- What Is Cyber Threat Intelligence (CTI)?
- What is an Exploit Kit?
- What is a Payload-Based Signature?
- Threat Intelligence Use Cases and Examples
- What is Digital Forensics and Incident Response (DFIR)?
-
What Is a Cybersecurity Risk Assessment?
- Cybersecurity Risk Assessment Explained
- Why Is Cyber Risk Assessment Important?
- Common Cybersecurity Risks and Threats
- Different Approaches to Cyber Risk
- How to Perform a Cybersecurity Risk Assessment
- Determine the Scope of the Assessment
- Cybersecurity Risk Assessment Benefits
- Cyber Risk Assessment FAQs
-
What is URL Filtering?
- What is an Intrusion Detection System?
-
What Is DNS?
-
What Is a Fast Flux Network?
- What Are Malicious Newly Registered Domains?
-
What is a Threat Intelligence Platform (TIP)?
- The Value of a Threat Intelligence Platform
- How Threat Intelligence Works
- Types and Examples of Threat Intelligence
- Why Do Organizations Need a Threat Intelligence Platform (TIP)?
- Key Characteristics of a Threat Intelligence Platform
- Types of Threat Intelligence Data
- Implementation of a Threat Intelligence Platform
- Threat Intelligence Platforms FAQs
- What Are Unknown Cyberthreats?
- What is an Intrusion Prevention System?
- What Are Cyberthreat Intelligence Tools?
- What is the Threat Intelligence Lifecycle?
- What are the Types of Cyberthreat Intelligence (CTI)?
- What Is Spear Phishing?
- What Is a Circuit Level Gateway?
- Firewall | Antivirus — What Is the Difference?
What Is Remote Browser Isolation (RBI)?
Remote browser isolation (RBI) is a web security technology that isolates users' internet browsing activities in a remote environment. By hosting browsing sessions on a separate server, RBI prevents web content from reaching and executing on the user's device. This approach safeguards against potential web threats while maintaining the browsing experience.
How Does Remote Browser Isolation Work?
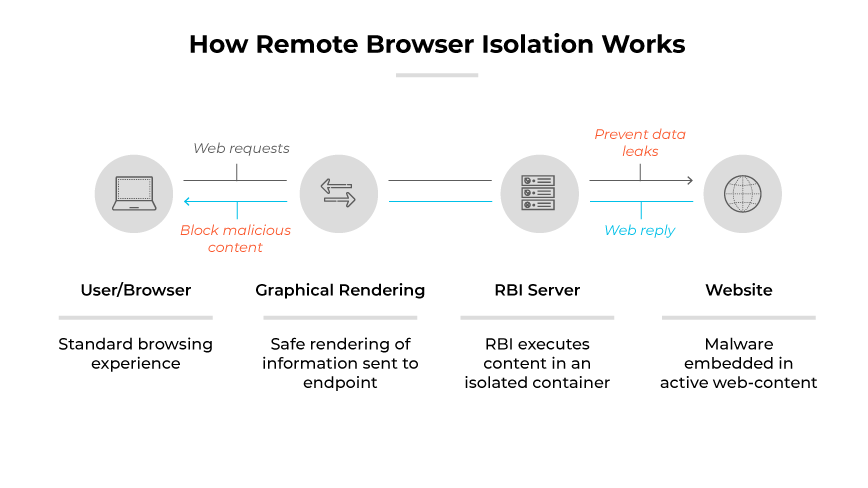
Remote browser isolation processes web content in a cloud-based, isolated environment. When a user attempts to access a webpage, the session is initiated within the remote container, away from the user's device. Any potential threats within the webpage are confined to this isolated space, preventing website code from executing on endpoints. The user then receives a safe, visual representation of the content.
This ensures that the user interacts only with a sanitized version of the webpage via the remote web browser, minimizing the risk of web-based threats. When encountering a website with potentially malicious code, RBI ensures that users are protected.
Evolution of Remote Browser Isolation
Remote browser isolation technologies have evolved over the years to balance performance with security. RBI has traditionally worked alongside secure web gateways, producing transient remote browser containers for potentially malicious websites and malicious content.
Remote browser isolation must also ensure unhindered access to internet users accessing webpages and applications. Running browser sessions remotely can disrupt user workflows, so RBI approaches have evolved to try and match web traffic and site interactivity demands over time.
