-
What Is Incident Response?
- Why Is Incident Response Important?
- Types of Cybersecurity Incidents
- What Is the Incident Response Lifecycle?
- What Is an Incident Response Plan?
- What Is Digital Forensics and Incident Response?
- Incident Response Frameworks and Phases
- Incident Response Teams
- Incident Response Tools and Technology
- Incident Response Services
- Incident Response FAQs
- What is an Incident Response Plan Template?
- What Is an Incident Response Plan (IRP)?
-
What is Cloud Incident Response?
- Cloud Incident Response (IR) Explained
- Why Cloud IR Differs from Traditional IR
- The Cloud Incident Response Lifecycle
- SOC IR vs. Cloud IR
- Best Practices for Cloud Incident Response
- Cloud Incident Response Frameworks and Standards
- The Role of Cloud-Native Security Tools
- Future Trends in Cloud Incident Response
- Key Challenges in Cloud Incident Response
- Solutions to Overcome Cloud IR Barriers
- Cloud Incident Response FAQs
- What is Cyber Incident Reporting?
- What is an Incident Response Playbook?
What Is an Incident Response Team (IRT)?
An Incident Response Team (IRT) is a specialized group within an organization that is responsible for managing and responding to cybersecurity incidents. Its primary duties include identifying, containing, mitigating, and recovering from security threats or data breaches. The IRT aims to minimize the impact of incidents, quickly restore normal operations, and prevent future occurrences.
Key functions of the IRT include:
- Continuous monitoring
- Threat detection
- Forensic analysis
- Communication with stakeholders
- Conducting post-incident reviews
The IRT ensures the organization is prepared to handle security incidents effectively, maintaining business continuity and protecting sensitive information.
What is an Incident Response Team?
An Incident Response Team (IRT) is a specialized group within an organization tasked with responding to and managing incidents that threaten the security of information systems and data. Typically comprised of cybersecurity experts, analysts, communication specialists, and other IT professionals, the IRT operates under a structured framework to address potential and active security breaches.
The primary role of the IRT is to quickly identify, assess, and neutralize threats, thereby minimizing the disruption and potential damage caused by security incidents such as data breaches, malware attacks, or insider threats. They play a crucial role in maintaining the integrity, confidentiality, and availability of an organization’s digital assets and operations.
This proactive and reactive capacity allows the IRT to implement more effective prevention measures and refine the organization's cybersecurity protocols as new threats emerge. Additionally, these teams are instrumental in coordinating with external entities like law enforcement agencies or cybersecurity consultants when specialized or broader skills and resources are required to handle complex threats.
Types of Incident Response Teams
Understanding the types of incident response teams available is crucial for organizations to effectively plan and implement a tailored incident response strategy that best suits their security needs and objectives.
In-House vs External IRTs
In-house incident response teams consist of dedicated staff who know the organization's operations and systems well. These internal teams understand the company's culture and access needs, and they can respond quickly during security events, leading to faster incident identification and resolution.
On the other hand, external incident response teams are hired as consultants or service providers. They bring a wide range of expertise from different industries and threat situations. These external teams can offer fresh perspectives and innovative solutions that can improve overall readiness.
Using in-house and external teams can help organizations balance deep internal knowledge with external skills and resources. This combination creates a flexible and thorough incident response strategy. The choice between in-house teams, external teams, or a mix depends on the organization’s size, budget, and current cybersecurity setup.
Examples of Incident Response Teams
Two prominent examples of incident response teams include the Computer Security Incident Response Team (CSIRT) and the Computer Emergency Response Team (CERT).
The CSIRT typically operates within a company or organization, managing and mitigating computer and network-related incidents through predefined processes and procedures. They are particularly valuable for organizations that require ongoing internal management of security incidents and proactive development of incident-handling capabilities.
CERTs are usually formed at a national or community level and tasked with responding to widespread cyber threats that could impact multiple organizations or sectors. They may also offer guidelines and share vital security information with industry partners. CERTs often collaborate with governmental bodies, coordinating efforts to enhance overall cyber resilience across different industries.
Both types of teams play a crucial role in the incident response ecosystem, providing specialized expertise, developing strategic frameworks, and fostering cooperation between different entities to tackle cyber threats effectively.
“Security leaders should have clear incident response processes in place when building an autonomous SOC. This clarity is required to ensure that automated response is operating properly and can be clearly analyzed and measured for improvement opportunities.”
— SCOTT COLEMAN
Global Solution Architect,
Cortex XSIAM—Security Operations, Palo Alto Networks
Key Functions and Responsibilities
Through their comprehensive roles, incident response teams manage immediate threats and enhance an organization's resilience against future cybersecurity challenges.
