-
Application Security: A Practitioner’s Guide
- Application Security Explained
- Types of Applications Organizations Need to Secure
- Whose Job Is It – Developers or Security?
- A Pragmatic Guide for Security-Minded Developers
- Types of Application Security Testing
- Application Security Tools and Solutions
- Compliance Is Not Security, But It’s Not Optional Either
- Application Security FAQs
-
What Is AppSec?
- AppSec Explained
- The Fundamentals of AppSec
- Building Security into the Development Lifecycle
- Implementing Secure Coding Practices
- Application Security Testing
- Implementing Security in CI/CD Pipelines
- Securing Application Architecture
- Access Control and Authentication
- Monitoring and Incident Response
- Managing AppSec in Production
- Training and Building a Security-First Culture
- AppSec Trends
- AppSec FAQs
- What is IaC?
- What Is Shift Left Security?
-
What Is Cloud Detection and Response (CDR)?
- Cloud Detection and Response (CDR) Explained
- How CDR Works
- Key Features of CDR
- CDR and Other Detection and Response Approaches
- How CDR and XSIAM Work Together
- How CDR Addresses Unique Challenges in Cloud Security
- Key Capabilities of CDR
- How CDR Bridges SOC and Cloud Security
- Challenges of Implementing CDR
- CDR Best Practices
- Cloud Detection and Response FAQs
- What Is Cloud Network Security?
-
What Is a Transit Virtual Private Cloud (VPC)?
-
What Is a Hybrid Data Center?
-
How Does VMware NSX Security Work
- Cloud Security Service, Cloud Storage and Cloud Technology
Cloud Security Threats: Detection and Challenges
Cloud security threats include data breaches, insider threats, account hijacking, insecure APIs, and malware attacks. These threats target cloud environments by exploiting misconfigurations, weak access controls, or human error.
Detection in cloud security involves using advanced tools like AI and machine learning to monitor, identify, and respond in real time to unusual behavior or potential security breaches.
Challenges in cloud security include:
- Integrating legacy systems
- Managing multi-cloud and hybrid environments
- Ensuring data privacy and regulatory compliance
- Maintaining visibility and control over complex cloud infrastructures
Addressing these requires a proactive and comprehensive approach to securing cloud environments.
What Is Cloud Threat Detection?
Cloud security threat detection focuses on identifying and responding to risks and threats in cloud environments. This includes using traditional and cloud-native security tools and techniques to detect potential issues early.
Cloud threat detection should also extend to containerized applications and their infrastructure. To do this, DevSecOps teams consider cloud threats when they containerize applications. They include protections throughout the lifecycle that include cloud threat detection systems, such as vulnerability scanning, configuration management, access management, network segmentation, and monitoring.
What Are the Main Types of Cloud Security Threats?
To overcome the challenges of cloud security threat detection, it is essential to understand the types of threats organizations face—from sophisticated zero-day attacks to simple human error. The following are several commonly cited examples of security threats to cloud-based systems and applications.
Data Breaches
Data breaches and subsequent data loss are among the most concerning security threats for most organizations because of their far-reaching implications. When unauthorized access results in sensitive information being stolen from cloud environments, organizations face legal, financial, compliance, and reputational issues.
Insecure APIs
A failure to secure APIs in cloud environments allows threat actors to bypass access controls and gain direct access to cloud environments. Insecure cloud APIs are routinely exploited for attacks, such as injection attacks, machine-in-the-middle (MITM) attacks, distributed denial of service (DDoS) attacks, and server-side request forgery (SSRF).
Insider Threats
One of the more challenging security threats to detect is an insider threat, where an authorized user takes advantage of their access privileges to conduct malicious activity. In some cases, insider threats are related to human errors that result in a security incident.
Misconfigurations
Misconfigurations are one of the most common cloud security threats due to the expansive attack surface and preponderance of human error. Threat actors exploit cloud resources to circumvent access controls and compromise cloud environments when they are not configured correctly.