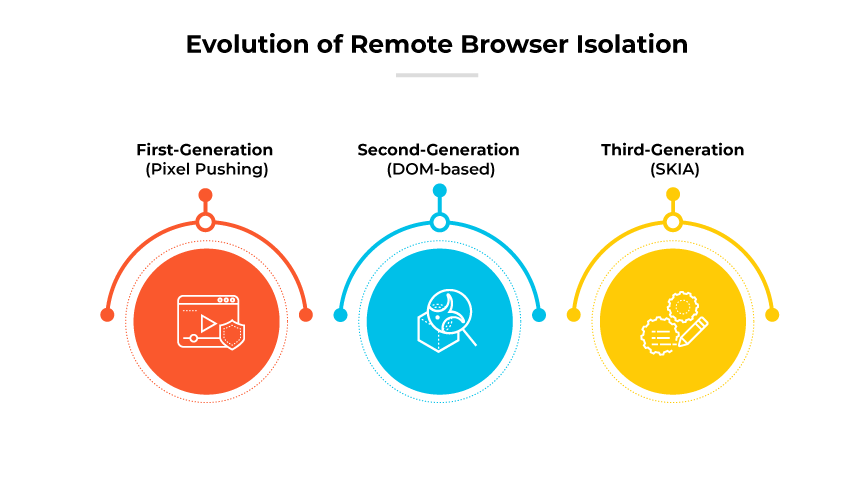
First Generation (Pixel Pushing)
This method processes web content on a remote server. It sends the visual representation of the page to user devices pixel by pixel. Pixel pushing ensures strong security through complete separation but demands high bandwidth. This increases costs and impacts user experience.
Second Generation (DOM-based)
This uses a Document Object Model (DOM) based method. It processes web content and then reconstructs the page on the user's device. The DOM-based method performs better than the pixel-pushing method but can expose users to malicious files and threats.
Third Generation (SKIA)
This uses an open-source 2D graphics library. It renders the webpage through a SKIA layer and addresses gaps found in pixel and DOM-based methods. The SKIA method lacks versatility for dynamic applications.
Why Is Remote Browser Isolation Important?
Migration to the cloud has made browsers essential tools for data access. This efficiency also exposes systems to vulnerabilities. Cybercriminals exploit browsers for cyberattacks using malicious extensions, malvertising, and browser-based trojans, among others. Interaction with compromised web content turns web browsing activity into potential threat entry points. In addition to browser-based attacks and vulnerabilities, zero-day malware can pose significant security risks. Unfortunately, there are no web security solutions that can address 100% of zero-day web attacks.
Individuals with access to critical data or privileged credentials, such as engineers, executives, and supply chain managers, are frequently targeted. Data breaches involving the human element account for 74% of cases.1 Protecting these individuals is paramount.
Remote browser isolation addresses these challenges by creating a web isolation mechanism that confines browser sessions in cloud-based sandboxes. This mechanism fully air-gaps web content from user devices, ensuring that even if malicious content is encountered, the threat is contained and doesn't reach the primary network. RBI serves as an added layer of security enforcement, especially against zero-day web threats, and offers a balanced approach to managing unknown or high-risk content without having to block it entirely.
1.Verizon 2023 Data Breach Investigations Report
Benefits of Remote Browser Isolation
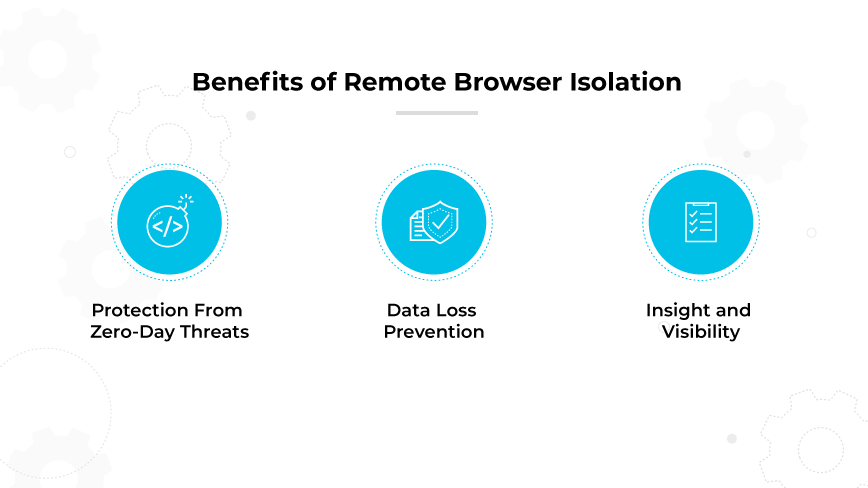
Protection from Zero-Day Threats
RBI ensures that users can access content on the web without any direct interaction with malicious elements. By isolating web sessions in the cloud, it delivers safe rendering of web content, effectively eliminating threats. RBI also minimizes the impact of novel browser vulnerabilities. Since the browsing session is isolated, even unidentified vulnerabilities have limited potential to cause harm.
