Layer 3 vs Layer 7 Firewall: What Are the Differences?
The difference between a layer 3 and layer 7 firewall is that layer 3 firewalls filter traffic based solely on IP addresses and port numbers, while layer 7 firewalls inspect the content within application data to make more detailed decisions.
More specifically, layer 3 firewalls quickly filter traffic based on IP addresses and ports, offering high throughput without inspecting content. In contrast, layer 7 firewalls examine application layer data to address complex threats targeting specific vulnerabilities, which is essential for thorough security but requires more computational resources.
What is a layer 3 firewall (network firewall)?
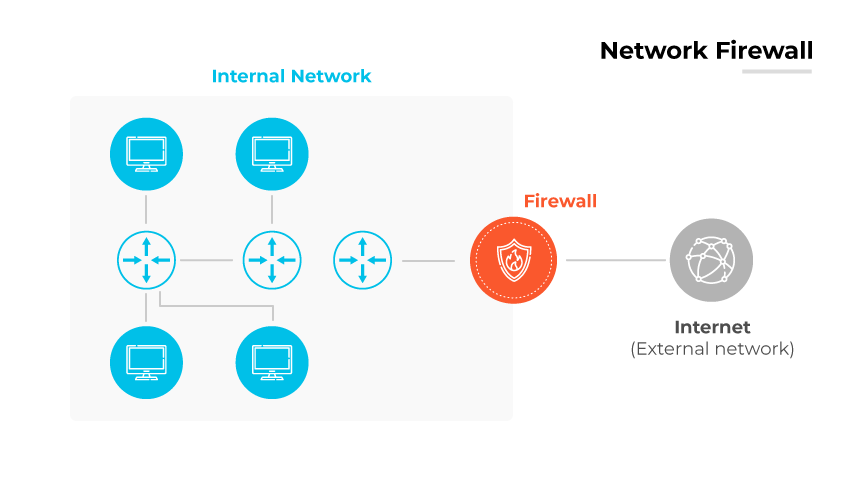
A layer 3 firewall, also known as a network firewall, operates at the network layer of the OSI model—the same level as routers. This type of firewall monitors and filters traffic based on IP addresses and port numbers, using protocols similar to those that routers use.
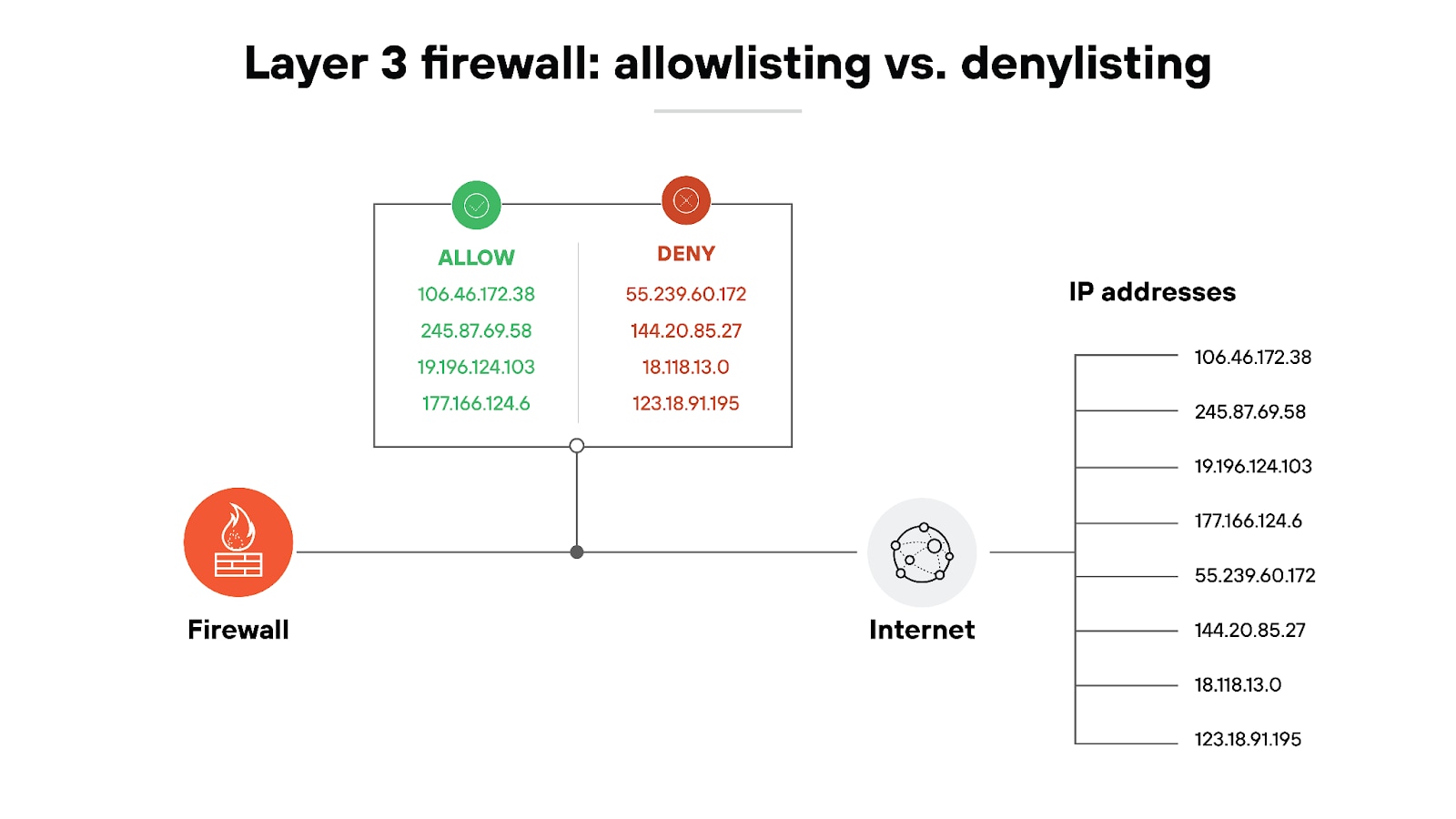
