- What Is Data Security? [Definition, Overview, & Why It Matters]
- DSPM Market Size: 2025 Guide
- How DSPM Is Evolving: Key Trends to Watch
- Top Cloud Data Security Solutions
- What Is Data Risk Assessment?
- What Is a Data Leak?
- Data Security Policies: Why They Matter and What They Contain
- What Is Data Loss Prevention (DLP) Compliance?
- What Is Data Encryption?
- What Is Data Storage?
- What Is Database Security?
- What Is Cloud Data Loss Prevention (DLP)?
- What Is a Data Lake?
- What Is a Data Warehouse?
- What Is Shadow IT?
- What Is an Insider Threat?
- What Is Data Sprawl?
What Is a Data Security Platform?
A data security platform refers to a comprehensive suite of tools and processes designed to safeguard sensitive information and maintain data integrity within cloud-based systems. The platform typically includes advanced encryption methodologies, access control mechanisms, and continuous monitoring capabilities to detect and mitigate potential threats.
Data Security Platform Explained
Organizations are moving their data to digital formats and storing it in cloud environments. This increases the risk of data breaches and security incidents increases. A data security platform protects sensitive data from unauthorized access, theft, loss, failure to comply with data protection regulations, and other security threats.
Key components of an effective cloud data security platform encompass data classification, data loss prevention (DLP), and seamless integration with existing security infrastructure. By implementing such a platform, organizations can ensure that critical data remains protected in their increasingly complex cloud ecosystem, while adhering to strict regulatory compliance requirements and industry best practices.
Key Features of a Data Security Platform
A data security platform aims to safeguard sensitive information from unauthorized access, theft, and malicious attacks while ensuring that business continues uninterrupted. The platform secures data in various forms, such as databases, applications, and cloud storage. The platform is also configurable and scalable to accommodate an organization's evolving needs.
- Data discovery and classification to identify sensitive data across the IT ecosystem and appropriately classify it based on its contents.
- Encryption to secure sensitive data both at rest and in transit.
- Access control to define who can access the data and what they can do with it.
- Data detection and response (DDR) to identify potential security threats and respond in real time.
- Data loss prevention (DLP) to prevent accidental or intentional loss of sensitive data.
- Compliance management to meet various regulatory requirements and standards.
- Identity and access management (IAM) to manage user identities and control access to resources.
- Data security posture management(DSPM) provides visibility into the data layer and handles identifying sensitive data, and monitoring risk, using static risk analysis that pinpoints sensitive and business-critical information at risk based on the data context.
- Audit and reporting to provide a complete record of activities related to date security for compliance and analysis purposes.
A data security platform should work with other IT security platforms. These might be firewalls, intrusion detection systems, and identity and access management solutions. This provides a comprehensive and layered approach to data security.