Data Loss Prevention
RBI shields sensitive data from threats embedded in webpages or downloadable content. This approach reduces the risk of data breaches due to compromised pages or unsafe plugins. Additionally, RBI's data loss prevention controls restrict user actions like cutting, copying, pasting, printing, and entering keyboard inputs. RBI permits only remote rendering of files, further strengthening browser-based data protection.
Insight and Visibility
IT security teams can gain valuable insight into users' internet browsing activities, which can be used for compliance monitoring and regulatory audits. Organizations can even detect anomalous behavior that may be indicative of insider threats.
Challenges of Remote Browser Isolation
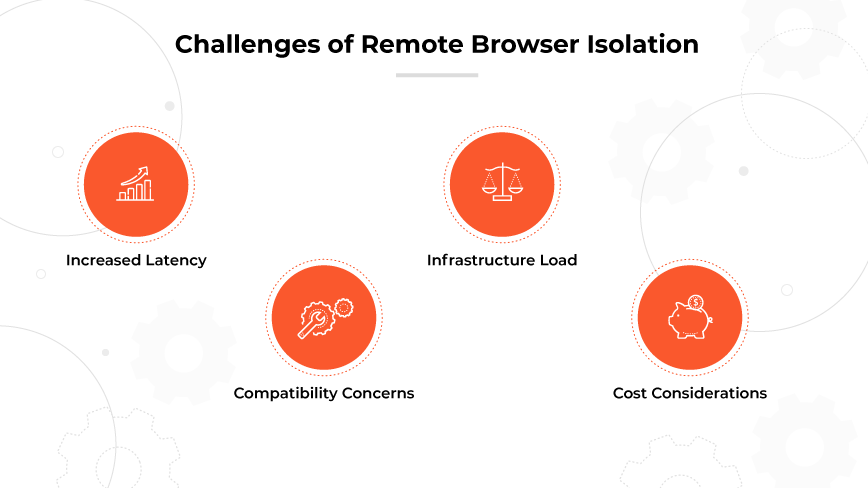
Increased Latency
RBI processes require redirecting browser traffic through a cloud-based system, which can introduce delays. Latency issues can lead to a suboptimal browsing experience for the user, especially when accessing content-rich webpages or streaming media.
Compatibility Concerns
Certain webpages with intricate designs or complex functionalities may not render properly in a remote browser environment. This can result in broken layouts, missing elements, or loss of interactive features, affecting the user's ability to interact with the website as intended.
Infrastructure Load
Implementing RBI means that all web content is streamed as visual data to users, demanding substantial bandwidth. Such extensive streaming can place a significant strain on existing infrastructure, potentially leading to slowdowns or disruptions.
Cost Considerations
Adopting remote browser isolation requires considerable computing resources. The need to route and analyze all of an organization's web traffic in the cloud can result in increased costs, especially when scaled across a large number of users or high-traffic environments.
The Role of RBI in SASE Architecture
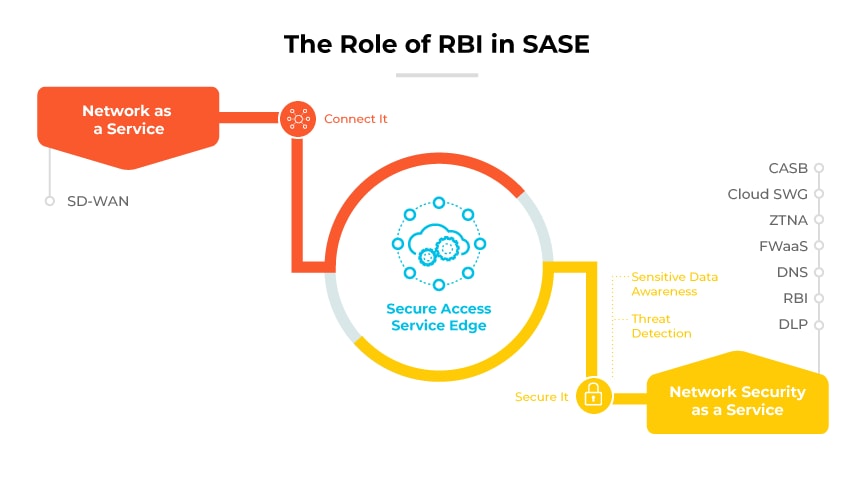
Secure Access Service Edge (SASE) architecture integrates networking and security services to provide comprehensive cloud-based protection. A pivotal component of this security structure is Remote Browser Isolation (RBI).
RBI operates on the foundational principle that web content is inherently risky. This method ensures that potential threats from the web do not reach the user's device.
Within the SASE framework, RBI complements secure web gateways (SWG). While SWG filters and monitors web traffic for threats, it can't guarantee complete safety from all zero-day threats. This is where RBI steps in. For web domains or pages deemed uncertain or risky, RBI provides an added layer of security.