-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
Dark Web Leak Sites: Key Insights for Security Decision Makers
- Dark Web Leak Sites Explained
- Evolving Extortion Tactics
- The Role of Leak Sites in Ransomware Double Extortion
- Critical Risks Exposed by Data Leak Sites
- Anatomy of a Dark Web Leak Site
- Proactive Defense: How Organizations Can Mitigate Dark Web Leaks
- Dark Web Leak Site FAQs
- What to Do If Your Organization Appears on a Dark Web Leak Site
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What Is a Cyber Attack?
Cyber attacks are deliberate, malicious actions designed to breach digital systems. Targeting vulnerabilities across networks, software, identities, and supply chains, cyber attacks often chain multiple techniques to evade detection. The modern threat landscape evolves daily, shaped by automation, monetization, and geopolitical friction.
Threat Overview: Cyber Attacks
Cyber attacks are orchestrated operations that exploit weaknesses across digital systems to achieve an adversary’s goal. Attackers pursue disruption and financial gain for strategic leverage or ideological messaging.
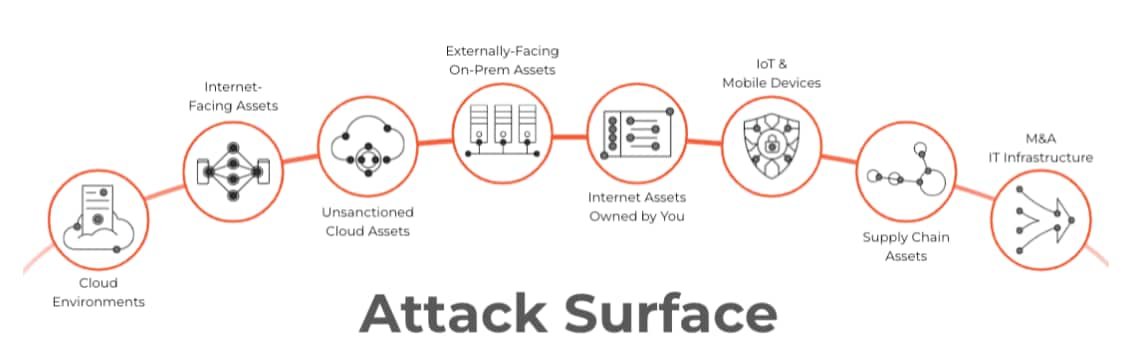
Figure 1: Cloud-based and on-premises internet-facing assets making up the attack surface
The modern attack surface includes everything with an IP address, API endpoint, token store, or misconfigured permission. Adversaries don’t need to bypass firewalls when they can exploit SaaS integrations, tamper with CI/CD pipelines, or steal machine identities to impersonate trusted automation. Then, having gained entry, they weaponize native tools and legitimate access and often evade detection by avoiding traditional malware signatures.
Attack sophistication of course varies. Some groups rely on brute automation and recycled credentials. Others invest in multistage campaigns that blend phishing, protocol abuse, and supply-chain tampering. Most operate with tooling comparable to enterprise-grade platforms.
Cyber attacks have matured from one-off intrusions into continuous campaigns. Organizations no longer face isolated breaches but endure persistent probing from financially and politically motivated actors. Preventing these attacks requires visibility and identity-aware enforcement, in addition to an exploit-aware defense posture and a coordinated response architecture that accounts for known and novel tactics.
Cyber Attack Types at a Glance
| Malware-Based Cyberattacks | Network-Based Cyberattacks |
|---|---|
|
|
| Web Application Cyberattacks | Password Cyberattacks |
|---|---|
|
|
| Social Engineering Cyberattacks | Other Cyberattacks |
|---|---|
|
|
Global Cyber Attack Trends
Threat actors now operate on a scale and cadence that challenge every layer of traditional defense. Security teams at Palo Alto Networks detect 1.5 million novel attacks each day — threats that didn’t exist the day before. Across its platforms, 8.6 billion attack attempts are blocked daily. But frequency alone doesn’t explain the shift. Attackers have adopted faster, more adaptive methods that evade detection and weaponize what defenders trust most — legitimate credentials, native tools, and misconfigured access.
Payloads no longer dominate. Nearly a third of intrusions in 2024 began with valid credentials. Infostealers infected 4.3 million devices and harvested 330 million usernames and passwords alongside 17.3 billion cookies. These session tokens gave adversaries seamless access to cloud platforms, messaging apps, and internal portals. Many bypassed endpoint protections entirely.
Attack chains span multiple domains. In 70% of incidents, the path to compromise crossed three or more surfaces, mostly combining endpoint access, cloud lateral movement, identity manipulation, and human targeting. Single-layer defenses have lost relevance in this environment. Security programs must now detect cross-domain tactics and block progression early.
AI has amplified the attacker’s advantage. Generative models now write phishing emails that mirror internal tone and automate malware development with variant obfuscation built in. The early 2025 spike in infostealer phishing campaigns — up 180% from the previous year — underscores how automation has replaced manual effort. Gartner projects that by 2027, 17% of all attacks will use AI-driven techniques and, to up the ante, that AI agents will reduce the time it takes to exploit account exposures by 50%.
Global telemetry recorded 6.06 billion malware attacks in 2023. Though its behavior has changed, malware remains prolific. Traditional signatures no longer suffice. Many strains now load filelessly, blend into memory processes, and use evasive delay tactics to outpace time-based detection.
Ransomware has become a near-universal threat. In 2023, 72.7% of organizations experienced at least one ransomware incident. U.S. critical infrastructure attacks rose 9% during 2024. Unlike earlier forms, today’s ransomware often incorporates double extortion, lateral discovery, and embedded remote access, turning containment into a race against irreversible damage.
Global Economic Impact
As defenders fall behind, the cost of successful cyber attacks continues to climb. Cybercrime inflicted $9.22 trillion in global damages in 2024. Forecasts diverge on pace but agree on direction, projecting $13.82 trillion to $23.84 trillion in annual losses by 2027. The growth curve now outpaces global GDP. Security programs — most of them — weren’t built for this level of bombardment.
Related Article: Unit 42 Threat Frontier Report: Prepare for Emerging AI Risks
Cyber Attack Taxonomy
Modern attacks follow an opportunistic logic: exploit whatever provides the least resistance with the highest return. To prepare an effective defense, organizations must understand how adversaries approach intrusion.
Social Engineering
Social engineering remains the lowest-cost entry point for attackers. Adversaries bypass technical defenses by exploiting human behavior. Phishing kits now include proxy-based token capture, rendering MFA ineffective unless session binding and token rotation policies are in place. Quishing (QR-based phishing) and callback phishing (voice-based pretexting) have also surged, particularly in support desk impersonation.
Web and API Abuse
Attackers increasingly target web apps and exposed APIs as primary vectors. OWASP Top 10 flaws still dominate entry points, particularly broken access controls and insecure deserialization. Meanwhile, attackers also exploit API misrouting, unvalidated inputs, excessive data exposure, and privilege overreach in GraphQL and REST interfaces. Automated discovery tools crawl for undocumented endpoints then probe for logic flaws behind authentication gates.
Network Intrusion
Network-layer intrusions now begin with credential abuse more often than exploit chaining. When exploits are used, attackers favor unpatched edge devices with a reliance on pre-auth RCEs. Inside, they then use protocol-level attacks (i.e., SMB relay, ARP spoofing, Kerberos ticket manipulation) to extend access. Lateral movement often follows predictable enterprise architecture, where flat VLANs and shared identity domains accelerate compromise.
Endpoint Compromise
Endpoints still represent the most visible target, but modern compromises rarely hinge on dropping detectable malware. Attackers run code in memory or abuse native scripting frameworks. Some subvert trusted apps with DLL sideloading. Browser session hijacking has outpaced ransomware as a precursor to major enterprise breaches. Without kernel-level visibility, most EDRs fail to detect execution paths that don’t trigger file-based telemetry.
Cloud Misconfiguration Exploitation
Public S3 buckets, unrestricted managed identities, open Kubernetes dashboards — attackers now treat cloud misconfiguration as a standing opportunity. CSPM tools surface risks but often drown teams in low-priority alerts. Cyberattackers move faster, scanning the internet for just-deployed services with default settings or leaked tokens.
Supply-Chain Manipulation
Software supply chains offer high-leverage targets. Attackers compromise upstream dependencies, package registries, or CI/CD automation to poison trusted artifacts. Dependency confusion, typo-squatting, and malicious update injection have affected widely used components in NPM, PyPI, and Docker Hub. Inside the build process, attackers often tamper with credentials stored in environment variables or override workflows through GitHub Actions or GitLab CI config files.
