- Buy or Build: Calculating ASPM ROI for Your Organization
- ASPM: The Evolution Beyond ASOC
- Overcoming AppSec Chaos: 7 Modes of ASPM Adoption
- Interactive Application Testing & ASPM: Closing DevSec Gaps
-
State of ASPM 2026: Key Trends & Emerging Threats
- ASPM Market Evolution and Adoption Trajectory
- AI-Native ASPM and Machine Learning Integration
- Cloud-Native Security Challenges and Container Orchestration Threats
- Software Supply Chain Vulnerabilities and SBOM Evolution
- DevSecOps Integration and Future ASPM Architecture
- ASPM Key Trends & Threats FAQs
- How DSPM Is Evolving: Key Trends to Watch
- Top Cloud Data Security Solutions
- Selecting Your ASPM Solution: Metrics That Matter
- ASPM in Action: 8 Real‑World Use Cases
-
Application Security Best Practices You Can’t Skip in ASPM
- ASPM Architecture: From Tool Sprawl to Unified Intelligence
- Advanced Risk Correlation and Contextual Prioritization Systems
- Policy-Driven Security Automation and Enforcement Architecture
- Seamless DevOps Integration and Cloud-Native Security Orchestration
- Enterprise Scalability, Performance Engineering, and Compliance Automation
- Application Security In ASPM Best Practices FAQs
-
How Supply Chain Threats Are Shaping ASPM Today
- The Supply Chain Attack Surface in Modern ASPM
- Critical Supply Chain Vectors Driving ASPM Evolution
- Software Supply Chain Risk Assessment and Prioritization
- Architectural Shifts in ASPM for Supply Chain Defense
- Operationalizing Supply Chain Security Within ASPM Programs
- Supply Chain Threats Are Shaping ASPM FAQs
-
How ASPM Strengthens Your Cloud Ecosystem
- ASPM's Role in Unified Cloud Security Architecture
- Integration Points Across the Cloud Security Stack
- Risk Intelligence and Contextual Prioritization in Cloud Environments
- Operational Efficiency Through Automated Cloud Security Workflows
- Strategic Advantages for Cloud-First Organizations
- ASPM Strengthening the Entire Cloud Ecosystem FAQs
-
Developer Infrastructure Posture: Integrating ASPM Early
- Understanding Developer Infrastructure Posture
- ASPM Fundamentals: Beyond Traditional Application Security
- Early Integration Strategies: Embedding ASPM in Developer Workflows
- ASPM Compliance Framework Integration
- Risk Prioritization and Remediation at Scale
- Developer Infrastructure Posture Management and ASPM FAQs
- Amplify ASPM with RBVM Risk‑Based Vulnerability Management
- CNAPP and ASPM Collaboration, Not Collision
- CSPM Vs ASPM: Where Your Focus Belongs
-
Why You Need Static Analysis, Dynamic Analysis, and Machine Learning?
-
What Is a Software Bill of Materials (SBOM)?
- Software Bill of Materials Explained
- Who Should Have a SBOM
- The Role of SBOMs in Cybersecurity and Compliance
- Why Is an SBOM Important?
- Software Composition Analysis and SBOMs
- How Does an SBOM Help Prevent Open-Source Supply Chain Attacks
- SBOM Formats
- Software Bill of Materials Best Practices
- SBOM FAQs
- What Is Policy-as-Code?
- What Is Static Application Security Testing (SAST)?
- What Is Code Security?
- What Is Software Composition Analysis (SCA)?
- What is Infrastructure-as-Code Security
- What is IaC?
- What Is Secrets Management?
- What Is Infrastructure as Code (IaC) Supply Chain Security?
- ASPM Tools: Evaluation Criteria and How to Select the Best Option
What Is Application Security Posture Management (ASPM)?
Application security posture management (ASPM) is a comprehensive approach to managing and enhancing the security of an organization's applications throughout their lifecycle. It combines continuous assessment, automated vulnerability management, and centralized policy enforcement to provide a holistic view of an application's security landscape — including its services, libraries, APIs, attack surfaces, and data flows. ASPM helps teams prioritize risks, streamline remediation, and maintain a strong security posture across diverse development environments and cloud infrastructures.
Application Security Posture Management (ASPM) Explained
Application security posture management involves continuously monitoring and improving the security posture of applications throughout their lifecycle. It integrates a system of security measures that include:
- Continuously assesses and monitors application security across development environments and cloud infrastructures.
- Integrates with various security testing tools, development pipelines, and ticketing systems to create a holistic view of an organization's application security landscape.
- Automates vulnerability detection, correlation, and prioritization based on risk and business impact.
- Centralizes policy management and enforcement to ensure consistent security practices across teams and projects.
