- 1. Why does quantum computing pose a threat to cybersecurity?
- 2. How soon could the quantum threat become real?
- 3. What cybersecurity risks will quantum computing create?
- 4. What are governments and standards bodies doing about it?
- 5. How are organizations preparing for post-quantum security, and what are the challenges?
- 6. What happens if organizations don't prepare in time?
- 7. What's next for quantum-safe cybersecurity?
- 8. Quantum computing cybersecurity risks FAQs
- Why does quantum computing pose a threat to cybersecurity?
- How soon could the quantum threat become real?
- What cybersecurity risks will quantum computing create?
- What are governments and standards bodies doing about it?
- How are organizations preparing for post-quantum security, and what are the challenges?
- What happens if organizations don't prepare in time?
- What's next for quantum-safe cybersecurity?
- Quantum computing cybersecurity risks FAQs
8 Quantum Computing Cybersecurity Risks [+ Protection Tips]
- Why does quantum computing pose a threat to cybersecurity?
- How soon could the quantum threat become real?
- What cybersecurity risks will quantum computing create?
- What are governments and standards bodies doing about it?
- How are organizations preparing for post-quantum security, and what are the challenges?
- What happens if organizations don't prepare in time?
- What's next for quantum-safe cybersecurity?
- Quantum computing cybersecurity risks FAQs
The cybersecurity risks associated with quantum computing include:
- Breaking public-key encryption
- 'Harvest now, decrypt later' attacks
- Compromising digital signatures & identity verification
- Undermining blockchain integrity
- Weakening secure communications
- Exposing IoT ecosystems
- Endangering critical infrastructure
- Creating geopolitical imbalance
To prepare, organizations should begin migrating to post-quantum cryptography, conduct cryptographic inventories, and adopt agile architectures that can integrate new standards as they're finalized.
Why does quantum computing pose a threat to cybersecurity?
Quantum computing threatens cybersecurity not because it hacks differently—but because it rewrites the mathematics that modern encryption depends on.