Attack Objectives
Attackers rarely compromise environments without purpose. Each intrusion maps to one or more objectives, shaping the techniques they choose and the urgency they exhibit.
- Data theft includes bulk exfiltration of intellectual property, authentication secrets, customer records, or surveillance targets. Stealer malware, cloud sync abuse, and exfiltration over HTTPS or DNS tunneling support this goal.
- Financial gain drives ransomware, business email compromise (BEC), cryptomining, and affiliate-based extortion. Attackers monitor internal finance workflows to intercept or redirect payments and often target payroll, vendor systems, or ERP platforms.
- Service disruption often appears in DDoS attacks, destructive wiper malware, or infrastructure tampering. State-aligned groups use this tactic to degrade public trust or disrupt critical industries during geopolitical conflict.
- Espionage motivates persistent access and lateral movement into sensitive departments. Threat actors use traffic shaping and dormant implants to avoid detection while siphoning policy memos, negotiation strategy, or defense R&D.
- Destructive sabotage emerges in attacks designed to degrade systems permanently. Wipers like AcidRain, WhisperGate, or CaddyWiper erase firmware, overwrite MBRs, or brick embedded devices. In critical infrastructure, attackers aim for physical-world disruption.
Framework Alignment
The MITRE ATT&CK Framework v17.1 remains the most comprehensive and structured catalog of adversary behavior. It categorizes tactics, as well as the techniques and sub-techniques that support each tactic:
|
|
Mapping observed activity to ATT&CK enables structured triage, threat hunting, and detection engineering. For example, use of PowerShell for credential dumping (T1003.001), exploitation of public-facing applications (T1190), or abuse of valid cloud accounts (T1078.004) should inform both prevention and response controls.
MITRE ATT&CK also helps teams align red-teaming exercises, SOC detection coverage, and policy enforcement with real-world attacker behavior. Its enterprise, mobile, cloud, and ICS matrices continue to expand, reflecting shifts in the threat landscape with each quarterly update.
Threat-Actor Landscape
No security strategy holds weight without a grounded understanding of who’s behind the attacks. Threat actors differ widely in capability, intent, targeting logic, and risk tolerance. Organizations that fail to distinguish between these groups often misallocate defenses, overspending on noise while leaving mission-critical assets exposed.
State-Sponsored Groups
Nation-state actors operate with long-term plans, dedicated infrastructure, and often zero operational cost sensitivity. Backed by intelligence services or military units, these groups conduct espionage, pre-positioning, and sabotage campaigns aligned with national interests. China's APT41, Russia’s APT28, North Korea’s Lazarus Group, and Iran’s OilRig each maintain distinct TTPs but increasingly share toolchains, as well as C2 infrastructure and laundering methods.
Their campaigns often target telecommunications, energy, defense contractors, political organizations, and semiconductors. Initial access usually involves spear phishing, zero-day exploitation, or credential theft. State groups then invest in stealth and achieve dwell times that can span months. Lateral movement prioritizes identity domain controllers and collaboration platforms or SaaS environments known to hold policy or supply-chain blueprints.
Organized Cybercrime
Cybercriminal groups operate as professionalized businesses. Some run affiliate-based ransomware operations while others specialize in credential harvesting or financial fraud. Most operate out of regions with limited extradition risk and often collaborate through brokered access markets and escrow-enforced forums.
Initial access brokers sell footholds for a price that reflects industry, geography, and privilege level. Having gained access, actors use post-exploitation toolkits like Cobalt Strike, Sliver, and custom loaders. Their goal is quick monetization through extortion or theft. Many criminal groups now blend operational tempo and technical rigor indistinguishable from advanced persistent threats.
Hacktivists
Hacktivist activity follows ideological lines. Though groups like Anonymous lack the technical maturity of state or criminal actors, they do achieve impact through distributed denial-of-service attacks, website defacements, and data leaks, to say nothing of social amplification. Their operations spike during geopolitical conflict, particularly high-profile legislation affecting civil liberties.
Recent years have seen hacktivism fragment into region-specific collectives. Pro-Russian or pro-Ukrainian hacktivists, for example, have disrupted critical infrastructure, leaked sensitive information, and flooded media platforms with disinformation. While sometimes dismissed, their access to leaked toolsets and stolen credentials tend to make their actions difficult to ignore.
Insider Threats
Internal actors present a category of threat both technically unique and organizationally disruptive. Insiders bypass perimeter defenses and often possess legitimate access, deep operational knowledge, and motive. Insider threats can act maliciously or unknowingly, and their motivations range from financial desperation to retaliation or coercion.
Most insider incidents don't originate with system administrators or privileged engineers. Instead, sales teams, contractors, and support staff frequently expose sensitive data through unauthorized transfers, session sharing, or bypassing controls to meet deadlines. Detection depends on behavioral baselines and session monitoring.
Motivations and Behaviors
Attack behavior correlates with what the actor stands to gain. Mapping motivations allows defenders to anticipate attacker dwell time, target, and tolerance for detection.
Financial Incentives
Financial incentives drive most intrusions. Ransomware-as-a-service (RaaS), BEC, and credential harvesting dominate the criminal economy. Financially motivated actors pursue rapid monetization with increasingly corporate structure (i.e., affiliates, QA, support, revenue sharing models). Many exploit legal gray areas in crypto payment processing, bulletproof hosting, and laundering services.
Strategic Intelligence
Strategic intelligence motivates state groups seeking geopolitical leverage. Targets include policy advisors, defense contractors, scientific research institutes, and public infrastructure providers. These actors persist, often avoiding detection for months to exfiltrate sensitive material or embed in firmware or administrative layers.
Ideological Goals
Ideological goals incite hacktivists and extremist-aligned groups. Their targets usually reflect public symbols such as government portals and corporations viewed as unethical. Operations succeed less on technical merit than on amplification, timed disruptions, and reputational harm.
Grievances
Personal grievances drive some insiders and fringe attackers. Layoffs, perceived discrimination, or rejected promotions frequently precede sabotage, data theft, or exposure of sensitive communications. While small in scope, these attacks can lead to disproportionate damage, particularly in regulated sectors.
Understanding the threat-actor landscape is requisite. Without clarity on who your adversaries are and what they want, prevention devolves into blind mitigation.
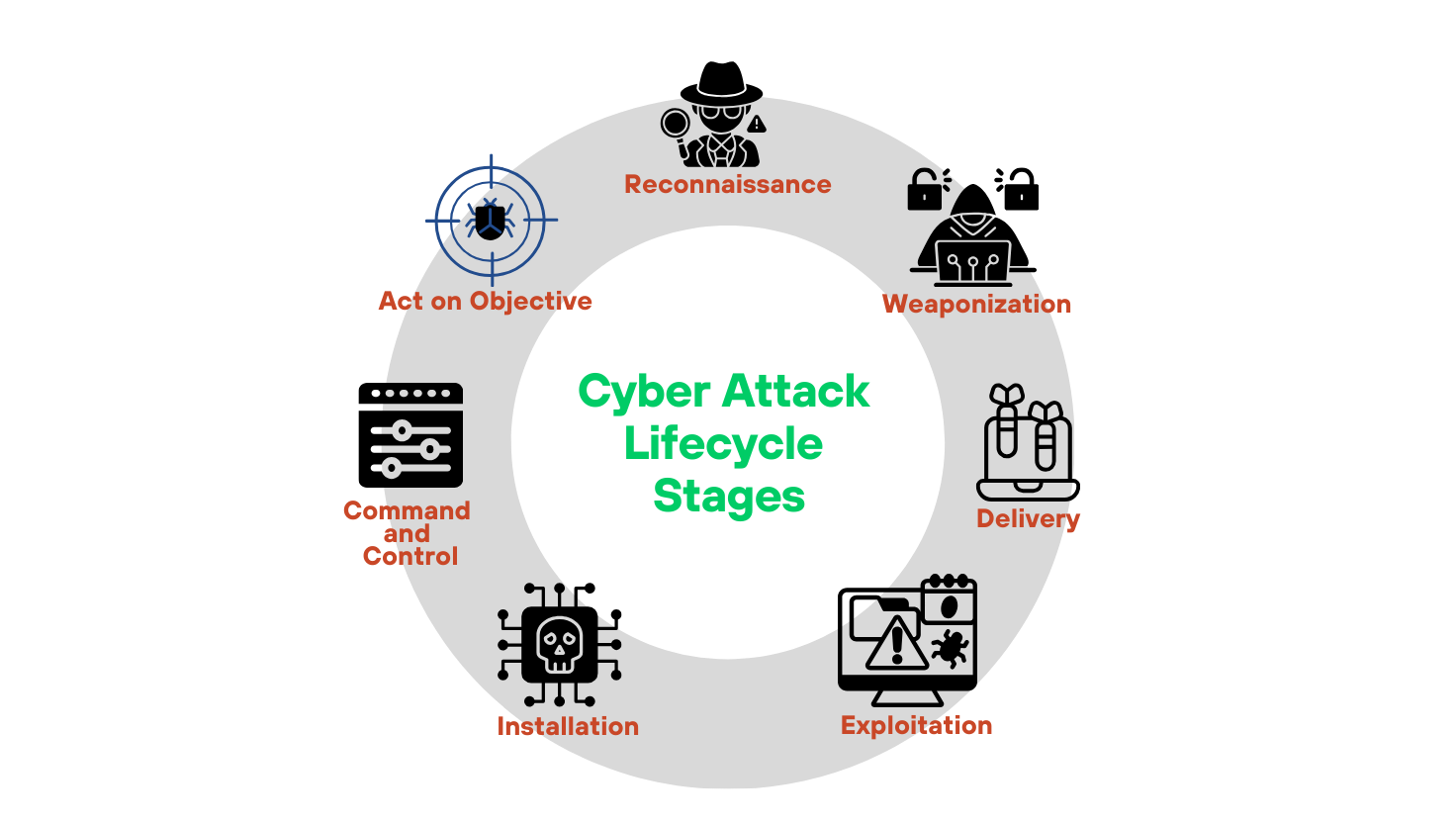
Figure 2: The cyber attack lifecycle
Attack Lifecycle and Methodologies
Adversaries don’t compromise environments in a single motion. They progress through defined stages, each enabling the next. Understanding the structure of an attack enables security teams to insert friction, breaking chains midstream and spotting indicators prior to impact.