- Provides contextual insights and risk-based scoring to help teams focus on the most critical security issues.
- Offers visibility into sensitive data flows and tracks changes (drift) in application architecture and dependencies.
- Facilitates collaboration between security and development teams by streamlining remediation workflows and providing a single source of truth for application security status.
ASPM often integrates with DevSecOps pipelines, ensuring that security measures are applied consistently from development to production. Advanced ASPM solutions use AI and machine learning to predict potential threats and recommend proactive measures. By consolidating and automating these functions, ASPM helps organizations scale their application security efforts while improving security posture.
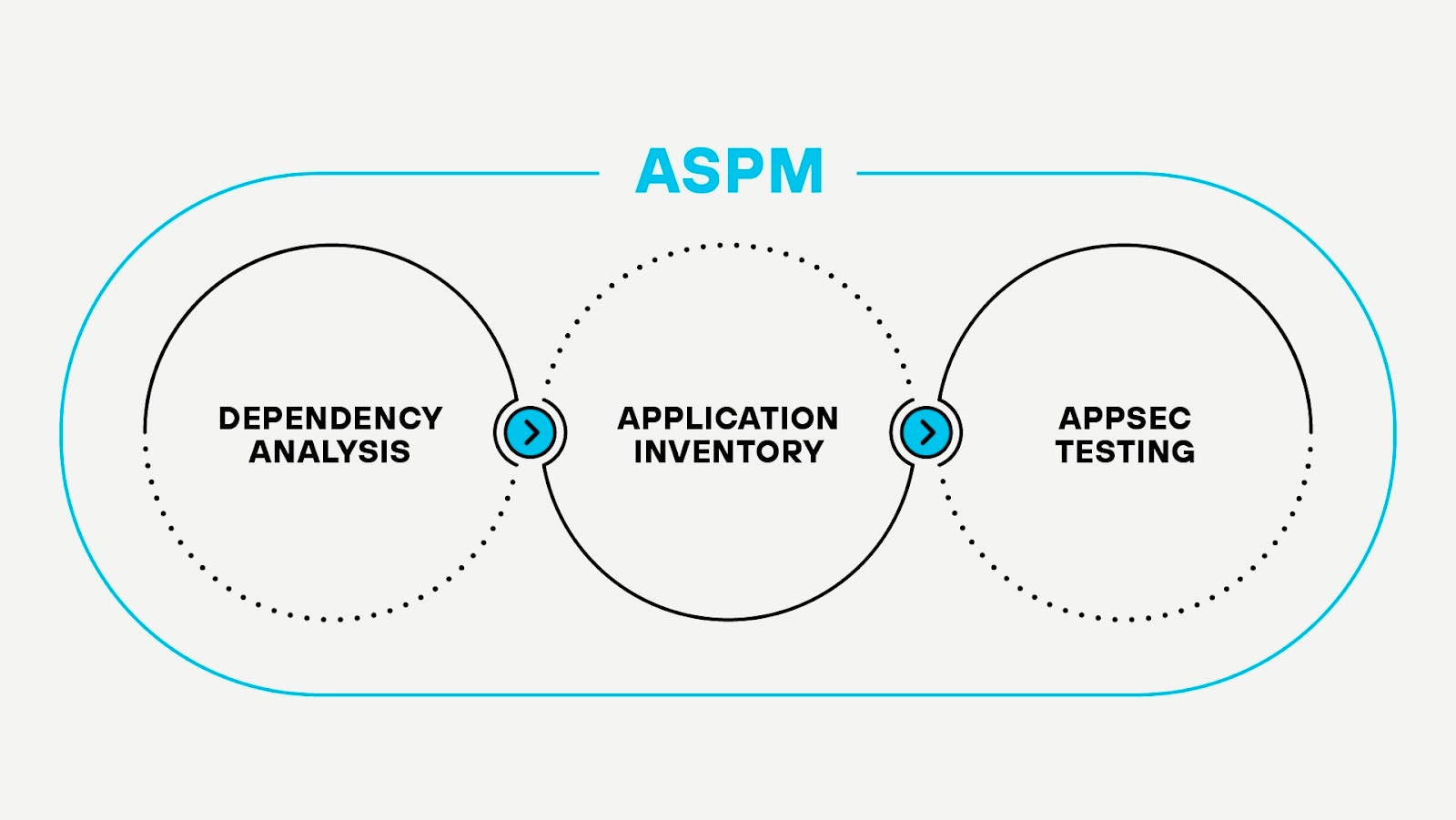
Why Is ASPM Important?
By proactively identifying and addressing vulnerabilities, ASPM helps prevent security breaches that could lead to data loss, financial damage, and reputational harm. Organizations face increasingly complex and dynamic application environments, making it essential to have a comprehensive strategy that defends against existing and emerging threats.
