SASE vs. ZTE: What Is the Difference?
The difference between SASE and ZTE is that ZTE emphasizes Zero Trust security principles across the network. However, SASE and ZTE refer to the same architecture model for managing and securing network access. ZTE is simply a refinement of the SASE model.
SASE and ZTE share common overall principles and goals such as network functionality consolidation and cloud-delivered security. They differ slightly in emphasis and approach.
What Is SASE?
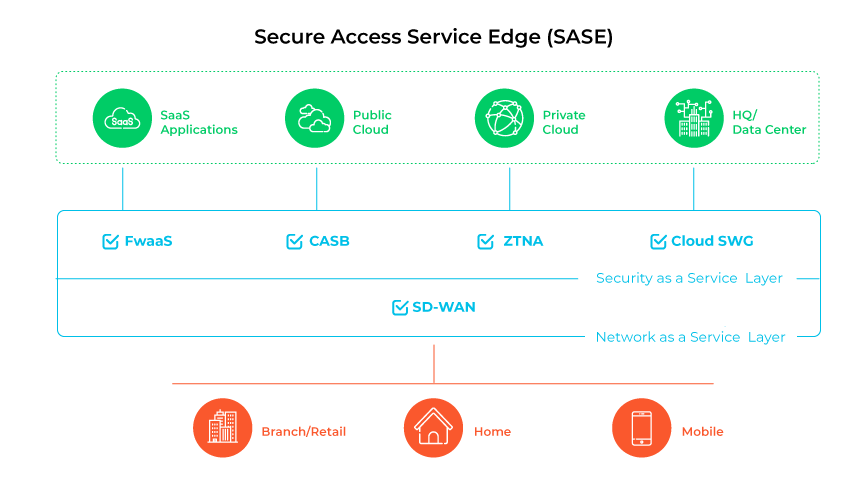
The secure access service edge (SASE) framework is a comprehensive cloud-based security solution that combines security and networking services, including software-defined wide area networking (SD-WAN), secure web gateway (SWG), cloud access security broker (CASB), firewall as a service (FWaaS), and Zero Trust network access (ZTNA) into one cohesive platform. SASE orchestrates various elements to safeguard network connections, manage an extensive array of security functions, improve management workflows, and provide a versatile network architecture that adapts to changing business requirements.
SASE architecture caters to the evolving demands for secure connectivity in modern enterprise environments. It extends the traditional network perimeter to include all access points, aiming to facilitate secure and efficient cloud interactions for remote users, regardless of location. SASE operates by routing network traffic through a cloud-based service platform that consolidates multiple security and network functions. By positioning these services at the network edge, closer to the user and device connection points, it minimizes latency, boosts network performance, and enhances the user experience. This approach ensures consistent application of security policies across the enterprise, centralizes control, and makes network and security management easier.
What Is ZTE?
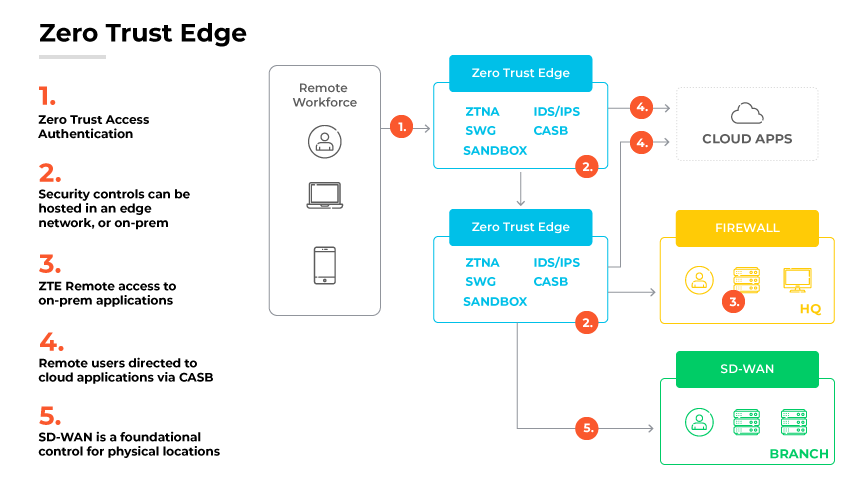
Zero Trust Edge (ZTE) is an architectural approach that integrates network infrastructure with rigorous security measures under the Zero Trust framework. Zero Trust is a security concept that requires authentication, authorization, and continuous validation for all users (whether inside or outside the network), before granting or keeping access to applications and sensitive data. ZTE adoption is growing because of its vital role in securely connecting an increasing array of devices and users to an organization's resources. It also aids in protecting remote work environments and lessening the dependency on traditional virtual private network (VPN) solutions.
ZTE creates a more secure point of access to the internet. This is particularly relevant in the context of digital acceleration, where hybrid work models and extensive application accessibility broadens potential points of vulnerability. ZTE design is responsive to modern threats, establishing a new security boundary that integrates protection and network functionality, which grants specific application access tied to the continuous validation of user credentials and device security status. This system plays a key role in fortifying an organization's digital landscape against an array of cyber threats.
