-
- Business Email Compromise Explained
- Mechanics Behind Business Email Compromise
- BEC as a Strategic Component in Multistage Attacks
- Use Cases: BEC Campaigns with Measurable Impact
- Detecting BEC in Enterprise Environments
- Practical Defenses Against BEC at the Identity Layer
- Why BEC Is a Board-Level Concern
- Business Email Compromise FAQs
What Is Business Email Compromise (BEC)?
4 min. read
Table of Contents
Business email compromise (BEC) is a targeted social engineering cyber attack that exploits trust in corporate email systems to manipulate employees into initiating unauthorized transactions or disclosing sensitive information. Threat actors often hijack or spoof executive email accounts using credential theft, domain lookalikes, or MFA fatigue techniques. Once inside the communication chain, attackers conduct reconnaissance to mimic writing styles, reference real-world projects, and redirect payments or data to attacker-controlled destinations.
Business Email Compromise Explained
Business email compromise (BEC) targets the human and procedural layers of email communication. Rather than exploiting technical weaknesses in email infrastructure, it attempts to manipulate legitimate communication channels to deceive targets and redirect trusted actions — most often involving credentials, sensitive data, or the wire transfer of funds.
Under the MITRE ATT&CK framework, BEC is mapped to T1586.002 (Compromise Infrastructure: Domain) and often overlaps with T1566.002 (Phishing: Spearphishing Link) and T1556.002 (Modify Authentication Process: Domain Trust Modification) depending on the stage and delivery.
Anything But a Random Attack
Unlike phishing campaigns that involve broad distribution and malicious links, BEC attackers use artificial intelligence (AI) and machine learning (ML) to research their targets and create convincing messages that appear like legitimate business correspondence.
The attacks rely heavily on social engineering tactics, often beginning with credential theft, domain impersonation, or inbox infiltration using ploys like MFA fatigue or session hijacking. Attackers monitor email threads, understand workflows, and inject themselves into conversations with carefully timed, highly contextual messages. They frequently impersonate executives, vendors, or legal counsel to pressure targets into bypassing standard approval processes.
BEC doesn’t rely on payloads or malware, which enables it to bypass technical detection by mimicking normal business operations. The attacker compromises, spoofs, or impersonates a legitimate business identity and then initiates a financially or operationally harmful request.
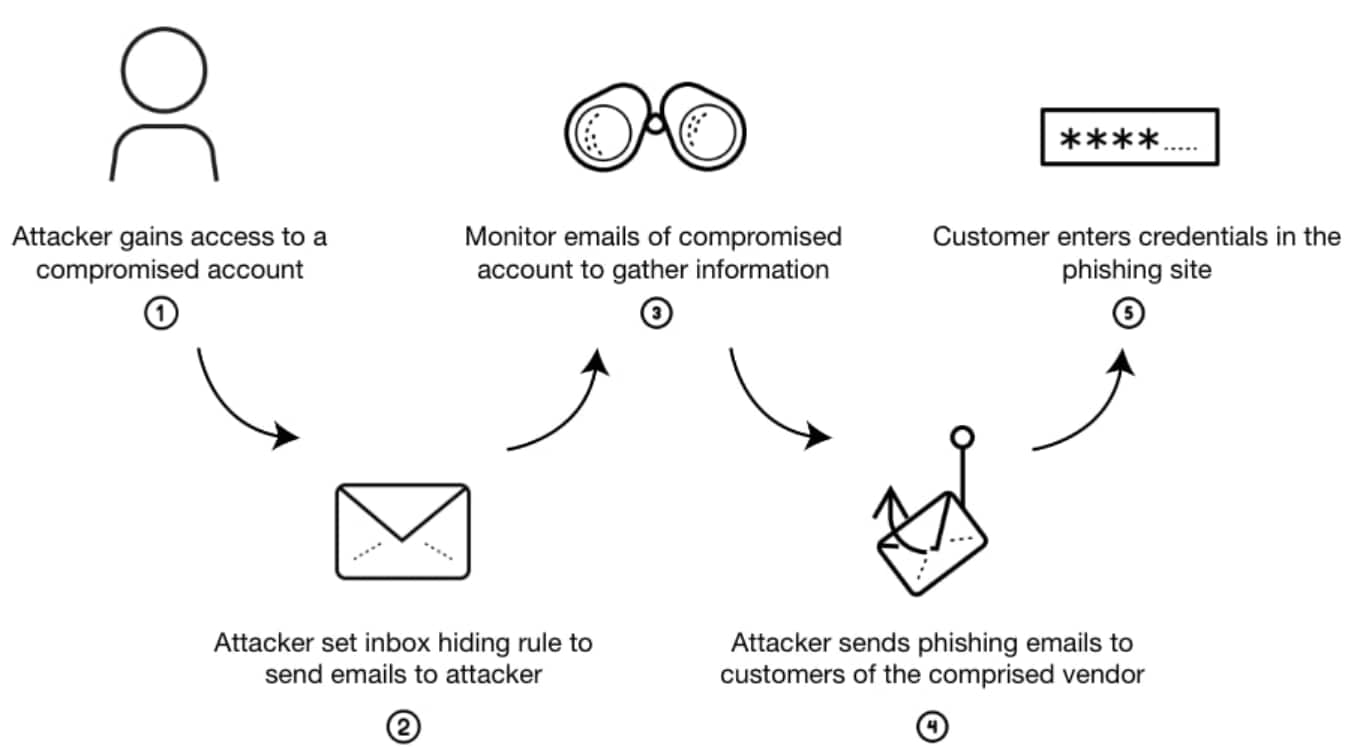
Figure 1: Built on compromises, spoofs, and business identity impersonation
Prevalence of BEC
Among cases Unit 42 investigated in 2023, BEC accounted for 34%, with the average financial loss per successful wire fraud reaching $286,000. The U.S. government considers BEC attacks one of the most financially destructive forms of cybercrime. In 2024, the FBI’s Internet Crime Complaint Center (IC3) attributed 73% of all reported cyber incidents to BEC, with cumulative losses exceeding $55 billion over the past decade.