ASPM provides the necessary visibility and control to manage these complexities. Regulatory compliance demands stringent security practices, and ASPM aids in meeting these standards, helping organizations to avoid legal penalties and lose customer trust. Effective ASPM also advances a culture of security awareness and accountability among development and operations teams, ultimately leading to more secure and resilient applications.
The Role of ASPM in Cyber Defense
ASPM focuses on managing and improving the security posture of applications throughout their lifecycle, from development to deployment and beyond.
In the development phase, ASPM tools integrate with CI/CD pipelines to identify vulnerabilities and misconfigurations in code before it moves to production. Shifting left allows developers to address issues early and reduce the risk of security incidents, which reduces the time and cost associated with fixing vulnerabilities post-deployment.
Once applications are deployed, ASPM continues to provide value by continuously monitoring for vulnerabilities, misconfigurations, and potential threats. Collecting data from multiple sources — coupled with ongoing surveillance — it maintains a comprehensive view of the application's security posture.
ASPM boosts incident response capabilities. By providing high-priority, near real-time alerts, it allows organizations to swiftly respond to threats, minimizing the impact of security incidents. Security teams can use the insights gained from ASPM to perform root-cause analysis and implement corrective actions in a manner that prevents future occurrences of similar threats.
Additionally, ASPM supports compliance efforts by ensuring that applications adhere to industry regulations and standards. It streamlines the process of producing and verifying compliance reports, saving time and resources. Organizations can leverage ASPM to demonstrate their commitment to security and compliance to stakeholders, including customers, partners, and regulatory bodies.
ASPM: Business Value
ASPM delivers substantial business value to organizations, extending beyond its technical capabilities. Implementing an ASPM solution can significantly impact the organization's bottom line, risk posture, and operational efficiency.
Enhanced Risk Management and Decision-Making
By providing a comprehensive view of an organization's application security landscape, ASPM empowers executives to make informed, data-driven decisions. Leaders gain access to real-time insights and trend analyses, enabling them to allocate resources effectively. The ability to quantify and visualize security risks in business terms allows executives to communicate more precisely with board members and stakeholders, justifying security expenditures and demonstrating return on investment.
Accelerated Rollouts and Application Resilience
The ASPM platform's risk-based analysis correlates findings, assesses their potential impact, and prioritizes vulnerabilities based on severity, exploitability, and business impact. By automating security processes and providing real-time monitoring, ASPM ensures that applications remain resilient against emerging threats. These capabilities empower organizations to build and maintain secure, high-quality applications that can withstand evolving cyberthreats and minimize the risk of breaches or system failures.
ASPM supports and accelerates digital transformation initiatives. Executives can confidently drive innovation and digital initiatives, knowing that security measures are keeping pace with technological advancements.
Preserved Brand Reputation and Customer Trust
In an era where data breaches make headlines, a reliable application security posture is a competitive advantage. ASPM enables organizations to proactively address security vulnerabilities, reducing the likelihood of high-profile security incidents. Organizations can leverage this enhanced security stance to build customer trust, differentiate their products in the market, and potentially command premium pricing for services perceived as more secure.
Operational Efficiency and Cost Reduction
ASPM drives operational efficiencies across the organization by automating many aspects of security management. Reduced manual effort in security assessments, vulnerability management, and compliance reporting translates to significant cost savings. Furthermore, by shifting security left in the development process, ASPM helps catch and address vulnerabilities earlier, dramatically reducing the cost of remediation. Executives can appreciate the long-term cost benefits of preventing security issues rather than addressing them reactively.
Improved Collaboration and Security Culture
ASPM improves collaboration between security and development teams by integrating security checks directly into the development workflow. Developers receive timely, contextual feedback on potential security issues, allowing them to address vulnerabilities early in the development cycle. The streamlined communication and shared visibility provided by ASPM platforms minimize delays and reduce the need for rework late in the development process. As a result, friction is reduced and the release of secure software is accelerated.
Visibility into security metrics and risks encourages collaboration. Executives benefit from improved cross-functional alignment as it leads to heightened problem-solving and a shared responsibility for security outcomes.
Competitive Edge in Mergers and Acquisitions
During mergers and acquisitions, a well-implemented ASPM solution can provide a reliable picture of the security posture of both the acquiring company and the target. Organizations gain valuable insights into potential security risks associated with the acquisition, enabling more informed decision-making and potentially influencing deal valuations. Post-acquisition, ASPM facilitates the smooth integration of new applications and systems into the existing security framework.