It is important to note that transitioning to a ZTE network can involve significant challenges. Operational technology (OT) and internet of things (IoT) devices may complicate the transition because of the need to modernize or replace legacy networking equipment. Organizations might have to enhance infrastructure to accommodate ZTE's demands, especially where existing capacity is insufficient. Adopting ZTE can also disrupt traditional network security methods, requiring careful planning and a shift to cloud-based points of presence (POPS) for effective implementation. ZTE lacks the capacity to replace high-volume network and security services that provide access to data centers.
What Are the Differences Between SASE and ZTE?
| ZTE vs. SASE: What Are the Differences? | ||
|---|---|---|
| SASE | ZTE | |
| Architectural Focus | Integrates networking and security into a single cloud service. | Focuses on security verification using Zero Trust principles. |
| Implementation and Deployment | Cloud-native, with a suite of security capabilities. | May include on-premises components along with cloud solutions. |
| Access and Trust Model | Secures access to resources with a focus on user experience. | Applies Zero Trust rigorously, not trusting users or devices by default. |
| Network Design Orientation | Supports remote environments via cloud gateways. | Ensures continuous monitoring and validation of network transactions. |
| Adaptation to Evolving Threats | Quickly adjusts to changing business requirements with cloud capabilities. | Adapts by consistently applying strict authentication and security policies. |
Architectural Focus
SASE integrates various networking and security functions into a single, cloud-based service. It fuses SD-WAN and security services to deliver secure access to resources. In contrast, ZTE emphasizes Zero Trust principles, focusing on the authentication and constant validation of network interactions. The distinction lies in SASE’s combination of networking and security into one service versus ZTE’s integration of security verification at every network layer. Both include effective security measures.
Implementation and Deployment
SASE deployment usually involves embracing a broad suite of security capabilities provided via cloud services to streamline network access and management. On the other hand, ZTE requires implementing security measures that may include on-premises components, depending on bandwidth needs and the location of users. ZTE can require local infrastructure to complement the cloud or edge-hosted security stack, whereas SASE is entirely cloud-native.
Access and Trust Model
SASE operates on the principle of providing secure access to an organization's resources, with a strong emphasis on user experience and simplifying management through cloud-based delivery. ZTE, by its nature, applies Zero Trust principles vigorously, ensuring no user or device is trusted by default. Zero Trust edge applies meticulous authentication and validation. It considers every network transaction as potentially risky.
Network Design Orientation
SASE design supports dispersed and remote environments by connecting users to the nearest cloud gateway, optimizing both security and network performance. ZTE design depends on the needs of the organization, with implementation typically following one of three paths: cloud-based service, extension of a wide area network (WAN), or homegrown. In all cases, ZTE adopts a more restrictive posture by default.
Adaptation to Evolving Threats
While both frameworks are responses to modern security challenges, they adapt differently. SASE is adaptive by virtue of its cloud-native capabilities that can quickly scale or adjust in response to changing business requirements. In contrast, ZTE's approach focuses on a rigorous and continuous validation process, adapting by consistently applying strict authentication and security policies to every network interaction—not by scaling.
What Are the Similarities Between SASE and ZTE?
| SASE vs. ZTE: What Are the Similarities? | |
|---|---|
|
Integration of Networking and Security
Both SASE and ZTE integrate networking and security into streamlined services. They address the need for organizations to support a remote and hybrid workforce while maintaining secure access to applications and resources. This integration is fundamental in both frameworks, representing a shift away from traditional network security models toward a more unified approach that is inherently more adaptable to the distributed nature of modern workforces.
Cloud-Delivered Architecture
SASE and ZTE are both designed as similar, cloud-driven architectures. The cloud-centric designs allow for the consolidation of various functions and capabilities, enhancing operational speed and management simplicity. This approach enables organizations to extend consistent security policies across dispersed geographical locations, optimizing network performance, and user experience.
Support for Digital Transformation
Both frameworks support the evolving digital transformation of organizations. As businesses increasingly move toward SaaS and other cloud-based services, SASE and ZTE offer solutions that accommodate these changes by providing secure and efficient network connectivity. Their designs account for the expanded attack surface that comes with digital transformation, focused on improving security in hybrid workplace models.
Centralized Management
SASE and ZTE facilitate centralized management of network and security services. This centralized approach provides visibility and control over the enterprise's hybrid network environments, allowing for better monitoring, reporting, and response to incidents. Both frameworks aim to reduce the complexity and administrative overhead associated with managing disparate security and network solutions.
What Is the Difference Between SASE and Zero Trust?
Zero Trust is a cybersecurity policy that mandates validation for all access attempts in a network. In contrast, SASE combines an array of security services, including the principles of Zero Trust, within a cloud infrastructure. Zero Trust is based on the premise that no user or system should be automatically trusted, either inside or outside the network, and must be verified rigorously before access is permitted.
SASE, on the other hand, goes further than just controlling access. It includes various security features provided at the network's edge, aiming to safeguard access and enhance performance. SASE solutions accommodate the fluid, spread-out nature of organizations by incorporating Zero Trust into a wider, methodical strategy for network security and administration.