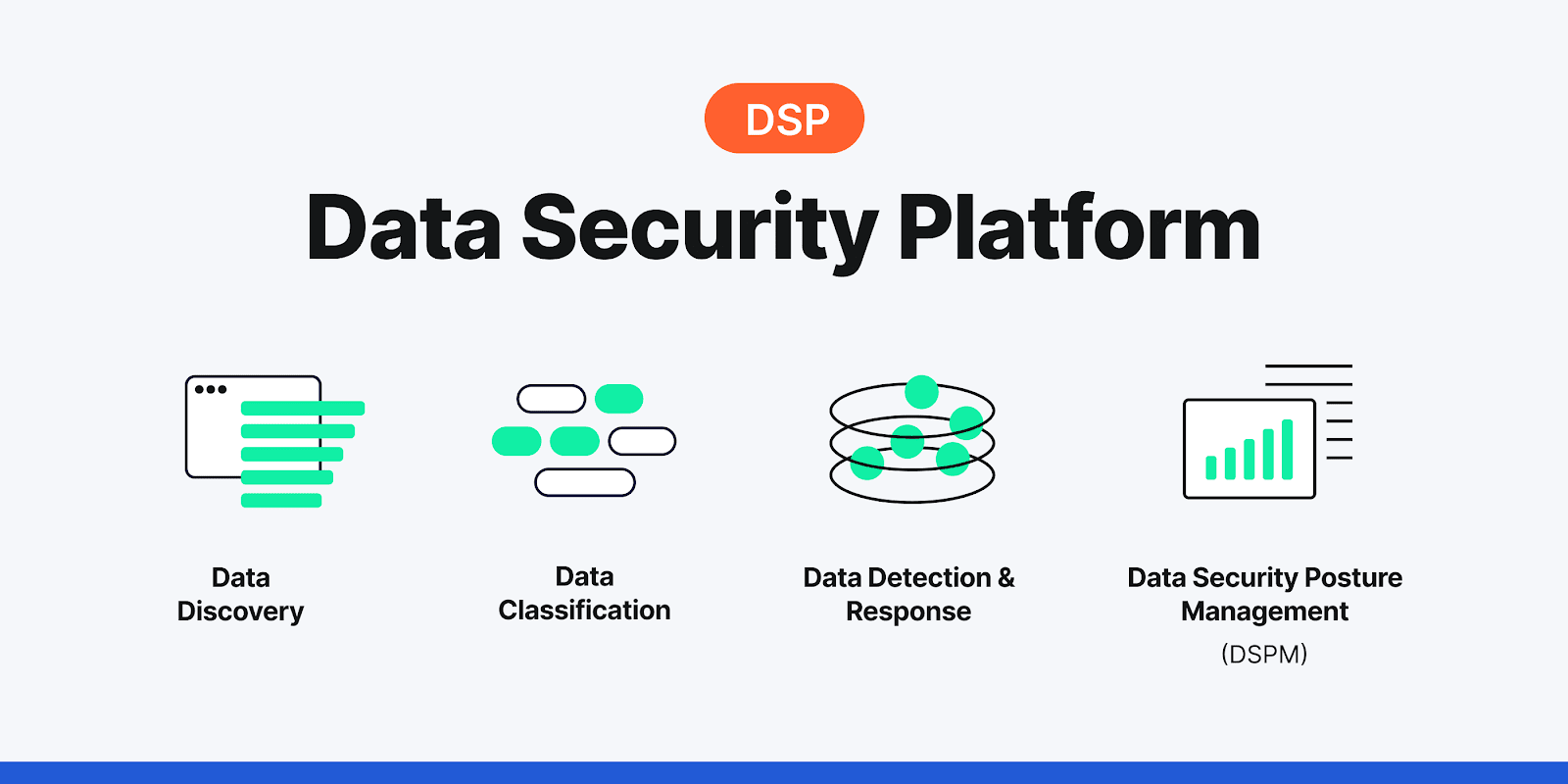
Figure 1: Primary components of a data security platform.
How a Data Security Platform Solves the Complexity of Data Protection
A data security platform integrates data from various sources to provide a holistic view of the security environment. This unified data helps identify potential threats and risks. It also provides a better understanding of the context in which security events occur.
The platform offers visibility into all aspects of the security environment, including user activity, network traffic, and system logs. This allows businesses to monitor and track security events, identify anomalies, and promptly respond to potential security threats.
Data security platforms also provides:
- Centralized management of security measures
- Consistency across the organization and minimizing the risk of security breaches
- Ability to better assess and address security posture
A Data Protection Platform Reduces Risk
Cloud compromises cost organizations 3.5% of their revenue in a year. A data security platform reduces risk by providing a comprehensive and integrated solution to security challenges. It integrates data from various sources. This integration helps security teams to identify potential threats and risks and to understand the context in which security events occur.
- Managing Cloud Security: A data security platform can secure sensitive data stored in multi-cloud environments. This includes public clouds and private clouds.
- Mitigating Data Loss: A data security platform can implement DLP policies and monitor access to data.