Alternative Classifications and Related Terminology
- Vendor Email Compromise (VEC): BEC targeting third-party suppliers to reroute invoice payments or gain downstream access.
- CEO Fraud: A subtype where attackers impersonate executives to pressure subordinates into unauthorized wire transfers or confidential disclosures.
- Payroll Diversion: A specific BEC variant that redirects employee pay deposits.
- Email Account Compromise (EAC): The initial foothold used to launch BEC from a real account rather than a spoofed identity.
These terms describe functional variations of the same underlying mechanism — the manipulation of trust within business communications.
Key Differences Between BEC and Phishing
While phishing and business email compromise are related cyberthreats, they have distinct characteristics and operate at different levels of sophistication and targeting. Understanding their differences enables organizations to leverage effective training and preventive technologies to reduce the risk of breaches.
Category |
BEC |
Phishing |
Targeting and Personalization |
Focuses on specific individuals or departments with financial authority or access to sensitive data. Highly personalized emails based on detailed reconnaissance. |
Broad targeting with minimal personalization. Relies on mass messaging to reach as many recipients as possible. |
Attack Complexity and Effort |
Sophisticated attacks that involve reconnaissance and may use AI/ML to mimic writing style and email behavior of the impersonated user. |
Ranges from basic to complex, but often uses templated messages sent to many recipients. |
Objectives |
Aims for financial gain through wire fraud or payment redirection. May also steal sensitive business information. |
Seeks personal information—credentials, credit card numbers—for financial theft, identity theft, or ransomware deployment. |
Method of Delivery |
Delivered almost exclusively via email. |
Delivered via email, but also through SMS (smishing), voice calls (vishing), or social media messages. |
Scale and Scope |
Targets fewer individuals, but each attack aims for a high payout. |
Casts a wide net to maximize chances of catching victims, often with lower value per target. |
BEC Attacks Commit to the Long Study
Like phishing, early BEC operations relied on spoofed domains and basic social pressure. Attackers sent emails that appeared to originate from senior leadership or trusted vendors, urging quick action. Modern BEC campaigns are more invasive and persistent. Attackers now:
- Compromise real accounts to maintain internal visibility and legitimacy
- Leverage generative AI to write in brand and voice
- Insert rules into inboxes to redirect or delete replies
- Target shared mailboxes, billing queues, and procurement teams where financial action is common
- Exploit unmonitored calendar events and automated approval systems
BEC has also expanded in sophistication through multiparty pretexting — where attackers engage both internal and external targets simultaneously, manipulating entire threads across multiple organizations to reroute payment flows or delay fraud discovery.
The most damaging BEC incidents today are not one-time frauds. They’re staged compromises designed to embed themselves in the fabric of trust-based processes. Detection and defense now require more than email filtering — they demand visibility into behavior, approval logic, and relationship context.
Mechanics Behind Business Email Compromise
Business email compromise succeeds by mimicking legitimate correspondence, positioning itself at just the right point in a business process, and issuing a request that is procedurally valid but strategically harmful.