More specifically:
Quantum computing changes how information can be processed.
So instead of bits that represent either a 0 or a 1, quantum computers use qubits—units that can exist in both states at once through a property called superposition. When qubits interact, they can also become entangled. That means the state of one instantly relates to another, no matter the distance between them.
Why does that matter?
Because it means a quantum computer can explore many possible solutions at the same time.
Classical computers must check one option after another. But quantum systems can evaluate patterns in parallel. And that difference is what makes them powerful—and dangerous—to today's encryption.
Here's why.
Most of the world's secure communication depends on asymmetric cryptography. That includes RSA, elliptic-curve cryptography (ECC), and Diffie–Hellman (DH). These algorithms rely on math problems that are intentionally hard to solve, like factoring very large numbers or finding discrete logarithms. They're safe because classical computers would take billions of years to solve them.
Quantum algorithms change that math.
Shor's algorithm can factor those large numbers exponentially faster. That means it could expose the private keys that protect encrypted data, digital signatures, and certificates. Grover's algorithm does something similar for symmetric encryption, reducing brute-force time from 2ⁿ to roughly √2ⁿ operations. Symmetric keys would need to double in length to maintain the same security strength.
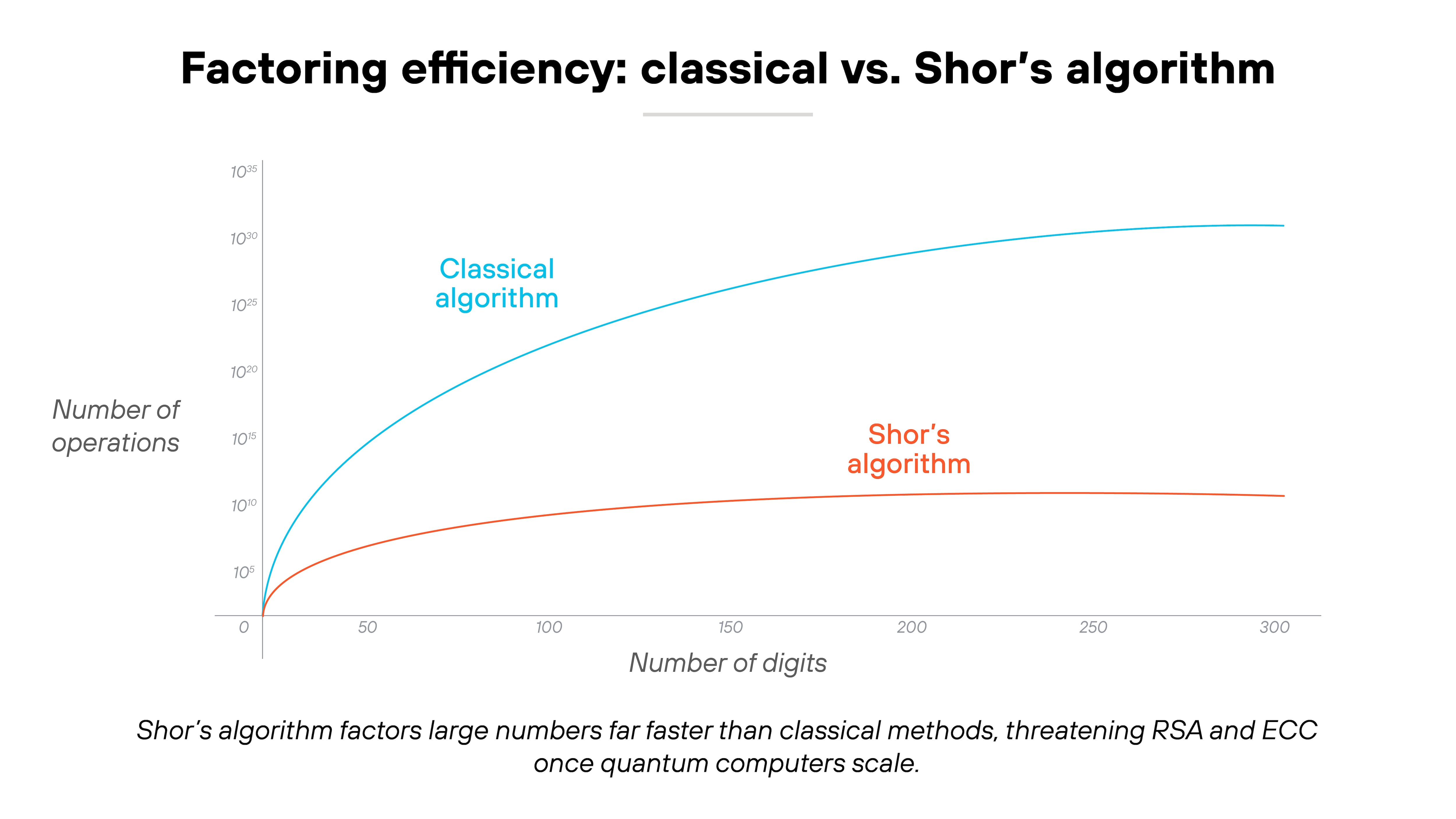
In other words:
While symmetric encryption can be strengthened with longer keys, public-key systems can't be saved that way. They'll need entirely new, quantum-resistant algorithms.
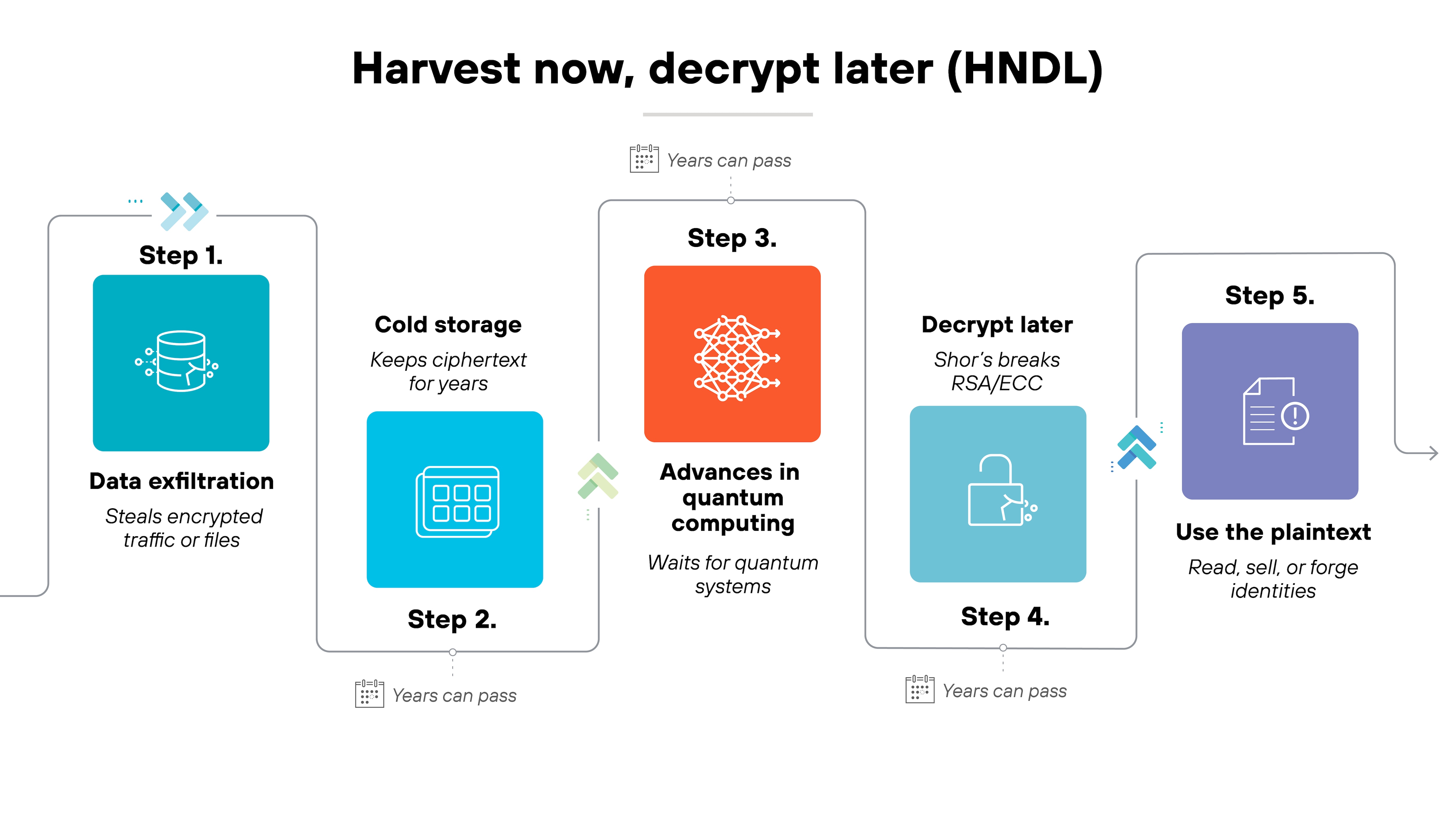
NIST and CISA call the class of system capable of doing this a cryptographically relevant quantum computer (CRQC). Once one exists, much of the world’s public-key encryption becomes obsolete overnight. Even data encrypted today could be collected and stored for later decryption once that capability arrives, also known as harvest now, decrypt later (HNDL).
