-
What Is Endpoint Detection and Response (EDR)?
- Understanding EDR
- Key Benefits of EDR Solutions
- How EDR Works: A Detailed Breakdown
- Evolution of EDR
- EDR Implementation Process
- Common Challenges and Solutions in EDR Adoption
- Advanced EDR Strategies and Optimization Techniques
- EDR and the Evolving Threat Landscape
- How to Evaluate an EDR Solution
- EDR FAQs
- What is EDR vs. XDR?
-
What Is Endpoint Detection and Response (EDR) Management?
- EDR Management Explained
- Key Capabilities of EDR Management
- The Crucial Role of EDR Management in Modern Cybersecurity
- EDR Management Challenges and Solutions
- Best Practices for Effective EDR Management
- EDR vs. EPP: A Complementary Relationship
- Integrating EDR Management with a Broader Security Ecosystem
- Case Study of a Successful EDR Implementation
- EDR Management FAQs
- What Are Endpoint Detection and Response Tools?
- What Is Endpoint Detection and Response (EDR) Compliance?
- What is the Difference Between EDR vs. SIEM?
- What is EDR vs. Antivirus?
- What Is Endpoint Detection and Response (EDR) Deployment?
- What is EDR-as-a-Service Managed Security?
- How Does EDR Leverage Machine Learning?
- How Does EDR Enhance Small Business Cybersecurity?
What is the Role of EDR in Digital Forensics and Incident Response (DFIR)?
Endpoint Detection and Response (EDR) is a critical cybersecurity technology designed to detect, investigate, and respond to suspicious activities on endpoints in real time. It plays a pivotal role in digital forensics and incident response (DFIR) investigations, providing visibility and control that are essential for modern cybersecurity efforts.
Digital Forensics vs. Incident Response
Both forensics and incident response are essential for a comprehensive cybersecurity strategy. They often work hand-in-hand to ensure incidents are effectively managed and understood.
Forensics aims to understand the root cause and gather evidence, focusing on investigation and evidence collection after an incident has been contained or resolved.
On the other hand, incident response occurs during and immediately after an incident's detection and focuses on immediate action to handle and mitigate it. The aim is to manage the incident, minimize the damage, and restore normal operations.
Exploring Fundamentals of EDR Incident Response and Forensics
EDR is a vital incident response and forensics tool, offering rapid threat detection, comprehensive visibility, automated response capabilities, and rich forensic data for investigation and analysis.
H3. The Role of EDR in Modern IT Security
EDR continuously monitors and collects data from endpoints, such as laptops, cellphones, IoT appliances, and other user devices and servers. It uses behavioral analysis and machine learning techniques to scan for suspicious behaviors or anomalies.
EDR generates alerts and detailed reports for further analysis when a threat is detected. The most effective EDR solutions feature automated response capabilities that can quickly mitigate threats, such as isolating infected endpoints.
The Core Features of EDR Solutions
Conventional EDR tools used to focus solely on endpoint data, which provided limited visibility into suspected threats. This limited visibility often led to missed detections, increased false positives, and longer investigation times.
These challenges compounded existing issues faced by security teams, including event overload, skills shortages, narrowly focused tools, lack of integration, and time constraints. In contrast, today's most advanced EDR and XDR solutions offer more robust detection and response capabilities across various areas.
Real-Time Monitoring and Threat Detection
By integrating threat intelligence data from multiple sources, today's EDR solutions allow users to view the root cause of threats and address alerts from any source, significantly reducing investigation times.
Intelligent alert grouping and deduplication simplify triage and reduce the required experience at every stage of security operations. It's also possible to build advanced queries across multiple data sources and visualize results to hunt down the most covert threats.
Automated Response Capabilities
Advanced EDR solutions can conduct lightning-fast investigations and responses, allowing you to quickly investigate threats by obtaining a complete picture of each attack through incident management. With just a single click, you can view the root cause of any alert and promptly halt attacks across your environment.
These solutions enable real-time endpoint scanning to uncover and eliminate threats and swift recovery from attacks by restoring damaged files and registry keys.
After-Incident Reporting and Forensics Tools
Incident management and scoring features within EDR solutions are powerful forensic tools that enable you to get a complete picture of an attack by viewing related alerts, key artifacts, and threat intelligence in one place.
This allows you to get a side-by-side view of all incidents or to take a deep dive into a single incident. These capabilities can be extremely valuable if you need to pursue legal actions after an attack or interact with law enforcement and industry regulators.
Integration with Other Security Solutions
Once threats are identified, they need to be contained quickly. The right SecOps tool can integrate with endpoint, network, and cloud enforcement points to stop the spread of malware.
