-
- Cloud Detection and Response (CDR) Explained
- How CDR Works
- Key Features of CDR
- CDR and Other Detection and Response Approaches
- How CDR and XSIAM Work Together
- How CDR Addresses Unique Challenges in Cloud Security
- Key Capabilities of CDR
- How CDR Bridges SOC and Cloud Security
- Challenges of Implementing CDR
- CDR Best Practices
- Cloud Detection and Response FAQs
Table of Contents
-
What Is AppSec?
- AppSec Explained
- The Fundamentals of AppSec
- Building Security into the Development Lifecycle
- Implementing Secure Coding Practices
- Application Security Testing
- Implementing Security in CI/CD Pipelines
- Securing Application Architecture
- Access Control and Authentication
- Monitoring and Incident Response
- Managing AppSec in Production
- Training and Building a Security-First Culture
- AppSec Trends
- AppSec FAQs
-
What Is Sandboxing?
- Sandboxing Explained
- Sandboxing in Email Security
- Endpoint Sandboxing and EDR
- Browser Isolation and Web Sandboxing
- Sandboxing in Cloud-Native Workflows
- Sandbox Evasion and Threat Actor Tradecraft
- Real-World Case Studies in Sandboxing Effectiveness
- Feeding Sandboxed Intelligence into XDR and SOC Pipelines
- Sandboxing FAQs
-
Application Security: A Practitioner’s Guide
- Application Security Explained
- Types of Applications Organizations Need to Secure
- Whose Job Is It – Developers or Security?
- A Pragmatic Guide for Security-Minded Developers
- Types of Application Security Testing
- Application Security Tools and Solutions
- Compliance Is Not Security, But It’s Not Optional Either
- Application Security FAQs
- How to Transition from DevOps to DevSecOps
- Cloud Security Service, Cloud Storage and Cloud Technology
-
How Does VMware NSX Security Work
-
What Is the Software Development Lifecycle (SDLC)?
- Software Development Lifecycle Explained
- Why the SDLC Matters
- Foundational Phases
- Common SDLC Models
- Security and Compliance Integration
- SDLC in Context
- SDLC Challenges
- Choosing or Tailoring an SDLC Model
- SDLC Tooling and Automation
- Version Control and CI/CD Pipelines
- Value-Stream Metrics and Visibility
- Cloud, On-Premises, and Hybrid Considerations
- Best-Practice Guidelines for High-Velocity Delivery
- Next Steps Toward Lifecycle Maturity
- Software Development Lifecycle FAQs
-
What Is SDLC Security?
- SDLC Security Overview
- Security Across the Classic SDLC Phases
- Common Vulnerabilities and Attack Vectors in the SDLC
- Foundational Secure-SDLC Practices
- Tooling and Automation Layers
- Frameworks and Standards for Secure SDLC
- DevSecOps Integration
- Metrics and Continuous Improvement
- Advancements in Software Supply Chain Defense
- Roadmap to Secure-SDLC Maturity
- SDLC Security FAQs
What Is Cloud Detection and Response (CDR)?
5 min. read
Table of Contents
Cloud detection and response (CDR), also referred to as cloud-native detection and response (CNDR) and cloud threat detection and response (CTDR), provides threat prevention, detection, and response capabilities tailored for multicloud environments. It employs agentless technology to offer protection, real-time visibility, and identification of threats, vulnerabilities, misconfigurations, and compliance gaps without interfering with operations.
Cloud Detection and Response (CDR) Explained
Cloud detection and response is a security capability that provides real-time visibility, threat detection, and automated response across cloud environments. It helps security teams identify suspicious activity, correlate data from multiple cloud sources, and take immediate action to mitigate threats. CDR integrates with other security tools like cloud-native application protection platforms (CNAPP) and security information and event management (SIEM) systems to deliver a centralized, proactive defense against cloud threats.
Enhanced Context and Data Correlation
A unified platform that integrates CDR with CNAPP and SIEM tools centralizes data from multiple sources—cloud telemetry, workload activity, identity data, and runtime security events. With this holistic approach teams can:
- Correlate Threat Signals: By aggregating data from multiple planes (data, identity, network, and control), the platform reduces alert noise and reveals multi-stage attack patterns.