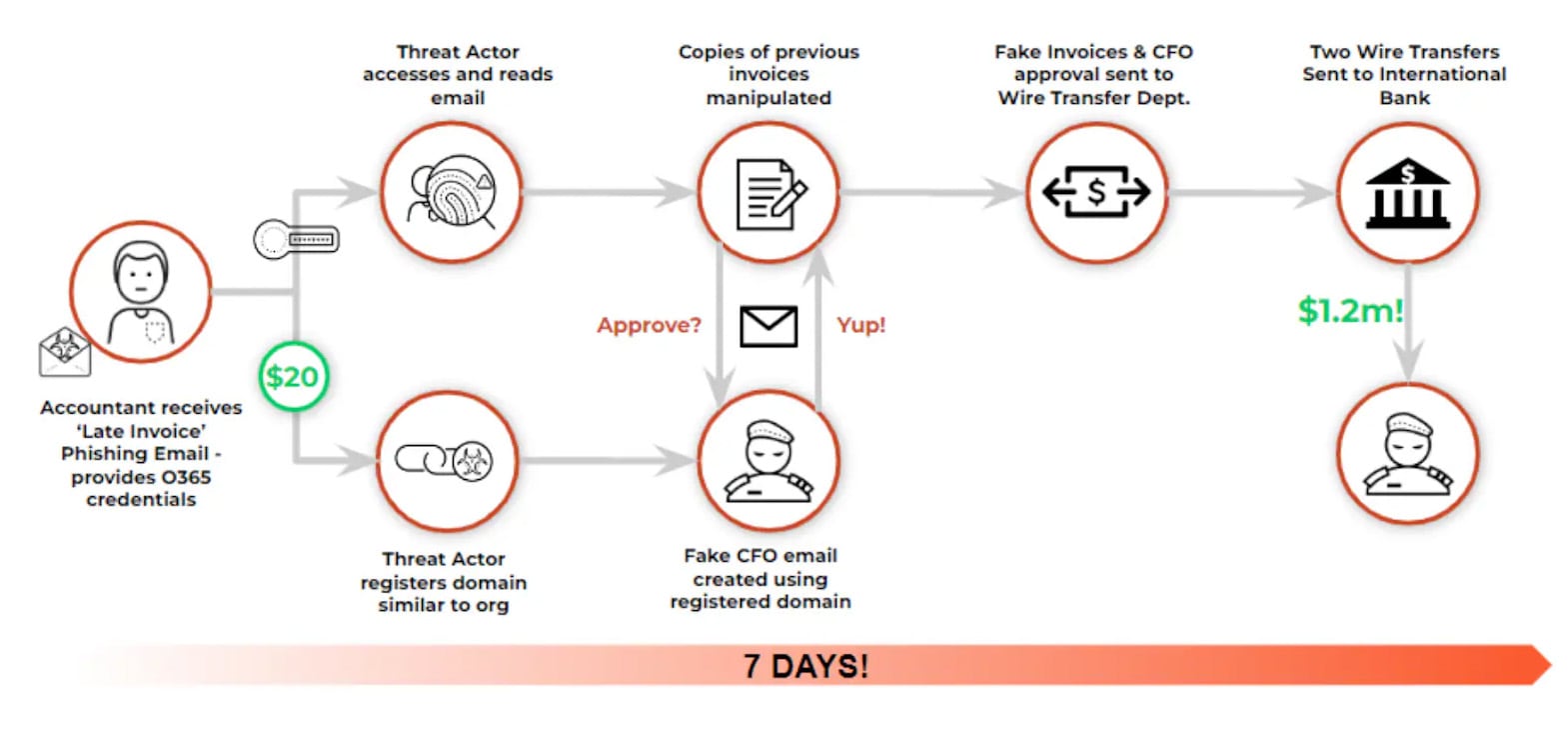
Figure 2: The social engineering blueprint of business email compromise
Progression of a BEC Attack
Reconnaissance and Target Mapping
The attacker profiles the organization. Public data, social media, job postings, breach dumps, and supply chain disclosures reveal who communicates with whom, when, and about what. The goal is to understand reporting lines, recurring transactions, and timing windows.
Initial Access and Credential Harvesting
Entry is often achieved through phishing, password reuse, or third-party compromise. The attacker doesn’t always need inbox access at first. Spoofing domains and display names is often enough to begin engagement while credential attacks continue in parallel.
Internal Observation or Spoofed Engagement
If inbox access is gained, attackers read historical conversations and monitor upcoming transactions. They set forwarding rules, insert inbox filters, and prepare spoofed follow-up messages that match internal tone and cadence.
Payload Execution: Social Engineering, Not Malware
The attacker sends a crafted message — usually mimicking a vendor, executive, or internal approver — requesting a wire transfer, invoice payment, or login credential. The email is timed and phrased to fit the existing workflow.
Execution and Exit
Funds are moved to attacker-controlled accounts, often through multiple intermediaries. The infrastructure used is frequently short-lived and globally distributed. In some cases, attackers remain in the mailbox to repeat the process or pivot to additional targets.
Infrastructure and Tactics Supporting BEC
BEC operations rely on infrastructure that maximizes credibility and minimizes traceability.
- Lookalike domains and typosquatting: Domains that resemble legitimate ones down to the character
- Free or hijacked email services: Gmail, Outlook, or compromised third-party accounts used to maintain distance from attribution
- Email forwarding and inbox rules: Silent redirection of responses to external systems
- HTML injection in messages: Visual manipulation of display names, replies, or metadata
- AI-generated text and tone matching: Language that adapts to the communication style of the person being impersonated
Attackers often avoid detection tools by avoiding links, attachments, and known malware indicators entirely.
Exploited Weaknesses Across the Environment
BEC depends on specific failures across layers of trust and process enforcement.
- Application layer: Lack of sender authentication (e.g., missing or unenforced SPF, DKIM, DMARC) and unrestricted inbox rules
- Identity layer: No MFA on user or admin accounts, or recovery flows that allow takeover with limited verification
- Process layer: Payment workflows that allow email-only approvals, or fail to verify changes in payment destinations
- Human layer: Lack of training on high-risk pretexts and failure to escalate urgent financial requests
The most damaging BEC incidents occur when weaknesses align across these layers, giving the attacker room to maneuver without triggering friction.
Variants in Real-World Campaigns
- Executive impersonation: Posing as a CEO or CFO during travel, requesting urgent wire transfers or document access
- Vendor invoice fraud: Hijacking or spoofing a supplier’s domain to submit updated banking details for a known invoice
- Legal or audit impersonation: Fabricating requests for sensitive data under the guise of regulatory or legal review
- Payroll redirection: Targeting HR or finance teams to reroute employee salary deposits
- M&A deception: Exploiting nondisclosure conditions during active acquisitions to insert fraudulent payment instructions
BEC attacks are operationally simple but procedurally effective. The closer the attacker can get to mimicking real business, the less likely anyone is to question the ask.