Agility in Responding to Market Changes
ASPM enables organizations to adapt quickly to changing market conditions and customer demands. By providing a clear view of the security implications of new applications or features, executives can make rapid decisions about product launches or service expansions. The ability to assess and mitigate security risks in real-time allows organizations to seize market opportunities without compromising on security.
Talent Attraction and Retention
A strong commitment to application security, demonstrated through the implementation of advanced solutions like ASPM, can be a powerful draw for top talent in the technology sector. Executives can leverage their investment in cutting-edge security practices as a recruiting tool, attracting skilled professionals who value working with state-of-the-art technologies and best practices.
Long-Term Strategic Planning
ASPM provides executives with valuable data and trends that inform long-term strategic planning. By analyzing historical security data and identifying patterns, leaders can anticipate future security needs, plan for technology investments, and align security strategies with broader business objectives. The predictive capabilities of advanced ASPM solutions enable proactive rather than reactive security planning, ensuring the organization stays ahead of emerging threats and technological shifts.
Comparing ASPM with Other Security Technologies
By understanding various security categories and solutions, organizations can better determine which technology aligns with their security needs and strategies.
ASPM Vs. AST
Application security posture management and application security testing (AST) serve different but complementary roles in application security. AST tools, such as static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA), focus on scanning applications to identify vulnerabilities at various stages of the software development lifecycle. These tools generate numerous findings, including false positives and duplicates, which can overwhelm development and security teams.
ASPM addresses these limitations by aggregating and analyzing findings from multiple AST tools. It distills the vast quantity of alerts into the most critical issues, allowing developers to focus on true positives that significantly impact risk. ASPM provides a holistic view of application security, enabling better prioritization and management of vulnerabilities across the entire application lifecycle.
Related Article: Infrastructure as Code Security and AppSec: Streamlined DevSecOps From App to Infra
ASPM Vs. ASOC
Application security orchestration and correlation (ASOC) and ASPM share some similarities, but ASPM extends the capabilities of ASOC. ASOC solutions focus on orchestrating security testing processes and consolidating scan results to correlate findings and prioritize remediation efforts. They help streamline the management of security testing activities and improve the efficiency of vulnerability management.
ASPM builds on ASOC by incorporating DevSecOps practices and providing comprehensive visibility into application security. It emphasizes a risk-based approach, enabling organizations to prioritize vulnerabilities based on their potential impact. ASPM can be seen as an evolution of ASOC, offering a more integrated and holistic approach to managing application security.
ASPM Vs. CSPM
Cloud security posture management (CSPM) and ASPM target different layers of the IT stack. CSPM focuses on securing cloud infrastructure by detecting and mitigating misconfigurations and risks within cloud environments. It provides observability into cloud resources, ensuring that the infrastructure adheres to security best practices and compliance requirements.
In contrast, ASPM manages the security posture of applications, from design through production. It aggregates findings from AST tools to provide visibility and risk-based prioritization of application vulnerabilities. While CSPM ensures the cloud environment is secure, ASPM ensures the applications running within that environment are secure.
ASPM Vs. CNAPP
Cloud-native application protection platforms (CNAPP) and ASPM both aim to enhance application security but focus on different aspects. CNAPP is designed to protect cloud-native applications by integrating various security capabilities, such as container scanning, cloud security posture management, infrastructure as code scanning, and runtime protection. It provides specialized security controls tailored to the unique requirements of cloud-native environments.
ASPM focuses on managing the overall security posture of applications, regardless of their deployment environment. It consolidates security findings from various scanning tools and provides risk-based prioritization and automated workflows to manage vulnerabilities throughout the application lifecycle. While CNAPP is tailored for cloud-native applications, ASPM offers a broader approach that can be applied to applications across diverse environments.
ASPM Vs. CASB
While ASPM secures the applications, cloud access security broker (CASB) focuses on securing the interactions between users and cloud services. ASPM provides deep insights into application vulnerabilities and helps prioritize remediation efforts, whereas CASB addresses visibility and control over cloud usage. They offer capabilities such as data loss prevention (DLP), threat protection, and compliance monitoring to ensure that data moving to and from cloud services is secure and compliant.
Together, ASPM and CASB provide a comprehensive security framework, addressing both application-level security and cloud service interactions.
How ASPM Works
ASPM serves several critical functions to enhance the security of applications.
Up-to-Date Inventory
ASPM automatically catalogs and maintains a comprehensive inventory of an organization's applications and their dependencies, including library, configuration file, microservices, APIs, databases, third-party services, and environment variables within an organization's software ecosystem. Teams gain a clear understanding of the architecture and potential security risks through continuous and dynamic inventory management. By indexing and baselining all elements, ASPM provides a reliable foundation for risk analysis and security posture insights.
