- What Are Types of Business Email Compromise (BEC) Scams?
-
What Is Business Email Compromise (BEC)?
- Business Email Compromise Explained
- Mechanics Behind Business Email Compromise
- BEC as a Strategic Component in Multistage Attacks
- Use Cases: BEC Campaigns with Measurable Impact
- Detecting BEC in Enterprise Environments
- Practical Defenses Against BEC at the Identity Layer
- Why BEC Is a Board-Level Concern
- Business Email Compromise FAQs
What Are Business Email Compromise (BEC) Tools and Technologies?
There are two main categories of tools and technologies related to business email compromise (BEC) scams, both relying on automation, artificial intelligence (AI), and machine learning (ML) to enhance their effectiveness.
The first category includes the tools and technologies used by the scammers who execute these attacks, while the second encompasses the tools and technologies employed by cybersecurity teams to prevent such incidents.
These tools work together to protect organizations from email-based threats by:
- Identifying malicious emails before they reach employees
- Educating users on how to spot and avoid phishing scams
- Ensuring sensitive data remains protected and uncompromised
- Responding quickly to suspected incidents to minimize damage
By combining these tools and technologies, organizations can significantly reduce the risk of falling victim to BEC attacks.
What Is Business Email Compromise (BEC)?
Business email compromise is a type of cyberattack that uses social engineering, artificial intelligence, machine learning, spoofing, spear phishing, and other technologies to trick employees into taking actions that can compromise their organizations.
BEC attacks are incredibly dangerous due to the advanced tools and technologies employed by scammers to make their emails appear authentic and legal. These attacks pose a significant threat to businesses as they can cause substantial financial harm, costing companies billions of dollars.
Tools and Technologies Used by BEC Scammers
BEC scammers have long relied on familiar tactics like phishing and email spoofing. However, advancements in automation, AI, and ML advancements have elevated these methods, enabling attackers to deploy them with remarkable speed and effectiveness.
BEC attacks have become increasingly sophisticated, with scammers exploiting shifts in work culture, such as remote and hybrid environments, to target more vulnerable employees. By leveraging AI, ML, and social engineering, attackers now craft highly authentic and deceptive emails, making it easier to deceive victims.
Using advanced technologies, attackers can target victims with exceptional precision and deploy attacks on an unprecedented scale, making the tools and techniques behind BEC scams more potent than ever. Below are some primary tools and technologies commonly used in BEC attacks.
Email Spoofing Software
Scammers use this software to manipulate email header information and make their emails appear as if they come from a trusted source. By altering the "From" address and other details, scammers can deceive recipients into believing the email is legitimate.
Phishing Kits
These pre-packaged tools enable scammers to create and distribute authentic-looking phishing emails. Phishing kits often include templates that mimic the look and feel of legitimate emails from well-known organizations, making it easier for scammers to trick their targets.
Social Engineering Techniques
Scammers use various social engineering tactics to manipulate individuals into divulging confidential information. They might pose as company executives or IT personnel to trick employees into revealing passwords or transferring funds.
Malware and Keyloggers
Some BEC attacks involve malware or keyloggers that are covertly installed on a victim's computer. These tools capture keystrokes, allowing scammers to gain access to sensitive information like login credentials and financial data.
Credential Harvesting Tools
BEC attackers often use tools designed to collect and store credentials obtained through phishing or malware. These tools can store large amounts of data, which scammers can later use or sell.
Fake Domain Registration
Scammers frequently register domain names that are slight variations of legitimate company domains. These fake domains are used to send deceptive emails that appear from a genuine source but are part of a BEC scheme.
Caller ID Spoofing for Vishing
BEC scammers use vishing (voice phishing), where they spoof caller IDs to make phone calls appear as if they're coming from a trusted number within the organization or from a known business partner.
Automated Scripts
Scammers may use automated scripts to send phishing emails in bulk. These scripts can personalize emails with the recipient’s name or other details, making the scam more convincing.
Proxy Servers and VPNs
BEC scammers often use proxy servers or VPNs to hide their location and evade detection. This makes it more difficult for authorities to trace the scam back to its source.
Deepfake Technology
Advanced scammers employ deepfake audio or video technology to create realistic simulations of a person’s voice or appearance, typically a senior executive, to request fraudulent transactions or sensitive information.
Tools and Technologies to Mitigate BEC Risk
As automation, artificial intelligence, and machine learning enhance the sophistication of business email compromise attacks, they also improve the effectiveness of tools and technologies designed to prevent such attacks.
Security operations centers (SOCs) are becoming more resilient with the integration of AI and automation, providing analysts with better tools to prioritize alerts effectively. Furthermore, traditional technologies, including email filtering tools and endpoint protection platforms, benefit from AI and machine learning advancements.