Detection and Analysis of Incidents
In the detection and analysis phase of incident response, the team focuses on quickly identifying anomalies or unauthorized activities within the network. This starts with continuous monitoring of security systems for irregularities suggesting a breach.
Once an anomaly is detected, a preliminary investigation is conducted to assess the incident's severity and potential impact by examining system logs, network traffic, and other relevant data.
Effective detection combines advanced threat intelligence with automated tools to analyze large data sets and reveal patterns indicating malicious intent.
Detailed analysis is crucial for understanding the incident's scope and developing an effective response strategy. This phase also involves anticipating potential vulnerabilities to enhance the organization's defense posture.
Sources of incidents for Unit 42 IR cases in 2023
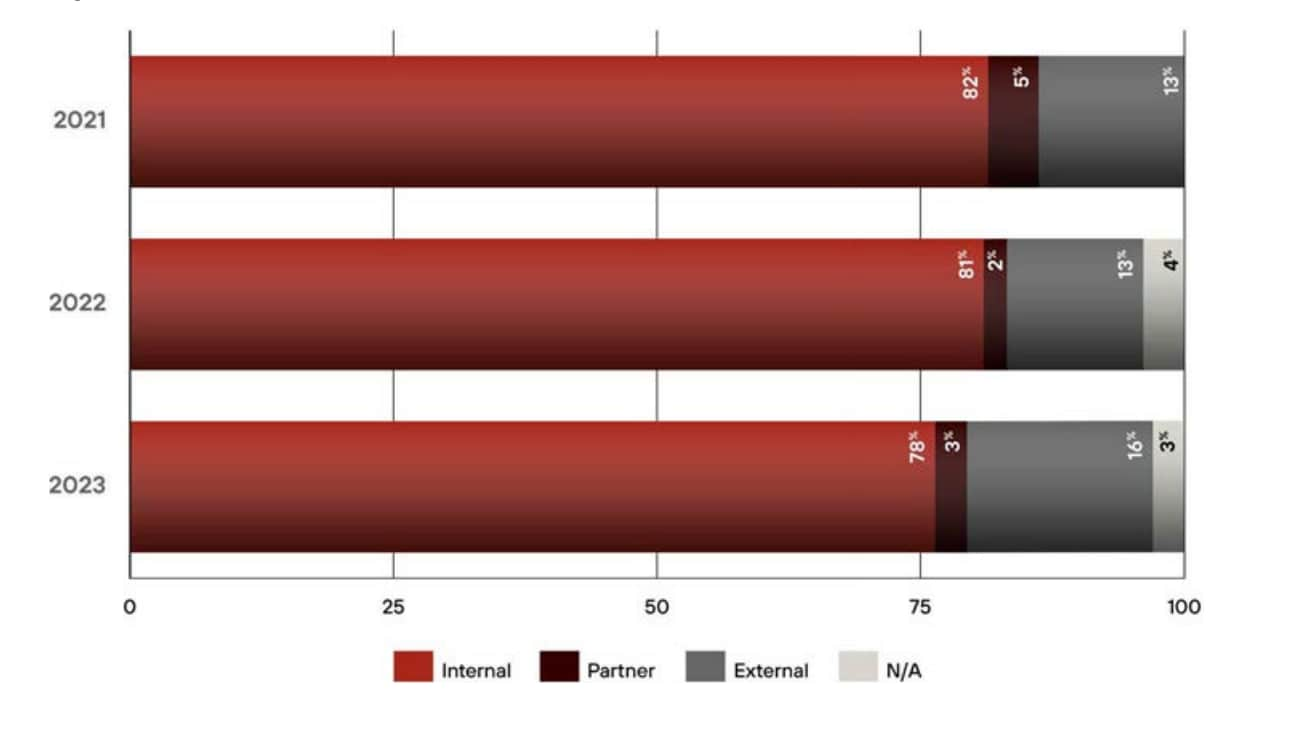
Containment, Eradication, and Recovery
The next critical step for the incident response team is containment, which prevents the threat from causing further damage. This involves implementing strategies to isolate affected systems, thereby protecting other network elements and minimizing the spread of the threat.
Following containment, the team moves to eradication, where they work to remove the threat from the organization's infrastructure altogether. This stage is crucial in eliminating malware or resolving vulnerabilities that could lead to future incidents.
Recovery is the final phase, focusing on restoring affected systems and services to normal operations, ensuring that all systems are fully operational without residual effects of the incident. This might include restoring data from backups, patching systems, or more comprehensive updates to ensure that business operations can resume with strengthened security defenses.
Throughout these phases, clear communication and documentation are essential to inform all stakeholders about the progress and any further actions needed to avert future threats.
