurations.
Implement role-based access controls (RBAC) so that users only have the permissions necessary for their roles.
Don’t forget to regularly review user access and monitor any changes to help prevent unauthorized modifications.
5. Use a centralized firewall management system
Deploying a centralized firewall management system streamlines rule management, policy enforcement, and monitoring across the network. Centralization enhances visibility and control, making it easier to maintain consistent security measures and respond to incidents.
6. Train and educate staff
Investing in training and education for staff involved in firewall management is essential. Ensuring that they are knowledgeable about best practices, security threats, and the latest technologies helps maintain a high level of network security. Regular training sessions and staying updated with industry developments are key components of this practice.
How to choose the right firewall management system for your needs
Choosing the right firewall management system is crucial for maintaining network security and ensuring efficient operations. With numerous options available, it can be challenging to determine which system best fits your organization's needs. Here’s a guide to help you make an informed decision.
Assess your network size and complexity
First, evaluate the size and complexity of your network. Smaller networks may require simpler solutions, while larger, more complex networks need advanced features and scalability. Understanding your network’s structure and needs will help you narrow down your options.
Ensure scalability
Choose a firewall management system that can scale with your organization. As your business grows, the system should handle increasing traffic, users, and devices without compromising performance.
Look for integration capabilities
Select a system that integrates seamlessly with your existing security tools and systems. This includes SIEM (Security Information and Event Management) systems, intrusion detection systems, and threat intelligence platforms.
Opt for automation features
Choose a system with automation capabilities for rule creation, policy enforcement, and threat detection. Automation reduces manual workload, minimizes errors, and ensures timely responses to security incidents.
Check for a user-friendly interface
Ensure the system has a user-friendly interface. The system should be easy to navigate, with clear dashboards and intuitive controls, helping administrators quickly configure, monitor, and manage firewalls.
Verify security and compliance support
Ensure the firewall management system supports compliance with industry standards and regulatory requirements like PCI DSS, HIPAA, or GDPR. The system should provide regular updates to address new vulnerabilities and threats.
Evaluate vendor support and reputation
Research the vendor’s reputation and the level of support they offer. Reliable customer support and a solid track record can make a significant difference in the effectiveness of your firewall management system. Check reviews, testimonials, and case studies.
Demand robust reporting and analytics
Choose a system that provides detailed reports on firewall activities, rule effectiveness, and potential threats. These insights help in making informed decisions and optimizing firewall configurations.
Assess cost and budget
Ensure the chosen system is cost-effective. Compare pricing models, including initial costs, subscription fees, and potential hidden charges. Ensure the system provides good value for the features and support offered.