SIEM Integration
IT security teams typically integrate their EDR solution with their security information and event management (SIEM) system to centralize data analysis and correlation. This integration allows for a more comprehensive view of security events across the organization's network.
SOAR Integration
Additionally, it's important to integrate the EDR solution with Security Orchestration, Automation, and Response (SOAR) platforms. This integration enables the automation of response workflows, streamlining security incident management and improving overall response times.
Threat Intelligence
It is crucial for EDR solutions to be connected to threat intelligence feeds to receive real-time updates on emerging threats. This integration improves the solution's capability to identify and respond to the latest cybersecurity threats, ultimately strengthening the organization's overall security posture.
The Intersection of EDR and Incident Response
In today's threat landscape, the capability to launch incident response efforts quickly is vital for IT security. An EDR solution that integrates data from any source eliminates blind spots. With full visibility, intelligent alert grouping, and incident scoring, SOC teams can effectively cut through the noise and prioritize what's most important.
Accelerating Incident Detection
EDR tools are like the first responders in a cybersecurity emergency. They detect and alert you to potential threats and offer automated responses to contain and mitigate the damage. This efficiency is key in reducing the impact of cyber incidents and accelerating recovery.
Cross-data insights accelerate investigations, streamlining incident response and recovery. The most advanced EDR tools now harness the power of AI, analytics, and rich data. Because AI-powered EDR tools continuously learn, organizations are better positioned to detect stealthy threats and uncover novel attack vectors. Overall, it becomes possible to simplify security operations and cut mean time to respond (MTTR).
Enhancing Incident Analysis and Prioritization
One of the standout capabilities of EDR is real-time monitoring. This means an organization’s system is under constant surveillance, and any suspicious activity is flagged immediately. The real time analysis allows for swift action, crucial in stopping attacks before they cause significant harm.
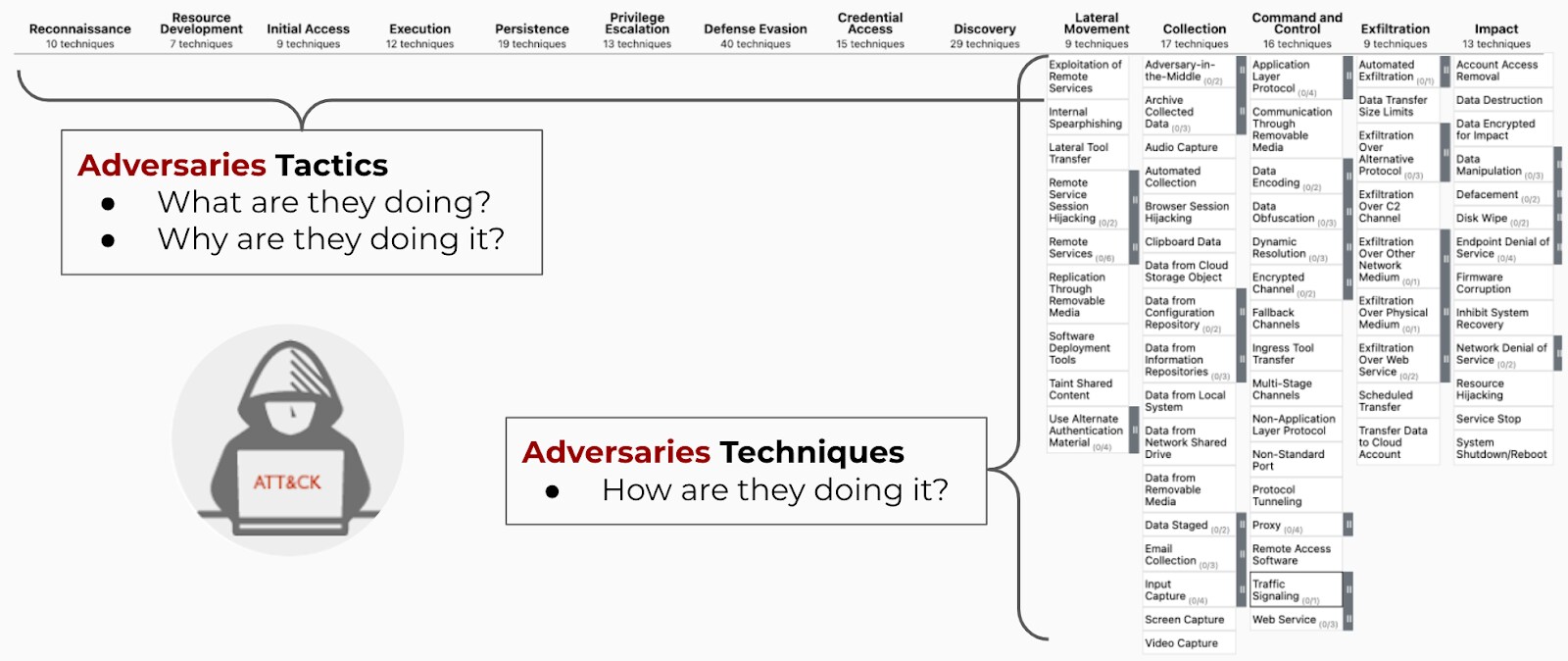
The gold standard for incident analysis today is the MITRE ATT&CK Framework. Advanced EDR solutions provide dashboards that show a comprehensive overview of your threat landscape in relation to the MITRE ATT&CK framework.