And while that level of computing power may still be years away, preparing for it takes just as long. Which means migration has to start well before the threat materializes.
How soon could the quantum threat become real?
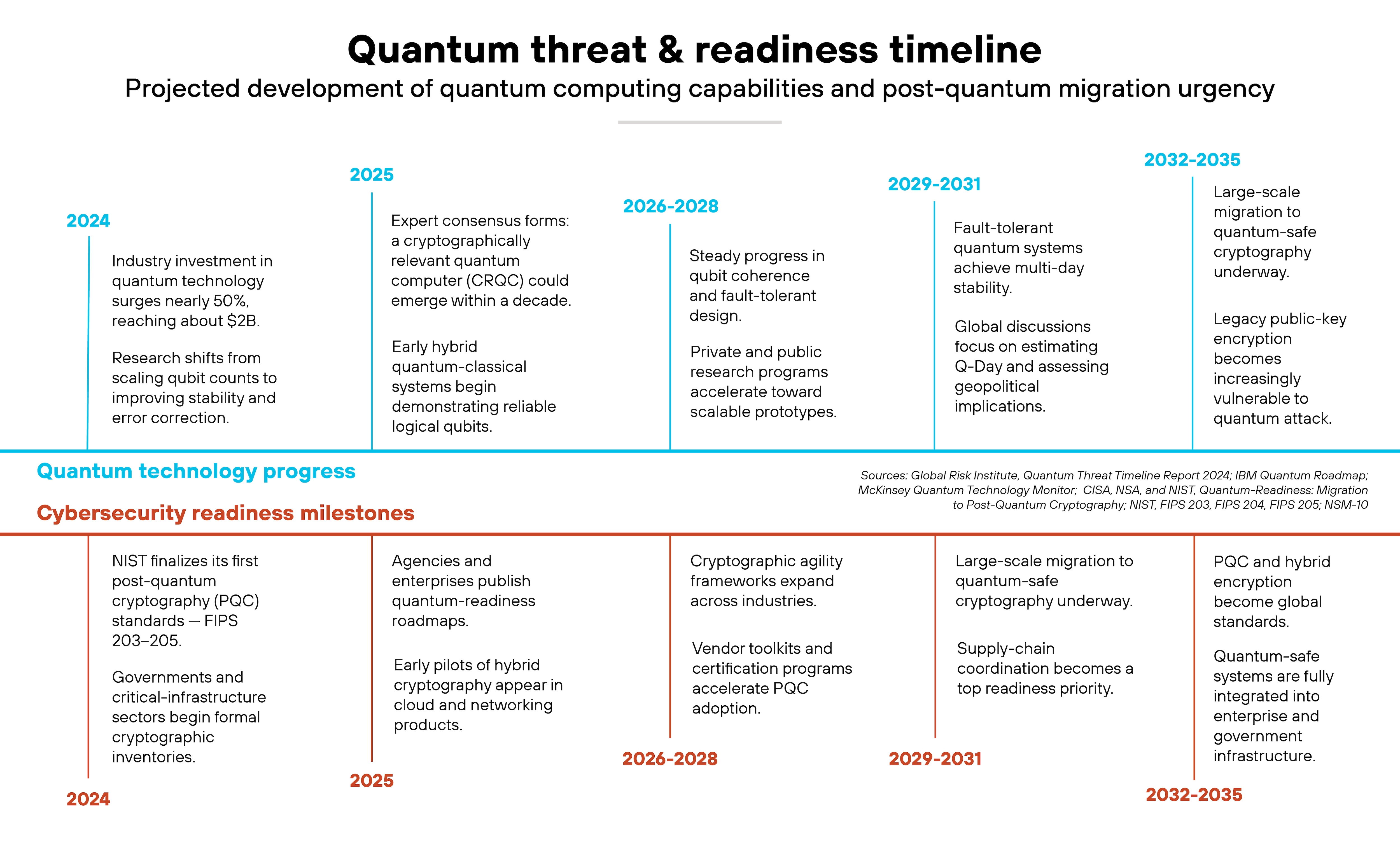
The timeline for a quantum computer capable of breaking modern encryption is uncertain. But experts agree it's no longer theoretical. It's a question of when, not if.
Each year, the Global Risk Institute surveys quantum and cybersecurity specialists about the pace of progress. In its 2025 report, most participants said the threat window is shrinking fast:
- "More than half (17/32) felt it was more than 5%-likely already within a 10-year timeframe, and almost a third of the respondents (10/32) indicated a likelihood of about 50% or more."