Targets of BEC Scams
Threat actors tend to target people with decision-making authority or access to financial information processes.
- Leaders and Executives: These roles are targeted for impersonation, as leaders sometimes have contact information on the company website or their personal LinkedIn page.
- Finance: Whether dealing with internal or external finances, people in roles within Accounts Payable are targeted because of their access to information like banking details and the ability to authorize and send payments.
- Human Resources: HR managers are targeted for information-stealing campaigns because they are near important personal information, such as contact information or social security numbers.
BEC as a Strategic Component in Multistage Attacks
Business email compromise operates as a mid-chain enabler in adversary campaigns. It’s rarely the point of entry, and it’s not the end goal. Instead, BEC provides a pivot point that converts digital access into operational influence. When executed successfully, it allows cybercriminals to bypass authentication controls, policy enforcement, and anomaly detection by working within trusted business logic.
BEC’s low technical profile and high impact make it attractive to both state-aligned groups and financially motivated actors. Its flexibility allows it to function across verticals and across stages of attack progression.
Where BEC Appears in Real-World Kill Chains
BEC usually enters after the attacker has achieved initial access through credential harvesting, phishing, or third-party compromise. In many cases, it follows a successful account takeover, but not always. Spoofing and display-name manipulation can be used to initiate the attack without inbox control.
Once the attacker has embedded into the communication chain, BEC enables:
- Credential escalation, by directing users to reauthenticate on attacker-controlled portals
- Financial redirection, by altering payment instructions during live invoice discussions
- Internal reconnaissance, by reading emails, calendar events, or shared documents for additional access points
- Delegated compromise, by impersonating the victim in downstream interactions with suppliers, partners, or internal approvers
The access gained via BEC also enables lateral movement through delegated credentials, OAuth tokens, or abuse of shared mailboxes and alias groups. If the attacker lands in a privileged mailbox — legal, finance, or executive — BEC becomes a mechanism for high-trust command execution.
Preconditions That Enable BEC
BEC thrives under specific structural weaknesses. The attack itself is flexible, but its success depends on process blind spots and identity drift.
- Federated authentication without uniform MFA enforcement
- Email clients that allow unaudited inbox rules or forwarding
- Finance and HR processes that rely on static email approvals
- Third-party vendors with weaker identity hygiene
- Inconsistent implementation of DMARC, SPF, and DKIM across domains
Where organizations rely on email for transaction validation or authority delegation, BEC becomes not just possible — but expected. Attackers adapt to whatever workflow delivers the least resistance.
How BEC Connects with Other Techniques
BEC doesn’t stand alone. It layers well with social engineering, phishing, credential stuffing, and cloud session hijacking. It often follows a data breach and enables the next.
- Phishing and credential harvesting may be used to compromise the initial account, which is then used for BEC activity
- OAuth abuse often appears after BEC has allowed token access to integrated platforms such as billing or document signing tools
- Cloud-to-cloud pivoting may occur after inbox compromise, leveraging file shares, calendar permissions, and integration APIs to access non-email assets
- Persistence is often achieved through inbox rules, mobile sync tokens, or secondary access methods planted during the BEC phase
BEC is rarely detected in isolation because the attacker’s behavior mirrors the legitimate user’s context. Once inside the business process, BEC becomes a method of invisibly steering decisions that have already passed technical checks.
Use Cases: BEC Campaigns with Measurable Impact
Modern BEC doesn’t exploit email systems. It exploits workflows, timing, and trust. The most successful campaigns align their tactics with how organizations actually operate — through distributed approvals, third-party coordination, and email-first transactions.
Multinational Manufacturing Firm: $25 Million Redirected
In 2023, a European manufacturing conglomerate lost the equivalent of $25 million to a coordinated BEC campaign. The attacker compromised a regional finance director’s mailbox and monitored invoice workflows between the firm and one of its key suppliers.
After identifying a recurring payment schedule, the attacker inserted themselves into a genuine thread using the compromised account. They provided a legitimate-looking PDF with updated banking instructions, registered to an offshore entity. The wire was approved without a callback.
The fraud was only discovered weeks later during routine reconciliation, long after the funds were moved through multiple holding accounts and crypto rails.
Healthcare System: Credential Theft to HIPAA Exposure
The U.S.-based Hospital Sisters Health System (HSHS) disclosed a BEC incident that originated with a phishing email targeting a shared billing inbox. The attacker gained access to internal correspondence with insurers, claim processors, and external legal counsel.
Within two days, inbox rules were created to silently forward new messages containing keywords like “invoice,” “transfer,” or “ACH.” During that time, the attacker exfiltrated patient PII and payer account data. Individuals affected by the 2023 data breach exceeded 882,000.
Though no direct wire fraud occurred, the breach triggered mandatory breach notification under HIPAA and led to a full forensic review of 18 months of email records. The resulting audit and remediation costs exceeded $3 million.
SaaS Payment Platform: Vendor Compromise Cascade
In 2024, the major SaaS billing platform Dropbox Sign suffered a BEC-related compromise after one of its integration partners had credentials exposed in a third-party breach. The attacker used the vendor’s access to impersonate a system administrator, sending routine-looking API key rotation notifications to several enterprise customers.
