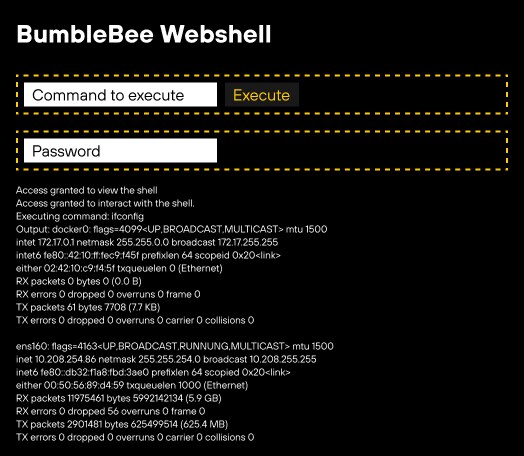
Escape Characters or Delimiters Injection
Special characters like escape characters and delimiters can be used to nest malicious contexts or scopes within innocuous-seeming prompts. By prematurely ending strings, introducing unexpected command sequences or shifting the context in which the LLM interprets the text, attackers can obscure prohibited phrases and subvert the LLM’s safety alignment.