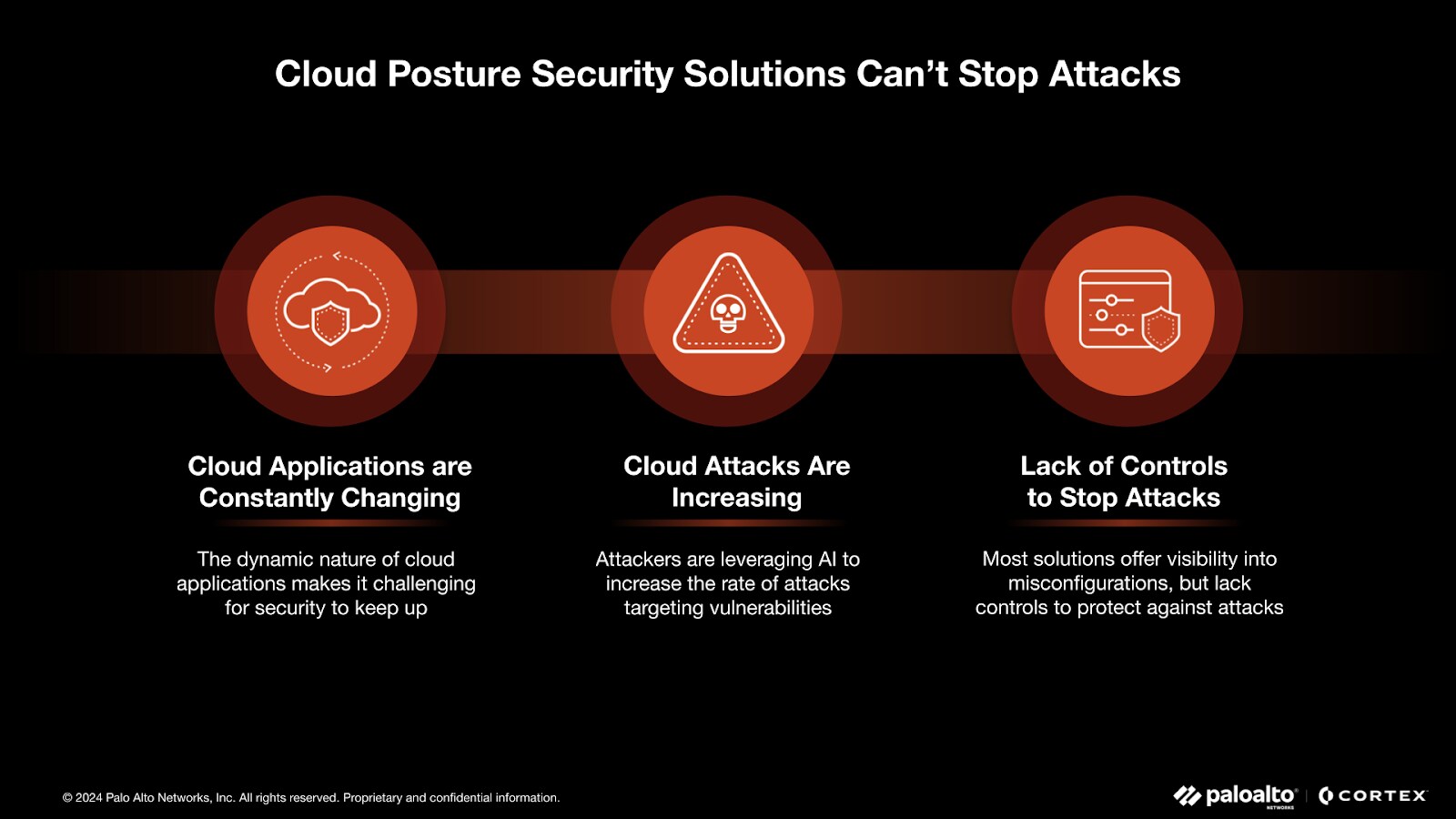
Who Is Responsible for Cloud Security Risks and Threat Detection?
The responsibility for identifying risks and detecting threats in cloud environments is shared between cloud service providers and the organizations that use their services. The delineation of responsibility varies depending on the type of cloud deployment.
In public cloud environments, the cloud provider owns the infrastructure and is responsible for its security, while data protection is the responsibility of each organization.
Software-as-a-service's responsibility for threat detection and prevention varies based on the provider and service offered. Examples of typical areas of responsibility for threat detection and prevention include the following:
Infrastructure-as-a-Service (IaaS)
- Organizations secure data, applications, operating systems, user access, and virtual network controls.
