-
- Why Cybersecurity Matters: An Enterprise Risk
- Key Principles of a Layered Defense
- Core Domains of Cybersecurity (Types of Security)
- Understanding the Threat Landscape
- Industry-Specific Cybersecurity Challenges
- The Dual Role of AI
- The Acceleration of AI-Driven Threats
- Cybersecurity Best Practices
- Cybersecurity Frameworks and Standards
- The Cybersecurity Workforce
- Cybersecurity FAQs
Table of contents
-
What Is Cybersecurity Platformization?
- Cybersecurity Platform Consolidation: An Overview
- Benefits of Security Tool Consolidation
- How AI Enhances Cybersecurity Consolidation
- Selecting the Right Consolidation Strategy
- Aligning Investments with Business Goals
- Challenges in Platformization
- Future Trends in Cybersecurity Platform Consolidation
- Cybersecurity Platformization FAQs
-
4 Ways Cybersecurity Automation Should Be Used
- Cybersecurity Automation Explained
- Cybersecurity Automation Use Cases: Four Key Areas
- How Cybersecurity Automation Works
- Benefits of Automating Your Security Operations
- The Critical Role of Human Oversight
- Challenges and Best Practices for Implementation
- How Automation Stops the Attack Lifecycle
- Cybersecurity Automation FAQs
-
What Is a Cybersecurity Risk Assessment?
- Cybersecurity Risk Assessment Explained
- Why Is Cyber Risk Assessment Important?
- Common Cybersecurity Risks and Threats
- Different Approaches to Cyber Risk
- How to Perform a Cybersecurity Risk Assessment
- Determine the Scope of the Assessment
- Cybersecurity Risk Assessment Benefits
- Cyber Risk Assessment FAQs
- What is Cybersecurity for Small Businesses?
What is Cybersecurity?
5 min. read
Table of contents
Cybersecurity is the practice of protecting digital systems, networks, cloud environments, and data from unauthorized access, misuse, or disruption. It’s a constantly evolving discipline that integrates technology, policy, and human expertise to defend the confidentiality, integrity, and availability of critical assets across the modern digital landscape.
Key Points
-
Holistic, layered defense: People + process + technology, spanning endpoint, network, cloud, application, data, and identity. -
Guiding principles: Confidentiality (keep data private), Integrity (keep data accurate), Availability (keep services reliable). -
Zero Trust by default: Continuous verification and least-privilege access limit lateral movement after compromise. -
AI’s dual role: Accelerates defense (automation, behavioral analytics) and offense (faster phishing, polymorphic malware). -
Human factor dominates: Social engineering and credential abuse remain leading initial access vectors. -
Broad scope: Core domains include Network, Cloud, Endpoint, Application, Data/Information, Identity & Access Management (IAM), Mobile, OT/ICS & Critical Infrastructure, and AI Security.
Why Cybersecurity Matters: An Enterprise Risk
Cybersecurity is no longer just an IT issue—it’s a business survival requirement and an enterprise risk that directly impacts continuity and reputation.
The Financial and Operational Impact
Today’s cyber threats are more frequent, sophisticated and financially devastating. Attackers exploit automation, AI, and supply-chain vulnerabilities, often halting operations and eroding trust.
- Average Breach Cost: The average global cost of a data breach is approximately $4.44 million, with the U.S. average often exceeding $10 million due to higher regulatory penalties and response costs.
- Operational Downtime: Unplanned outages can cost organizations an average of $14,000 per minute.
- Reputational Damage: Beyond direct costs, companies spend months rebuilding trust with customers and partners, often seeing sharp drops in customer retention and market valuation.
- Regulatory fines: Noncompliance with GDPR, HIPAA, and similar frameworks can incur multi-million-dollar penalties.