Reconnaissance
Attackers begin with information collection. Domain records, employee LinkedIn profiles, exposed GitHub repositories, and cloud asset metadata often reveal internal architecture, naming conventions, and identity schemes.
Open-source intelligence (OSINT) tools like Maltego, SpiderFoot, and Recon-ng aggregate this data at scale. Automated scrapers extract credential reuse patterns from breach databases. Adversaries map VPN endpoints, subdomains, and application surfaces before engaging.
Target profiling narrows the aperture. Attackers prioritize targets based on privilege exposure, external misconfigurations, and the presence of valuable credentials or data processing functions.
Weaponization
Once a target profile is built, adversaries craft the payload. Off-the-shelf exploit kits include loaders, obfuscators, and prebuilt modules for browser, document, and memory-based delivery. Builders support encryption, sandbox evasion, and multivector deployment.
Malware customization ensures payloads avoid signature-based detection. Tools like Shellter, Veil, and custom C2 droppers support polymorphism, encryption layering, and stage-separated delivery. In higher-skill groups, payloads match system architecture, endpoint security posture, and operational cadence.
Delivery
Phishing remains the dominant delivery method. Embedded links, weaponized attachments, fake MFA prompts, and QR codes lure targets into executing scripts or disclosing credentials. Advanced phishing proxies intercept tokens in real time and pass MFA checks using session forwarding.
Smishing (SMS phishing) and callback phishing campaigns increase credibility by triggering live interaction. VoIP spoofing and fake support lines remain common in initial compromise chains.
Drive-by downloads exploit weak browser configurations or malicious advertising infrastructure. Exploit kits inspect the user agent and deliver platform-specific payloads only after meeting exploitation prerequisites. Some use zero-click exploits delivered through image parsing or font rendering vulnerabilities.
Exploitation
Credential abuse outpaces software vulnerabilities in initial exploitation. Stolen tokens and weakly protected API keys allow direct access without triggering IDS signatures. Cloud environments suffer from default configurations where possession of a valid identity bypasses perimeter controls.
Zero-day exploitation targets unpatched or undisclosed vulnerabilities. While rare, zero-days often become operational within days of discovery, especially when disclosed under partial embargo. Attackers favor remote code execution flaws in edge devices, authentication bypass in SaaS platforms, and sandbox escapes in browser engines.
Installation
With exploitation success, attackers deploy implants to retain access. Remote access trojans (RATs) install silently and connect to external command servers over encrypted tunnels. Many operate under the guise of legitimate system processes or abuse signed binaries to evade detection.
In containerized environments, attackers often seek escape. Misconfigured runtime permissions or insecure container images allow traversal to the host, elevation of privileges, or compromise of orchestration platforms. Attackers inject malicious sidecars, override kubelet behavior, or pivot via lax secrets management.
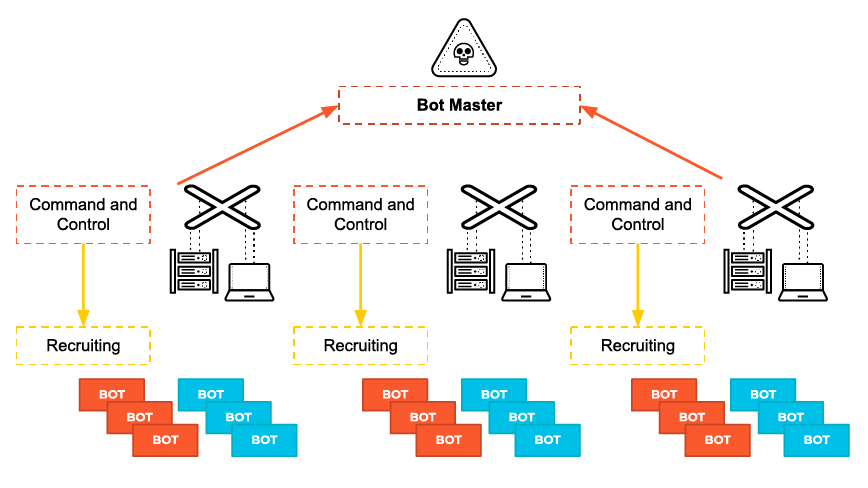
Figure 3: C2 servers used by adversaries to recruit and control BOT devices, forming a network of compromised machines.
Command and Control
After establishing presence, attackers set up command and control (C2) channels. DNS tunneling is frequently used due to its ubiquity and lack of inspection. Malicious payloads encode instructions in TXT or A record lookups and exfiltrate data in reverse.
Cloud-hosted C2 infrastructure blends into trusted services. Attackers host payloads and stage commands in Dropbox, GitHub Gists, Google Docs, or pastebins. Traffic to these providers rarely triggers alerts, especially when encrypted and masked through user agents that mimic automated processes.
More advanced groups deploy custom C2 frameworks that support fallback protocols, beaconing intervals, and dynamic configuration changes. Some maintain tiered infrastructure, routing through proxy layers or infected nodes to frustrate attribution.
Actions on Objectives
Data exfiltration occurs through compressed and encrypted blobs sent over HTTPS, WebDAV, or SFTP. In stealth campaigns, attackers may sync directly to cloud storage services or encode exfiltrated content into legitimate application telemetry.
Lateral movement relies on stolen credentials, token impersonation, and remote management tooling already approved in the environment. Common techniques include pass-the-hash, Kerberos ticket forging, and abuse of remote desktop or MDM protocols. In cloud-native contexts, attackers enumerate IAM roles, hijack automation pipelines, or traverse resource boundaries via shared metadata services.
Impact creation varies by motive. Ransomware encrypts systems and data then deletes backups and logs. Wipers overwrite disk headers or firmware to permanently render systems inoperable. In fraud campaigns, attackers reroute financial transactions, alter payroll, or stage BEC events with internal credibility. Political actors leak sensitive documents to influence public discourse or damage reputations.
Technical Deep Dives
Attackers target infrastructure wherever defenders misconfigure controls or fail to apply least privilege. Understanding the current toolkit used against endpoints and networks helps security leaders align investments with adversary behavior.
Endpoint Attacks
Endpoints serve as both initial footholds and lateral transit points. Their exploitation requires no zero-day when adversaries can bypass control with execution chaining, native tooling, or temporary token theft.
Ransomware Evolution
Modern ransomware rarely operates in isolation. Groups follow structured playbooks with stages for data theft, access monetization, and destruction. Double-extortion models dominate. Before encrypting data, attackers exfiltrate terabytes of internal records, contracts, legal memos, and customer data. They then threaten public disclosure, and negotiations begin before the ransom note even lands.
RaaS ecosystems have lowered the technical barrier. Affiliates license payloads, share profits with operators, and receive C2 infrastructure, payment support, and even victim negotiation playbooks. Families like Black Basta, 8Base, and LockBit evolve rapidly, often outpacing static detection signatures.