The primary tools and technologies cybersecurity teams use to mitigate risks and reduce potential damages from BEC attacks include:
Email Authentication Protocols (SPF, DKIM, DMARC)
These are fundamental tools for validating email authenticity. They help ensure that emails are sent from legitimate sources and have not been altered in transit, which is crucial in preventing email spoofing and phishing.
Advanced Email Filtering Solutions
These systems employ various techniques, including AI, to identify and block phishing emails and suspicious attachments. They can analyze email content, sender reputation, and other behavioral patterns.
Endpoint Protection Platforms (EPP)
EPPs prevent malware infections that could lead to credential theft. They often include antivirus, anti-malware, and personal firewalls. They can integrate AI-driven behavioral analysis to detect and block suspicious activities on endpoints.
User and Entity Behavior Analytics (UEBA)
UEBA tools leverage AI to analyze user behavior and detect anomalies, such as unusual access patterns or large file transfers, that could indicate a compromised account.
Next-Generation Security Operations Center (SOC)
A next-generation SOC integrates advanced technologies like AI and ML for proactive threat hunting and incident response. This approach can quickly identify and respond to BEC attempts, reducing attackers' time to cause harm.
Zero Trust Framework
Implementing a Zero Trust security model ensures that access to sensitive data and systems is strictly controlled and monitored, reducing the chance of unauthorized access through compromised email accounts.
Security Awareness Training
Ongoing training is essential, including tools that provide continuing education and training for employees about the latest BEC tactics, phishing schemes, and best practices for email security. These programs often include simulated phishing campaigns to test and reinforce employee awareness.
Multi-Factor Authentication (MFA)
MFA is a key security measure that adds an extra layer of protection. It ensures that attackers still need a second verification form to access accounts even if login credentials are compromised.
Secure Email Gateways (SEGs)
SEGs are deployed to inspect incoming and outgoing emails for malicious content and anomalies. They provide features like anti-malware scanning, URL filtering, and data loss prevention (DLP).
Incident Response Platforms
These platforms facilitate the quick detection, investigation, and remediation of security incidents, including BEC attacks. They often include automated workflows and integrate with other security tools for a coordinated response.
Threat Intelligence Platforms
These platforms gather and analyze data on current cyberthreats, including BEC tactics. They provide insights that help update and fortify cybersecurity strategies against emerging threats.
Cloud Access Security Brokers (CASBs)
CASBs provide visibility into cloud-based applications and services in organizations that use cloud services heavily. They help monitor suspicious activities that could indicate a BEC attack, like unauthorized access to cloud email services.
Platform Model for Cybersecurity
A platform-based approach to cybersecurity ensures integrated and comprehensive protection across all levels of an organization’s digital infrastructure. This integration is key in BEC prevention, allowing for coordinated defense mechanisms and streamlined threat responses.
The Role of the Dark Web in BEC
The dark web gives scammers easy access to tools and technologies for business email compromise attacks. Cybercriminals can find user-friendly phishing kits, malware, and email spoofing software, allowing even those with limited technical skills to launch sophisticated attacks.
Additionally, the dark web serves as a platform for exchanging stolen data, including email addresses, passwords, and other sensitive information. BEC attackers can utilize this data to create more targeted and convincing phishing emails.
It also offers services like VPNs, proxy servers, and other methods to mask identities and locations, providing security for scammers. This anonymity fosters a collaborative environment among cybercriminals, who share tactics, techniques, and experiences to refine their methods and continually evade detection.
How to Use BEC Tools and Technologies for BEC Prevention
Best practices for utilizing BEC tools and technologies for security measures extensively use automation, AI, and ML while emphasizing ongoing monitoring, advanced threat detection, training, and awareness (for employees and cybersecurity teams), and an integrated platform model consolidating tools and cybersecurity management.