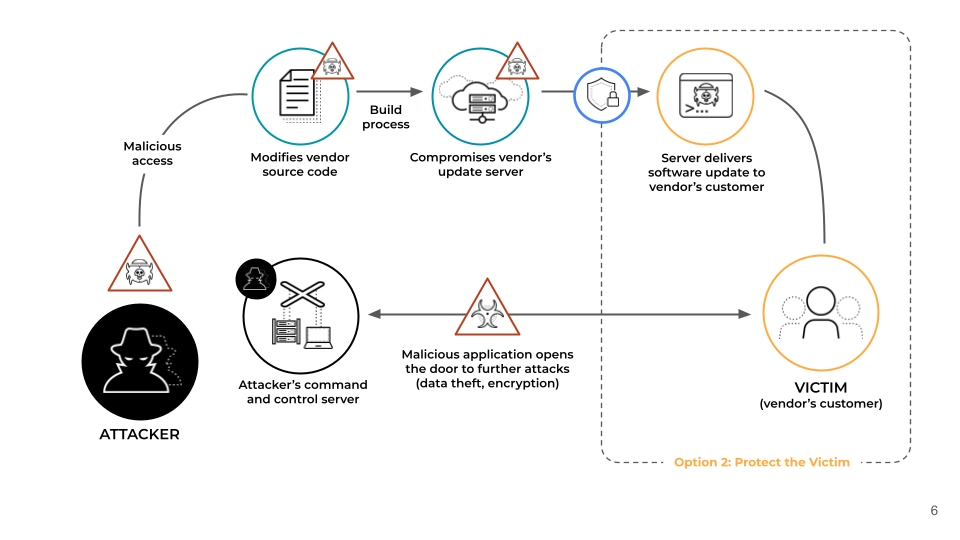
Figure 1: Anatomy of a Supply Chain Attack
The Small Business Crisis
While global enterprises dominate headlines, small and midsize businesses (SMBs) are the most frequent victims, often representing easy targets due to limited budgets and a false sense of security.
- Target Ratio: 43% of all cyberattacks target SMBs.
- The Ultimate Cost: Nearly 1 in 5 SMBs that suffer a breach close permanently within six months.
Key Principles of a Layered Defense
Effective cybersecurity is fundamentally about risk management, combining preventive controls with detection and response mechanisms. It operates on a principle called Defense in Depth, which uses multiple, overlapping layers of protection.
1. The CIA Triad: Guiding Principles
These three principles define every effective security strategy:
- Confidentiality: Ensuring only authorized users can access sensitive data.
- Integrity: Guaranteeing that data and systems remain accurate and unaltered.
- Availability: Maintaining system uptime and accessibility even during attacks or outages.
2. The Zero Trust Framework
The shift to cloud and remote work has made the traditional network perimeter obsolete. Zero Trust is the modern response:
- Mandate: "Never trust, always verify" for every user, device, and application.
- Continuous Verification: Access is not granted just once; it is continuously authenticated based on context and risk posture.
- Least Privilege Access (LPA): Users are granted only the minimum level of access necessary for their specific task, preventing a threat actor from moving laterally through the network if a single account is compromised.
- CISO and SOC Imperative: Zero Trust is essential for mitigating the top initial access vector (social engineering/stolen credentials), which, according to Unit 42, often leverages over-permissioned access that allows lateral movement after an initial compromise.
Core Domains of Cybersecurity (Types of Security)