- Prioritize Threats Effectively: CNAPP tools can identify toxic combinations of risks (e.g., misconfigurations paired with exposed credentials), while CDR uses this context to prioritize threats based on exploitability.
Streamlined Investigation and Response
By consolidating CDR with CNAPP and SIEM capabilities, the platform provides a consistent investigation interface, eliminating the need for tool-switching:
- Unified Investigation Dashboard: Security teams can trace threats across the entire cloud stack without pivoting between platforms.
- Automated Playbooks: SIEM integration ensures automated responses (e.g., isolating compromised containers or disabling compromised IAM roles) based on insights from both CNAPP and CDR data.
Operational Efficiency and Speed
A centralized security command center powered by CDR, CNAPP, and SIEM integration reduces operational overhead by:
- Reducing Tool Sprawl: A single pane of glass view reduces the number of platforms security teams need to manage, improving collaboration across CloudSec, AppSec, and SecOps.
- Accelerating Incident Response: Automated correlation between cloud misconfigurations and runtime threats shortens mean time to detect (MTTD) and respond (MTTR).
Business and Security Alignment
Integration via CDR also supports broader business goals by:
- Lowering Costs: Consolidation reduces licensing fees, maintenance overhead, and training requirements associated with managing multiple tools.
- Improving Security Posture: Consistent enforcement of security policies across code, runtime, and infrastructure enhances resilience against modern threats.
How CDR Works
Cloud detection and response joins high-fidelity telemetry with real-time analytics and automated containment to enhances an organization’s ability to defend against cyber attacks. The system ingests control-plane, data-plane, and workload signals, builds incident-grade context on a unified object model, and enforces remediation through cloud-native controls and platform APIs.
Telemetry Ingestion
CDR collects cloud control-plane activity from provider audit logs such as AWS CloudTrail, Azure Activity Logs, and Google Cloud Audit Logs. Many teams now centralize this stream in queryable security lakes, including CloudTrail Lake, to accelerate investigations and enable retention with integrity guarantees.
Network-level data flows in from VPC and VNet flow logs and load balancer access logs, while service logs cover gateways, serverless, and managed databases. Workload-level runtime signals arrive through kernel-native instrumentation such as eBPF, which captures process, file, network, and syscall activity across containers and VMs with low overhead. Kubernetes audit events and API-server logs round out cluster context. Recent eBPF advances expanded policy enforcement and pre-execution visibility, which strengthens real-time detection without the performance tax of traditional agents.
Identity telemetry anchors the model — IdP sign-ins, token minting and exchange, role assumptions, conditional-access outcomes, and privilege changes. SaaS and office-suite events matter as well, given adversaries’ lateral moves across mail and storage, for example. Public guidance such as CISA’s SCuBA baselines and BOD 25-01 pushed organizations to standardize collection and configuration hygiene across M365 and Google Workspace, improving signal quality for CDR.
Normalization, Enrichment, and Graphing
Pipelines normalize provider-specific events into common schemas, attach cloud resource metadata, and resolve principals to owners and business units. The solution builds a time-ordered graph linking identities, tokens, resources, and network paths, so a single incident object represents the end-to-end exposure and all related activity. That graph powers lineage, blast-radius estimation, and what-changed analysis during response.
Detection Methods
Modern CDR aligns analytic coverage to the MITRE ATT&CK Cloud matrices for IaaS, SaaS, office suites, and identity providers. Engines combine rules, temporal correlation, baselining, and sequence models to surface techniques such as credential abuse, role chaining, cloud persistence, control-plane modification, lateral movement via serverless, container breakout attempts, and exfiltration over sanctioned services. Mapping detections to ATT&CK clarifies residual gaps and drives roadmap priorities.
Behavioral analytics turn raw signals into adversary-centric stories. Examples include detecting anomalous STS role use after conditional-access failure, IMDS probing followed by credentialed API calls, or kubectl exec against a workload with no prior operator access. Runtime sensors validate exploit reachability and confirm impact by observing process trees, socket connections, and policy violations at the kernel boundary. Independent references note the growing use of eBPF to achieve this depth with minimal performance impact.