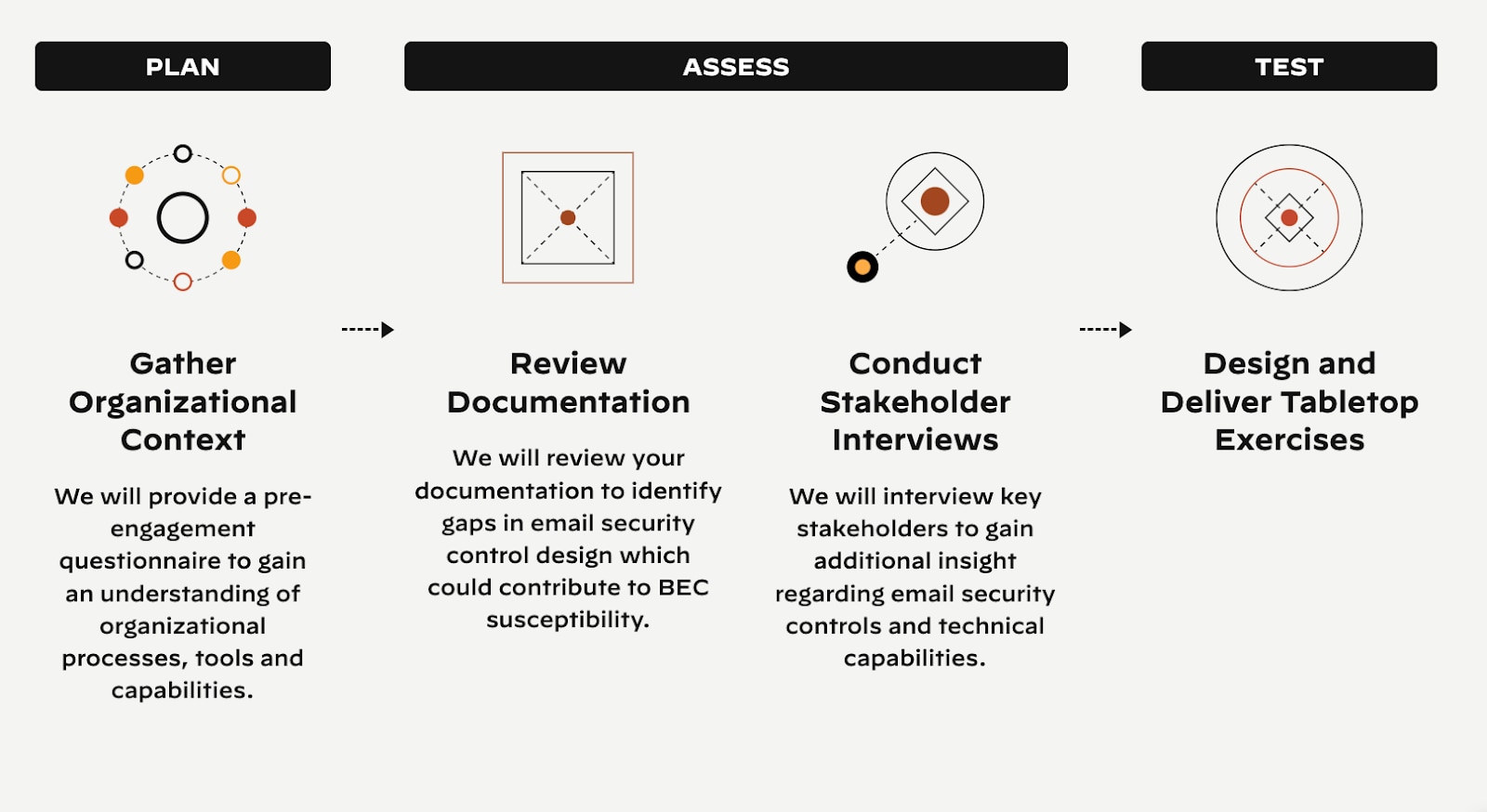
An Integrated Security Approach
Utilize a cohesive combination of tools like email filters, endpoint protection, and security operations centers. Ensure these systems communicate and share intelligence for a more comprehensive defense. Consolidate tools wherever possible.
Regularly Update and Configure Security Systems
Keep all cybersecurity tools updated to protect against the latest threats. Configure email authentication protocols (SPF, DKIM, DMARC) and secure email gateways to block malicious emails.
Leverage AI and Machine Learning Extensively
Implement AI-based tools for advanced threat detection and behavioral analysis. These systems identify anomalies and patterns indicative of BEC attacks more efficiently than traditional methods. Use AI, ML, and automation extensively in SOCs to simplify analysts' work and ease pressure while there is a severe shortage of skilled cybersecurity personnel.
Ongoing Employee Education and Training
Regularly train employees on the latest BEC tactics and general cybersecurity awareness. Use simulated phishing exercises to reinforce training and assess the effectiveness of employee knowledge. These tools and techniques are essential for remote and hybrid employees, representing a growing target for BEC scams.
Zero Trust
Adopt a Zero Trust security model, which assumes that threats can originate from anywhere and require verification at every stage of digital interaction. This approach is vital in mitigating the risk of internal threats and compromised accounts.
Proactive Monitoring and Response
Utilize next-generation SOCs for continuous monitoring and swift response to potential threats. Establish clear procedures for responding to suspected BEC incidents.
Regular Audits and Compliance Checks
Conduct regular security audits to assess the effectiveness of current security measures and ensure compliance with relevant cybersecurity standards and regulations.
Incident Response Planning
Develop and regularly update an incident response plan with protocols for responding to BEC attacks. This should involve coordination across different departments and clear communication strategies.
Evolve to a Platform Model for Cybersecurity
Integrate cybersecurity tools into a unified platform for better threat visibility and coordinated response. This approach ensures that security policies are uniformly applied across the organization.
Data Backups and Recovery Plans
Maintain regular backups of critical data and establish a robust disaster recovery plan. This reduces the risk of data loss in the event of a successful BEC attack.