Cybersecurity is categorized into specialized domains, each protecting a different aspect of the digital environment:
Domain |
Focus |
Key Practices |
Protecting the connections and communication channels. |
Monitoring traffic, VPNs, firewalls, and network segmentation. |
|
Protecting devices (laptops, phones, servers) that connect to the network. |
Antivirus/Anti-malware, firewalls, and Endpoint Detection & Response (EDR). |
|
Protecting software applications from attack. |
Writing secure code, thorough testing, and continuous monitoring. |
|
Information Security (Data Security) |
Safeguarding sensitive data (also known as Data Security). |
Encryption, access controls, risk management, and clear data-handling policies. |
Protecting data, applications, and services hosted in the cloud. |
Encryption, access controls, and compliance management in shared environments. |
|
Identity & Access Management (IAM) |
Ensuring users are who they claim to be and have appropriate permissions. |
Multi-Factor Authentication (MFA) and least privilege access. |
Protecting vital systems (energy, transportation, communication). |
Threat detection, access control, and regulatory compliance for OT/ICS. |
|
Mobile Security |
Shielding smartphones and tablets from malware and unauthorized access. |
Encryption, secure app usage, and remote device management. |
Keeping artificial intelligence systems safe from cyber threats and misuse. |
Data integrity and privacy, model robustness, governance & lifecycle security (operational framework) |
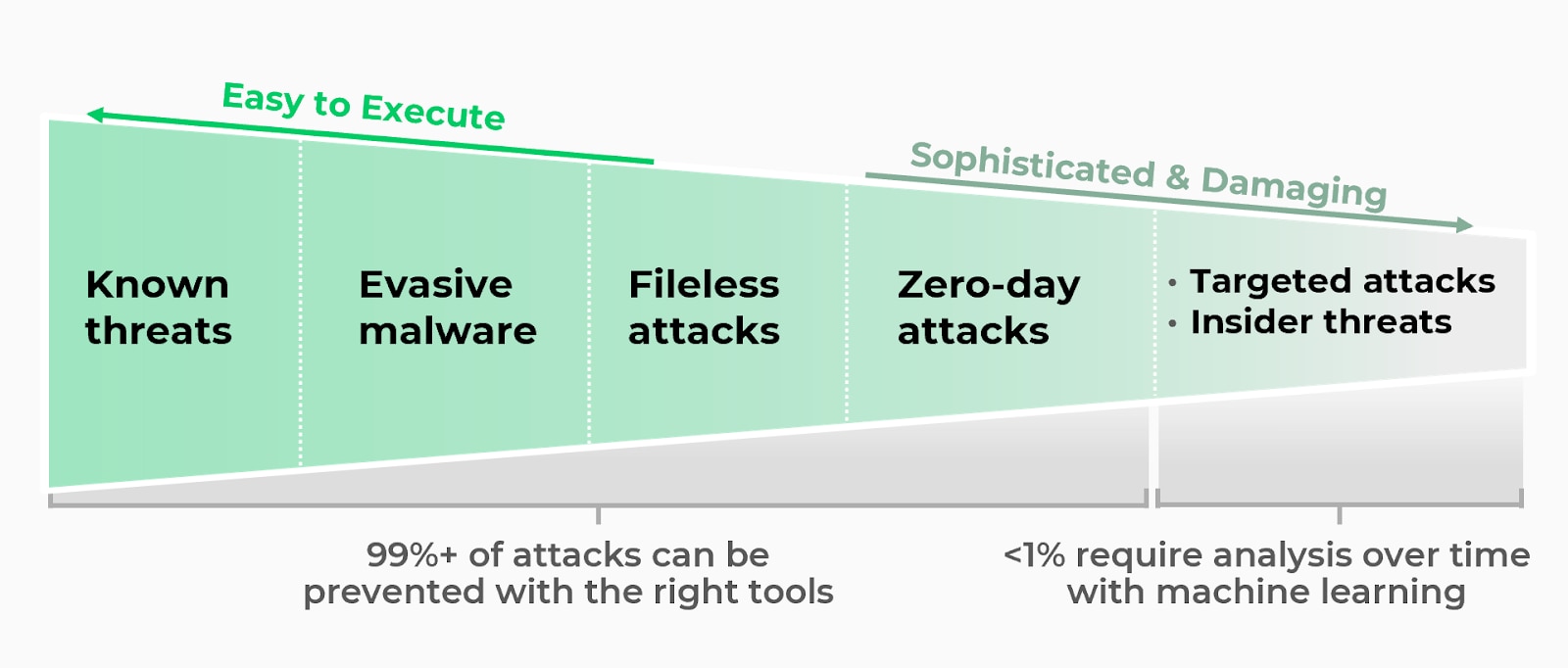
Figure 2: The Spectrum of Cybersecurity Threats Categorized by Ease of Execution
Understanding the Threat Landscape
The cybersecurity threat landscape is constantly shifting—driven by the convergence of automation, artificial intelligence, and increasingly sophisticated adversaries. The human element remains the single most significant vulnerability. The table below highlights today’s leading cyberattack methods, their trends, and actionable strategies to mitigate risk.