Case Construction and Triage
The system assembles detections, telemetry, and enrichment into a single, incident-grade case object. Ownership, last change, effective permissions, and business criticality attach to the same assets and principals that appear in the graph. Analysts pivot within the case, not across tools, and view ATT&CK-aligned timelines, related alerts, and recommended next actions.
Automated Response
CDR orchestrates cloud-native controls to contain threats with precision:
- Identity containment: Revoke refresh tokens, disable risky sessions, reduce role trust, and rotate keys across affected accounts.
- Endpoint and workload isolation: Quarantine a VM, cordon and drain a node, evict or kill a pod, and block process families observed in the attack path.
- Network interdiction: Insert narrowly scoped security-group or NSG rules, update firewall policies, and sever egress used for exfiltration.
- Control-plane rollback: Revert unauthorized policy or configuration changes through versioned templates and organizational policies.
- Data protection: Lock buckets, disable public access, and enforce service-side encryption where the case indicates exfiltration risk.
Provider audit lakes and queryable logs speed scoping and verification during automation, an area where recent CloudTrail Lake enhancements have shortened investigative loops.
Continuous Verification and Coverage Management
Coverage dashboards track ATT&CK technique detection across cloud, identity, and SaaS surfaces to expose blind spots and measure improvement. Program guidance from CSA and CISA emphasizes structured logging baselines to raise signal quality, which directly improves CDR efficacy.
Operating Model
Effective CDR runs as a joint program between CloudSec, identity, and the SOC. Cloud teams own guardrails and resource metadata quality. The SOC owns detection logic, triage, and automation policy. Product security validates exploitability and feeds hardening changes back into infrastructure as code. The shared goal is fewer, higher-confidence cases, faster containment, and durable posture fixes anchored to the same incident object and graph. Aligning to cloud-specific ATT&CK matrices keeps the program threat-led and measurable.
Key Features of CDR
- Flexible Deployment: Supports agent-based and agentless options, allowing seamless integration into cloud environments.
- Centralized Dashboard: Offers a unified view of threats, vulnerabilities, and compliance status across all cloud assets.
- Real-Time Monitoring: Continuously tracks workloads, configurations, and activities to detect threats such as malware, ransomware, and data breaches.
- Automated Response: Provides actionable insights and automation to enable quick containment of threats.
- Risk Prioritization: Assesses and ranks risks based on their potential impact, helping security teams focus on critical issues.

CDR and Other Detection and Response Approaches
Traditional detection and response solutions are primarily designed for on-premises environments, which need more scalability and flexibility for today's cloud landscapes.
Unlike these legacy systems, CDR is purpose-built for cloud environments. It harnesses its expansive resources to provide real-time threat detection and automated response capabilities that meet the dynamic needs of modern cloud-based infrastructures.
CDR vs. Endpoint Detection and Response (EDR)
CDR and EDR serve different but complementary roles in cybersecurity. CDR is focused on detecting and responding to threats within cloud environments, while EDR is centered on protecting individual endpoints. Together, they provide a holistic security approach by covering cloud-specific and endpoint-level threats, ensuring comprehensive protection across an organization’s entire digital infrastructure.
CDR vs. Security Information and Event Management (SIEM)
CDR and SIEM complement each other by combining their strengths to provide a comprehensive security solution:
- Integrated Data: CDR feeds cloud-specific telemetry and insights into SIEM, enriching its dataset and improving its overall threat detection and correlation capabilities.
- Coordinated Response: CDR’s automated responses to cloud-specific threats can trigger alerts or actions within SIEM, enabling a unified, coordinated response to security incidents across all environments.
- Unified Visibility: Together, cloud detection and response and SIEM provide a complete view of the organization’s security posture, ensuring consistent monitoring, detection, and response across cloud, hybrid, and on-premises infrastructures.
CDR vs. Network Detection and Response (NDR)
CDR and NDR work together by offering specialized threat detection and response at both the cloud and network levels, ensuring a more resilient and comprehensive security strategy across the organization's digital ecosystem.
CDR identifies threats specific to the cloud, while NDR detects threats moving across networks, providing comprehensive coverage of cloud and network layers. Insights from CDR can inform NDR about cloud-specific threats and vice versa, enabling coordinated, faster responses to incidents across the entire environment.
