- What Is Attack Surface Management?
- What Is Exposure Management?
- What Are the Types and Roles of Attack Surface Management (ASM)?
-
What Are Common Use Cases for Attack Surface Management?
- What Is the Purpose of Attack Surface Management?
- Decoding the Attack Surface: Ten Examples
- Understanding ASM from the Threat Actor’s Perspective
- Ethical Hackers and Attack Surface Management: A Unique Use Case
- Examples of Attack Surface Management Use Cases
- Common Use Cases for Attack Surface Management FAQ
- What Is Continuous Threat Exposure Management (CTEM)?
- How Does a CISO Effectively Manage the Attack Surface?
- What Is the Attack Surface Management (ASM) Lifecycle?
- ASM Tools: How to Evaluate and Select the Best Option
- What is the Difference Between Attack Surface and Threat Surface?
-
What Is External Attack Surface Management (EASM)?
- External Attack Surface Management Explained
- Internal vs. External Attack Surface Management
- How External Attack Surface Management Works
- Why EASM Is Important
- Use Cases for External Attack Surface Management
- Benefits of EASM
- Approaches to Attack Surface Management
- EASM Challenges
- How to Choose an Attack Surface Management Platform
- External Attack Surface Management FAQs
What is Attack Surface Assessment?
An attack surface assessment involves identifying and evaluating cloud-based and on-premises internet-facing assets as well as prioritizing how to fix potential vulnerabilities and threats before they can be exploited. Organizations should use attack surface assessments to jump-start or improve an attack surface management program and reduce the risk of successful cyberattacks.
What Is an Attack Surface?
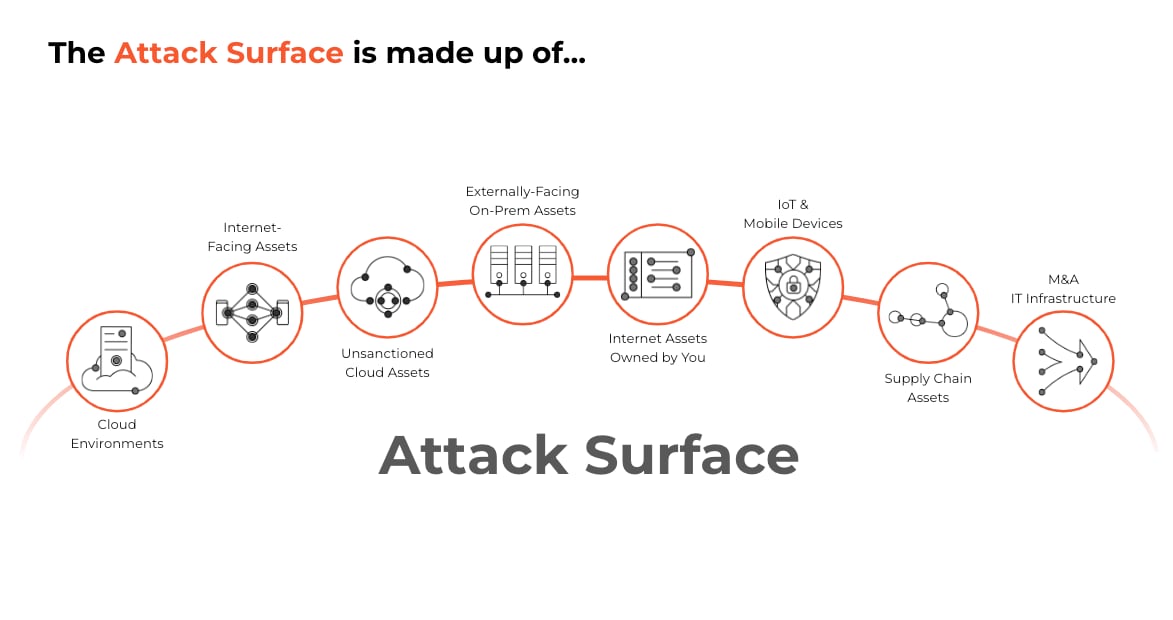
An attack surface refers to all the possible ways an attacker can interact with internet-facing systems or networks in order to exploit vulnerabilities and gain unauthorized access. These may include cloud-based and on-premises asset entry points, such as network ports, services and application interfaces, as well as the code and processes that protect them.
For example, company websites, servers in the cloud and supply chain partner systems are just some of the assets a threat actor might seek to exploit to gain unauthorized access. Flaws in processes, such as poor password management, insufficient asset inventories or unpatched applications and open-source code, can broaden the attack surface. The larger the attack surface, the more opportunities an attacker has to compromise an organization and steal, manipulate or disrupt data.
Types of Attack Surfaces
There are various types of common attack surfaces a threat actor might take advantage of, including digital, physical and social engineering attack surfaces.
Digital Attack Surface
Digital attacks are executed through interactions with digital systems or networks. The digital attack surface refers to the collective digital entry points and interfaces through which threat actors can gain unauthorized access or cause harm, such as network ports, cloud services, remote desktop protocols, applications, databases and third-party interfaces. It also refers to code that protects digital assets and any valuable data held within them. A digital attack surface assessment can include identifying vulnerabilities in processes surrounding digital assets, such as authentication and authorization processes, data breach and cybersecurity awareness training, and security audits.