Common Cybersecurity Vectors
🔥 Critical ⚠️ High 🟡 Moderate 🟢 Low
Attack Vector / Risk Level |
Trend Insight (Unit 42) |
CISO Action |
Remains the top initial access vector, accounting for 36 % of all incidents. |
Strengthen the Human Layer: Mandate awareness training and deploy AI-driven filters to block sophisticated phishing campaigns. |
|
⚠️ Software / API Vulnerabilities |
Favored by nation-state actors for high-impact, targeted intrusions. |
Patch Management & Threat Prevention: Prioritize patching and use advanced threat prevention to block unpatched exploits. |
🔥 Phishing |
Resurged as a top entry point (23 % of cases) due to AI-crafted emails. |
Email Security & MFA: Enforce multi-factor authentication to prevent credential compromise and escalation of breaches. |
🔥 Ransomware |
59% of organizations experienced ransomware in 2024; average payments rose from $400K to $2M. |
Zero Trust & Backup Resilience: Segment networks, maintain immutable offline backups, and regularly test recovery plans. |
~15% of incidents stem from supply-chain compromises (e.g., MOVEit affecting 1,500+ MSPs). |
Third-Party Risk Management: Vet vendors, require NIST/ISO certifications, apply Zero Trust segmentation, and maintain SBOMs. |
|
⚠️ AI Attacks |
Generative AI enables faster, more scalable attacks such as polymorphic malware and AI-driven phishing. |
AI Security Integration: Monitor for AI-driven anomalies, secure training data, and use AI-based defensive models. |
⚠️ Malware |
Evolving through obfuscation and fileless execution to evade traditional defenses. |
Endpoint Protection & Threat Hunting: Use EDR/XDR for behavioral analysis and sandbox containment. |
Disgruntled or compromised insiders remain difficult to detect and often cause data leaks. |
User Behavior Analytics: Monitor for anomalies, limit data access, and enforce least-privilege controls. |
|
Botnets and IoT devices are increasingly used to flood and disable services. |
DDoS Mitigation & Redundancy: Use cloud-based scrubbing, CDNs, and elastic infrastructure to absorb traffic. |
|
Compromised passwords remain a leading cause of unauthorized access. |
Identity Security & MFA: Require MFA, use password vaulting, and monitor credentials for breach reuse. |
|
Long-term, stealthy nation-state campaigns target high-value data and infrastructure. |
Threat Intelligence & Segmentation: Integrate intel feeds, isolate critical assets, and monitor for lateral movement. |
|
Newly discovered vulnerabilities are weaponized before patches exist. |
Virtual Patching & IPS: Deploy intrusion prevention systems and behavioral analytics to detect threats early. |
|
⚠️ Man-in-the-Middle (MitM) Attacks |
Attackers intercept traffic to steal credentials or inject malware. |
Encryption & Certificate Pinning: Use TLS/SSL end-to-end, VPNs for remote users, and validate certificates. |
Still a prevalent method for compromising poorly secured web apps. |
Secure Coding & Validation: Use parameterized queries, sanitize user input, and conduct regular code audits. |
|
⚠️ IoT Attacks |
Proliferation of connected devices expands the attack surface dramatically. |
IoT Device Management: Require strong authentication, timely firmware updates, and network segmentation. |
Industry-Specific Cybersecurity Challenges
Different sectors face unique risks and regulatory pressures that require tailored defenses:
- Healthcare: Protecting patient data (PHI) and medical devices from ransomware and data breaches.
- Finance: Preventing fraud, insider threats, and regulatory violations under PCI DSS and SOX.
- Energy and Manufacturing: Defending operational technology (OT) and industrial control systems (ICS) from state-sponsored attacks.
- Technology: Securing intellectual property, AI models, and supply-chain dependencies.
- Public Sector: Safeguarding national infrastructure, elections, and citizen data from geopolitical cyber operations.
Each industry’s risk profile underscores one truth: cybersecurity isn’t optional—it’s foundational to resilience, compliance, and public trust.
The Dual Role of AI
Artificial intelligence and machine learning (AI/ML) are transforming both sides of the cyber domain:
AI as the Defender (Defensive) |
AI as the Attacker (Offensive) |
Automated Threat Detection: Sifts through billions of data points to quickly identify subtle anomalies that human analysts miss. |
Accelerated Intrusions: Reduces the time for a full-scale attack (e.g., ransomware) to minutes. |
Faster Response: Integrates with SOAR (Security Orchestration, Automation, and Response) platforms to automate incident triage and containment. |
Sophisticated Social Engineering: Generates highly personalized, grammatically flawless phishing emails at a massive scale. |
Behavioral Analytics: Establishes a baseline of normal user and network behavior to flag risky deviations. |
Polymorphic Malware: Creates self-mutating code that constantly changes to evade traditional, signature-based defenses. |
The Acceleration of AI-Driven Threats
The impact of Artificial Intelligence (AI) and Generative AI (GenAI) on the cyber threat landscape is characterized by acceleration, sophistication, and scale. AI lowers the barrier to entry for novice cybercriminals while equipping sophisticated threat actors with tools that automate and enhance every phase of an attack.