Two responded with valid credentials, believing the messages were part of a known quarterly rotation process. Those credentials were used to generate session tokens, gain access to sensitive customer data, and push unauthorized billing changes to customer accounts.
The result was a cascade of refund fraud and account manipulation that affected dozens of end customers, forcing the SaaS provider to suspend services temporarily and issue global reset instructions.
$60 Million Lost in Social Engineering-Driven Wire Fraud
Orion S.A., a global specialty chemicals company headquartered in Luxembourg with significant U.S. operations, reported a loss of $60 million due to a sophisticated BEC attack. The event occurred in 2024 after an employee was tricked into making multiple fraudulent wire transfers to accounts controlled by third parties.
Orion S.A.'s filings with the U.S. Securities and Exchange Commission (SEC) indicated that there was no evidence of additional fraudulent activity or unauthorized access to the company's data or systems. This suggests the attack was purely focused on social engineering and manipulating financial processes rather than exploiting technical vulnerabilities.
NSW Government Department: $2.1 Million Redirected via BEC Scam
In late 2024, a New South Wales (NSW) government department in Australia fell victim to a BEC attack, resulting in a $2.1 million AUD loss. Cybercriminals impersonating a legitimate financial institution used email deception to convince government employees to alter payment details, redirecting $2.1 million to attacker-controlled accounts. The breach was discovered after irregularities in payment records triggered internal review.
This incident is part of a broader trend of BEC attacks targeting Australian organizations, including government bodies and businesses. In the 2023-2024 financial year, BEC scams cost Australian companies almost $84 million AUD.
Targeted Industries and Strategic Timing
BEC disproportionately affects finance, legal, real estate, and healthcare — sectors where email often substitutes for workflow tooling. Many incidents occur at quarter-end, during tax season, or while executives are traveling.
Attackers often use social events, public travel plans, or industry-wide reporting deadlines to time their fraud. In many successful cases, the emails were well written, cleanly formatted, and devoid of technical red flags — no links, no attachments, no misspellings.
Operational Metrics That Frame the Threat
- $2.9 billion in adjusted losses attributed to BEC in 2023, per FBI IC3
- 71% of large enterprises surveyed in 2023 reported at least one attempted BEC attack
- Median dwell time of 5 days before the attacker initiates a fraudulent action after inbox compromise
- Less than 8% of incidents are discovered through technical controls — most are uncovered through reconciliation or third-party notification
BEC’s impact doesn’t come from system disruption. It comes from impersonation, misdirection, and precision timing. The organizations hit hardest are often the ones with the most trust distributed through email.
Detecting BEC in Enterprise Environments
Business email compromise doesn’t generate traditional indicators of compromise. There’s no malware hash, no exploit chain, and often no anomalous file activity. Detection relies on recognizing subtle behavior shifts within trusted systems. The challenge is that BEC typically operates within authenticated sessions using legitimate infrastructure.
Identifying BEC requires layering identity signals, message behavior, and access telemetry. Systems must correlate user context with communication patterns to surface misuse that looks authorized at the protocol level but is clearly off-pattern in business logic.
Behavioral Indicators of BEC in Progress
BEC manifests through small deviations in how a user communicates, where they authenticate from, and how quickly privileges shift. Behavioral context often provides the earliest signal.
- Unusual login geography that doesn’t align with historical travel or device patterns
- Inbox rules created without corresponding user behavior (e.g., auto-forward to external addresses, delete if subject contains “invoice”)
- Authentication attempts from consumer cloud services outside of expected business platforms
- Sudden volume of finance-related messages sent from a previously low-volume account
- Emails referencing urgent payments or bank changes during holidays, quarter-close, or M&A events
- Message headers lacking internal routing details, or originating from external relay points with spoofed display names
Attacks often delay active use of compromised accounts for several days, using that time to monitor threads, intercept approvals, and study process cadence.
Technical IOCs Associated with BEC Infrastructure
While BEC rarely uses malware, supporting infrastructure may still leave detectable traces. These indicators don’t point to the BEC payload itself — they signal the infrastructure that makes BEC possible.
- IP addresses originating from VPNs, proxy networks, or cloud compute regions not used by employees
- Domain names mimicking vendors or partners with typos, character substitutions, or additional words
- SPF/DKIM failures on inbound messages that appear to come from internal or trusted addresses
- User-agent strings associated with outdated email clients or headless browser automation
- Login timestamps showing impossible travel or overlapping active sessions on geographically distant nodes
These indicators have limited standalone value but gain power when linked across identity and communication flows.
SIEM and XDR Monitoring Recommendations
Detection must extend beyond mail filters and into behavioral analytics, identity telemetry, and message flow. SIEM and XDR tools should focus on correlation rather than thresholding.
- Track authentication attempts from high-risk geographies or previously unseen IPs, especially those followed by inbox rule creation
- Flag the creation of forwarding or deletion rules within enterprise mailboxes, particularly targeting financial terms
- Monitor for messages where display names match internal users but originate from external domains
- Alert on privilege use anomalies, such as admin portal access from previously non-privileged users
- Correlate payment requests with recent changes in login context or MFA enforcement gaps
- Inspect message reply headers for divergence from original thread participants
Systems should also watch for sentiment and phrasing changes in routine email threads. Sudden shifts in tone, structure, or urgency can signal that a human is no longer in control of the account.