- "An 'optimistic' interpretation of the responses … leads on average to a ~34% estimate of a CRQC being developed within a decade and ~14% within 5 years. Even a 'pessimistic' interpretation … gives a ~19% average likelihood estimate of a disruptive quantum threat in the next 10 years."
People aren't debating feasibility anymore. Only timing. Quantum computing research is accelerating across both private and public sectors.
Meanwhile, IBM's Quantum Roadmap shows steady advances in qubit stability, logical qubits, and error correction. These improvements matter because reliable qubits are what make large-scale systems practical.
Not to mention, McKinsey's Quantum Technology Monitor 2025 notes that quantum-tech investment grew by nearly 50% in 2024—reaching about $2 billion—as progress in qubit stability and error correction signaled a shift from scaling qubit counts toward building more practical, reliable systems.
However:
There's still a gap between laboratory performance and a cryptographically relevant quantum computer—the point where it could break RSA or elliptic-curve encryption.
Estimates vary, but many researchers place that milestone sometime in the 2030s. CRQC capability could be ten years away. Migration can take a decade by itself. And migrating to post-quantum cryptography will take years of coordination, testing, and infrastructure change.
Which means:
The real deadline isn't Q-Day itself—the moment a CRQC arrives. It's the years leading up to it. Organizations that wait for certainty will be too late.
That's why NIST, CISA, and NSA urge planning now. Because readiness depends on starting before the threat becomes real.
What cybersecurity risks will quantum computing create?
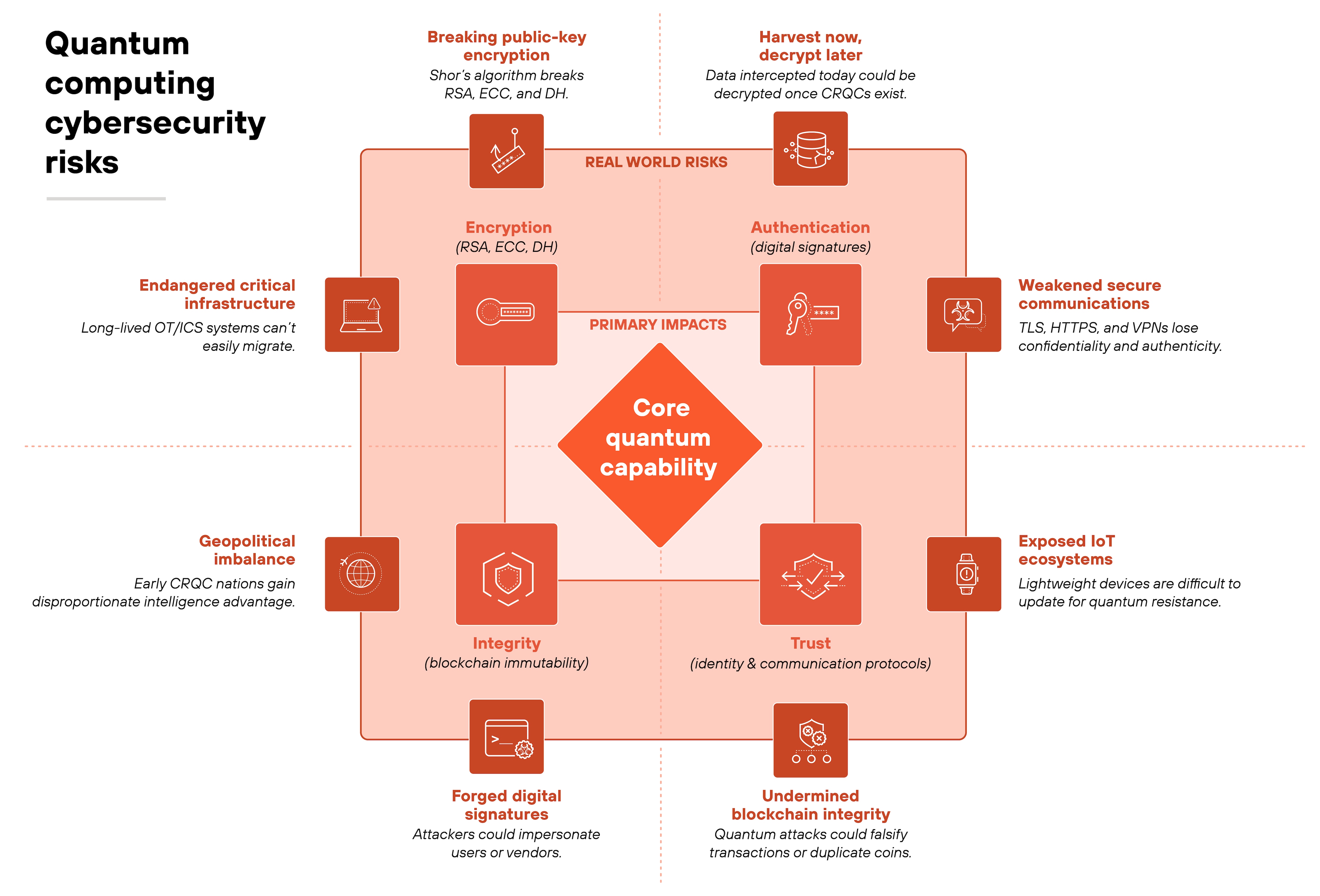
The biggest risks from quantum computing come from how it undermines the cryptography that secures nearly every digital system.