- Stopping Data Theft: As more data is stored in cloud environments and on mobile devices, the risk of data theft increases. A data security platform prevents data theft with DDR by monitoring for data-related events and responding when an event could lead to data theft. It also implements other security measures to prevent theft and protect data from falling into the wrong hands.
- Meeting Compliance Mandates: A data security platform implements security measures that comply with mandates, such as GDPR, HIPAA, and PCI DSS.
- Find And Eliminate Active Threats: Detecting security incidents and violations, such as data breaches and unauthorized access, and alerting administrators. This helps security teams respond more quickly to security threats and reduce the impact of security incidents.
Benefits of a Data Protection Platform
The benefits of a data platform far outweigh the costs. Leveraging a data security platform provides significant business benefits and security benefits. Here is a comparison of these benefits:
Business Benefits of Platform Security
- Improved efficiency. A data security platform integrates multiple security measures and technologies into a single, comprehensive solution. This reduces the need to manage multiple-point solutions and improves efficiency.
- Enhanced compliance. Organizations must comply with various data protection regulations, such as GDPR, HIPAA, and PCI DSS, along with internal data governance. A data security platform helps meet these requirements, which can reduce the risk of financial penalties and legal liability.
- Improved reputation. Data security is customer service. The security of customer profiles or unified customer data is more important today than it was ten years ago. Businesses can improve their reputation and build trust with customers, partners, and other stakeholders.
- Informed Decisions. A data security platform provides visibility into who is accessing their sensitive data, when, and from where. This information can be used to improve security and make informed business decisions.
Platform Security Benefits
- Improved data security. A data security platform ensures encryption, access controls, implements monitoring and other security measures. This helps protect their sensitive data from unauthorized access, theft, loss, and other security threats.
- Minimized risk. A data security platform implements a comprehensive and layered approach to data security based on the classification of the data and its context. This helps minimize the risk of data breaches and security incidents, which reduces the potential for financial and reputation damage.
- Enhanced threat detection. A data security platform monitors access to data and alerts administrators when there are security incidents or violations. Doing this helps organizations detect and respond to security threats more quickly.
- Improved business continuity. A data security platform helps maintain business productivity during a data loss incident or other security events. This reduces risk and improves resilience.
Data Security Platform FAQs
DLP systems are a set of tools, processes, and policies designed to prevent unauthorized use, transfer, or theft of sensitive data. These systems work by identifying sensitive information, monitoring data access and usage, and enforcing data protection policies.
DLP solutions can be deployed across various environments, including on-premises, cloud-based, and endpoint devices. Key components of DLP systems include data classification, policy management, monitoring and control, and incident response. By implementing DLP systems, organizations can safeguard against data breaches, maintain regulatory compliance, and reduce the risk of unauthorized data exposure.
Data protection regulations are legal frameworks that mandate how organizations must handle and secure sensitive information, particularly personal data. These regulations aim to protect individuals' privacy and ensure that their data isn’t misused or compromised.
Examples of data protection regulations include the General Data Protection Regulation (GDPR) in the European Union, the Health Insurance Portability and Accountability Act (HIPAA) in the United States, and the Payment Card Industry Data Security Standard (PCI DSS) for handling credit card information.
Compliance with data protection regulations often requires organizations to implement appropriate security measures, such as data encryption, access control, and data loss prevention solutions, to safeguard sensitive data. Failure to comply with these regulations can result in significant fines, legal consequences, and reputational damage.
Threat intelligence is the collection, analysis, and dissemination of information about existing and emerging cybersecurity threats, such as malicious IP addresses, domains, and URLs, as well as the tactics, techniques, and procedures (TTPs) employed by threat actors. This intelligence enables organizations to proactively detect, prevent, and respond to potential cyberattacks by informing security teams about known threats, vulnerabilities, and attack patterns.
Threat intelligence can be derived from various sources, including open-source intelligence (OSINT), industry-specific threat feeds, and commercial providers, allowing organizations to enhance their overall security posture and make informed decisions about their cybersecurity strategy.