Physical Attack Surface
Physical attacks on systems or infrastructure can vary greatly but might include theft, vandalism, physical installation of malware or exfiltration of data through a physical device like a USB drive. The physical attack surface refers to all ways in which an attacker can physically gain unauthorized access to the IT infrastructure. This includes all physical entry points and interfaces through which a threat actor can enter an office building or employee's home, or ways in which an attacker might access devices such as laptops or phones in public. In addition, vulnerabilities in processes designed to prevent unauthorized access to an organization are considered part of the physical attack surface. This might include on-premises security, including cameras, security guards, and fob or card systems, or off-premise precautions, such as password guidelines and two-factor authentication protocols. The physical attack surface also includes vulnerabilities related to physical devices such as routers, servers and other hardware. If this type of attack is successful, the next step is often to expand the attack to the digital attack surface.
Social Engineering Attack Surface
Social engineering attacks are based on psychological manipulation and deception and may be launched through various communication channels, including email, text, phone or social media. The goal of this type of attack is to find a path into the organization to expand and compromise the digital attack surface. Popular attack methods include phishing, baiting, pretexting and scareware, all designed to trick the victim into handing over sensitive information or performing actions that compromise systems. The social engineering attack surface refers to the collective ways an attacker can exploit human behavior, trust and emotions to gain unauthorized access to networks or systems.
Examples of Attack Surfaces
Examples of attack surfaces vary by category and should be monitored according to their size, scope, risk factor and complexity:
- Within the digital attack surface category, there are several areas organizations should be prepared to monitor, including the overall network as well as specific cloud-based and on-premises hosts, servers and applications.
- The network attack surface includes items such as ports, protocols and services. Examples include open ports on a firewall, unpatched software vulnerabilities and insecure wireless networks.
- Host-based attack surfaces refer to all entry points on a specific host or device, such as the operating system, configuration settings and installed software. Unpatched vulnerabilities, poor password health and misconfigurations are common in host-based attack surfaces. Misconfigurations are an especially big problem with cloud-based assets.
- The application-based attack surface refers to a specific application, with weaknesses often appearing in open-source code, interfaces and databases. Examples include Log4Shell, SQL injection vulnerabilities and insecure file access.
How to Reduce Attack Surfaces
Organizations’ attack surfaces are constantly evolving and, in doing so, often become more complex and difficult to protect from threat actors. But detection and mitigation efforts must keep pace with the evolution of cyberattacks. What's more, compliance continues to become increasingly important, and organizations considered at high risk of cyberattacks often pay higher insurance premiums. As such, it’s important for organizations to lower their cyber risk and position themselves with the best chance of protecting against cyberattacks. This can be achieved by taking steps to reduce the attack surface as much as possible, with documentation of cybersecurity improvements that can be shared with CxOs, cyber insurance carriers and the board.
1. Identify on-premises and cloud-based assets and infrastructure
Before you can begin reducing the attack surface, it's imperative to have a clear and comprehensive view of its scope. The first step is to perform reconnaissance across the entire IT ecosystem and identify every asset (physical and digital) that makes up the organization's infrastructure. This includes all hardware, software, networks and devices connected to your organization's systems, including shadow IT and unknown or unmanaged assets. It's also essential to assess how each component is utilized and how all assets are connected. Identifying the attack surface lets you see the organization from an attacker's viewpoint and remediate vulnerabilities before they're exploited.
2. Review policies related to asset management
Existing policies and procedures offer an excellent basis for identifying cybersecurity program strengths and gaps. These might include security protocols, access controls, interactions with supply chain vendors and other third parties, and incident response plans. Any obvious gaps in policies should be addressed quickly. It is often helpful to simulate security incidents to test the effectiveness of your policies and ensure everyone knows their role before they are needed in a real crisis.
3. Eliminate or reduce complexity
Systems and networks can be unnecessarily complex, often due to adding newer tools to legacy systems or moving infrastructure to the cloud without understanding how your security must change. The ease of adding workloads to the cloud is great for business but can increase shadow IT and your overall attack surface. Unfortunately, complexity can make it difficult to identify and address vulnerabilities. As such, a key step in reducing the attack surface is conducting an audit and eliminating, locking down or simplifying internet-facing services and protocols as needed. This will, in turn, ensure systems and networks are more secure and easier to manage. This might include reducing the number of access points, implementing access controls and network segmentation, and removing unnecessary and default accounts and permissions.
4. Prioritize the most important crucial attack points
Of course, the attack surface of most organizations is incredibly complex, and it can be overwhelming to try to address the whole area simultaneously. Instead, determine which assets, applications, or accounts represent the highest risk vulnerabilities and prioritize remediating those first. These might be assets, applications, or accounts critical to operations or those most likely to be targeted by threat actors.
5. Conduct regular attack surface analyses
An attack surface assessment is not a one-and-done activity. Reducing the attack surface is an ongoing process as your business grows, people leave the organization, or you add workloads to the cloud so it's important to frequently assess your security posture and seek new ways to improve it. Regularly conducting an attack surface analysis and vulnerability scanning can help you identify new threats and points of exploitation that may have emerged since the last assessment. This includes keeping software and systems updated, monitoring for new threats and vulnerabilities, and regularly reviewing access controls and security protocols to ensure they are still effective.
The attack surface is a broader cybersecurity term that encompasses all internet-facing assets, both known and unknown, and the different ways an attacker can try to compromise a system or network. It refers to all the potential ways an attacker can interact with a system or network, exploit vulnerabilities, and gain unauthorized access.
A significant change, such as a merger or acquisition, will likely expand or alter the attack surface. This might also be the case if the organization is in a high-growth stage, expanding its cloud presence, or launching a new product or service. In those cases, an attack surface assessment should be a priority.
Of course, if an organization has never undergone such an assessment or needs help starting an attack surface management program, then it's certainly a good idea to conduct one. It's also wise to conduct an assessment after a security breach or attempted attack, which indicates current security controls may be inadequate.