CDR vs. Cloud Workload Protection Platform (CWPP)
CWPP and CDR complement each other by addressing different aspects of cloud security, providing a more comprehensive protection strategy. CWPP ensures that the workloads are secure, while CDR monitors the broader cloud environment for any threats or anomalies, providing end-to-end protection.
CDR specializes in detecting and responding to threats across the entire cloud infrastructure. It continuously monitors services, applications, and networks for malicious activity, misconfigurations, or breaches. It identifies potential threats and provides alerts or automated responses to help mitigate cyber attacks like account takeovers or malware infections.
In contrast, CWPP protects specific cloud workloads, such as applications, containers, virtual machines, and serverless functions. It offers a range of security measures, including vulnerability management, runtime protection, and compliance management, to secure workloads from development through runtime. Together, CDR and CWPP offer a comprehensive approach to cloud security.
How CDR and XSIAM Work Together
CDR complements extended security intelligence and automation management (XSIAM) by enhancing its capabilities to provide threat prevention, detection, and response for cloud environments.
Specifically, CDR Complements XSIAM in the following ways:
- Runtime Threat Prevention: CDR starts with a prevention-first approach, blocking threat activity in real-time on cloud workloads.
- Enhanced Detection: CDR adds cloud-specific threat detection to XSIAM, processing events in the cloud with AI to surface anomalies.
- Automated Response: CDR extends XSIAM response actions to the cloud, enabling faster, automated incident responses tailored for cloud environments.
- Unified Data Integration: CDR feeds cloud-native telemetry into XSIAM, enriching its data for better threat correlation and detection across all platforms.
- Streamlined Operations: With CDR’s insights, XSIAM can prioritize alerts and reduce false positives, optimizing security team efficiency.
- Comprehensive Security Posture: Together, CDR and XSIAM create a unified approach to security, protecting against both cloud-specific threats and the rest of the attack surface.
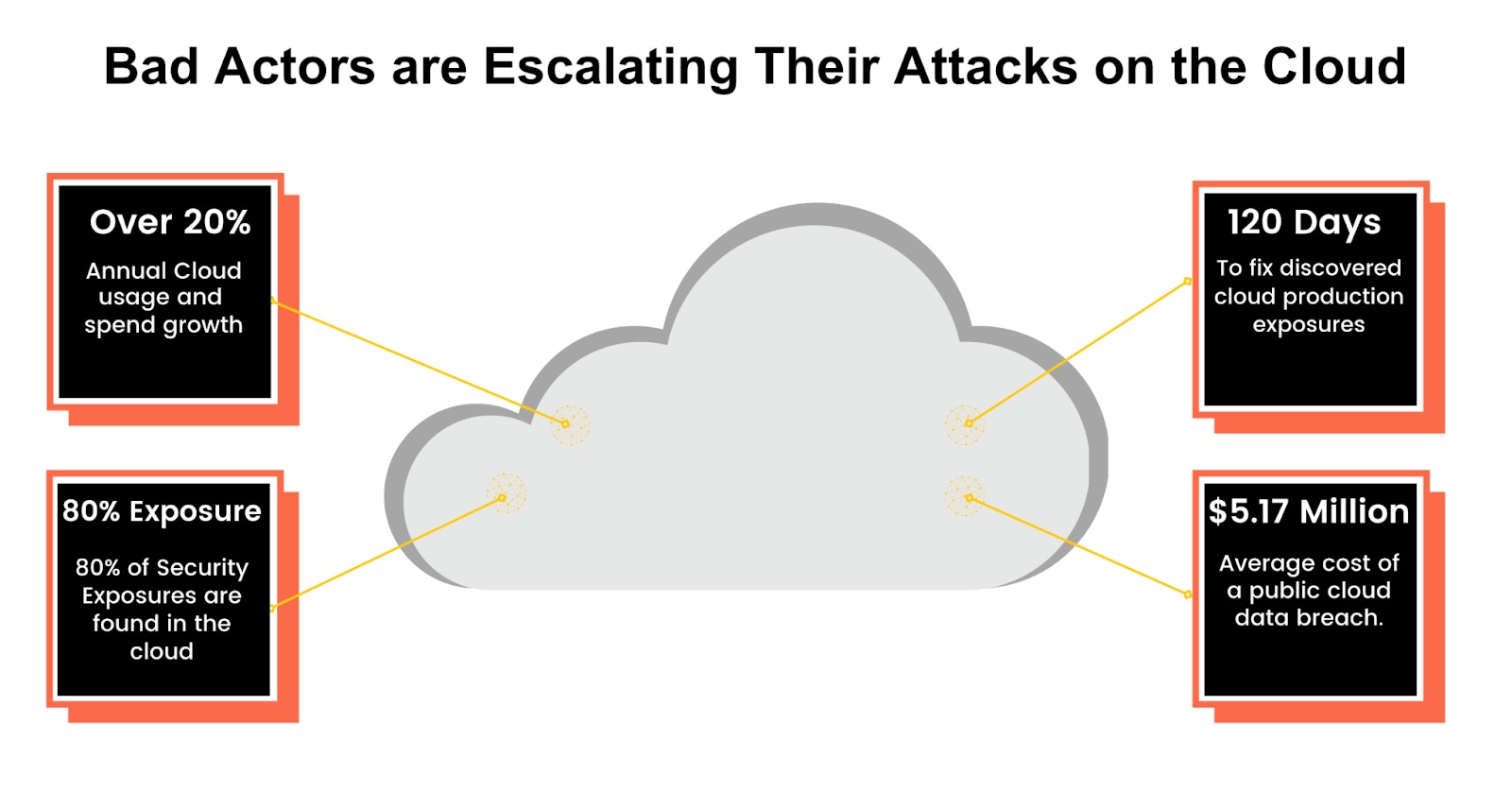
How CDR Addresses Unique Challenges in Cloud Security
As organizations migrate to the cloud, they encounter new security challenges that traditional tools need help managing. Cloud environments' dynamic and distributed nature introduces complexities such as data overload, rapid infrastructure changes, and fragmented security postures.