For example: A layer 3 firewall might allow traffic from specific IP addresses while blocking all others, which is a strategy known as allowlisting. Alternatively, it could block traffic from known malicious sources, AKA denylisting. This level of traffic management is effective because it allows or denies access based on source and destination ports, without examining the contents within the data packets.
Like this:
This method means that layer 3 firewalls can handle a fairly high volume of traffic efficiently. They’re designed to provide broad coverage, applying universally across any IP-based scenarios without the need for complex protocol-specific configurations.
However:
Layer 3 firewalls don’t inspect the content of data packets. They focus only on the outer parameters. For threats that exploit the content within packets, a more detailed inspection at a higher OSI model layer is necessary.
Further reading:
- What Is a Network Firewall?
- What Is a Packet Filtering Firewall?
- What Is a Stateful Firewall? | Stateful Inspection Firewalls Explained
- What Is a Perimeter Firewall?
What is a layer 7 firewall (application firewall)?
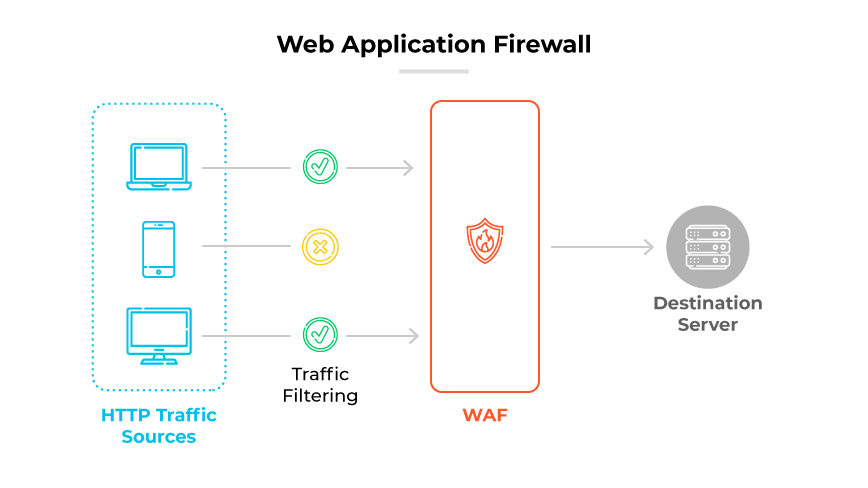
A layer 7 firewall, also known as an application firewall, operates at the application layer of the OSI model. The application layer is the topmost layer, which handles the actual content of the data traveling over the network.