- Cloud service providers secure compute, storage, and physical networks and manage all updates, patches, and configurations.
Platform-as-a-Service (PaaS)
- Organizations secure data, user access, and applications.
- Cloud service providers secure computing, storage, physical networks, virtual network controls, and operating systems.
Software-as-a-Service (SaaS)
- Organizations secure data and user access.
- Cloud service providers secure computing, storage, physical networks, virtual network controls, operating systems, applications, and middleware.
What Are Key Indicators of Compromise (IoCs) in Cloud Environments?
To effectively detect and deter cloud threats, it is essential to understand what IoCs to look for and how they work. The main categories of IoCs in cloud environments are network-based, file-based, host-based, and behavioral-based IoCs.
The types of activities that can alert administrators to potential cloud security threats include:
- Abnormal modifications to files, applications, or the Windows Registry
- Irregularities in Domain Name System (DNS) queries, such as requests for known malicious domains
- Multiple failed login attempts, login from an abnormal location, or access to files unusual for a user
- Obscure port usage within a network
- Privileged account usage irregularities, such as administrators changing user-access settings or granting unwarranted access rights
- The sudden surge in requests for sensitive files, particularly from a single user or IP address
- Unexpected or unauthorized changes to configurations or access management policies
- Unusual outbound network traffic, such as a data spike, leaves the network
What Are the Main Challenges in Cloud Security?
Understanding the challenges in cloud security can help teams refine cloud threat detection strategies to optimize efficacy. Each organization will have unique challenges, but the following are several of the most common challenges that security teams struggle to overcome.
Identity and Access Management (IAM)
IAM is vital to cloud security, but implementing it across complex cloud environments challenges even the best security teams. Not only must IAM strategies address role assignments, including privileged access management, but they must also consider how access is monitored.
Monitoring access by various user types is critical for cloud threat detection, providing security teams with early indications of potential attacks. The challenge lies in maintaining visibility for all users across all cloud resources.
Lack of Cloud Security Strategy and Skills
Some security teams have struggled with the rapid growth in cloud environments. Since many traditional security models do not apply to this new environment, security teams must develop and implement cloud-specific security strategies.
In addition, some organizations’ existing teams lack the experience to develop these strategies and support cloud-specific security solutions. This deficiency requires organizations to train existing teams or recruit new team members. However, a shortage of resources with cloud security expertise makes it difficult to recruit new staff.
Limited Visibility
Many cloud environments need more visibility, making monitoring configurations, network traffic, and user activities challenging. This lack of visibility makes it difficult for security teams to detect cloud misconfigurations, unauthorized access, and other security vulnerabilities.
Managing a Rapidly Evolving Attack Surface
Cloud environments are increasingly complex, with numerous services and users being rapidly provisioned and decommissioned across exploding multi-cloud environments. This expansion creates a large, dynamic attack surface that requires continuous monitoring, assessment, and tuning to enable rapid threat detection and ensure that configurations are set correctly.
Shadow IT
Cloud systems' expansive use includes sanctioned and unsanctioned resources (i.e., shadow IT). Because cloud solutions are easily accessible, shadow IT has become more prevalent, exposing organizations to cloud security threats.
These threats are difficult to detect when teams are unaware that the systems are in use. This lack of visibility and control over unauthorized cloud services means that security and IT teams cannot effectively enforce security policies or protect sensitive data.
What Is the Role of Automation in Cloud Threat Detection?
The scale of cloud environments makes cloud security automation imperative for detecting cloud security threats and ensuring a timely response. Cloud security automation tools can continuously monitor potential threats across cloud infrastructure and services. Leveraging cloud security automation helps teams safeguard data, applications, and infrastructure within cloud environments.
Unlike traditional manual monitoring methods, cloud-specific security automation tools are designed to keep pace with the volume and sophistication of cloud-focused cyber threats. These AI-driven tools enable real-time cloud threat detection and analysis across complex multi-cloud environments.
Tools for Cloud Threat Detection
Despite the preponderance of cloud security threats, a number of tools are available to protect cloud environments. Many of these solutions are AI-driven, leveraging artificial intelligence and machine learning to enable granular threat detection and analysis and support a zero-trust security model. The following are several cloud security tools available to protect cloud environments.