Vulnerability Prioritization
Dynamic contextual insights from ASPM correlate security findings from application security testing (AST) tools, code repositories, static metadata, and runtime environments. Centralization offers a comprehensive view of risk across the organization, equipping teams to triage and remediate individual findings efficiently and effectively.
Additionally, ASPM assesses and prioritizes risks, including business risks associated with application vulnerabilities. Risk scores, assigned based on potential business impact, allow organizations to focus on addressing the most critical security issues first. A risk-based approach ensures efficient resource allocation to mitigate the most significant threats.
Related Article: Security Theater: Who Cares About Your AppSec Findings?
Data Intel
Sensitive data, such as personally identifiable information (PII), protected health information (PHI), and payment card information (PCI), are identified and mapped within applications by ASPM. Teams can assess risks based on the type of data that might be exposed, ensuring compliance with data protection regulations. Understanding data flows across applications and systems helps prevent data leakage and unauthorized access.
Drift Awareness
By establishing a baseline for application architecture and implementing version control, ASPM manages drift effectively. It detects unauthorized or unexpected changes in application code or configuration that could introduce new security risks. Monitoring for drift ensures that applications remain secure over time and that deviations from the baseline are promptly addressed.
Policy Enforcement
Security policies across the software development lifecycle (SDLC) are enforced by ASPM. By automating policy checks and providing visibility into compliance status, it ensures that applications adhere to internal security standards and regulatory requirements. Maintaining consistent security practices and avoiding noncompliance penalties becomes easier with this capability.
Automation
Many aspects of traditional security reviews and testing are automated by ASPM, reducing the burden on security and development teams. Automated monitoring, vulnerability detection, risk scoring, and policy enforcement streamline processes, freeing teams to focus on strategic tasks. Continuous monitoring and automated remediation workflows, in particular, ensure that security controls remain effective and up to date.
Easy Deployment and Scaling
ASPM solutions are designed for easy deployment and scaling across development teams and environments. Seamless integration with existing DevSecOps pipelines and tools enables organizations to extend their security posture management efforts as they grow. Security practices keep pace with the rapid development and deployment of applications, thanks to this scalability.
ASPM Use Cases
Application security posture management addresses several critical needs in modern application security.
Application Observability
Organizations gain comprehensive visibility into their application ecosystem through ASPM's aggregation of data from multiple security tools into a single interface. Teams can easily track the security posture of each application, ensuring no component is overlooked.
API Discovery
ASPM supports API security, helping organizations maintain a single-source-of-truth inventory of internal, external, and third-party APIs — including both known and unknown APIs. Gaining comprehensive visibility into their API landscape provides security teams with vital information about each API's purpose, data handling practices, exposure level, and criticality to business operations. What’s more, the continuous nature of ASPM's API discovery allows organizations to keep pace with evolving application environments. As new APIs are developed or existing ones are modified, the inventory updates automatically, ensuring that security teams always have a current, accurate picture of their API landscape.
Compliance and Reporting
Meeting regulatory compliance requirements with regulations such as GDPR, HIPAA, and CCPA becomes easier with ASPM's automated policy enforcement and detailed audit report generation. Visibility into compliance status and demonstration of adherence to security best practices are provided through these reports. Continuous compliance is ensured through automated checks, reducing the risk of noncompliance penalties.
Incident Response and Remediation
Streamlined incident response and remediation are achieved through actionable insights and guidance on mitigating vulnerabilities. Automated workflows, such as ticket creation and escalation, enable security teams to respond to incidents more efficiently. Consequently, disruption is minimized and mean time to resolution (MTTR) is reduced, ensuring prompt addressing of vulnerabilities.
Disaster Recovery
In disaster recovery scenarios, having an accurate and up-to-date baseline is critical for restoring systems to their last known good state. Drift awareness ensures that any deviations from the baseline are identified and corrected, enabling a more reliable and efficient recovery process. This ASPM function minimizes downtime and ensures that restored systems are secure and compliant.
Top Considerations When Choosing an ASPM Solution
When selecting an ASPM solution, organizations must consider several broader factors beyond core functionalities. These considerations will help ensure the chosen solution aligns with the organization's specific needs, resources, and long-term goals.
Vendor Reputation and Support
Organizations should research potential ASPM vendors, evaluating their track record, industry reputation, and customer satisfaction levels. A vendor's longevity in the market, financial stability, and commitment to ongoing product development are crucial indicators of reliability. Robust customer support, including responsive helpdesk services, comprehensive documentation, and regular training sessions, can significantly impact the successful implementation and ongoing use of the ASPM solution.
Total Cost of Ownership
While the initial price tag is important, organizations must consider the total cost of ownership over time. Factors to evaluate include licensing models (per-user, per-application, or enterprise-wide), potential hardware requirements, ongoing maintenance costs, and any necessary staff training or additional personnel needs. Hidden costs, such as those associated with integrations or customizations, should also be factored into the decision-making process.