1. Data Overload: Cloud environments generate vast volumes of data that can overwhelm traditional security tools. CDR uses advanced analytics and machine learning to efficiently sift through this data, identifying anomalies and potential threats in real time.
2. Dynamic Infrastructure: Cloud infrastructure changes continuously, with resources scaling up or down rapidly, making it challenging to enforce consistent security policies. CDR solutions adapt dynamically to these changes, providing continuous protection regardless of the cloud's evolving state.
3. Fragmented Security: Integrating multiple cloud services often leads to fragmented security controls and visibility gaps. CDR unifies these elements, providing a cohesive security framework across various platforms to ensure comprehensive coverage.
How CDR Addresses Today’s Cloud Threats
CDR has become a critical tool in modern cybersecurity, explicitly designed to handle the unique threats cloud environments pose as cybercriminals employ sophisticated tactics like advanced malware, phishing, ransomware, and lateral movement attacks. CDR leverages cloud-native capabilities to detect and respond to these threats swiftly.
CDR enhances threat detection and streamlines incident response by providing centralized visibility across multicloud and hybrid environments. It integrates machine learning and artificial intelligence to automatically analyze large data volumes, identify risks, and initiate responses faster than ever before.
Proactive Cloud Security
CDR represents a proactive approach to cloud security, ensuring that even the most complex threats are quickly identified and neutralized. This approach reinforces the resilience of cloud-based operations, helping cybersecurity teams stay ahead in the ongoing battle against sophisticated attackers.
Key Capabilities of CDR
CDR systems offer essential capabilities to safeguard cloud environments.
Continuous Security Monitoring
Real-time analytics scrutinize cloud environments, detecting anomalies instantly. Security teams gain actionable insights through continuous data collection and analysis. This persistent vigilance ensures rapid identification of vulnerabilities and maintains up-to-date analysis against sophisticated cyberattacks.
Threat Intelligence and Analytics
CDR systems analyze large datasets and enhance threat detection through pattern recognition and anomaly detection. Machine learning models predict potential threats, while real-time analytics and historical data correlation enable proactive defense measures.