Post-Incident Activities
After an incident has been successfully managed, the incident response team engages in a series of essential post-incident activities to prevent future occurrences and enhance overall security protocols:
- Conduct a thorough post-incident analysis, often called a "lessons learned" review, which involves evaluating the response efforts to identify what strategies worked well and what areas need improvement.
- Develop a comprehensive report that documents the incident, the response actions taken, and any findings from the analysis; a valuable resource for ongoing training and adjustment of security strategies.
- Implement updates or patches to the affected systems and review the effectiveness of existing security measures, ensuring that vulnerabilities are adequately addressed.
- Participate in debriefing sessions to discuss and formalize changes to incident response plans and other relevant policies, fostering a culture of continuous improvement and readiness within the organization.
Building an Effective Incident Response Team
Establishing an effective Incident Response Team (IRT) is critical for any organization striving to safeguard its digital assets and maintain comprehensive cybersecurity protocols.
Considerations for Creating an IRT
Consider the following to enhance the overall resilience and effectiveness of your organization's incident response strategy:
- Assess the unique and specific needs of your organization's cybersecurity landscape to determine the size and scope of the IRT, ensuring that it aligns with your risk profile and industry standards.
- Select the right members with diverse skill sets, including technical expertise, communication skills, and problem-solving abilities, to address the multifaceted challenges of security incidents.
- Provide continuous training and development for IRT members, equipping them with the latest cybersecurity knowledge and tools to stay ahead of emerging threats.
- Establish clear protocols and communication channels within the team and with external entities to ensure swift and coordinated responses during incidents.
Choosing the Right Members
Identifying individuals with technical expertise, effective communication skills, and the ability to solve complex problems under pressure is essential. Team members must also have a strong understanding of cybersecurity and be able to adapt quickly to evolving threats.
Detail-oriented individuals who maintain composure during high-stress situations are crucial. The team should be diverse, including forensic analysts to investigate breaches and communication specialists to liaise with stakeholders. A multidisciplinary team enhances the Incident Response Team's capability to address all aspects of a security incident.
Skills Needed in an IRT
Incident Response Team (IRT) members require comprehensive skills beyond technical proficiency, including the following:
- Analytical skills are paramount, as team members must be adept at interpreting data from various sources to detect potential security incidents swiftly and accurately.
- Understanding networking, operating systems, and cyber threat landscapes is essential for identifying vulnerabilities and anticipating threat actors' tactics.
- Problem-solving abilities are also crucial, enabling the team to quickly devise and implement containment, eradication, and recovery strategies.
- Communication skills cannot be overlooked; members must communicate effectively with stakeholders, including internal team members, management, and external partners such as law enforcement or external consultants. This ensures everyone knows the incident's status and the actions required to mitigate risks.
- Adaptability is a must as cyber threats are constantly evolving, and IRT members must remain flexible in updating their skills and strategies to counteract these changes effectively.
Incident Response Team Structure
A well-defined Incident Response Team (IRT) structure is critical for successfully managing cybersecurity incidents, ensuring each member understands their role and responsibilities. Typically, an IRT operates under a systematic framework that outlines the steps for detection, analysis, containment, eradication, and recovery, allowing for a cohesive and well-coordinated response to threats.
Typical Team Roles
Depending on the organizational structure and resource allocation, team members may be located within or geographically dispersed. Maintaining constant and clear communication pathways is vital to ensuring an effective and prompt response to any security incident, regardless of their physical location.
Typical IRTs consist of the following specialized personnel:
- Incident Response Managers - Oversee the response efforts
- Security Analysts - Investigate the incident and assess its impact
- IT infrastructure Specialists - Focus on system restoration and mitigation measures
- Communication Specialists - Facilitate clear dialogue between the team, management, and any external partners involved, ensuring timely updates and coordination are maintained.
- Threat Researchers - Analyze threat intelligence and malware to understand the nature of the attack and provide insights for mitigation.
- Forensic Investigators - Collect and analyze evidence to understand how the breach occurred and its ramifications.
- IT Support Staff - Provide technical support, assist in isolating and mitigating affected systems, and ensure the success of recovery operations.
- Legal/Compliance Advisor - Ensures the response actions comply with legal and regulatory requirements and advises on privacy and disclosure issues.
How an IRT Operates
An IRT operates through a defined incident response plan that details procedures for identifying, analyzing, and addressing security incidents. The team is activated immediately after an incident is detected, with members fulfilling specific roles for swift, coordinated action.
Collaboration among specialists helps assess the threat's scope, prioritizing efforts based on severity and impact. Effective communication keeps all stakeholders informed and aligned during the response.