Access is typically purchased from initial access brokers. Deployment occurs through RDP abuse, compromised VPNs, or macro-laden attachments. Encryption targets both local and mapped drives. Many strains now disable backup processes and tamper with hypervisors to corrupt snapshots.
Fileless Techniques
Fileless malware eliminates the need for persistent files by executing directly in memory. PowerShell, WMI, and .NET are the preferred platforms. Attackers load payloads as reflective DLLs, use LOLBins to stage secondary tools or inject shellcode into trusted processes via process hollowing.
Living-off-the-land binaries (LOLBins) support everything from credential dumping (rundll32, regsvr32) to lateral movement (wmic, mshta). Most endpoint protection platforms allow these by default, making behavioral context the only viable detection strategy. Adversaries chain these binaries with native scripting to remain silent, fast, and difficult to attribute.
Network and Infrastructure Attacks
While identity has become the new perimeter, core network infrastructure remains a prime attack target.
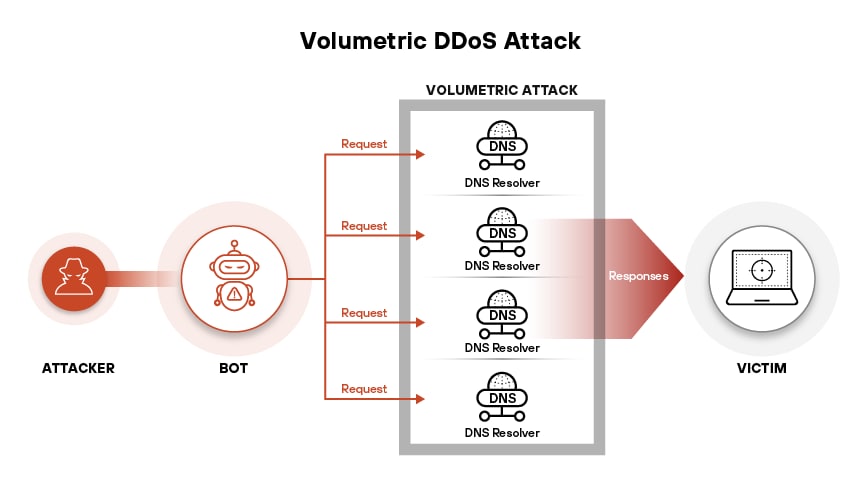
Figure 4: DDoS attacks are categorized into volumetric, protocol, and application layer attacks, based on their target layer and operational mechanisms.
Distributed Denial of Service
DDoS attacks have regained prominence as political and financial tools. Volumetric campaigns frequently exceed 2 Tbps. Attackers use botnets made up of compromised IoT devices, exposed APIs, and rented cloud VMs. Mitigation becomes complex when attacks originate from geographically distributed sources with randomized payloads.
Orchestration platforms like Mirai variants, Condi, and Pandora offer attackers prebuilt dashboards and plugin modules for dynamic targeting. Attackers increasingly shift from network-layer floods to application-layer (Layer 7) techniques, overwhelming specific endpoints with high-request concurrency and low-resource saturation.
Layer 7 floods often target authentication workflows, search functions, or checkout carts — areas with high database interaction. These floods don't require much bandwidth but create latency and failure by exhausting back-end resources.
Man-in-the-Middle
Man-in-the-middle (MitM) attacks exploit unsecured or misconfigured communication channels to intercept or modify traffic. Enterprise Wi-Fi deployments remain particularly vulnerable where certificate pinning or mutual TLS isn’t enforced.
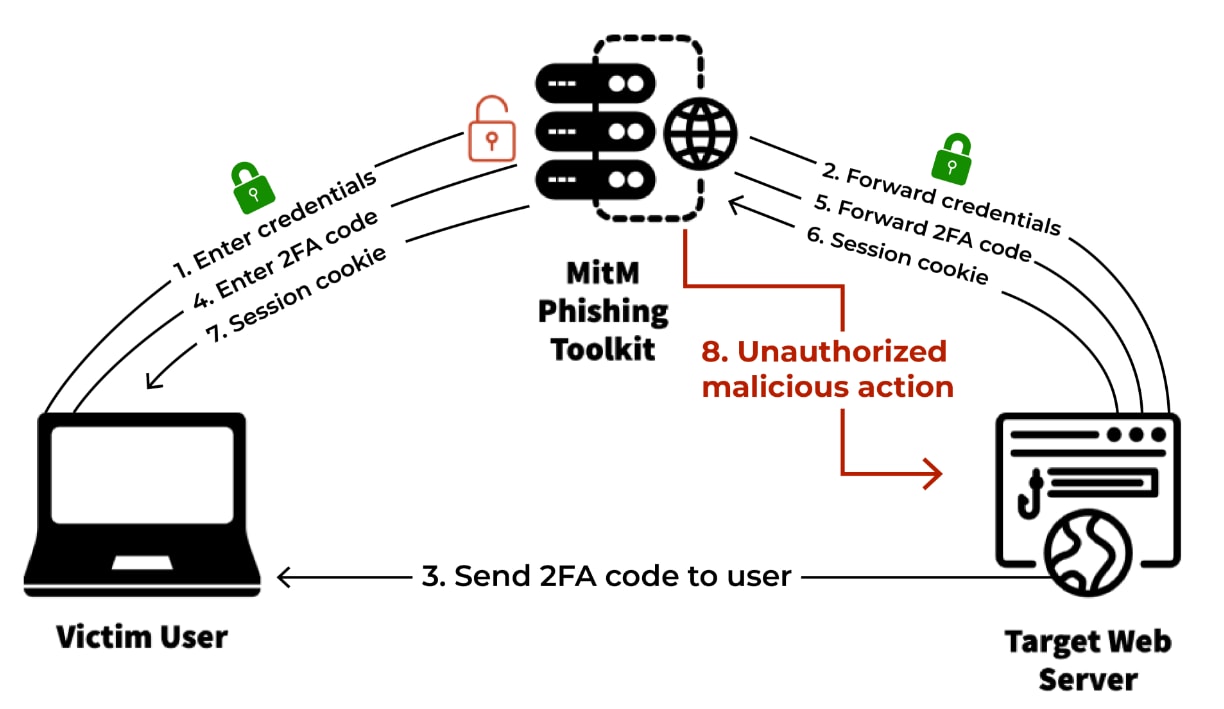
Figure 5: Visual representation of a MitM phishing attack (reproduced from Catching Transparent Phish).
TLS downgrade attacks exploit version fallback behavior. Attackers intercept the handshake, force a deprecated cipher suite, and re-encrypt traffic with keys they control. In cases where TLS is absent, plaintext interception yields credentials, session tokens, or sensitive operational data.
Rogue access points mimic trusted SSIDs and proxy connections through attacker-controlled gateways. Unsuspecting devices autoconnect and route traffic through hostile infrastructure. Tools like WiFi Pumpkin and Bettercap automate the setup of captive portals that phish credentials or inject payloads into traffic streams.
Network-based attacks often evade cloud-native detection systems because the attack vector resides below the application layer. Defense requires not just network segmentation, but protocol-aware monitoring, encrypted transport enforcement, and session anomaly detection at the edge.
Web and Application Attacks
Web applications remain a top-tier attack surface because they often expose business logic and privileged backend systems. Most enterprises lack complete inventories of their web assets, and few perform full-context validation on API inputs or session behavior. Attackers exploit that gap through direct injection, logic tampering, or chained workflows that bypass enforcement.