Real-Time Threat Detection
Sophisticated algorithms analyze vast data streams, pinpointing suspicious behavior instantly. Machine learning models adapt to evolving threats, enhancing detection accuracy. Security teams receive immediate alerts, allowing rapid intervention. This proactive stance mitigates risks before they escalate, safeguarding sensitive data and maintaining operational integrity.
Automated Response and Remediation
Systems autonomously identify and alert teams to threats, dramatically reducing response times. AI-driven tools execute predefined remediation protocols, ensuring consistent and swift action. This automation minimizes human error and frees up security teams to focus on complex issues. Continuous learning from each incident refines future responses and security resilience.
Integration with Existing Tools
CDR systems integrate seamlessly with existing security tools, such as SIEM platforms, consolidating alerts and streamlining incident response. This integration allows security teams to manage and mitigate risks efficiently across diverse environments, ensuring a cohesive defense strategy.
Automating Compliance Reporting
A CDR solution automates compliance reporting by continuously monitoring and alerting on security policies, providing real-time visibility into cloud environments, and generating automated reports that align with regulatory requirements.
Continuous Monitoring and Real-Time Alerts
CDR solutions continuously monitor cloud activities, including data access, file transfers, and user behavior, to detect any policy violations or suspicious activities that could impact compliance. When a potential breach or noncompliance event is detected, the system can trigger real-time alerts, allowing for immediate response and remediation.
Automated Policy Enforcement
CDR solutions automatically enforce security policies and controls aligned with compliance standards, such as GDPR, HIPAA, PCI DSS, or others. By setting predefined rules, the system ensures that only authorized actions are performed and automatically blocks or mitigates unauthorized activities, reducing the risk of compliance violations.
Compliance Reporting and Audit Readiness
CDR solutions provide automated compliance reporting features that generate detailed reports on security events, incidents, and remediation actions. These reports are designed to meet the specific requirements of regulatory bodies, making it easier for businesses to demonstrate compliance during audits. The solution can also maintain an audit trail of all cloud activities, simplifying the documentation process for compliance purposes.
Data Protection and Privacy Management
CDR solutions help automate data protection by identifying and categorizing sensitive data, ensuring it is appropriately encrypted, stored, and accessed according to regulatory requirements. They can also detect and respond to data breaches or leaks, ensuring that personal and sensitive data remains secure and compliant with privacy laws.
Integration with Compliance Frameworks
Many CDR solutions integrate directly with industry-standard compliance frameworks and tools, automating the mapping of security controls to compliance requirements. This integration allows organizations to automatically align their cloud security posture with regulatory obligations, reducing manual effort and the risk of human error.
Detecting Threats Pre-Exfiltration
Organizations can proactively detect threats and reduce vulnerabilities by combining advanced threat detection techniques and comprehensive security measures.
Machine learning algorithms and real-time analytics monitor network traffic and user behaviors to identify anomalies and deviations from established baselines, flagging suspicious activities before data exfiltration occurs.
Threat intelligence platforms correlate these anomalies with known threat patterns, while behavioral analysis tools detect unusual access attempts and unauthorized data movements, enabling early threat interception and preventing data breaches.
Reducing the Attack Surface
To minimize potential vulnerabilities, do the following:
- Implement strict access controls and network segmentation to limit attackers' entry points.
- Isolate critical assets to reduce risk.
- Use automated patch management to address security gaps quickly.
- Regularly audit and remove unused services and accounts to eliminate unnecessary risks.
Organizations can effectively reduce how attackers exploit weaknesses by continuously monitoring and improving these measures.
How CDR Bridges SOC and Cloud Security
CDR improves security by unifying security operations centers (SOC) and cloud security (CloudSec) through centralized visibility, streamlined collaboration, and automated threat response. Here's how:
Centralized Data and Visibility
CDR consolidates data from both SOC and CloudSec sources, providing a unified view of cloud-native application activity, security events, and infrastructure behavior. This eliminates the blind spots caused by tool fragmentation and enables both teams to work from the same security dataset.
- SOC Benefit: Access to cloud-specific telemetry alongside enterprise data.
- CloudSec Benefit: Context on real-time threats alongside cloud misconfigurations and vulnerabilities.
Consistent Threat Detection and Prioritization
By correlating signals from the cloud control plane, workload activity, and identity sources, CDR ensures both SOC and CloudSec teams prioritize the most critical threats.