Integration Capabilities
An effective ASPM solution must seamlessly integrate with existing development and security tools. Look for a platform that can connect with various AppSec testing tools, developer tools, and issue trackers — or one built into a full-service CNAPP. The ability to pull data from development, deployment, and operations environments is foundational to application security.
Customization and Flexibility
Every organization has unique security needs and workflows. An ideal ASPM solution should offer a high degree of customization to adapt to specific organizational requirements. The ability to tailor dashboards, reports, and risk scoring models allow for better alignment with existing processes and more meaningful insights for stakeholders at various levels of the organization.
Compliance and Regulatory Alignment
For many organizations, especially those in highly regulated industries, compliance with specific standards and regulations is paramount. The chosen ASPM solution shouldn’t only support current compliance requirements but also demonstrate agility in adapting to evolving regulatory landscapes. Built-in compliance reporting features and the ability to map security controls to various regulatory frameworks can significantly streamline audit processes.
User Experience and Adoption
The effectiveness of an ASPM solution depends on its adoption across the organization. A user-friendly interface, intuitive navigation, and clear, actionable insights can encourage wider use among development, security, and operations teams. Solutions that offer role-based access and customizable views cater to the diverse needs of different stakeholders, from developers to C-level executives.
Integration Ecosystem
While core integrations are a priority, organizations should also consider the breadth and depth of the ASPM solution's integration ecosystem. A wide range of prebuilt integrations with popular development tools, cloud platforms, and security solutions can reduce implementation time and costs. Additionally, robust APIs and webhooks allow for custom integrations, enabling organizations to connect the ASPM solution with proprietary or niche tools in their technology stack.
Scalability and Performance
As organizations grow and their application portfolios expand, the chosen ASPM solution must be able to scale accordingly without significant performance degradation. Evaluating the solution's ability to handle increasing data volumes, support a growing number of users, and maintain responsiveness under load is crucial for long-term success.
Machine Learning and Predictive Capabilities
Advanced ASPM solutions leverage machine learning algorithms to enhance threat detection, prioritize risks, and provide predictive insights. Organizations should assess the maturity and effectiveness of these AI-driven features, as they can significantly improve the accuracy of risk assessments and the efficiency of security operations over time.
Vendor Lock-In Considerations
Organizations should carefully evaluate the potential for vendor lock-in when choosing an ASPM solution. The ability to export data in standard formats, the use of open APIs, and the ease of migrating to alternative solutions are important factors to consider. Avoiding excessive dependence on proprietary technologies or formats can provide flexibility and protect the organization's interests in the long run.
Future Roadmap and Innovation
Lastly, organizations should examine the vendor's product roadmap and commitment to innovation. A forward-thinking ASPM provider should demonstrate plans for incorporating emerging technologies, addressing evolving security challenges, and continuously improving their solution. Regular feature updates, a clear vision for future development, and responsiveness to customer feedback are indicators of a vendor's dedication to long-term product excellence.
By carefully weighing these broader considerations alongside core functionalities, organizations can make a more informed decision when selecting an ASPM solution that not only meets their current needs but also supports their long-term security and business objectives.
ASPM FAQs
SAST involves analyzing source code, bytecode, or binary code for security vulnerabilities without executing the program. It identifies flaws such as SQL injection, cross-site scripting (XSS), and buffer overflows by examining the codebase. SAST tools integrate into the development environment, providing real-time feedback to developers and allowing them to remediate issues early in the development lifecycle. They typically employ pattern matching, data flow analysis, and control flow analysis to pinpoint vulnerabilities.
Advanced SAST tools can handle complex codebases and support multiple programming languages and frameworks. By offering detailed insights into the code structure and potential security flaws, SAST helps organizations enforce secure coding practices, reduce the attack surface, and ensure compliance with industry standards and regulations.
DAST focuses on identifying security vulnerabilities in running applications. Unlike static analysis, DAST tests applications in their operational state, interacting with them via the frontend to simulate real-world attack scenarios.
DAST captures runtime issues such as authentication flaws, injection vulnerabilities, and misconfigurations that static analysis might miss. DAST tools typically employ automated scanners that probe applications for weaknesses, capturing HTTP requests and responses for analysis.
Runtime application self-protection (RASP) secures applications by detecting and mitigating threats in real time during execution. Integrated into the application or its runtime environment, RASP monitors and analyzes the application's behavior and context to identify malicious activities. When a threat is detected, RASP can take immediate actions such as blocking the execution, alerting security teams, or logging the incident for further analysis.