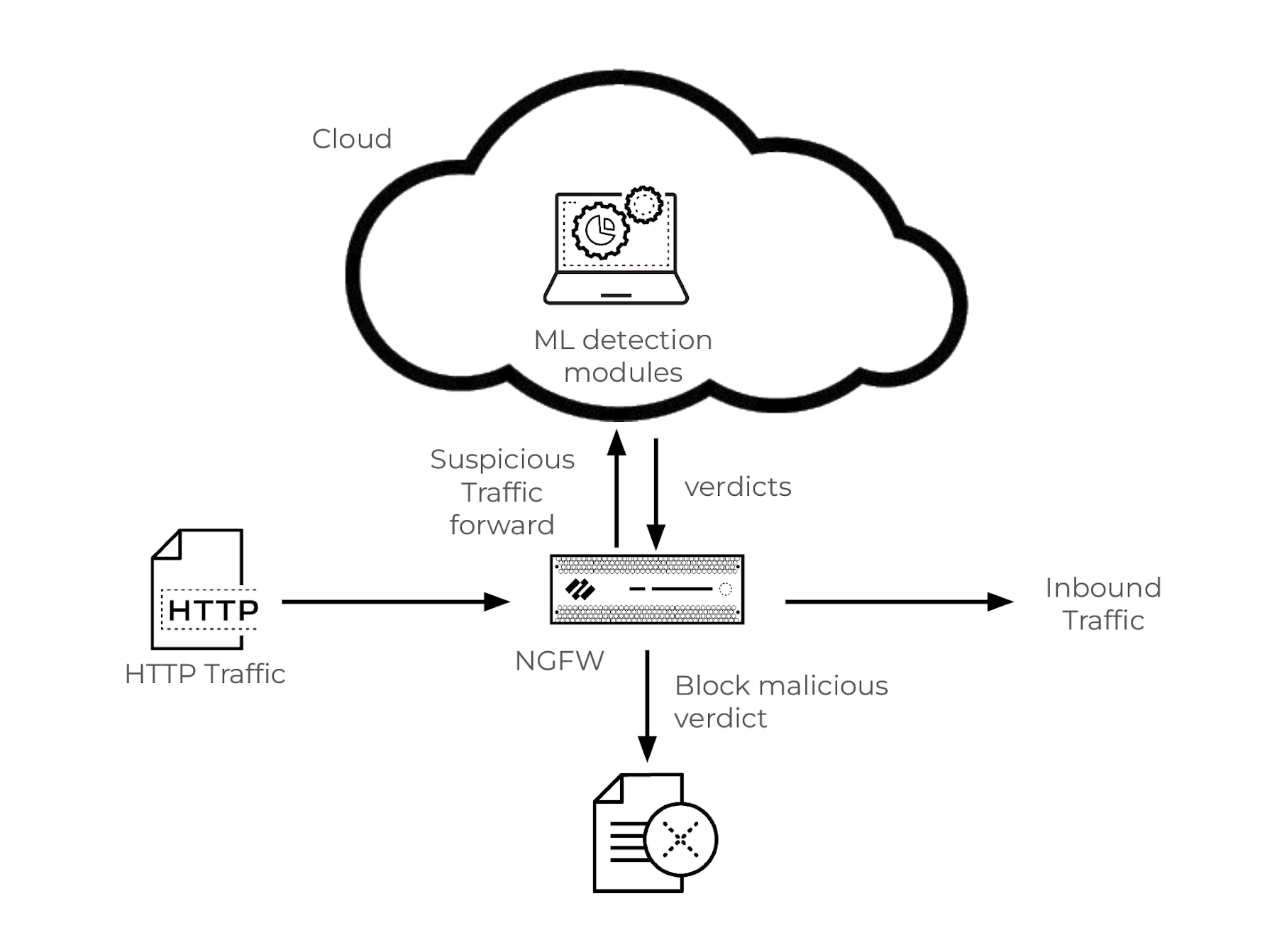
Figure 6: Detection of SQL injection attack within HTTP traffic using an NGFW and cloud-based machine learning for analysis and blocking
Injection Flaws
SQL injection persists despite two decades of awareness. Attackers craft inputs that modify SQL queries executed by backend databases, sometimes extracting entire schemas or modifying records. Blind SQLi techniques remain effective when error messages are suppressed, using timing-based inference to retrieve data one bit at a time. Modern web stacks built on outdated ORM frameworks often fail to sanitize edge-case payloads.
Server-side request forgery (SSRF) forces the application to initiate outbound requests to arbitrary destinations. Attackers exploit SSRF to access internal metadata services, cloud IAM roles, and internal admin endpoints (not externally exposed). In cloud-native environments, SSRF often results in privilege escalation or cross-tenant data exposure. You’ll see this even more if the service misuses trust-based authorization or allows recursive redirects.
Logic Abuse
Broken access control no longer means “missing login page.” It now reflects authorization failures — where access is improperly enforced based on headers or URL parameters. Attackers escalate privileges by tampering with request structures, elevating roles, or reusing API tokens tied to higher-privilege sessions. Cloud misconfigurations often mirror these patterns, where permission boundaries exist in documentation but not in practice.
Business-logic manipulation exploits gaps between what the application allows and what it should prevent. In addition to timing mismatches, attackers exploit race conditions and discount calculation errors. In financial systems, manipulation of currency conversion, invoice generation, or transfer limits leads to direct loss. Flaws like these evade scanners and require adversarial modeling.
Identity and Credential Abuse
Every campaign involving lateral movement, privilege escalation, or impersonation relies on some form of credential access. Identity has become the dominant attack vector across cloud, hybrid, and SaaS ecosystems.
Phishing Variants
Phishing no longer stops at fake login pages. MFA fatigue attacks bombard users with repeated authentication requests until one is approved. Some campaigns use reverse proxies to intercept tokens in real time, allowing immediate reuse without triggering alerts.
Deepfake voice calls have entered operational use. Cybercriminals synthesize a leader’s voice using minutes of leaked audio and place calls requesting credential resets or urgent approvals. Paired with spoofed caller ID and fabricated email threads, these campaigns succeed even in hardened environments.
Credential Stuffing
Credential stuffing attacks exploit reused passwords across services. Automation platforms like OpenBullet, SentryMBA, and custom Python tooling test thousands of username-password combinations per minute against login portals, mobile APIs, and OAuth flows. Modern campaigns inject behavior evasion like randomized headers or device fingerprints to avoid rate limits and detection.
Attackers acquire fresh credentials from infostealers, breach dumps, and token-harvesting malware. Many credentials include session cookies or cloud access keys embedded in browser storage or developer environments. Defenders must assume reuse, rotate secrets aggressively, and detect anomalies. Authentication isn’t a control unless it includes behavior, context, and intent validation.
Cloud-Native Attacks
Most cloud breaches stem from preventable misconfigurations or implicit trust assumptions that collapse under pressure.
Misconfiguration Exploits
Unrestricted storage buckets remain among the most frequently exposed assets in multicloud environments. Public-read access, inherited permissions, and lack of encryption-at-rest controls allow adversaries to enumerate and extract sensitive data with a single unauthenticated request. Attackers automate discovery using tools like Grayhat Warfare, S3Scanner, and CSP-specific APIs.
Overprivileged roles are more damaging than exposed buckets. Many organizations fail to adhere to least privilege, granting service accounts or lambda functions wildcard permissions (i.e., iam:PassRole or s3:*). An attacker that obtains an identity can escalate across the environment through legitimate calls. Expect role chaining, cross-account assumption, and lateral movement.
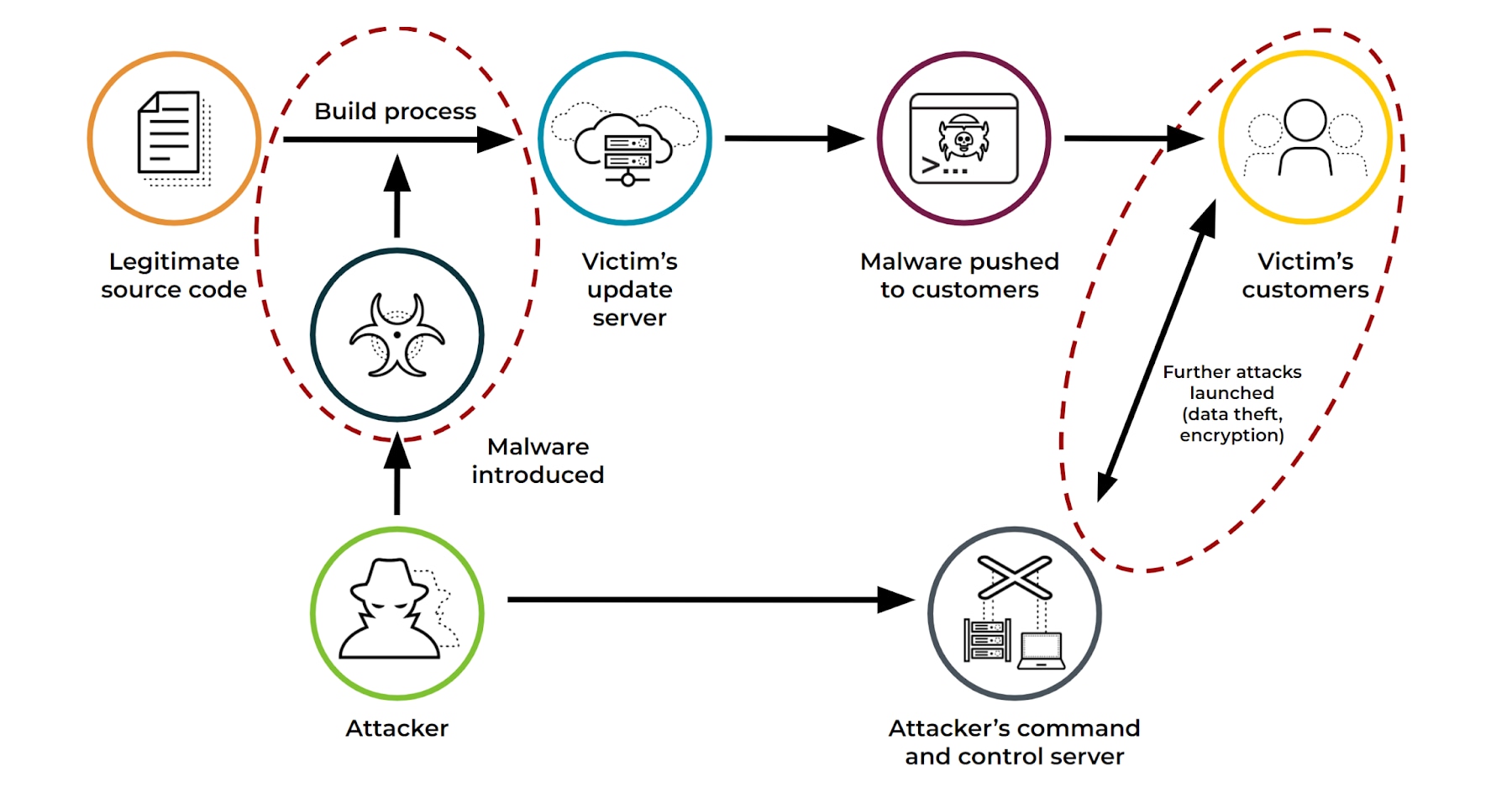
Figure 7: Supply chain attack, from malware injection into source code to the compromise of victim's customers and subsequent malicious activity.