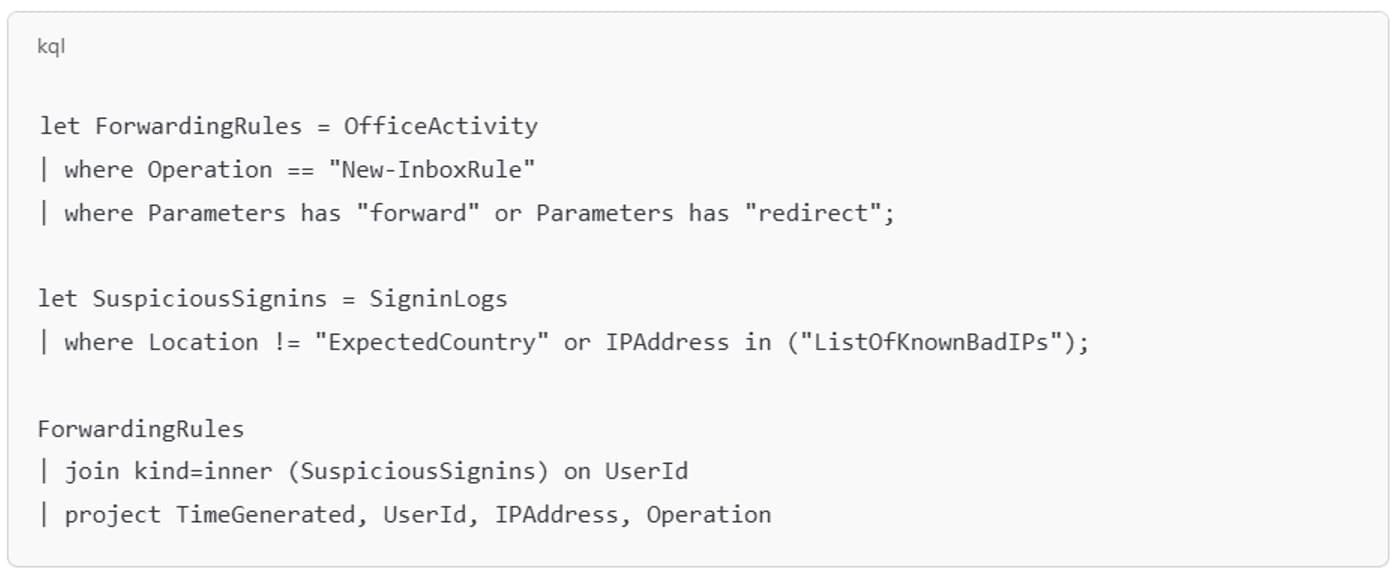
Figure 3: Example KQL Query: forwarding rule + suspicious login correlation surfaces users who created mailbox forwarding rules shortly after signing in from an unusual or high-risk IP address
BEC is a behavioral attack masked by normal infrastructure. Rather than forcing their way in, attackers assume a seat at the table and speak in your voice. Without identity-linked behavioral visibility, they pass unnoticed until they skip away with the money.
Practical Defenses Against BEC at the Identity Layer
Preventing business email compromise starts with hardening the identity plane. The most critical defenses are those that restrict impersonation, disrupt unauthorized session persistence, and validate the legitimacy of communication, not just its syntax.
- Enforce phishing-resistant MFA: Hardware-backed FIDO2 authenticators eliminate the effectiveness of credential-based account takeover. Avoid SMS- or email-based MFA, which is vulnerable to real-time interception and fatigue attacks.
- Apply conditional access policies across all users: Block access based on anomalous geography, unfamiliar devices, or risk scores derived from endpoint posture and behavioral deviation.
- Restrict the creation of inbox rules and forwarding configurations: Use admin-enforced policies to log and block any forwarding to external domains or auto-delete rules based on financial keywords.
- Expire and rotate stale credentials: Service accounts, long-lived tokens, and admin credentials not actively managed become persistent footholds post-compromise.
- Harden federation and SSO implementations: Validate that SAML and OIDC integrations enforce MFA and session constraints uniformly across all apps — not just core services.
Authentication control without visibility is incomplete. Identity signals must be correlated with message behavior and access scope.
Messaging Security and Domain Controls
Attackers often rely on weak sender validation and domain hygiene to spoof internal users or trusted vendors. Message authenticity is a prerequisite for safe automation and reliable human verification.
- Deploy and enforce SPF, DKIM, and DMARC: DMARC enforcement must be set to ‘reject’ for the organization’s primary domains. Monitoring-only configurations leave the spoofing window open.
- Harden MX and SMTP configurations: Block unauthenticated relays, strip external display names mimicking internal addresses, and log failed auth headers for external sender impersonation attempts.
- Validate reply-to domain alignment: BEC messages frequently insert a correct-looking display name with a different reply-to address. Systems should flag and route these for additional review.
- Disallow lookalike domains in internal email traffic: Use domain similarity detection to block or quarantine messages from typo-variant domains that differ by character substitution or prefixing.
Well-formed messages from malicious infrastructure bypass most filtering. That makes domain and header inspection foundational — not optional.
Process Controls That Break BEC Timing
The most effective BEC defenses interrupt the attacker’s ability to exploit urgency, impersonate authority, or redirect funds without secondary verification. These are not technical controls — they’re procedural mandates.
- Enforce callback verification for any change to payment instructions: Require confirmation using a phone number or channel stored independently of the email thread.