- SOC Benefit: Faster identification of high-risk cloud threats without manual data correlation.
- CloudSec Benefit: Clear visibility into how cloud misconfigurations may be exploited during active attacks.
Automated and Coordinated Incident Response
CDR enables automated response actions based on prebuilt playbooks, reducing manual effort and accelerating containment across both cloud and on-premises environments.
- SOC Benefit: Automated responses for cloud-based threats integrated into broader enterprise-wide security playbooks.
- CloudSec Benefit: Immediate containment of cloud-native threats, such as disabling compromised IAM roles or quarantining compromised containers.
Collaboration and Knowledge Sharing
CDR breaks down operational silos by allowing both teams to share insights and collaborate using a single security platform.
- SOC Benefit: Cloud threat intelligence enhances on-premises security strategies.
- CloudSec Benefit: SOC expertise in threat hunting improves cloud-native investigations.
Operational Efficiency
By unifying SOC and CloudSec workflows under a single platform, CDR reduces tool sprawl, simplifies alert management, and minimizes the need for specialized skill sets for cloud-specific threats.
- SOC Benefit: Less time spent switching between tools and manually investigating cloud threats.
- CloudSec Benefit: Enhanced visibility without managing separate cloud security platforms.
Challenges of Implementing CDR
Implementing CDR presents a dual-edged sword of opportunities and obstacles. Organizations gain enhanced security visibility and faster response times but face challenges like alert fatigue and integration complexities. Balancing these aspects requires strategic planning and resource allocation. Effective CDR deployment can transform security operations, but it demands continuous improvement and adaptation to evolving threats.
Integrating CDR tools with existing security infrastructure can be complex and require considerable customization. The automated nature of CDR can sometimes result in false positives, overwhelming security teams, and alert fatigue. Additionally, implementing and maintaining CDR solutions can be expensive, which might be a barrier for smaller organizations.
CDR tools can also be resource-intensive, potentially impacting the performance of the cloud environment. Effective use of these solutions demands skilled personnel who understand cloud environments and advanced security practices. Lastly, CDR's continuous monitoring and data collection might raise privacy concerns, especially in industries with strict data protection regulations.
Reducing Alert Fatigue
Security teams often drown in a sea of false positives, which dilutes their focus on genuine threats.
Implementing adaptive filtering mechanisms helps prioritize alerts based on contextual relevance and historical data. Automated correlation of events across multiple cloud environments further refines alert accuracy. Regularly updating detection rules and incorporating threat intelligence feeds ensure that alerts remain relevant and actionable.
By streamlining alert management, organizations can enhance their response efficiency, allowing security professionals to concentrate on critical incidents without being overwhelmed by noise.
Enhancing Visibility
Organizations can implement real-time monitoring tools to gain comprehensive insights into their cloud environments:
- By leveraging advanced analytics, they can identify patterns and anomalies that may signal potential threats. Integrating cloud-native security solutions ensures seamless visibility across diverse platforms.
- Employing user and entity behavior analytics (UEBA) helps detect unusual activities and proactively mitigate risks.
Organizations can swiftly identify and respond to emerging threats by maintaining a clear view of cloud activities, bolstering their overall security posture.
How CDR Improves Response Times
CDR improves response times by enabling real-time detection, automating responses, providing centralized visibility, prioritizing threats, and integrating with existing security tools. These features help security teams respond to threats faster and more effectively.
Real-Time Threat Detection
CDR continuously monitors cloud environments and identifies threats, minimizing the delay between threat occurrence and detection. This immediacy allows security teams to act faster, reducing the exposure window.
Automated Responses
CDR solutions automate threat response actions, such as isolating compromised resources or blocking malicious activity, significantly reducing the need for manual intervention. Automated responses are executed instantly, which speeds up containment and mitigation.
Centralized Visibility
CDR provides a unified view of security incidents across all cloud assets, eliminating the time-consuming process of gathering and correlating data from multiple sources. This centralized visibility enables quicker assessment and decision-making.
Contextual Risk Prioritization
CDR leverages advanced analytics to assess and prioritize threats based on their severity and potential impact, helping security teams focus on the most critical issues first. This prioritization streamlines response efforts and reduces overall response time.