Supply-Chain Exploits
CI/CD pipelines offer attackers a trusted path into production. Compromised build systems allow insertion of malicious code, leakage of environment secrets, or modification of artifacts pushed to production registries. Jenkins, GitHub Actions, GitLab Runners, and self-hosted agents often run with elevated privileges and minimal egress monitoring.
Malicious package insertion exploits trust in third-party dependencies. Attackers trojanize libraries using typo-squatting, repo-jacking, or contributor impersonation and then publish to open repositories. If consumed by downstream projects, the malicious code executes during build or install time, often reaching production without scrutiny.
Related Article: Anatomy of a Cloud Supply Pipeline Attack
Supply-chain compromises bypass runtime defenses by operating within the bounds of signed, verified artifacts. Defenders must enforce provenance, apply reproducible builds, and adopt software bill of materials (SBOM) validation to reduce exposure. Pipeline secrets, especially those granting cloud access, must rotate automatically and remain scoped to the absolute minimum.
OT and IoT Attacks
The convergence of IT and OT has opened industrial environments to threat actors who previously focused on digital systems alone. Meanwhile, IoT ecosystems expand faster than most organizations can secure, often exposing under-tested firmware and unmanaged APIs.
Industrial Control Systems
Protocol manipulation targets deterministic, unauthenticated OT protocols such as Modbus, DNP3, and Profinet. These protocols lack encryption or authentication, allowing attackers to inject commands, read process states, or modify sensor values with physical consequences. In environments with direct PLC access from flat networks, adversaries can manipulate valves, relays, or control loops in real time.
Firmware corruption takes the attack deeper, embedding malicious code at the bootloader or controller level. Through compromised update servers or insecure field-upgrade protocols, attackers implant code that persists across reboots and defies conventional detection. Some variants delay emergency shutdowns or interfere with safety interlocks.
Modern ICS environments often contain bridging hosts — Windows machines with dual connectivity to OT and IT networks. These become pivot points. Without strict segmentation, adversaries can transit from a phishing email to plant-floor control in a few lateral moves.
IoT Botnets
IoT botnets remain a dominant force in large-scale DDoS attacks and credential-stuffing campaigns. Mirai variants dominate due to their source code availability, ease of modification, and default-password scanning logic. If compromised, devices like routers, DVRs, and smart sensors will relay instructions from C2 servers and overwhelm targets with HTTP floods or DNS amplification.
API exploitation provides attackers access to the management plane. Many IoT platforms expose APIs that lack authentication, allow privilege escalation, or return overly verbose metadata. Attackers exploit these endpoints to locate devices, replay telemetry, or deploy firmware downgrades that reintroduce known vulnerabilities.
IoT ecosystems rarely enforce secure onboarding. The same is true for patching and remote management. A device that joins the network, in other words, becomes part of the attack surface unless visibility and policy controls follow immediately. Most don't, and attackers know that.
Cyber Attack Case Studies
Recent attacks reveal how threat actors exploit misaligned controls, flat architectures, or user trust assumptions created structural weaknesses.
MOVEit Mass-Exfiltration Breaches
In May 2023, Clop exploited a zero-day in Progress Software’s MOVEit Transfer product, launching one of the largest data theft campaigns in recent history. The flaw allowed unauthenticated SQL injection, enabling attackers to deploy web shells and exfiltrate files from MOVEit servers en masse.
Within weeks, hundreds of organizations (government agencies, universities, and financial institutions) had their MOVEit servers exploited. Attackers deployed automation to scale access across instances globally. They then followed with extortion threats via leak sites. Victims included Shell, the BBC, and the U.S. Department of Energy.
The data breach exposed a systemic risk in third-party managed file transfer (MFT) services. Many organizations failed to isolate MOVEit servers from sensitive network segments, which gave attackers direct paths to internal systems after compromise.
Related Article: MOVEit Transfer SQL Injection Vulnerabilities: CVE-2023-34362, CVE-2023-35036 and CVE-2023-35708
MGM Resorts Social-Engineering Intrusion
In September 2023, MGM Resorts suffered an attack after threat actors used LinkedIn profiles to identify IT service desk staff and socially engineered access credentials by phone. After breaching systems, the group deployed ransomware and disrupted operations across multiple casinos and hotels.
The attackers, affiliated with the Scattered Spider group, leveraged legitimate RMM tools to move laterally and disable security software. Outages affected digital room keys, gaming systems, and payment terminals for over a week. Public filings indicated a financial impact exceeding $100 million.
The breach underscored two points. First, attackers now use phone-based pretexting and behavioral insights to bypass identity controls. Second, many enterprise SOCs fail to detect abuse of legitimate admin tooling during an active campaign.
Healthcare Ransomware Wave 2024
Throughout 2024, ransomware attacks surged across the healthcare sector. ALPHV, LockBit, and Rhysida targeted hospitals, insurance providers, and electronic medical record vendors. Common entry points included RDP exposure, VPN vulnerabilities, and infostealer-derived credentials harvested from staff workstations.
The attacks often included data exfiltration prior to encryption, with stolen patient records leaked to increase pressure. In some cases, critical care systems went offline. Recovery times stretched into weeks due to dependencies on legacy software and lack of immutable backups.
Healthcare organizations suffered because they operated flat internal networks, relied on outdated endpoint software, and lacked application-layer segmentation. Ransomware operators exploited those conditions with surgical precision, demonstrating that industry-specific compliance doesn’t equate to operational resilience.
AI-Assisted Phishing During Global Elections
In early 2024, coordinated phishing campaigns exploited generative AI to impersonate election officials and trusted public figures. Deepfake audio messages and AI-written emails targeted election workers, voter databases, and campaign teams in multiple countries, including the United States, as well as India and several EU member states (AP News).
The campaigns used language models to create convincing messages in local dialects, adjusted dynamically based on public news cycles. Some operations paired email phishing with AI-generated calls to reinforce urgency or credibility. Attackers harvested credentials to manipulate voter information systems and leak sensitive planning documents online.
The attacks highlighted how generative models can reduce the cost and increase the effectiveness of social engineering. Public institutions, even those with hardened infrastructure, remained vulnerable due to human response triggers and inconsistent identity verification processes across jurisdictions.
Related Article: DeepSeek Tricked into Generating Code for SQL Injection and Lateral Movement
Tools, Platforms, and Infrastructure
Attackers no longer write exploits from scratch or build their infrastructure manually. They operate within a mature ecosystem of tools and services that mirror legitimate software development practices.
Malware Families
Cobalt Strike remains the most emulated and abused post-exploitation framework in use. Originally designed for red teams, it enables payload staging, command execution, lateral movement, and beaconing over HTTP, DNS, or named pipes. Threat actors routinely deploy cracked versions with modified sleep intervals, custom obfuscation, and disabled IoCs.
