SASE and Secure Web Gateway: How Are They Related?
SWG is a foundational element of SASE architecture, which provides a more holistic and flexible approach to secure network access and traffic control.
A secure web gateway (SWG) filters and monitors web traffic, ensuring adherence to established policies. Secure access service edge (SASE) encompasses this function and extends it by integrating additional security and networking capabilities, optimizing security and performance for diverse environments.
What Is a SWG?

A web security gateway, also known as a secure web gateway or SWG, is a critical network security component, acting as a mediator between users and the internet. It filters and monitors internet traffic to enforce corporate policies and defend against cyber threats. Organizations deploy SWGs either on premises or in the cloud. They inspect outgoing web requests, authenticate users, and enforce security policies to ensure internet usage complies with organizational standards.
A SWG’s primary function is to offer a secure gateway for internet traffic, protecting against malicious code in seemingly legitimate websites, malware, and other cyber threats. By filtering and inspecting web traffic in real time, SWGs can detect and block threats before they reach the end user's device. This helps organizations prevent data breaches, maintain compliance with regulatory requirements, and safeguard sensitive information.
SWG plays a crucial role in ensuring the security and integrity of an organization's network. They provide a comprehensive security solution that surpasses traditional network security measures by offering advanced features such as URL filtering, application control, and antimalware protection. Additionally, SWGs can help organizations optimize network performance by caching frequently accessed web content and reducing bandwidth usage.
What Is a Secure Web Gateway (SWG)?
What Is SASE?
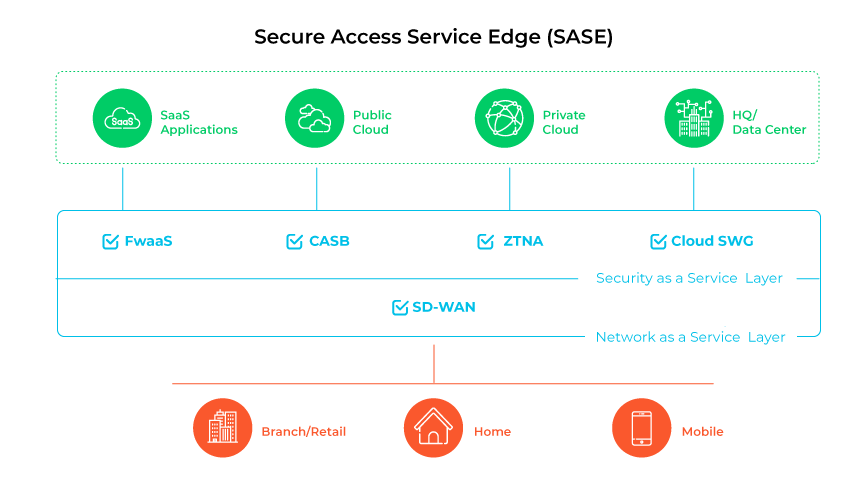
Secure Access Service Edge, or SASE, is a unified network architecture that combines comprehensive WAN capabilities and network security functions directly into the cloud. This structure supports the dynamic, secure access needs of modern organizations. SASE extends the traditional network perimeter to include all access edges, aiming to provide secure and fast cloud connectivity for all users, regardless of location.
SASE operation involves directing traffic through a cloud based service that integrates various security and network functions. By deploying these services at the network's edge, closer to where the users and devices connect, SASE reduces latency and improves performance. It provides consistent policy enforcement and security across the entire organization, centralizing the management of these functions.
SASE components include SD-WAN, zero trust network access (ZTNA), secure web gateways (SWG), cloud access security brokers (CASB), and firewall as a service (FWaaS). These components work in concert within the SASE framework to ensure secure network access, streamlined management, and a responsive network infrastructure that adapts to an organization's evolving demands.
What Are the Differences Between SWG and SASE?
| SWG vs. SASE: What Are the Differences? | ||
|---|---|---|
| Parameters | Secure Web Gateway (SWG) | Secure Access Service Edge (SASE) |
| Architectural Integration | A specific component providing secure internet access and web filtering. | A comprehensive framework integrating SWG with SD-WAN, CASB, FWaaS, and ZTNA into a unified, cloud native service model. |
| Scope of Functionality | Focuses on internet security, managing web access, detecting threats, and enforcing policies. | Offers a broader range of functionalities, combining networking and network security services from the cloud for dynamic, secure access. |
| Network Optimization | Deals with security related aspects of web traffic. | Optimizes network performance in addition to security through SD-WAN technology. |
| Access Control | Enforces access policies based on users' web activity. | Provides granular access control with ZTNA for detailed policy enforcement based on the principle of least privilege. |
| Response to Cyber Threats | Includes threat prevention mechanisms. | Combines multiple security functions to respond more comprehensively to cyber threats. |
Architectural Integration
A SWG is a specific component that provides secure internet access and web filtering. In contrast, SASE represents a comprehensive framework that integrates SWG with other services including SD-WAN, CASB, FWaaS, and ZTNA into a unified, cloud native service model.
Scope of Functionality
SWG primarily focuses on internet security, specifically managing web access, detecting web based threats, and enforcing corporate policies. SASE, however, offers a broader range of functionalities, including combining networking and network security services delivered from the cloud to support dynamic, secure access.
Network Optimization
While SWG deals with security related aspects of web traffic, SASE optimizes network performance in addition to security. SASE architecture provides optimal network routing, enhancing performance for remote and distributed users through SD-WAN technology, which is not a feature inherent to SWGs.
Access Control
SWG enforces access policies based on users' web activity. SASE, conversely, provides more granular access control with ZTNA, allowing for more detailed policy enforcement that grants access on a need-to-know basis, aligning with the principle of least privilege across all organizational resources.
Response to Cyber Threats
While both SWG and SASE include threat prevention mechanisms, SASE's integrated approach combines multiple security functions to respond to cyber threats more comprehensively, beyond the capabilities of a standalone SWG solution.
What Are the Similarities Between SWG and SASE?
| SWG vs. SASE: What Are the Similarities? |
|---|
|
Security and Policy Enforcement
Both SWG and SASE are integral in enforcing security policies within an organization. They provide secure internet access by monitoring and controlling the traffic between users and the internet, applying corporate and regulatory compliance standards to prevent cyber threats.
Cloud Centric Design
SWG and SASE share a cloud centric design that allows for scalability and centralized policy management. This design is essential for the support of distributed and remote workforces, enabling secure access to corporate resources regardless of geographic location.
Traffic Inspection and Management
Both SWG and SASE include traffic management and inspection. They each provide visibility into user activities and offer the means to control access to websites and applications.
Support for Compliance and Privacy Requirements
Both technologies are crucial for maintaining compliance with regulatory requirements, as well as protecting sensitive data and privacy. They achieve this by inspecting traffic, enforcing data loss prevention (DLP) policies, and offering detailed logging and reporting capabilities to aid in audits and compliance verification.
Enhancing User Experience
SWG and SASE focus on enhancing the user experience by ensuring users access applications and services securely and efficiently. They both utilize mechanisms to reduce latency and improve performance, ensuring security measures do not negatively impact productivity.
The Role of SWG in a SASE Solution