The IRT utilizes advanced tools for quick data analysis and threat identification, enabling decisive actions to mitigate risks. Continuous evaluation and strategy updates ensure the team remains agile in the evolving cyber threat landscape.
Location of Team Members
The location of IRT members can significantly impact their efficiency and agility. Centralized teams benefit from cohesion and speed, while distributed teams offer resilience, ensuring some members are always available to respond to threats.
Teams based in the exact physical location can collaborate in real time, which is crucial for effective cybersecurity coordination. However, as remote work gains popularity, many organizations opt for geographically dispersed IRTs, using digital tools for seamless communication. This approach broadens the talent pool and enhances flexibility for managing incidents across various time zones.
Benefits and Best Practices for IRTs
An IRT provides organizations with a structured and rapid response capability, significantly reducing the impact and duration of security incidents. A designated IRT fosters a proactive security posture as team members continually assess and enhance cybersecurity measures, adapting to evolving threats and technologies. Best practices for IRT members include:
- Continuous training to stay current with the latest threat landscapes
- Maintaining transparent and open communication channels with stakeholders to ensure transparency and alignment
- Documenting incidents comprehensively to improve future responses
What is an EDR Team?
An Endpoint Detection and Response (EDR) team is a specialized group within an organization's cybersecurity framework that focuses on monitoring, detecting, investigating, and responding to threats and security incidents at the endpoint level.
Endpoints include laptops, desktops, servers, and mobile devices connecting to the organization's network. An EDR team is crucial for several reasons:
- Enhanced Visibility: Provides deep visibility into endpoint activities, allowing for the early detection of threats that might bypass traditional security defenses.
- Rapid Response: Enables swift containment and remediation of security incidents, minimizing damage and reducing recovery time.
- Improved Security Posture: Proactive threat hunting and continuous monitoring help identify and address vulnerabilities before they can be exploited.
- Compliance: Helps meet regulatory requirements by providing detailed documentation and reporting on security incidents and response actions.
What is an ERT?
An Emergency Response Team (ERT) is a specialized group of professionals responsible for quickly and effectively responding to critical security incidents and emergencies. The primary goal of an ERT is to mitigate the impact of severe incidents, ensure business continuity, and restore normal operations as swiftly as possible.
An ERT performs the following roles and responsibilities:
- Rapid Response: Ensures a swift and coordinated response to critical incidents, minimizing damage and downtime.
- Business Continuity: Helps maintain business continuity by quickly addressing and resolving incidents that could disrupt operations.
- Risk Mitigation: Reduces the risk and impact of security breaches, data loss, and other emergencies.
- Regulatory Compliance: Ensures compliance with legal and regulatory requirements for incident response and reporting.
- Stakeholder Confidence: Maintains the confidence of customers, partners, and stakeholders by demonstrating the organization's commitment to security and resilience.
Incident Response Team FAQs
An effective incident response team should include the following key roles:
- Incident Response Managers oversee the entire incident response process, coordinate between team members, and communicate with upper management.
- Security Analysts identify, analyze, and respond to security incidents. They also perform threat detection, log analysis, and forensic investigation tasks.
- IT Specialists are technical experts who assist in implementing security measures, restoring systems, and ensuring that the infrastructure is secure after an incident.
- Legal and Compliance Advisors ensure the response actions comply with legal and regulatory requirements. They may also handle any legal implications of the incident.
- Communication Officers manage internal and external communications, including informing stakeholders and potentially the public about the incident and response actions.
An incident response team should be equipped with the following tools and technologies:
- Security Information and Event Management (SIEM) Systems: These systems aggregate and analyze log data from various sources to detect suspicious activities.
- Endpoint Detection and Response (EDR) Tools: These tools provide continuous monitoring and response capabilities for endpoints, helping to detect and mitigate threats.
- Forensic Tools: These tools are used to analyze compromised systems, collect evidence, and understand the scope of an incident.
- Threat Intelligence Platforms: These platforms provide real-time data on emerging threats, helping the team stay informed and proactive.
- Incident Management Software: This helps track and document incidents, coordinate response efforts, and ensure consistent communication among team members.
Incident response teams often face several common challenges, including:
- Lack of Resources: Insufficient staffing, tools, or budget can hinder the team’s effectiveness. Mitigation involves securing executive buy-in and adequate funding for necessary resources.
- Communication Gaps: Poor communication can lead to confusion and delays. Establish clear communication protocols and designate a communication officer to manage internal and external communications.
- Skill Gaps: Team members may lack the necessary skills or expertise. Regular training, certifications, and participation in industry forums help bridge these gaps.
- Coordination with Other Departments: Ensuring alignment and collaboration with other departments, such as legal, HR, and public relations, can be challenging. Establish cross-functional teams and hold regular coordination meetings to foster collaboration.