Unlike traditional perimeter defenses, RASP offers granular, context-aware protection that adapts to the application's state and environment. It can thwart sophisticated attacks like zero-day exploits and advanced persistent threats (APTs) by understanding the application's logic and flow.
Software composition analysis identifies and manages open-source components within an application's codebase. SCA tools scan the code to detect third-party libraries and dependencies, assessing them for known vulnerabilities, licensing issues, and compliance with organizational policies. They provide detailed reports on security risks, versioning, and remediation recommendations, enabling developers to address issues promptly.
Advanced SCA solutions integrate with CI/CD pipelines, offering real-time insights and automated alerts when new vulnerabilities are discovered. By maintaining an up-to-date inventory of open-source components, organizations can mitigate risks associated with outdated or unpatched libraries. SCA also supports legal and regulatory compliance by ensuring that software components adhere to licensing requirements. Shifting left in a proactive approach to managing open-source software significantly enhances application security.
Threat intelligence integration involves incorporating external and internal threat data into an organization's security operations. It provides actionable insights on emerging threats, attacker tactics, and potential vulnerabilities. Security teams use this data to enhance detection, response, and mitigation strategies.
Advanced threat intelligence platforms aggregate, normalize, and analyze data from multiple sources, including open-source feeds, commercial providers, and proprietary research. They use machine learning and analytical algorithms to identify patterns, correlate indicators of compromise (IOCs), and predict potential attack vectors.
By integrating threat intelligence into SIEM systems, firewalls, and endpoint protection solutions, organizations can proactively defend against sophisticated threats and improve overall situational awareness, significantly enhancing security posture.
Security orchestration, automation, and response (SOAR) streamlines and automates security operations, enhancing incident response capabilities. It integrates disparate security tools and systems, enabling seamless data sharing and coordinated actions.
SOAR platforms automate repetitive tasks like alert triage, incident investigation, and threat hunting, freeing up security analysts to focus on complex issues. They use playbooks — predefined workflows — to standardize response procedures, ensuring consistent and efficient handling of incidents.
Microservices security focuses on protecting applications built using a microservices architecture, where functionalities are broken down into loosely coupled, independently deployable services. Each microservice communicates over network protocols, making them susceptible to various attack vectors.
Security measures include mutual TLS for service-to-service encryption, authentication and authorization mechanisms, and API gateways for traffic management. Implementing security policies at the service mesh layer provides granular control over communication and access.
Microservices also require logging and monitoring for anomaly detection and incident response. Containerization, commonly used in microservices, adds an additional layer of security requirements, including image scanning and runtime protection. Effective microservices security ensures that each component maintains its integrity while contributing to the overall resilience of the application.
Container security involves protecting containerized environments throughout their lifecycle, from development to deployment and runtime. Containers encapsulate applications and their dependencies, making them portable but also introducing unique security challenges. Key practices include image scanning to detect vulnerabilities and misconfigurations before deployment.
Runtime security involves monitoring container behavior for anomalies, such as unauthorized network connections or file system changes. Implementing least privilege principles and enforcing network segmentation can mitigate risks. Orchestrators like Kubernetes require secure configurations and role-based access control to manage container clusters effectively. Additionally, maintaining an up-to-date registry of trusted images and leveraging automated patching mechanisms are vital.
API security focuses on protecting Application Programming Interfaces (APIs) from threats and vulnerabilities. APIs expose application functionalities and data to external and internal consumers, making them prime targets for attacks like injection, unauthorized access, and data breaches.
Security measures include implementing strong authentication and authorization mechanisms, such as OAuth and JWT tokens, to ensure that only legitimate users access APIs. Input validation and rate limiting prevent abuse and injection attacks. API gateways act as intermediaries, providing additional layers of security, including traffic monitoring, throttling, and threat detection. Encryption ensures data confidentiality during transmission. Regular security assessments, including penetration testing and code reviews, help identify and mitigate vulnerabilities.
Zero Trust architecture is a security model that assumes no implicit trust for any user or device inside or outside the network perimeter. It requires continuous verification of identities and strict access controls based on the principle of least privilege. Key components include multifactor authentication (MFA), microsegmentation, and end-to-end encryption.
Microsegmentation isolates network resources, limiting lateral movement in case of a breach. Identity and access management (IAM) systems enforce granular access policies, ensuring that users and devices have the minimum necessary permissions. Continuous monitoring and behavioral analytics detect anomalies and potential threats in real time. Zero Trust architecture reduces the attack surface and enhances an organization's security posture by enforcing rigorous verification and access controls for all interactions within the network.
CI/CD security focuses on integrating security practices into the CI/CD pipelines to ensure secure software delivery. It involves automated security checks at various stages, from code commits to deployment.