Unlike simpler firewalls that filter traffic merely based on IP addresses and ports, layer 7 firewalls dive deeper—they examine the actual contents of data packets.
In other words, a layer 7 firewall can scrutinize the specifics of what's inside a data packet, like application data.
For example: A layer 7 firewall might allow traffic to a web server through HTTP but can block requests that contain malicious content like SQL injection attacks. This makes layer 7 firewalls incredibly effective at protecting against application-specific attacks that other types of firewalls might miss.
Here’s what it looks like:
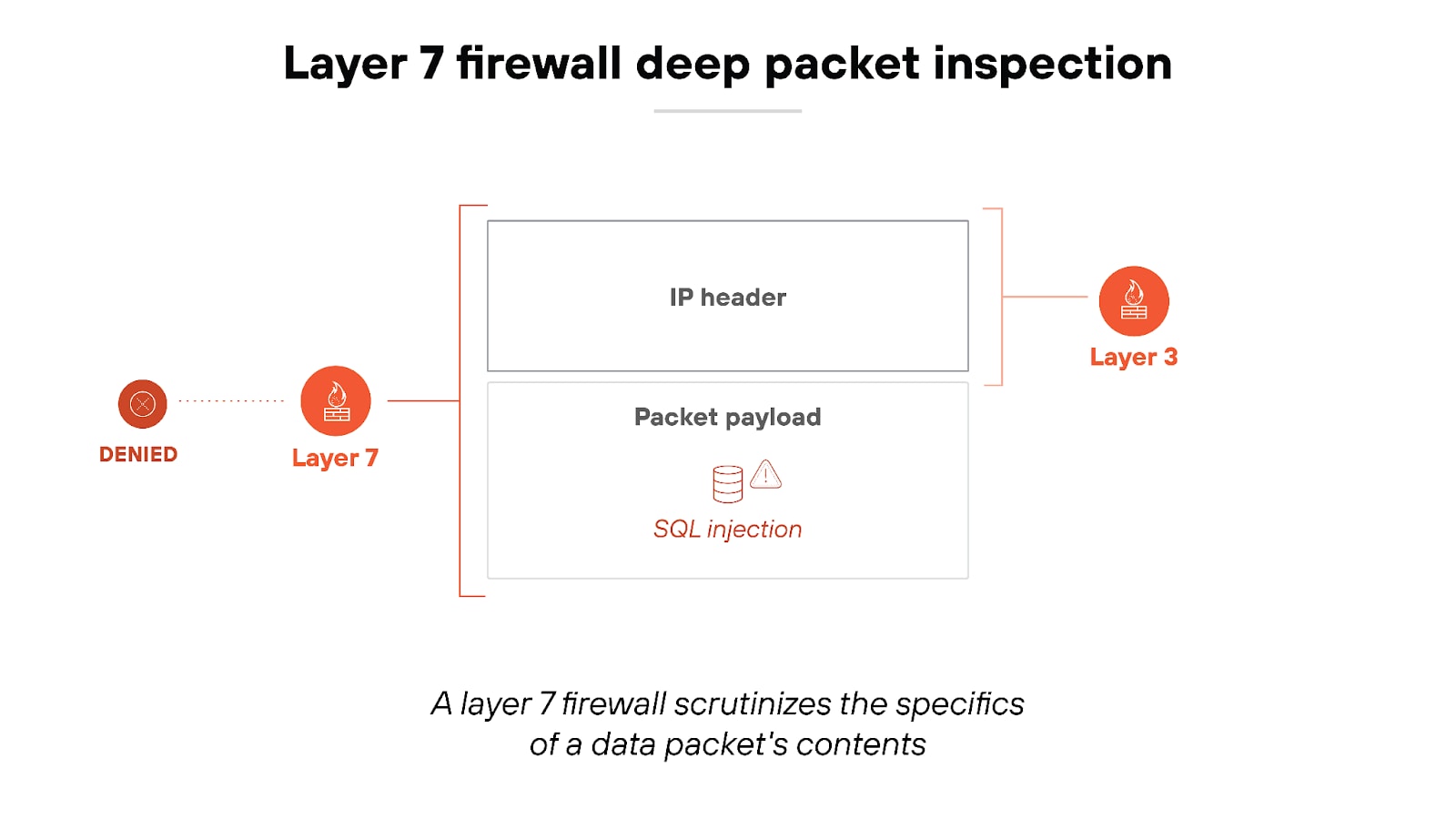
Note: Deep packet inspection does have its trade-offs.