Put simply, each of these risks stems from one core property: the ability of a powerful quantum computer to solve certain math problems far faster than classical ones.
These risks span everything from encryption and authentication to national security.
Here's what that means in practice.
Breaking public-key encryption
Quantum computers could use Shor's algorithm to factor large integers and compute discrete logarithms efficiently. That directly compromises RSA, elliptic-curve cryptography (ECC), and Diffie–Hellman (DH).
Once a CRQC exists, the public keys protecting encrypted traffic, digital signatures, and authentication mechanisms could all be exposed.
Note:This is the foundational risk. Because nearly every security protocol, from VPN handshakes to SSL certificates, depends on these same algorithms.Decrypting stored data later (“harvest now, decrypt later”)
Attackers can intercept encrypted traffic today and store it for future decryption. When quantum computers mature, that archived data could be decrypted quickly.
This creates a delayed risk. Because sensitive information thought to be secure for decades may be readable overnight once quantum capability arrives.
Note:Intelligence agencies have warned that this threat changes how data lifespans must be managed. Especially for information that needs to remain confidential for decades, such as defense or medical records.Compromising digital signatures and identity verification
Digital signatures confirm integrity and authenticity. If quantum computers can derive private keys, they can forge signatures that appear legitimate.
That would allow malicious actors to impersonate trusted software vendors or users without detection.
Undermining blockchain integrity
Most blockchain systems depend on ECC for transaction verification.
Quantum attacks could enable users to falsify transactions or duplicate coins. That breaks the immutability that blockchain depends on, threatening cryptocurrencies and any enterprise system built on distributed ledgers.
Weakening secure communications
Technologies like TLS, HTTPS, VPNs, and email encryption rely on public-key exchange to establish trust.
A quantum-enabled adversary could decrypt traffic, impersonate endpoints, or intercept credentials in transit.The result is the loss of confidentiality and authenticity across global communication systems.
Exposing IoT ecosystems
Internet of Things devices often use lightweight encryption designed for efficiency, not quantum resistance.
They're also difficult to update once deployed. That makes large, distributed IoT networks especially vulnerable to post-quantum exploitation.
Note:Unlike enterprise networks, most IoT deployments lack over-the-air update mechanisms, meaning even awareness of a vulnerability doesn't guarantee it can be patched.Endangering critical infrastructure
Operational technology (OT) and industrial control systems (ICS) often use long-lived hardware and cryptographic keys. These systems can't be upgraded quickly.
Quantum attacks could jeopardize essential sectors like energy, healthcare, and transportation if migrations lag behind.
Creating geopolitical imbalance
The first nations or organizations to develop CRQC capability will gain a disproportionate intelligence and defense advantage.
Encrypted diplomatic, military, and economic data from other nations could be exposed. That imbalance may reshape global power dynamics in cyberspace.
Note:Quantum advantage could trigger a new phase of cyber-espionage competition, where access to CRQC resources determines which nations can read or protect the world's encrypted archives.
In short:
Quantum computing doesn't just pose one cybersecurity risk. It cascades across encryption, identity, and trust. Each layer of digital security built on public-key cryptography must eventually change to stay secure in the quantum era.
What are governments and standards bodies doing about it?
Governments and standards bodies are treating quantum readiness as a global security priority. Their focus is on replacing vulnerable cryptographic systems before large-scale quantum computers emerge.

As we touched on, that effort is being led by the U.S. National Institute of Standards and Technology (NIST).
Here's why that matters.
Over the past several years, NIST has run a public competition to identify post-quantum cryptography (PQC) algorithms strong enough to withstand quantum attacks. The process has now entered its final stage.
As a result, the agency has standardized three algorithms, published as FIPS 203–205:
- Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM)
- Module-Lattice-Based Digital Signature Algorithm (ML-DSA)
- Stateless Hash-Based Digital Signature (SLH-DSA)
NIST also selected HQC (Hamming Quasi-Cyclic) for standardization as a second key-encapsulation mechanism and is preparing a draft FIPS for FN-DSA (FALCON) as another digital signature option.
These standards pave the way for post-quantum cryptography to be adopted across public and private sectors.
On the defense side, the National Security Agency (NSA) has issued the Commercial National Security Algorithm Suite 2.0 (CNSA 2.0). It requires government and defense systems to migrate to quantum-resistant algorithms by the early 2030s.
Supporting that mandate, National Security Memorandum-10 (NSM-10) directs all federal agencies to inventory existing cryptography and begin transition planning.
The CISA/NSA/NIST Quantum Readiness Roadmap extends that guidance to critical infrastructure and vendors, emphasizing cryptographic inventories and vendor coordination.
This work isn't limited to the United States.
The European Telecommunications Standards Institute (ETSI) published TR 103 967, outlining migration frameworks for post-quantum systems.
And the European Union Agency for Cybersecurity (ENISA) continues to push for international cooperation on interoperability and shared security standards.
Still, alignment across jurisdictions remains a challenge.
Each country is setting its own timelines and priorities, which complicates coordination for multinational organizations. Achieving true quantum security will require not only new algorithms but global consistency in how they're implemented.
These initiatives show that readiness isn't optional. It's already underway. While governments are setting the standards, organizations must now translate those policies into action.
How are organizations preparing for post-quantum security, and what are the challenges?
Most organizations are still in the early stages of preparing for a post-quantum future. But the transition has begun.
Quantum readiness is now being treated as a multiyear program, not a single upgrade.