1. Accelerated & Scalable Phishing and Social Engineering
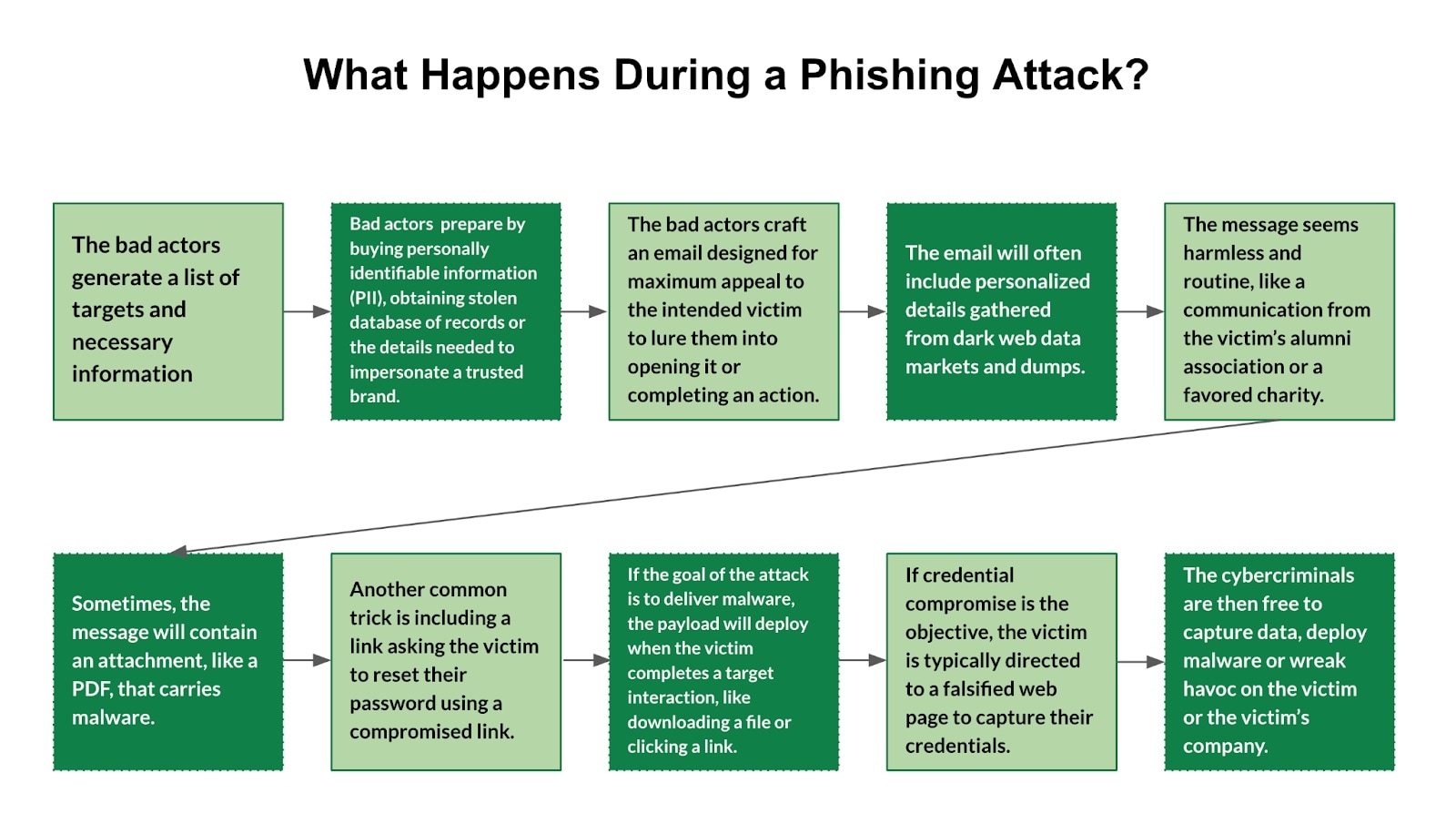
Figure 3: The Stages of a Phishing Attack
GenAI models (such as Large Language Models) enable attackers to create hyper-realistic, highly personalized, deceptive content rapidly.