Sliver, an open-source alternative, has gained popularity among both security teams and adversaries. Written in Go, it compiles to multiple architectures, supports encrypted peer-to-peer C2, and offers rapid customization. Its modular architecture makes it difficult to fingerprint and harder to detect across diverse operating systems.
Havoc represents the latest generation of post-exploitation toolkits designed to bypass modern EDR. Released publicly in late 2023, Havoc includes in-memory payload generation, sandbox evasion, and encrypted C2 channels designed to blend into common network protocols. Its popularity grew quickly among affiliate ransomware groups due to its minimal signature overlap with Cobalt Strike.
Related Article: Threat Actor Groups Tracked by Palo Alto Networks Unit 42
Offensive Security Frameworks
Metasploit continues to serve as the foundation for automated exploitation and payload delivery. It supports exploit chaining, reverse shell generation, and in-memory staging. Metasploit’s regular module updates make it a reliable resource for attackers seeking low-friction access paths into outdated systems.
Empire, built in PowerShell and later ported to Python 3, specializes in fileless attacks within Windows environments. It supports privilege escalation, credential dumping, and Kerberos ticket manipulation — all with native tools. Because it relies on PowerShell remoting, AMSI evasion, and modular scripting, Empire remains relevant in phishing-heavy campaigns where native execution is preferred.
Frameworks such as these reduce the time between vulnerability discovery and exploitation. Adversaries can pivot from scanning to compromise using well-maintained libraries and prebuilt modules tailored to enterprise weaknesses.
Initial-Access Brokerage
Access-as-a-service has matured into a formal supply chain. Brokers compromise systems, extract credentials, validate network presence, and auction access to ransomware crews, data miners, or espionage groups. Access levels include RDP, VPN, Citrix gateways, Active Directory, and cloud management consoles.
Dark-web marketplaces facilitate the exchange. Forums such as Exploit, BreachForums (until its shutdown), and RuTOR offer listings with uptime guarantees, industry verticals, and even previews of compromised environments. Many brokers operate under strict reputation models, using escrow and middlemen to ensure transaction integrity.
Buyers often act within hours. The speed of monetization means that once credentials appear in these markets, detection windows collapse. Many organizations remain unaware of their exposure until lateral movement has already begun or data exfiltration triggers an external notification.
Exploit Economies
Zero-day brokers bridge the gap between independent researchers and nation-state or commercial buyers. These firms operate privately, offering hundreds of thousands of dollars for remote code execution vulnerabilities in widely deployed platforms. iOS, Android, Chrome, and hypervisors remain the most valuable targets.
Brokered vulnerabilities frequently bypass vendor coordination. Buyers request exclusive rights to the exploit, allowing them to use it operationally without public disclosure. Some brokers specialize by region, while others supply multiple governments with overlapping interest areas, resulting in re-exploitation.
Bug-bounty platforms such as HackerOne and Bugcrowd serve a different function. They incentivize responsible disclosure at scale, but some researchers use bounties as a fallback after private offers fail. In some cases, vulnerabilities disclosed through bounties appear repackaged in gray-market toolchains, particularly when the original report lacked exploit detail.
Attack infrastructure continues to evolve toward modularity, resale, and automation. Defenders who fail to monitor this ecosystem will operate behind the curve.
The Effect of Cyber Attacks
IBM’s 2025 Cost of a Data Breach Report places the average cost of a data breach at $4.45 million, with U.S.-based organizations averaging $9.48 million. The calculation excludes regulatory fines, legal settlements, and insurance premium hikes, which often double total exposure.
Operational Disruption
For 86% of organizations, cyber attacks impact business operations, with downtime trends growing longer and more consequential. For SaaS providers or real-time logistics operators, even a four-hour outage cascades across customer ecosystems.
Disruption typically begins upstream. Suppliers’ availability, quality, or data integrity degrade post-breach. A single OT-targeted attack can delay manufacturing for months. In cloud-based ecosystems, interdependencies magnify outages, with one platform’s downtime affecting reliant services.
Incident containment frequently disrupts core operations. To isolate spread, security teams must revoke tokens, reimage systems, shut down network segments, and pause CI/CD pipelines. Even if ransomware is avoided, containment halts revenue-driving functions.
Reputational Damage
Organizations face a collapse in credibility in the wake of breach headlines and leaked customer information. Stakeholders often question not only the technical failure but also the ethical posture of the company’s response.
Trust loss materializes fast. Public companies experience stock price dips post-disclosure, with longer-term underperformance in sectors like healthcare and finance. In private markets, investors may delay rounds or lower valuations if security controls appear insufficient.
Loss of market confidence extends to third parties. The scope of impact can't be measured in dollars when trust is degraded.
Global Breach-Notification Requirements
GDPR Timelines
Under the General Data Protection Regulation (GDPR), organizations must notify their supervisory authority within 72 hours of discovering a breach involving personal data of EU residents. Failure to meet this timeline, even if unintentional, exposes firms to fines up to 4 percent of global annual turnover.
The regulation also mandates prompt notification to impacted individuals if the breach creates a high risk to their rights and freedoms, which includes credential theft, behavioral profiling, or any data that could fuel further exploitation. Most organizations delay because they lack clarity on whether the incident meets the “high risk” threshold. Regulators have signaled little tolerance for ambiguity when consumer data is involved.
CIRCIA Mandates
In the United States, the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) will become fully enforceable by 2026, but foundational requirements already apply. Covered entities must report substantial cyber incidents to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours and report ransomware payments within 24 hours.
CIRCIA applies across 16 critical infrastructure sectors, including energy, finance, transportation, and public health. Reports must include:
- Incident scope
- Vulnerabilities exploited
- Asset types affected
- Mitigation steps taken
Sector-Specific Rules
Financial Resilience Guidance
In financial services, regulators now frame cybersecurity as systemic risk. The U.S. Office of the Comptroller of the Currency (OCC), the Basel Committee, and the European Banking Authority have introduced guidance requiring boards to own security oversight, which involves maintaining recovery playbooks and demonstrating continuity of critical functions.
The Digital Operational Resilience Act (DORA), effective across the EU starting in January 2025, codifies these expectations. DORA requires incident classification and mandatory reporting within hours of detection. Additionally, it requires continuous testing of operational resilience, including red-teaming of third-party providers. Noncompliance exposes firms to supervisory sanctions and market-facing scrutiny.
Healthcare HIPAA Enforcement
In the United States, the Health Insurance Portability and Accountability Act (HIPAA) remains the dominant regulatory framework for protecting health information. The Office for Civil Rights (OCR) mandates notification to affected individuals within 60 days of breach discovery and expects covered entities to maintain audit logs, access controls, and encryption standards aligned with NIST guidance.
The stakes extend beyond fines. Under the Health Information Technology for Economic and Clinical Health (HITECH) Act, organizations may face civil lawsuits, multiagency investigations, and long-term compliance monitoring, which frequently entails accelerated capital spending to modernize cybersecurity controls.
Detection, Response, and Intelligence
Preventing impact starts readiness, with the capacity to detect anomalies, investigate signals across environments, and disrupt malicious activity before it achieves its purpose.
Hypothesis-Driven Threat Hunting
Effective hunting models attacker behavior against enterprise telemetry and seeks evidence of activity that wouldn’t otherwise trigger automated detection. A hypothesis might assert that a compromised service account is being reused for lateral movement using remote management tools. Hunters test this theory across authentication logs, PowerShell transcripts, and asset behavior over time. Detections created from validated hunts then become operationalized into SOC workflows.
Indicator Pivoting
Pivoting from known indicators accelerates discovery of related compromise. Threat hunters ingest IoCs and correlate them across endpoint, network, and cloud telemetry. A single hash tied to a loader may expose multiple infected hosts or shared C2 infrastructure.
Attackers often reuse tactics across campaigns. Pivoting uncovers common operational fingerprints and reveals scope beyond initial compromise. When paired with enrichment sources like VirusTotal, PassiveTotal, or GreyNoise, pivoting can isolate adversary behavior before impact is felt.
Incident-Response Readiness
Playbook Development
IR playbooks define how organizations respond under pressure. Whether credential compromise or supply-chain abuse, an attack vector requires a tailored sequence of detection and validation, containment steps, escalation triggers, and recovery workflows. Playbooks spare teams from wasting time improvising.
Effective playbooks include:
- Systems of record
- Role assignments
- Legal and regulatory touchpoints
- Criteria for triggering external communications
Rigid scripts fail in real intrusions, which is why playbooks are tested, version-controlled, and tied to actual telemetry sources. Response must account for variations in attacker behavior, internal dependencies, and the reality of degraded environments.