- Mandate dual-approval workflows for wire transfers or financial disbursements: One person should never both approve and execute the transaction. Escalations should be logged and time-bound.
- Require out-of-band communication for high-risk decisions: No financial or access change should be approved based solely on email. Use Slack, Teams, or verified callback procedures to confirm.
- Log and monitor all exceptions: Every override of a standard process — manual account update, urgent transfer, invoice override — should trigger automated review.
If the attacker can’t rely on email to execute a decision, they can’t turn BEC into a payout.
User Awareness That Targets Business Logic
Most BEC simulations fail to prepare users because they test link clicking, not trust exploitation. Awareness should mirror real tactics.
- Train on financial impersonation, not malware delivery: Users should be able to recognize tone shifts, domain mismatches, and requests for procedural deviation.
- Target executive assistants, finance, HR, and procurement teams: These roles are BEC focal points. They should receive tailored simulations.
- Reinforce escalation pathways: Make it easy for users to verify an unusual request without penalty or friction. Security fatigue leads to blind acceptance.
User behavior is the final gate. When trained to pause on financial authority delivered through email, users force the attacker into a harder, more detectable position.
Controls That Don’t Work as Advertised
- CAPTCHAs and link scanning: BEC messages typically contain no links or files. These controls add noise without value in BEC defense.
- Basic phishing simulations: Tests focused on misspellings and obvious spoofing don’t reflect the nuance of modern BEC messages.
- Enforcing MFA without phishing resistance: MFA fatigue and token replay can be exploited unless hardware-backed protocols are used.
- Relying on perimeter-based DLP: Most BEC attacks don’t exfiltrate data. They redirect trusted actions internally or outward.
Immediate Response Priorities After a BEC Incident
Responding to business email compromise begins with the assumption that access has already been used to manipulate trust. Recovery depends not just on disabling the attacker’s access, but on identifying what they saw, what they changed, and what decisions they may have influenced. The goal is to cut off access, contain the exposure window, and validate the integrity of any transaction or interaction tied to the compromised account.
Containment Without Delay
Once BEC is suspected or confirmed, the affected user’s session must be revoked immediately. Waiting to “investigate further” gives the attacker more time to operate from within trusted channels.
- Force sign-out of all sessions tied to the compromised identity
- Revoke tokens and API access grants, especially in environments where OAuth or third-party integrations are used
- Reset credentials using a channel that’s out-of-band from the compromised email address
- Temporarily disable external mail flow, or set up header tagging to alert recipients of elevated risk
- Preserve mailbox state before making changes. Every inbox rule, deleted item, or calendar invite is evidence. Forensics depends on a complete view of attacker behavior.
Containment should focus on halting attacker operations while preserving the forensic trail for later validation.
Eradication Requires Full Credential Hygiene and Visibility
Eradication isn’t just about disabling the known entry point. It’s about neutralizing every method the attacker may have used to maintain or regain access.
- Scan for malicious inbox rules, forwarding configurations, or filters that may allow silent surveillance
- Audit external message headers and verify reply chains involving financial, legal, or executive conversations
- Review sign-in logs for geographic and timing anomalies that may indicate shared or secondary account compromise
- Check for linked services, including cloud storage, calendars, or collaborative platforms where the same credentials may provide access
- Identify all recipients of attacker-sent messages and validate that no instructions were followed, funds transferred, or credentials provided
Eradication ends when there are no residual channels for communication, command execution, or visibility.
Internal and External Communication Strategy
The longer BEC remains hidden, the greater the operational and reputational impact. Internal alignment and external notification must run in parallel with technical response.
- Notify legal and compliance teams immediately to determine disclosure obligations and reporting timelines
- Engage finance and procurement leaders to validate all transactions, especially those involving account updates or invoice rerouting
- Communicate to employees whose mailboxes were compromised or who received messages from attacker-controlled accounts
- Inform customers, partners, or vendors who were engaged in compromised threads, especially where trust in instructions was assumed
Clarity and speed are essential. Communicate with precision, and document the timeline of events for both legal and strategic review.
Teams and Tools That Should Be Activated
Response coordination should span technical, operational, and executive layers. Organizations should already have these roles integrated into the response plan.
- Security operations teams, to manage threat hunting and log correlation
- IT administrators, to revoke access, harden configurations, and assist in session management
- Legal counsel and privacy officers, to interpret breach implications and draft disclosures
- Finance leadership, to suspend or review impacted payments and prevent further losses
- Digital forensics and incident response (DFIR) partners, when internal telemetry is insufficient or tampering is suspected
The faster these teams are mobilized, the narrower the attacker's window to cause harm.
Post-Incident Review and Security Hardening
Recovery ends with confidence — not only that the attacker is gone, but that the path they took no longer exists.
- Map the entire attacker timeline, from initial access to message delivery, and identify every system they touched
- Validate authentication controls, ensuring MFA, conditional access, and token expiration policies are enforced across all accounts
- Retest workflows, especially those used to approve payments, request credentials, or initiate account changes
- Update playbooks and response protocols, incorporating lessons learned into tabletop exercises and live readiness drills
- Refine telemetry visibility, ensuring mail system logs, identity provider logs, and third-party integrations feed into central detection platforms
Hardening after a BEC incident is about more than preventing recurrence. It’s about eliminating the gap between visibility and action so the next attacker is seen before they speak.