Here’s why.
Layer 7 firewalls process and analyze much more information—which means they generally have lower throughput compared to layer 3 firewalls.
The process a layer 7 firewall undergoes includes:
- Decomposing each packet
- Inspecting its contents according to a complex set of rules
- Making a decision about whether to allow it through
The detailed scrutiny is computationally expensive. But crucial for securing applications from sophisticated attacks.
Why is this significant?
First, because web applications have effectively become the norm. Plus, cyber threats are exponentially increasing in sophistication.
Which makes a firewall’s ability to understand application-level data nonnegotiable. Layer 7 firewalls aren’t just filtering traffic. They’re actively analyzing it to detect and block potentially harmful interactions that occur at the highest level of network communication.
Further reading:
- What Is a Web Application Firewall?
- What Is a Proxy Firewall? | Proxy Firewall Defined & Explained
- What Is a Container Firewall?
- What Is a Virtual Firewall?
How do layer 3 and layer 7 firewalls compare?
Comparison: Layer 3 vs. layer 7 firewalls |
||
|---|---|---|
Layer 3 firewalls |
Layer 7 firewalls |
|
OSI model layer |
Network layer |
Application layer |
Traffic filtering |
Based on IP addresses and ports |
Examines contents within data packets |
Performance |
High throughput; handles large volumes of traffic |
Lower throughput due to deep packet inspection |
Speed of inspection |
Fast; simple filtering based on addresses & ports |
Slower; detailed analysis of packet contents |
Security focus |
General threats; basic access control |
Complex, application-targeted threats |
Use case |
Suitable where speed and volume are critical |
Needed for sensitive applications needing deep inspection |
Typical threat mitigation |
Blocks threats based on source/destination info |
Mitigates threats exploiting application vulnerabilities like SQL injections, XSS |
Layer 3 and layer 7 firewalls provide distinct forms of protection.
Again, layer 3 firewalls operate at the network layer of the OSI model. They filter traffic based purely on IP addresses and ports. And that allows them to manage and sift through large volumes of data quickly and efficiently by checking where traffic is coming from and where it’s headed.
On the other hand, layer 7 firewalls function at the application layer. As discussed, they provide a deeper level of scrutiny by examining the contents within the data packets themselves instead of just the source or destination. So layer 7 firewalls can identify and mitigate threats that exploit specific application vulnerabilities, like SQL injections or cross-site scripting attacks.