Crisis-Communications Channels
Crisis communications require predefined internal and external channels, executive spokespersons, legal review cadence, and clear messaging. Executives must coordinate with legal, operations, and public relations, as misstatements can violate SEC disclosure rules or trigger regulatory inquiry. Communications must reflect the current forensic state, acknowledging what’s confirmed, what’s under review, and when updates will follow.
Cyber-Threat Intelligence
High-fidelity threat intelligence aggregates from internal telemetry, commercial feeds, ISACs, and open-source channels. Intelligence must include contextual detail (i.e., infrastructure usage, TTPs, targeting logic, attribution confidence). Feeds that provide IPs without context degrade signal and overwhelm SOCs with false positives.
Effective programs distinguish between three types of intelligence:
- Strategic intelligence informs long-term defense planning.
- Tactical intelligence drives immediate detection engineering.
- Operational intelligence connects intrusions to campaigns, infrastructure overlaps, or threat-actor tradecraft.
Fusion centers align intelligence with detection, investigation, and response. Without cross-domain integration of endpoint, cloud, network, identity, and third-party telemetry, organizations miss correlations.
Mature teams enrich telemetry at ingestion, tagging sessions, artifacts, or flows with risk scores and contextual labels. Analysts pivot across layers, moving from DNS queries to identity behavior to SaaS admin logs without losing time.
Emerging Cyber Attack Trends
Attack surfaces shift faster than most organizations can update their playbooks. Defensive strategies built for current-state risk often fail under future-state velocity. The threat landscape now includes adversaries that scale with compute, adapt using models, and exploit structural transitions before defenders finish reading the standard.
Figure 8: Cross-channel attacks from a single agent capable of pivoting to achieve the attacker’s ends
Automated Social-Engineering Bots
Adversaries now deploy AI agents that ingest OSINT and adapt to real-time responses. These bots, not to be underestimated, generate tailored phishing lures and impersonate executives in multilingual contexts, automating pretext development based on scraped communications. What’s more, they improve targeting logic with every failed attempt.
Some bots operate across channels. A single agent might send a phishing email, follow up with a deepfake voice call, and pivot into Slack or Teams messages using harvested session cookies. Attackers use fine-tuned large language models (LLMs) with role-specific prompts to manipulate customer support and password reset flows.
Code-Gen Malware
AI-assisted malware development has moved from theoretical to operational. Attackers fine-tune models to generate obfuscated payloads that evade static and heuristic detection. They feed LLMs with detection rules and iterate until the generated code avoids YARA hits or EDR signatures.
Code-generation tools also assist in creating polymorphic droppers, loader scripts, and domain-specific exploits that target edge cases in cloud platforms or misused SDKs. Combined with automated fuzzing, AI accelerates discovery and weaponization at a scale, breaking current patching models.
Related Article: Now You See Me, Now You Don’t: Using LLMs to Obfuscate Malicious JavaScript
Self-Learning Worms
No longer bound to preprogrammed logic, autonomous, self-learning worms can now observe and adjust to environment variables, going so far as to select payload modules based on system configuration, domain structure, or telemetry feedback. They may, for instance, switch from credential harvesting to wiper behavior midoperation, depending on detection likelihood. And by continuously scoring outcomes, they evolve with each node compromised.
Cloud-Scale Impact Scenarios
Cloud-native autonomous worms exploit shared control planes, lateral privileges in IAM roles, and overpermissioned service accounts to propagate across tenants and geographies. A single vulnerable microservice, once exploited, allows deployment of agentless propagators that replicate via orchestration APIs, misconfigured CI/CD tokens, or exposed infrastructure-as-code secrets.
Within multicloud environments, these worms use standard SDKs to enumerate resources, escalate within identity hierarchies, and destroy observability tooling before payload execution. Impact becomes multiplicative, affecting telemetry, redundancy, and recovery workflows.
Bottom line? Next generation of threats won’t rely on brute force. They’ll rely on context awareness, adaptive logic, and the speed of inference over the speed of code execution. Cyber defense must evolve. Anticipation, instrumentation, and architectural hardening define the path forward.
Testing and Validation
No control operates as designed unless it’s tested under live conditions. Simulation, red-teaming, and validation exercises expose assumptions. Maturity comes from validated readiness under pressure.
Red-Team Operations
Objective-Based Engagements
Red-team exercises simulate real-world adversaries with defined goals, timeframes, and operational constraints. Unlike generic penetration tests, red teams pursue mission objectives using tactics aligned with known threat actors.
Red teams often start with minimal information. They perform reconnaissance, evade detection, pivot across domains, and exploit real misconfigurations. Their success or failure validates the key efficacies, including:
- Endpoint telemetry
- Alerting thresholds
- Analyst workflows
- Incident escalation paths
Purple-Team Collaboration
Purple teaming blends offense and defense in real time. Red and blue teams work side by side to execute specific techniques, validate detection coverage, and tune response processes, which accelerates feedback loops between operators and defenders.
Rather than scoring success on breach outcomes, purple teams measure telemetry quality, signal-to-noise ratios, and SOC response time. Every action taken by the red team becomes a learning opportunity for the blue team to create or refine a detection rule, response playbook, or escalation path.
When executed properly, purple teaming builds muscle memory, reinforces threat modeling assumptions, and improves adversary alignment across detection engineering, SOC, and cyber threat intelligence.
Adversary Simulation
ATT&CK Emulation Plans
Simulations based on MITRE ATT&CK techniques allow organizations to test control coverage against a known behavioral model. Rather than launching full kill chains, simulation tools execute discrete techniques (i.e., credential dumping, registry tampering, remote file transfers) and measure whether they trigger telemetry, alerts, or automated response.
In addition to detecting rules, simulations test the integrity of log pipelines and alerting thresholds. Mapping test results to ATT&CK matrices helps security leaders understand which tactics are covered and where defensive gaps persist.
Breach-and-Attack Platforms
Automated breach-and-attack simulation (BAS) platforms offer continuous testing by executing predefined attack paths across production or staging environments. Tools like SafeBreach, AttackIQ, and Cymulate execute payloads at the network, endpoint, and cloud layers to validate defense readiness.
BAS platforms simulate events like credential theft and data exfiltration under realistic constraints. Unlike one-time tests, they enable recurring validation, along with regression testing after control changes and consistent benchmarking across teams.
Metrics and Continuous Improvement
Do you know where your defenses work, where they fail, and where attackers will strike next? Here’s where KPIs become intelligence. Mature organizations treat metrics as operational leverage.
Key Risk Indicators
Attack Frequency Rate
Attack frequency measures how often threat actors target your environment. Frequency includes observed scanning, credential stuffing, phishing attempts, API probing, and exploit attempts against exposed assets. Tracking these over time surfaces patterns.
High-frequency targeting doesn’t always imply compromise risk, but it signals attraction. Spikes can indicate listing in breach dumps, reuse of leaked credentials, or presence in attacker automation loops. Low visibility here often results from blind zones in edge telemetry or fragmented logging in cloud environments.
Mean Time to Compromise
Mean time to compromise (MTTC) tracks the average duration between initial access and attacker privilege escalation or lateral movement. It reveals not only detection lag, but also architectural weaknesses such as token reuse or overprivileged accounts.
Measuring MTTC requires replaying red-team activity and post-incident timelines. Organizations with low MTTC typically rely on signature-based alerts without correlating identity or behavioral signals. Increasing MTTC by minutes can reduce attacker payload success by hours or even entirely.
Program Maturity Models
Capability Progression Stages
Maturity models assess your program's evolution across detection, prevention, response, and recovery. They move from reactive to proactive, from manual to automated, and from siloed to orchestrated. NIST’s Cybersecurity Framework, as with MITRE’s Cybersecurity Capability Model (C2M2) and CIS Controls Implementation Groups, offers tiered benchmarks.
Progression is measured by coverage depth, as well as operational speed and signal integrity. An organization may have world-class tooling and remain low maturity if alerts lack context or playbooks remain unused.
Capability gaps often concentrate around lateral movement visibility, cloud role enforcement, SaaS monitoring, and automated response logic. Maturity lifts when teams close gaps in ways measurable through validation.
Peer Benchmarking
Peer benchmarking positions your performance in the context of similar organizations grouped by industry, size, geography, or threat profile. It informs strategic investments by showing where you lead, lag, or align with standards.
Benchmarking must account for attack surface complexity. (A fintech company with 300 microservices, 5,000 IAM roles, and 12 third-party integrations doesn’t benchmark identically to a regional healthcare provider.) Effective comparisons normalize metrics.
Security leaders use benchmarking to justify program changes, such as reallocating investment from endpoint detection to identity governance or accelerating purple-team validation cycles. Without a reference point, improvement is subjective.