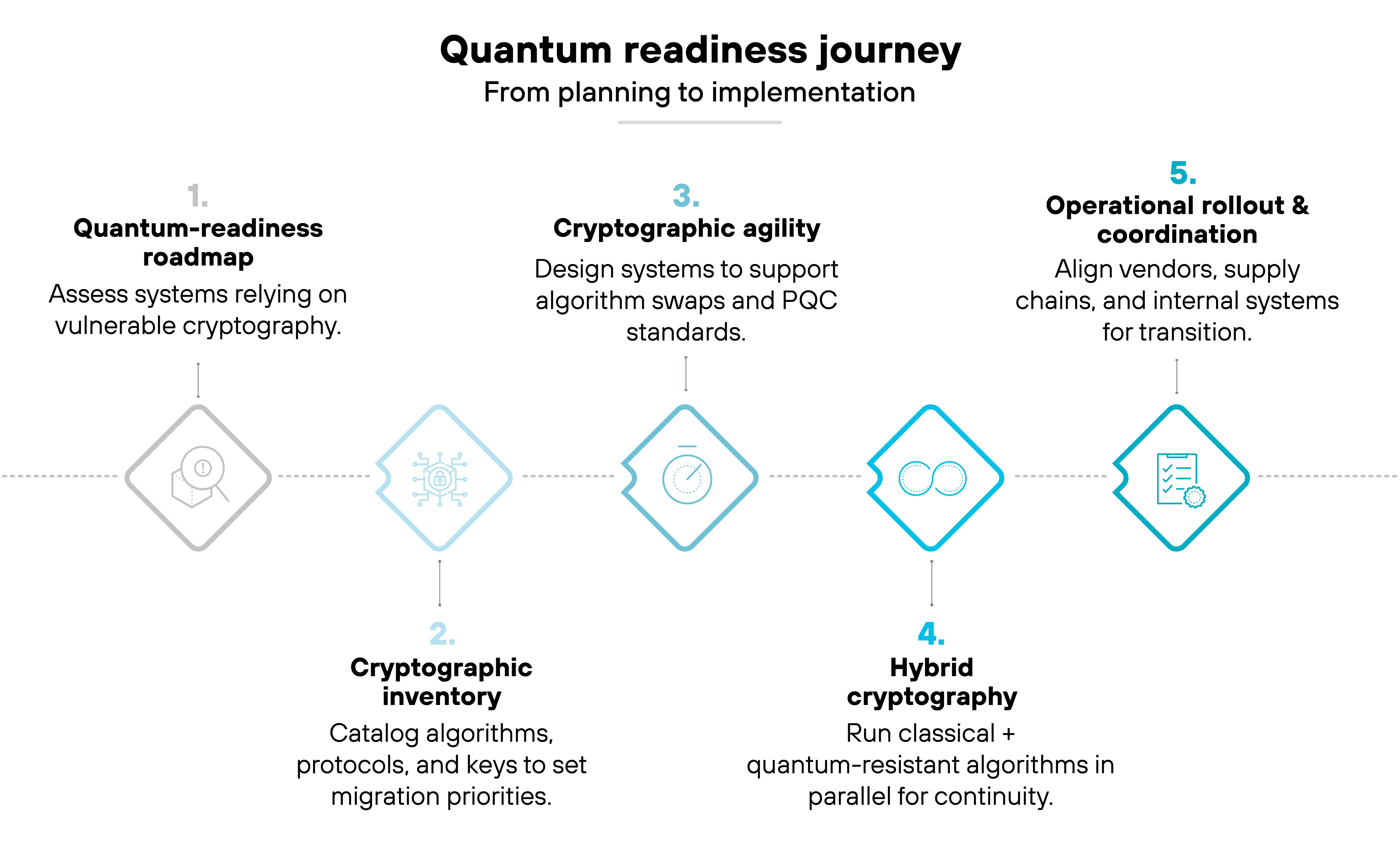
Here's what that looks like.
Many enterprises are starting with quantum-readiness roadmaps.
These plans outline what systems rely on vulnerable cryptography and how they'll eventually migrate to quantum-safe alternatives.
CISA and other agencies recommend beginning with a cryptographic inventory.
This involves cataloging all algorithms, protocols, and keys in use to set migration priorities based on risk exposure.
Next comes cryptographic agility.
That means designing systems flexible enough to swap algorithms as standards evolve. It's a key part of preparing for NIST's finalized post-quantum cryptography (PQC) standards, which will take years to fully implement across software, hardware, and cloud environments.
Some organizations are also experimenting with hybrid cryptography.
That combines classical and quantum-resistant algorithms during the transition period to maintain backward compatibility.
There are challenges to consider, though.
A lot of organizations show growing awareness but uneven urgency. They often recognize the risk but depend on vendor roadmaps before acting. That creates delays, especially for large organizations with deeply embedded systems.
Meanwhile, smaller organizations frequently rely on upstream providers—like cloud or hardware vendors—to make the transition for them.
Another challenge is the supply chain. Even if an enterprise updates its own systems, its partners or vendors might not. That interdependence means a single weak link can reintroduce risk long after migration begins.
Overall, The Global Risk Institute found that readiness across sectors varies widely, with only a minority of organizations maintaining formal quantum-transition plans.
In the end, the race to post-quantum security isn't just about cryptography. It's about coordination. And for most organizations, the work has to start now to be ready when the standards are.