- Sophisticated Lures: AI generates grammatically flawless and context-aware phishing emails, texts, and chat messages that mimic trusted contacts or organizational styles, making them much harder for users and traditional filters to detect.
- Scale and Speed: Attackers can automate the research and crafting of these personalized attacks, launching campaigns against millions of targets simultaneously—a significant scale-up from traditional, manual efforts.
2. Autonomous and Adaptive Malware
AI is used to create next-generation malicious code that can learn and change its signature to evade detection.
- Polymorphic Malware: Attackers utilize AI to develop self-mutating malware that constantly rewrites its own code. This enables the malware to bypass traditional, signature-based antivirus and detection tools, which rely on recognizing known patterns.
- Evasion and Speed: AI can accelerate the attack lifecycle, reducing the time from initial compromise to data exfiltration to minutes, drastically shrinking the window for defenders to respond.
3. Deepfakes and Credential Fraud
AI's ability to generate realistic synthetic media creates new avenues for impersonation and fraud.
- Deepfake Scams: Voice cloning and video deepfakes are used to impersonate executives, colleagues, or clients in real-time. This is often used in Business Email Compromise (BEC) or financial fraud to authorize fraudulent transfers.
- Credential Attacks: AI automates large-scale credential stuffing and brute-force attacks by efficiently testing millions of stolen password combinations across multiple accounts, often using cloud infrastructure.
4. New Attack Surfaces (Attacks Against AI Systems)
The AI models and their supporting data pipelines themselves become targets for specialized attacks.
- Prompt Injection: Attackers can use carefully crafted inputs (prompts) to trick an AI model (like a chatbot) into ignoring its safety guidelines, leaking sensitive training data, or performing malicious actions.
- Data Poisoning: Adversaries can intentionally feed bad or malicious data into an AI system's training dataset, corrupting its future behavior and causing it to produce inaccurate or harmful outputs (e.g., teaching a security model to ignore threats).

Figure 4: Top 10 Cybersecurity Best Practices.
Cybersecurity Best Practices
Implementing these practices is crucial for strengthening your security posture:
- Enable Multi-Factor Authentication (MFA): Enforce an extra layer of protection (e.g., a one-time code) for all critical accounts.
- Keep Software Updated: Regularly patch operating systems, software, and applications to close known vulnerabilities.
- Back Up Data Regularly: Perform routine backups of critical data to secure, segregated locations and test the restoration process.
- Enforce Least Privilege Access: Grant users and systems only the minimum permissions necessary for their tasks.
- Educate Employees: Train all users to recognize and report phishing attempts, social engineering tactics, and suspicious activity.
- Develop an Incident Response Plan (IRP): Create a clear plan to address security incidents, including containment, restoration, and communication, and conduct regular drills.
- Monitor and Audit Systems: Continuously monitor network activity for anomalies and conduct regular security audits.
Cybersecurity Frameworks and Standards
Cybersecurity frameworks provide structured guidelines for organizations to implement and manage security controls. Some prominent frameworks include:
- NIST Cybersecurity Framework: Provides a policy framework and computer security guidance for private-sector organizations in the United States.
- ISO/IEC 27001: A standard for information security management systems that helps in managing the security of assets.
- CIS Controls: A set of actions that provide specific ways to stop today’s most pervasive and dangerous cyberattacks.
- GDPR and CCPA Compliance: Frameworks for data protection and privacy requirements in Europe and California, respectively.
These standards serve as benchmarks for organizations, helping them assess their security posture and identify areas for improvement.
The Cybersecurity Workforce
The industry is facing a critical global skills gap, creating tremendous career opportunities.
- High Demand: Roles in Cloud Security, Zero Trust Architecture, AI Security, and Incident Response are in high demand.
- Essential Skills: Success requires a mix of technical skills (cloud platforms, security tools, Python) and non-technical skills (risk assessment, business process understanding, and communication).
- Career Growth: The field offers highly competitive salaries and clear advancement paths, supported by certifications such as CISSP, CISM, and cloud-specific credentials.