These dashboards allow you to see a breakdown of the protection modules and detection rules for each MITRE tactic and technique, allowing you to review the elements that affect your coverage and identify any gaps in your framework.
Facilitating Swift and Efficient Response to Threats
Automation is a game-changer in incident response. EDR systems can automatically isolate infected endpoints, block malicious processes, and remediate threats without human intervention. This speed and efficiency can make all the difference in limiting the damage of a cyberattack.
Ideally, EDR systems should enable security teams to instantly contain endpoint, network, and cloud threats from a single console or interface. The most advanced EDR solutions offer scripting features that enable analysts to verify swiftly and contain attacks without disrupting end users by running Python, PowerShell, or system commands and scripts directly on endpoints.
This makes it possible to stop the spread of malware, restrict network activity to and from devices, and update prevention lists like bad domains through tight integration with enforcement points.
Enhancing Forensic Capabilities with EDR
When a cyber incident occurs, a swift and thorough investigation is paramount to understanding the attack's scope, identifying the root cause, and preventing future compromises. EDR empowers organizations to enhance their forensic capabilities, providing them with the tools and data to conduct comprehensive investigations.
EDR solutions capture detailed evidence of malicious activity, enabling security teams to reconstruct the attack timeline, identify the attackers' techniques, and determine the extent of the compromise. By leveraging EDR's forensic capabilities, organizations can gain invaluable insights into attacker behavior and improve their overall security posture.
Forensic Data Collection by EDR Systems
EDR tools excel at collecting forensic data. They gather detailed logs and records of endpoint activities, providing a rich source of information for post-incident analysis. This data is critical for understanding the scope and nature of an attack.
Analyzing Forensic Data for Root Cause Analysis
Once the data is collected, it’s time for analysis. EDR systems help sift through mountains of data to pinpoint the root cause of an incident. This analysis helps identify exploited vulnerabilities and steps needed to prevent future incidents.
Leveraging EDR for Better Threat Intelligence
EDR (Endpoint Detection and Response) tools play a crucial role in contributing to threat intelligence by continuously gathering and sharing data on emerging threats and cybercriminals' latest attack patterns. This real-time information is essential for organizations to stay ahead of cyber threats, proactively defend against potential attacks, and enhance their overall security posture.
Integrating EDR into Your Cybersecurity Strategy
Integrating EDR into your cybersecurity strategy starts with planning. Assess your current security posture, identify gaps, and set clear goals for what you want to achieve with EDR. Preparation involves ensuring that your team is ready and that your infrastructure can support the new tools.
Best Practices for EDR Deployment and Management
Deploying EDR effectively involves following best practices. This includes regular updates, proper configuration, and continuous monitoring. Management is about maintaining the system, analyzing data regularly, and adapting to new threats as they emerge. To effectively deploy EDR, adhere to the following best practices:
- Regularly update the EDR system with the latest threat intelligence and security patches.
- Correctly configure the EDR system to ensure its effectiveness in detecting and responding to threats.
- Continuously monitor the EDR system to ensure that any potential security issues are promptly identified and addressed.
- Maintain the system by conducting regular checks and maintenance tasks.
- Regularly analyze data collected by the EDR system to allow for insights into potential vulnerabilities and threat patterns.
- Be adaptable and proactive in responding to new and emerging threats, allowing for the implementation of timely and effective security measures to counteract evolving threats.
Training Teams to Leverage EDR Effectively
Technology alone isn't enough; your team must know how to use it. Training is essential to ensure your cybersecurity personnel can effectively leverage EDR tools. This includes understanding how to interpret data, respond to alerts, and conduct forensic analysis.
