Introducing ztna 2.0 Solution
A paradigm shift in secure access
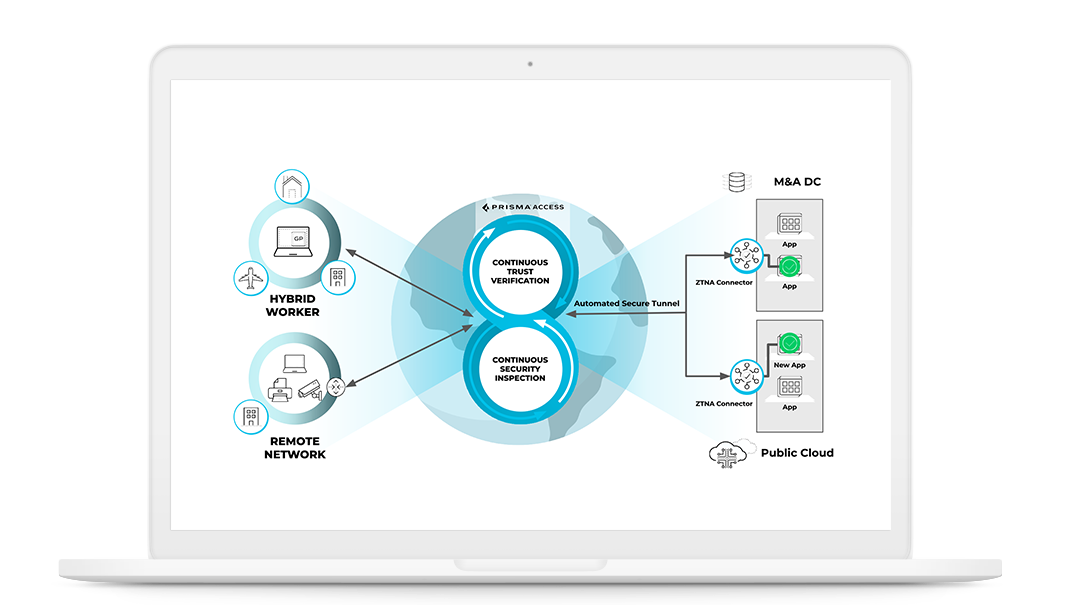
ZTNA 2.0 combines fine-grained, least- privileged access with continuous trust verification and deep, ongoing security inspection to protect all users, devices, apps, and data everywhere – all from a simple unified product.
- Superior security that stops zero-day threats in zero time
- Single-pane-of-glass visibility and management, consistent policy, and shared data for all users and all apps
- Cloud-native architecture provides uncompromised performance backed by leading SLAs
- Auto-discovery and onboarding of private applications - including automated tunnel management and routing - as well as support for apps in overlapped private networks.