- Static and dynamic analysis tools scan the code for vulnerabilities during the build process, providing immediate feedback to developers. Software composition analysis identifies risks in open-source dependencies.
- Secrets management tools ensure that sensitive information like API keys and passwords are securely stored and accessed.
- Container and infrastructure-as-code security ensure that deployment environments are free from vulnerabilities and misconfigurations.
Implementing these security measures within the CI/CD pipeline enables organizations to identify and remediate issues early, ensuring that only secure code reaches production.
Security information and event management (SIEM) solutions aggregate and analyze security data from multiple sources to provide real-time insights and threat detection. They collect logs and events from network devices, servers, applications, and other security tools, normalizing the data for analysis.
Advanced SIEM systems employ correlation rules and machine learning algorithms to identify suspicious patterns and anomalies. They generate alerts for potential security incidents, prioritizing them based on risk and impact. Integration with threat intelligence feeds enhances the context for detected threats, enabling more accurate detection and response. SIEM platforms also support compliance reporting by providing detailed audit trails and logs. By centralizing and analyzing security data, SIEM helps organizations detect, investigate, and respond to security incidents more effectively.
Behavioral analytics focuses on monitoring and analyzing user and entity behavior to detect anomalies indicative of security threats. It employs machine learning algorithms to establish a baseline of normal behavior patterns for users, devices, and applications. Deviations from these baselines, such as unusual login times, abnormal data access, or unexpected network activity, trigger alerts.
Behavioral analytics can identify insider threats, compromised accounts, and advanced persistent threats (APTs) that traditional signature-based methods might miss. Integration with SIEM and SOAR systems enhances the overall threat detection and response capabilities. By continuously learning and adapting to evolving behaviors, behavioral analytics provides a dynamic and proactive approach to identifying and mitigating security risks in real-time.
Advanced persistent threats (APTs) are sophisticated, targeted cyberattacks carried out by well-funded adversaries, often nation-states or organized crime groups. APTs aim to gain and maintain unauthorized access to a network over an extended period, exfiltrating sensitive data or disrupting operations. They employ multiple attack vectors, including phishing, zero-day exploits, and social engineering, to infiltrate the target. Once inside, attackers use lateral movement techniques to navigate the network, often leveraging legitimate credentials and tools to avoid detection. Advanced evasion tactics, such as polymorphic malware and encrypted communication, make APTs particularly challenging to identify and mitigate.
Effective defense against APTs requires a multilayered security approach, including threat intelligence, continuous monitoring, behavioral analytics, and incident response capabilities.
Security policy enforcement involves implementing and maintaining security controls to ensure compliance with organizational policies and regulatory requirements. It encompasses access controls, data protection measures, and network security configurations.
Tools like firewalls, intrusion prevention systems (IPS), and endpoint protection platforms (EPP) enforce these policies at various levels. Automated compliance checks and audits validate adherence to established policies, generating reports for security teams and auditors. Role-based access control (RBAC) restricts access based on user roles, minimizing the risk of unauthorized actions. Continuous monitoring and real-time alerts enable rapid identification and remediation of policy violations.
Application security metrics quantify the effectiveness of security measures and provide insights into the overall security posture of applications. Key metrics include the number of vulnerabilities detected, mean time to remediation (MTTR), and the percentage of applications passing security tests. Metrics also track the frequency and severity of security incidents, code coverage by security testing tools, and compliance with security policies.
Advanced metrics may involve the rate of false positives and negatives in security scans and the impact of security issues on business operations. Dashboards and reports visualize these metrics, enabling security teams to identify trends, prioritize remediation efforts, and demonstrate improvements over time.
Security baselines establish minimum security standards for systems, applications, and networks. They define the configuration settings, access controls, and security measures required to mitigate common threats. Organizations use baselines to ensure consistent security across all assets, reducing the risk of vulnerabilities due to misconfigurations. Security baselines often derive from industry standards such as CIS Benchmarks or NIST guidelines and are tailored to the specific needs of the organization. Automated compliance checks validate adherence to these baselines, generating reports and alerts for deviations. Regular updates to baselines accommodate new threats and technological advancements.
Incident response automation streamlines and accelerates the detection, investigation, and remediation of security incidents using automated workflows and tools. It integrates with existing security infrastructure, such as SIEM and SOAR platforms, to orchestrate responses across multiple systems. In addition:
- Automated playbooks execute predefined actions for common incidents, including isolating affected systems, blocking malicious IP addresses, and notifying relevant stakeholders.
- Machine learning algorithms enhance detection accuracy by analyzing patterns and predicting potential threats.
- Real-time data correlation and enrichment provide comprehensive context, enabling faster decision-making.
- Incident response automation reduces response times, minimizes human error, and frees up security analysts to focus on high-priority tasks.