Deploying SWGs as isolated solutions can pose challenges, notably in the lack of integration with the wider security infrastructure. Standalone SWGs can lead to siloed security postures and complex operational environments. Without the benefit of seamless workflow coordination with other security controls, organizations may struggle with a lack of agility and increased vulnerability to internet based threats.
When SWG functions converge within a SASE framework, the cloud native integration transcends these limitations. SASE's architectural design, which combines networking and security into a unified solution, streamlines the incorporation of SWG capabilities. This fusion allows for consistent security policy application and simplifies the enforcement of web access controls across the enterprise.
Within SASE, SWG plays a critical role by providing granular web session controls, such as URL filtering and SSL decryption. The SWG component in SASE extends security measures to include advanced threat detection and consistent application of security policies. As part of a SASE solution, SWG also contributes to the overall reduction in latency and enhancement of end user experience by connecting users directly to the internet.
The integration of SWG into SASE marks a significant shift from traditional network designs that rely on centralized, on premises security appliances. In a SASE solution, the SWG operates from the cloud, offering global, scalable protection. This approach ensures uniformly delivered security, whether users connect from remote locations, branch offices, or the corporate campus, facilitating a secure transition to the cloud and supporting modern enterprise requirements.
How to Choose a Modern SWG as Part of SASE Architecture

When considering vendors to work with for a SASE initiative initially focused on SWG, CASB, and ZTNA, organizations should consider these key questions:
What will the user transition entail when migrating from an established SWG to a new system?
The need for new software or alterations in policy routing can introduce extra layers of complexity and delay the migration process. The intricacy involved in the changeover is often a reason organizations continue with existing SWG systems. Using present agents or pre-existing PAC files could simplify and expedite the shift.
Can the provider expand its SASE offerings to suit evolving needs?
Initially, a SASE project might target specific needs, such as safeguarding remote workers. Over time, the goal will typically broaden. When starting with SWG, CASB, and ZTNA consolidation, it’s important to verify that potential providers can accommodate various access environments, including different device types and user categories. Providers with the capacity to incorporate comprehensive SASE solutions, like IoT device protection or networking and SD-WAN capabilities, offer adaptability for future expansion.
Are the management and oversight of various SASE functions integrated?
Possessing an array of SASE services is insufficient. Integrated management is crucial to address operational inefficiencies. Management via a graphical user interface that simplifies policy configuration across SASE services and minimizes mistakes is vital. Additionally, a unified dashboard providing complete oversight of all users and locations can aid security teams in swiftly identifying and prioritizing issues.
How extensive is the vendor's network and its infrastructure for connectivity?
Scalability and dependability are essentials for SASE solutions, demanding a robust, worldwide network. A network with a global reach and substantial peering agreements is essential to maintain high performance and a satisfactory user experience. Some providers may collaborate with cloud services to utilize their private networks, enhancing secure connectivity and mitigating the impact of public internet traffic congestion on performance.