Evaluating EDR Solutions: What to Look For
Not all EDR solutions are created equal. When evaluating options, consider factors like ease of use, integration capabilities, and the comprehensiveness of features. Look for solutions that offer optimal support and regular updates to keep pace with evolving threats.
DFIR vs. EDR
DFIR involves a range of activities to address the entire lifecycle of a security incident, while EDR focuses on detecting and responding to threats on individual endpoints. DFIR uses tools for forensic analysis, incident management, and reporting, while EDR provides real-time monitoring, detection, and response capabilities.
EDR tools support DFIR processes by enhancing threat detection, gathering endpoint data, facilitating forensic analysis, and offering immediate response actions.
CSIRT vs. Digital Forensics
A Computer Security Incident Response Team (CSIRT) and digital forensics play critical roles in an organization's cybersecurity. CSIRT manages and coordinates the response to cybersecurity incidents, while digital forensics involves collecting, preserving, analyzing, and presenting digital evidence related to these incidents.
CSIRT focuses on managing incident response, while digital forensics concentrates on investigating and analyzing digital evidence. Both are essential for a comprehensive approach to cybersecurity incident management and resolution.
Challenges with EDR in Incident Response and Forensics
Implementing EDR presents challenges, including integration issues, false positives, and resource constraints. Overcoming these challenges requires careful planning, regular system tuning, and ongoing training.
Forensic investigations can raise privacy and legal concerns. Ensuring that your EDR practices comply with relevant laws and regulations while protecting user privacy and gathering necessary data for security purposes is essential.
Cyber threats are constantly evolving, and so should your EDR strategy. Future-proofing involves staying updated with the latest threat intelligence, regularly reviewing and updating security practices, and adapting to new challenges.
Case Study: Impact of EDR in Real-World Scenarios
Endpoint detection and response (EDR) capabilities are crucial in ensuring compliance with today's major privacy and security regulations. Let's examine how Palo Alto Network's advanced EDR solution, Cortex XDR, assists financial services organizations in staying compliant with the Payment Card Industry Data Security Standards (PCI DSS).
The Challenges
The PCI DSS covers various aspects of system operations, data storage, and data transmission. However, the rules related explicitly to endpoint security are outlined in requirements 5 and 12:
- Requirement 5: Protect all systems against malware and update anti-virus software or programs regularly.
- Requirement 12: Maintain a security policy addressing information security for all personnel.
The Solution
Palo Alto Networks® offers the following solutions to address these challenges:
- Next-Generation Firewalls
- Cortex XDR® - Cortex XSOAR
- Cloud-Delivered Security Services
The Results
Proven Attack Prevention
Cortex XDR provides a complete prevention stack for the latest malware, exploits, and fileless attacks. It utilizes AI-driven local analysis and behavior-based protection to block malware before execution. Continuous updates ensure the availability of the latest local prevention. Integration with the WildFire service enhances security accuracy and coverage through deep inspection of unknown files, and automatic threat intelligence sharing.
Speedy Incident Investigation and Response
Analysts can expedite investigations by gaining a comprehensive picture of every incident and reviewing the root cause of network and endpoint alerts with a single click. Intelligent alert grouping and deduplication simplify triage and reduce the expertise required at each stage of security operations. Tight integration with enforcement points enables analysts to respond to threats promptly.
Strong Endpoint Protection
Cortex XDR prevents attackers from tampering with agent files or registry settings, addressing PCI Requirements. Furthermore, the service monitors all endpoint changes and can detect if protection is disabled.
Comprehensive Reporting
Palo Alto Networks offers interactive reports and investigative capabilities across endpoint, network, and cloud environments to expedite incident investigations and inform incident response.

Source: The State of Security Automation Report, Palo Alto Networks, December 2, 2021.
Additionally, endpoint, network, and cloud sensors can send alerts to Cortex XSOAR, assisting organizations in implementing an incident response plan. Playbooks can automate repetitive tasks in response to incidents, ensuring a consistent approach every time.
The Role of EDR in Incident Response and Forensics FAQs
Key features of EDR solutions that aid in incident response and forensics include:
- Real-time monitoring and alerting: Continuous monitoring of endpoint activities with immediate alerts on suspicious behavior.
- Detailed logging: Comprehensive logs of system events, file changes, and network connections.
- Behavioral analysis: Use of machine learning to detect unusual patterns and activities.
- Automated response actions: Capabilities such as quarantining files, isolating endpoints, and killing malicious processes.
- Investigation and reporting tools: These are tools for deep-dive investigations, including timeline reconstruction, root cause analysis, and evidence collection for forensic purposes.