Cybersecurity FAQs
The core functions of cybersecurity are:
- Protects Sensitive Data: Safeguards personal, financial, and business information from being accessed or stolen by unauthorized individuals or malicious actors.
- Prevents Cyber Threats: Detects, blocks, and mitigates threats such as malware, ransomware, phishing, and denial-of-service (DoS) attacks.
- Ensures Business Continuity: Keeps systems operational by preventing disruptions caused by cyberattacks, minimizing downtime and financial losses.
- Secures Digital Infrastructure: Protects critical systems like servers, databases, and cloud environments from being compromised.
- Maintains Confidentiality, Integrity, and Availability (CIA Triad)
- Confidentiality: Ensures information is accessible only to authorized parties.
- Integrity: Protects data from being altered or corrupted.
- Availability: Ensures resources are accessible when needed.
- Enables Secure Communication: Encrypts data during transmission to prevent interception and unauthorized access, especially for sensitive communications.
- Supports Regulatory Compliance: Helps organizations comply with data protection laws and regulations, such as GDPR, HIPAA, or PCI-DSS.
- Identifies and Mitigates Risks: Monitors systems for vulnerabilities and suspicious activities, enabling proactive risk management.
- Educates and Trains Users: Raises awareness about potential threats and teaches safe practices to minimize human error, which is a common cause of security breaches.
- Facilitates Incident Response: Develops and executes plans to quickly detect, contain, and recover from security incidents, limiting their impact.
Cybersecurity encompasses various domains, each addressing specific threats and vulnerabilities. Here are the seven primary types:
- Network Security
- Focuses on protecting computer networks from unauthorized access, misuse, and cyber threats.
- Key Measures: Firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), and encryption.
- Information Security
- Protects data in all forms—digital and physical—from unauthorized access, modification, or destruction.
- Key Principles: Confidentiality, integrity, and availability (CIA Triad).
- Examples: Encryption, data masking, and access controls.
- Endpoint Security
- Secures devices like computers, smartphones, and tablets that connect to a network.
- Key Tools: Antivirus software, endpoint detection and response (EDR), and device management policies.
- Cloud Security
- Focuses on protecting data, applications, and infrastructure in cloud environments.
- Key Practices: Access controls, secure configuration, and encryption of data in transit and at rest.
- Example: Securing Software as a Service (SaaS) and Infrastructure as a Service (IaaS) platforms.
- Application Security
- Ensures applications are secure throughout their development and lifecycle.
- Key Practices: Secure coding, vulnerability testing, and implementing security features like authentication and authorization.
- Examples: Web application firewalls (WAF) and penetration testing.
- Operational Security (OpSec)
- Focuses on protecting processes and decisions to ensure that sensitive information isn’t leaked.
- Key Elements: Risk management, secure workflows, and awareness of sharing and storing data.
- Example: Limiting access to sensitive operational information to reduce insider threats.
- Disaster Recovery and Business Continuity Planning
- Ensures systems and operations can recover quickly after a cyber incident or disaster.
- Key Elements: Backup solutions, incident response plans, and resilience strategies.
- Examples: Offsite data storage and redundancy planning.
Common threats include: malware, ransomware, phishing, denial-of-service (DoS) attacks, data breaches, insider threats, and advanced persistent threats (APTs).
Use strong, unique passwords, enable multi-factor authentication (MFA), avoid clicking on suspicious links, install antivirus software, and keep systems and applications updated.
Cybersecurity focuses on protecting digital systems and networks, while information security encompasses the protection of all types of data, whether physical or digital.
Key components include risk assessment, incident response planning, employee training, network monitoring, secure software development practices, and data encryption.
Phishing is a cyberattack where attackers trick users into providing sensitive information by pretending to be legitimate entities. It can be prevented by verifying email authenticity, avoiding clicking on unknown links, and using anti-phishing tools.
MFA requires users to verify their identity using multiple methods (e.g., password and fingerprint). It adds an extra layer of security, reducing the risk of unauthorized access.
Businesses can secure remote work by implementing VPNs, enforcing strong password policies, providing cybersecurity training, and using endpoint security solutions.
An incident response plan should include steps for identifying, containing, eradicating, and recovering from security incidents, along with roles and responsibilities, communication protocols, and regular drills.