Seamless Integration with Security Tools
CDR integrates with other security tools and platforms, such as XSOAR (security orchestration, automation, and response), to coordinate and accelerate response actions across the entire security stack.
CDR Best Practices
Establishing clear criteria is crucial when considering CDR best practices. Organizations should prioritize CDR solutions that offer comprehensive threat detection, seamless integration with existing security tools, and automated incident response features that can adapt to evolving threats.
CDR deployment strategies must be carefully planned to minimize disruption to existing workflows and maximize the new system's effectiveness. Thorough testing and training are also essential to ensure staff use the new tools proficiently.
Additionally, organizations must be prepared to address common challenges, such as false positives and integration complexities, and have efficient strategies to overcome them. Following these best practices can help organizations strengthen their cloud security posture and respond to threats more swiftly and effectively.
How to Select and Deploy a CDR Solution
Selecting and deploying a CDR solution requires a strategic approach, including the following.
Assess Your Business Needs
Determine your organization’s security objectives by identifying specific security needs, such as threat detection, incident response, and compliance with industry standards. To better understand the cloud environment, map out your cloud architecture, including cloud providers, services, applications, and workloads you must protect.
Evaluate Key Features
Ensure the solution offers the key capabilities mentioned above: real-time threat detection, automated incident response, continuous monitoring and analysis, and integration with existing security tools.
Plan Deployment
Begin by creating a comprehensive deployment strategy. This strategy should involve a phased approach, starting with a small-scale pilot test to identify potential issues and make necessary configuration adjustments.
Additionally, define and configure security policies aligning with its risk tolerance and regulatory requirements. Ensuring seamless integration with the existing IT infrastructure and security ecosystem is also crucial to the deployment's success.
Test and Optimize
- Conduct Security Testing: Perform penetration testing, red teaming, or simulated attacks to ensure the solution effectively detects and responds to threats.
- Monitor and Optimize: Monitor the solution’s performance and tune its settings based on detected threats and business needs.
Training and Awareness
Provide dedicated training sessions for security teams to ensure they understand how to use the solution effectively. Conduct awareness campaigns to educate all employees on recognizing and reporting potential security incidents, fostering a culture of vigilance and proactive response across the organization.
Review and Adapt
- Regularly Review Performance: Continuously review the CDR solution’s performance, staying updated on new features or updates from the vendor.
- Adapt to Emerging Threats: Adapt your deployment and configuration to address new threats and changes in your cloud environment.
By following these steps, you can effectively select and deploy a cloud detection and response solution tailored to your business needs, helping to secure your cloud assets and data against evolving threats.
Cloud Detection and Response FAQs
CDR solutions often integrate with security tools such as SIEM (Security Information and Event Management), EDR (Endpoint Detection and Response), and firewalls. This integration enables a unified security posture by correlating data from various sources, enhancing overall threat detection and providing comprehensive incident response capabilities.
Key features to look for in a CDR solution include:
- Real-time threat detection and alerting
- Advanced analytics and machine learning capabilities
- Automated incident response and remediation
- Integration with other security tools and platforms
- Comprehensive visibility into cloud environments
- Threat intelligence and context enrichment
- Compliance and audit reporting
How does CDR help in compliance and regulatory requirements?
CDR solutions assist in meeting compliance and regulatory requirements by providing continuous monitoring, detailed audit logs, and incident response capabilities. These solutions help organizations adhere to GDPR, HIPAA, and PCI-DSS standards by ensuring that cloud environments are secure and that any security incidents are promptly detected and mitigated.
Some challenges in implementing CDR include:
- Complexity of multi-cloud environments
- Integration with existing security infrastructure
- Managing and analyzing large volumes of cloud data
- Ensuring real-time detection and response
- Addressing cloud-specific threats and vulnerabilities
- Training and skill requirements for security personnel
Yes, CDR solutions are capable of detecting insider threats in the cloud. By monitoring user activities, access patterns, and data usage, CDR tools can identify unusual or suspicious behavior that may indicate an insider threat. Advanced analytics and behavior analysis help detect deviations from normal user behavior, enabling timely identification and response to potential insider threats.