What happens if organizations don't prepare in time?
Failing to prepare for post-quantum security doesn't just create operational risk. It creates a systemic trust problem that could take years to repair.
Here's why.
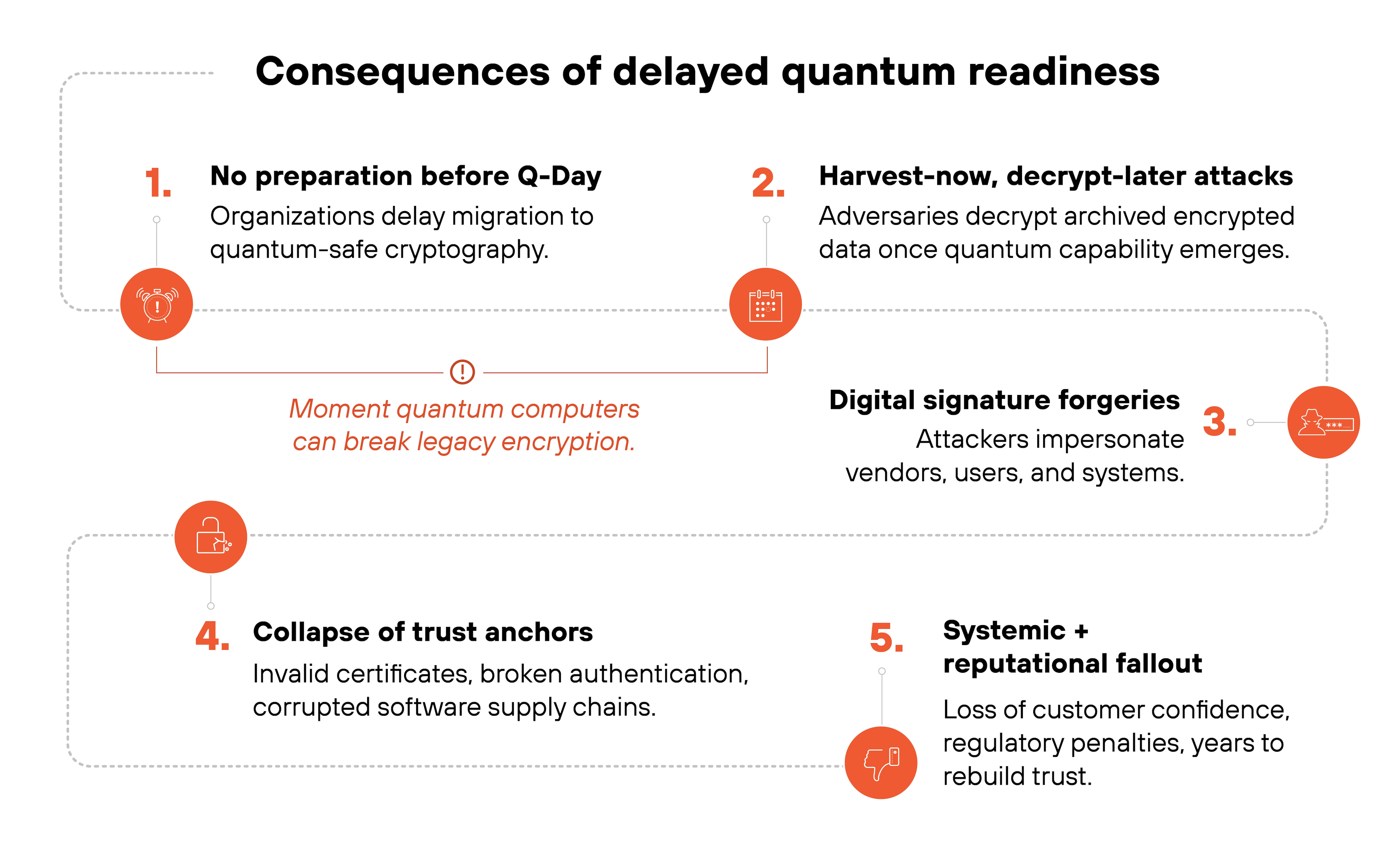
Once a cryptographically relevant quantum computer exists, data encrypted under today's algorithms will be vulnerable.
Attackers collecting encrypted traffic now could decrypt it later (also known as a harvest now, decrypt later, or HNDL attack), exposing intellectual property, customer information, and government communications that were once considered secure.
That makes quantum risk retroactive.
But the damage won't stop with data exposure.
If quantum computers can forge digital signatures, they can impersonate trusted users, vendors, and systems.
That breaks authentication chains, invalidates software updates, and undermines certificate authorities. When those trust anchors collapse, so does confidence in the entire digital ecosystem.
The reputational fallout could be just as severe. Many early adopters view quantum readiness as a reputational issue as much as a technical one.
A lack of visible preparation can erode customer confidence and market trust even before quantum attacks become practical.
The takeaway:
Waiting until Q-Day means being too late. By then, attackers may already hold decades of sensitive data. And rebuilding trust will be far harder than protecting it now.
What's next for quantum-safe cybersecurity?