Cloud Detection and Response (CDR)
CDR solutions are purpose-built for cloud environments. They are designed to provide real-time threat detection and automated response capabilities to provide effective security for cloud environments. Also referred to as cloud-native detection and response (CNDR) and cloud threat detection and response (CTDR), CDR solutions collect and analyze data from various sources, such as network traffic, cloud logs, and user activity, to help organizations detect and respond to threats.
Cloud-Access Security Brokers (CASBs)
A cloud access security broker (CASB) is an intermediary between users and cloud service providers to enforce security policies (e.g., multi-factor authentication). CASBs offer visibility into cloud application usage across multiple cloud services to facilitate cloud security threat detection.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM solutions manage access permissions and entitlements in cloud environments to prevent excessive access rights and privileges. Using CIEM solutions helps security teams detect and mitigate cloud security risks and threats associated with entitlements that grant a higher than-required level of access, which supports zero-trust security models.
Cloud Native Application Protection Platform (CNAPP)
CNAPPs combine functionality for cloud security posture management (CSPM), cloud workload protection platforms (CWPPs), cloud Infrastructure entitlement management (CIEM), and CI/CD security into a unified, end-to-end solution. This approach provides visibility across silos and allows security teams to protect cloud-native applications across the entire application lifecycle.
With CNAPPs, a single platform can protect applications at runtime while integrating security into development workflows to help DevSecOps teams detect and fix flaws that cloud security threats can exploit.
Cloud Security Posture Management (CSPM)
CSPM solutions automate the detection and remediation of misconfigurations across cloud environments. Purpose-built for cloud computing, CSPM tools help security teams continuously monitor and detect threats in cloud environments, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Cloud Workload Protection Platforms (CWPPs)
A CWPP is engineered to address the unique requirements of protecting workloads in cloud environments. Cloud security threats can be detected in workloads hosted across public, private, and hybrid clouds. CWPP provides comprehensive cloud security threat detection capabilities, including vulnerability identification, host intrusion detection and prevention, and behavioral monitoring of cloud workloads
Kubernetes Security Posture Management (KSPM)
KSPM is a cloud-native security solution that automatically detect vulnerabilities and remediate security threats for all Kubernetes resources. Critical for maintaining visibility and enforcing security controls across increasingly complex Kubernetes environments, KSPM solutions automate security scans across Kubernetes clusters to detect threats, assess and categorize threats, and identify Kubernetes misconfigurations.
User Entity Behavior Analytics (UEBA)
UEBA solutions leverage artificial intelligence and machine learning to detect user and entity behavior anomalies within an organization’s network and cloud environments. The advanced threat detection capabilities play a critical role in identifying sophisticated cloud security threats, such as insider threats, compromised accounts, or advanced persistent threats (APTs).
Cloud Threat Detection Best Practices
There are many approaches and solutions to support cloud threat detection. The following are several proven best practices that should be included in security plans to ensure the efficacy of cloud threat detection efforts.
Proactively Hunt Cloud Security Threats
Conduct regular threat-hunting exercises to detect and address potential vulnerabilities and threats proactively. Key elements to include in threat hunting are:
- Searching for hidden or evolving threats within cloud infrastructure, applications, and workloads
- Collecting and monitoring security data to detect usual behavior by human and machine users
- Integrating threat intelligence feeds into threat-hunting exercises
- Applying MITRE ATT&CK Cloud Matrix techniques for guidance on potential attack vectors
Implement a Zero-Trust Security Strategy
Apply the principles of zero-trust to cloud security programs. These include:
- Enforcing least-privilege access controls
- Using micro-segmentation across networks with sensitive data and services
- Monitoring and verifying the identity and trust levels of all users, devices, and applications continuously
- Assuming that a breach has occurred and having incident response plans in place
- Securing every endpoint and workload
Test Cloud Threat Detection Systems
Regular testing of cloud security detection tools is conducted to confirm that they are performing according to expectations and that response mechanisms are working effectively. These exercises proactively identify gaps in detection and response capabilities.
Methods for testing cloud security detection capabilities include simulated attack scenarios (i.e., red team-blue team and purple team exercises), breach and attack simulation tools, penetration testing, and adversary emulation.