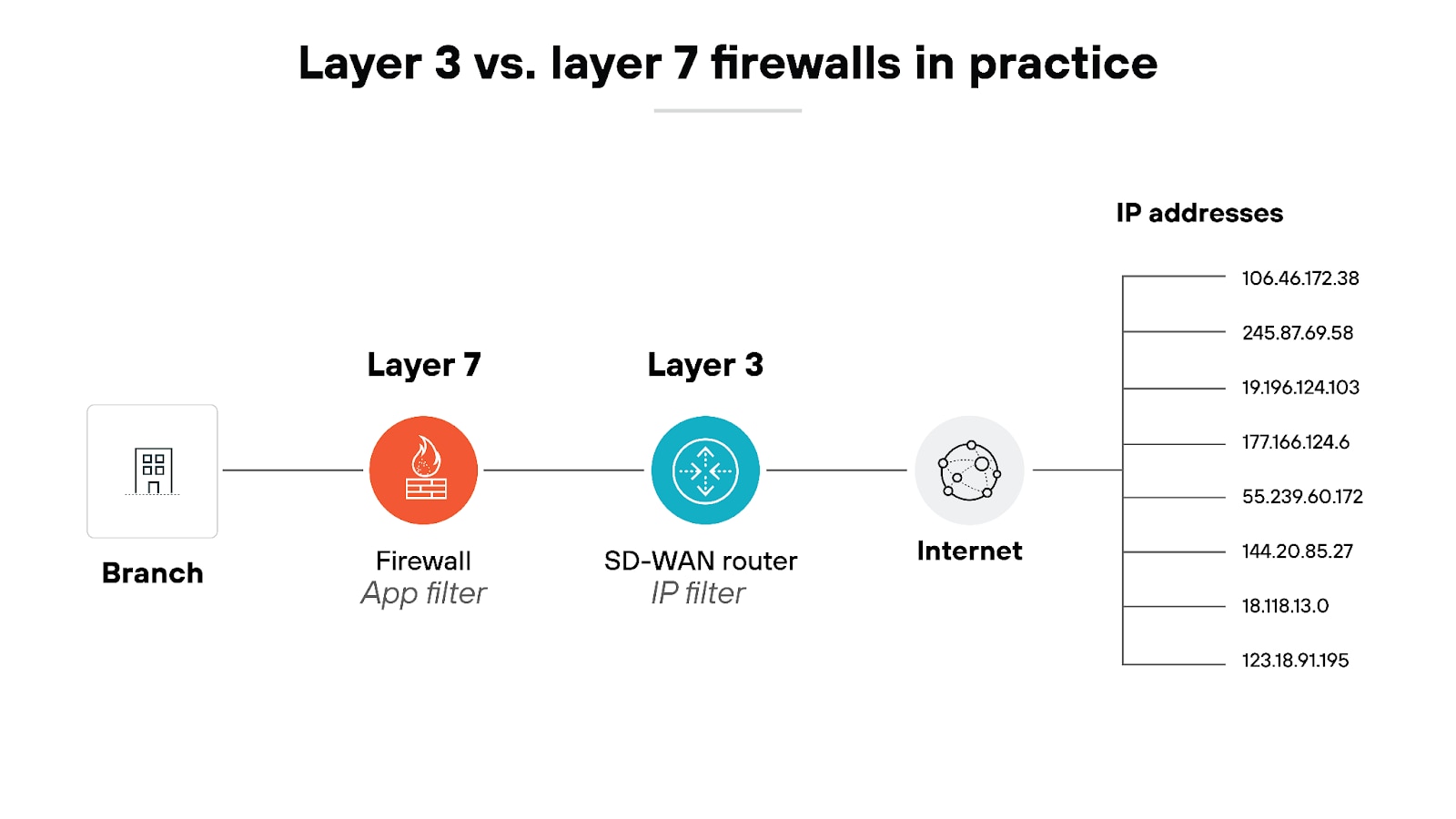
The primary differences between layer 3 and layer 7 firewalls are their approaches and depth of inspection.
Layer 3 firewalls are faster and can handle more traffic. Filtering is simpler and more straightforward because it’s just based on addresses and ports. Which makes them suitable for situations where speed and volume are critical.
Conversely:
Layer 7 firewalls—while slower and more resource-intensive because of the detailed analysis of packet contents—offer enhanced security by targeting more sophisticated threats that require inspection beyond IP and port filtering.
Although they target different aspects of traffic, layer 3 and layer 7 firewalls are in no way mutually exclusive. Both firewalls very often complement each other in network security architecture.
Ultimately:
- Layer 3 firewalls effectively block general threats and reduce the volume of traffic that needs more detailed inspection.
- Layer 7 firewalls provide critical defenses against complex, application-targeted attacks that might otherwise bypass simpler filtering methods.
- Together, they form a comprehensive shield, each layer addressing specific security needs that contribute to the overall protection of the network.
Further reading:
How to choose between layer 3 firewalls and layer 7 firewalls
In reality, the choice between a layer 3 and a layer 7 firewall won’t present itself because each does different things.
Both layer 3 and layer 7 firewalls have distinct functionalities. Which means, again, that they’re not mutually exclusive but complementary.
In environments where high throughput and basic access control are sufficient, a layer 3 firewall may be adequate on its own.
However:
For protecting sensitive applications or where security needs are more complex, a layer 7 firewall provides the necessary depth of inspection and enhanced security measures.
In practice, a complete approach to network security involves using both types of firewalls (at the very least).
A layer 3 firewall can be deployed at the network edge to handle high volumes of traffic and perform basic filtering. Traffic that passes the initial layer of security can then be directed to a layer 7 firewall for detailed inspection of data at the application level.
A layered defense strategy is the modern norm. This approach offers the best of both worlds: efficient processing and comprehensive security thanks to the strengths of each firewall where they’re most effective.
Which adds up to a flexible, adaptive security posture that can address a wide range of threats.
Further reading: What Does a Firewall Do? | How Firewalls Work