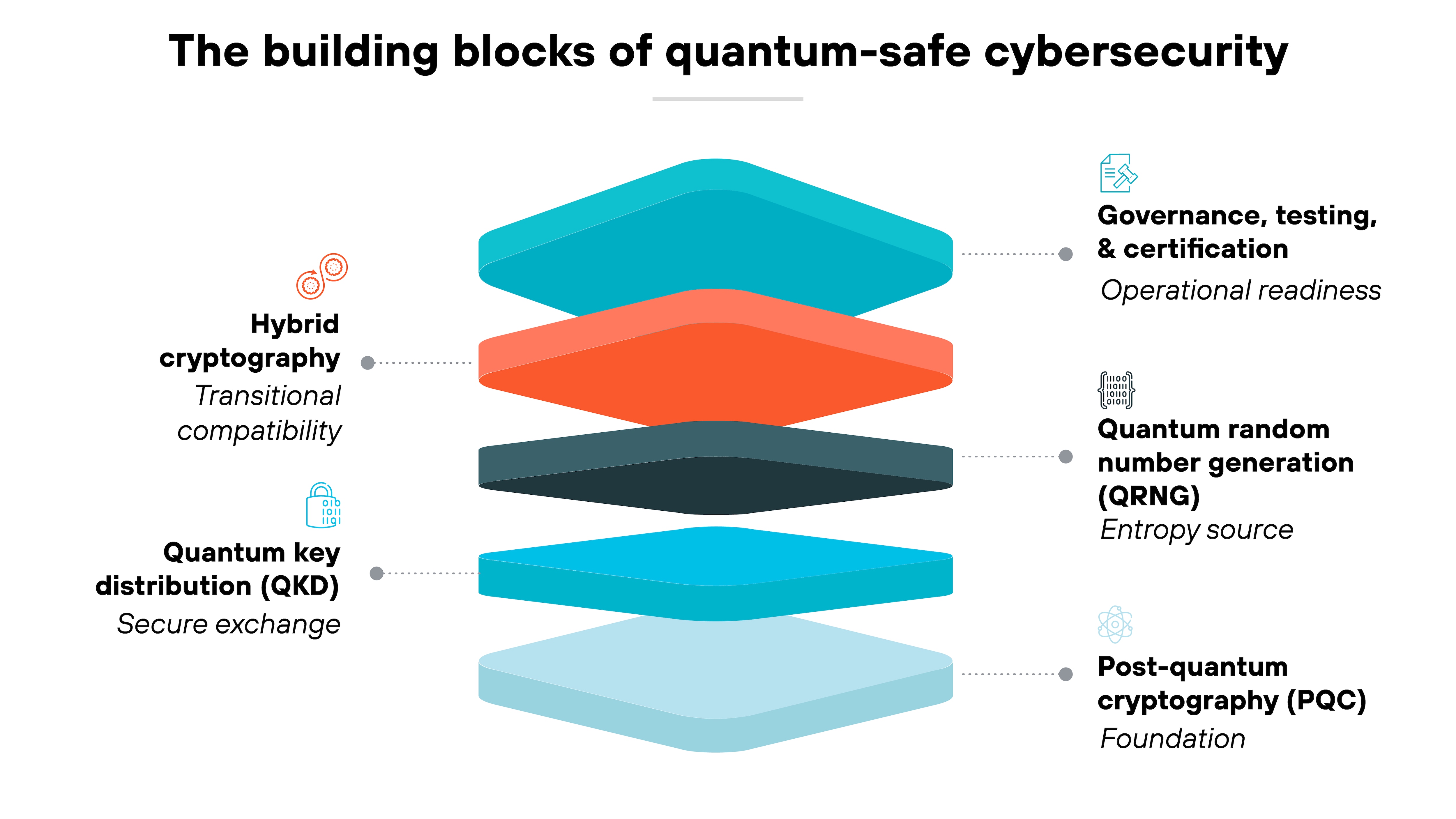
The path forward is already taking shape. The next phase of quantum-safe cybersecurity will focus on building systems that can withstand both classical and quantum attacks.
The foundation of that shift is post-quantum cryptography (PQC). It's designed to replace today's vulnerable public-key algorithms with new ones that rely on math problems resistant to quantum computation.
As mentioned, NIST’s post-quantum cryptography (PQC) standards—ML-KEM, ML-DSA, and SLH-DSA—are finalized as FIPS 203 through 205, with FN-DSA (FALCON) in draft and expected to follow as an additional digital signature standard.
However:
PQC isn't the only piece of the puzzle. Complementary technologies are emerging to strengthen the security stack even further:
- Quantum key distribution (QKD) uses quantum physics itself to detect eavesdropping during key exchange.
- Quantum random number generators (QRNGs) provide true entropy for cryptographic operations, eliminating bias and predictability in key creation.
Together, they enhance resilience in environments where high assurance is critical.
Enterprises are also experimenting with hybrid cryptography—combining classical and post-quantum algorithms for smoother migration. That approach allows organizations to adopt new standards without breaking compatibility across legacy systems.
At the same time, governments and vendors are building out toolkits, certification programs, and automated testing frameworks to speed up deployment.
Investment is accelerating too.
Quantum-safe products and readiness services are rapidly expanding, especially in finance, defense, and telecommunications.
And as more organizations perform cryptographic inventories and implement agility frameworks, the ecosystem as a whole is maturing.
What it comes down to:
The quantum revolution is inevitable. But so is the path to security.
Through preparation, agility, and collaboration, the world is already laying the groundwork for a quantum-safe future.
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- What Is a Quantum Random Number Generator?