Why BEC Is a Board-Level Concern
Consider the financial, regulatory, and strategic implications that cascade beyond the compromise. BEC must be made a board-level concern.
Risk Prioritization in Enterprise Contexts
BEC should be scored as a high-probability, high-impact threat across all verticals. Unlike ransomware or denial-of-service, which produce immediate disruption, BEC results in silent losses. The adversary leverages the organization’s processes against itself.
Risk scoring frameworks — such as FAIR or MITRE’s Engage — place BEC at the intersection of data integrity, financial loss, and third-party risk. Impact calculations must account for:
- Value and volume of recurring financial transactions conducted over email
- Scope of third-party relationships where email-based approval is the default
- Identity sprawl across federated cloud apps with inconsistent MFA enforcement
- Legal sensitivity of communications processed through email platforms
The threat is persistent. It’s adaptive. And it targets people who are rarely monitored with the same rigor as infrastructure.
Regulatory and Compliance Exposure
A successful BEC incident often triggers regulatory thresholds even when no data is exfiltrated. Laws prioritize outcome and exposure — not whether malware was involved.
- GDPR: If attacker-controlled email accounts expose or redirect PII belonging to EU subjects, a breach notification may be required within 72 hours under Article 33.
- HIPAA: Any compromise involving healthcare-related inboxes that contain PHI constitutes a reportable breach, regardless of whether the email was read or altered.
- CCPA: Even without a data breach, if attackers used compromised email threads to mislead California consumers, legal scrutiny applies under deceptive business practices.
- PCI DSS: While BEC typically doesn’t target payment card data directly, any misuse of email leading to payment rerouting or fraud involving stored cardholder data can raise compliance flags.
Legal risk multiplies when incident response or vendor relationships reveal that the organization failed to enforce basic controls — such as MFA, domain validation, or payment verification protocols.
Long-Term Reputational Damage and Platform Trust
The impact of BEC doesn’t end when funds are recovered or accounts are reset. The longer-term damage centers on lost confidence in internal communications, supplier trust, and digital workflows. Vendors may start second-guessing every invoice. Customers may no longer trust that support emails originate from the organization. Employees may hesitate to approve routine financial requests without offline validation, eroding business agility.
Platform reputation also takes a hit. If attackers compromise a vendor’s domain and use it to launch secondary BEC attacks downstream, the affected vendor becomes a liability to its ecosystem.
The strategic risk of BEC isn’t tied to how much money is lost. It’s tied to how trust gets redefined once an attacker has impersonated your voice from inside your system. Organizations that treat BEC as a workflow risk are better positioned to recover trust and maintain platform integrity over time.
Business Email Compromise FAQs
Vendor email compromise (VEC) is a subtype of BEC where attackers gain access to or impersonate a supplier’s email account to defraud customers. Once embedded, the attacker monitors invoice workflows and intercepts payment-related conversations, often modifying bank account details in legitimate-looking PDF invoices. Because the message appears to come from a known and trusted party, recipients often don’t question the update. VEC exploits trust between organizations rather than just within them.
Inbox rule abuse refers to the creation of automated rules within a compromised email account to hide, forward, or delete specific messages. Attackers use these rules to suppress responses that might alert the victim, redirect messages to external inboxes, or filter messages by keywords such as “invoice,” “wire,” or “urgent.” These rules allow persistence and visibility even after the user has resumed control of the account.
Session hijacking is a technique where an attacker gains unauthorized access to a valid user session, often by stealing a session token or cookie. In the context of BEC, this allows the attacker to bypass credential and MFA requirements entirely, taking over an active session without needing to log in. Common sources of session hijacking include man-in-the-middle attacks, token theft via malware, or harvesting through compromised browsers and cloud apps. Once hijacked, the attacker can impersonate the user, send emails, access files, and engage in BEC activity without triggering new authentication events.
MFA fatigue is a social engineering tactic that exploits push-based multi-factor authentication systems. Attackers repeatedly trigger MFA notifications to a user’s device — often dozens or hundreds of times — hoping the user will approve one out of annoyance, distraction, or assumption that the prompt is legitimate. It's commonly used in tandem with stolen or guessed credentials. Once the user accepts the prompt, the attacker is granted access without needing to bypass the MFA system itself. MFA fatigue has become a key enabler of BEC and account takeover in environments where weak MFA methods are deployed.
Phishing typically involves mass-distributed emails designed to steal credentials or deliver malware. BEC is more targeted and operational. It leverages either credential compromise or identity spoofing to impersonate trusted individuals, with the goal of manipulating internal workflows, rerouting payments, or accessing sensitive data. While phishing may initiate a BEC chain, the execution phase of BEC involves no payload — just social engineering within the bounds of legitimate systems.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication protocol that builds on SPF and DKIM to prevent domain spoofing. When set to “reject,” it tells receiving mail servers to block unauthenticated messages that appear to come from your domain. Without DMARC enforcement, attackers can spoof your brand’s domain in BEC campaigns without triggering message delivery failures or alerts.
Financial pretexting is the act of fabricating a scenario to manipulate someone into transferring funds or disclosing payment credentials. In the context of BEC, it often involves fake invoices, fabricated acquisitions, or urgent requests for vendor payment redirection. Unlike general phishing, the attack is structured around a believable financial event and often includes supporting documentation to increase legitimacy.