- 1. What created the need for SD-WAN?
- 2. How does SD-WAN work?
- 3. What is SD-WAN architecture?
- 4. What are the benefits of SD-WAN?
- 5. What are the challenges associated with SD-WAN?
- 6. What are the different types of SD-WAN deployment models?
- 7. How secure is SD-WAN?
- 8. How to choose the best SD-WAN vendor for your business (and what to look for)
- 9. Top 10 SD-WAN best practices, tips, and tricks
- 10. What is the role of SD-WAN in SASE?
- 11. How is AI used in SD-WAN?
- 12. How SD-WAN works with complementary technologies
- 13. Comparing SD-WAN with other security and technology solutions
- 14. SD-WAN FAQs
- What created the need for SD-WAN?
- How does SD-WAN work?
- What is SD-WAN architecture?
- What are the benefits of SD-WAN?
- What are the challenges associated with SD-WAN?
- What are the different types of SD-WAN deployment models?
- How secure is SD-WAN?
- How to choose the best SD-WAN vendor for your business (and what to look for)
- Top 10 SD-WAN best practices, tips, and tricks
- What is the role of SD-WAN in SASE?
- How is AI used in SD-WAN?
- How SD-WAN works with complementary technologies
- Comparing SD-WAN with other security and technology solutions
- SD-WAN FAQs
What Is SD-WAN? | SD-WAN Meaning & Explanation [+How tos]
- What created the need for SD-WAN?
- How does SD-WAN work?
- What is SD-WAN architecture?
- What are the benefits of SD-WAN?
- What are the challenges associated with SD-WAN?
- What are the different types of SD-WAN deployment models?
- How secure is SD-WAN?
- How to choose the best SD-WAN vendor for your business (and what to look for)
- Top 10 SD-WAN best practices, tips, and tricks
- What is the role of SD-WAN in SASE?
- How is AI used in SD-WAN?
- How SD-WAN works with complementary technologies
- Comparing SD-WAN with other security and technology solutions
- SD-WAN FAQs
SD-WAN (software-defined wide area network) is a type of networking technology that uses software-defined networking (SDN) principles to manage and optimize wide area network (WAN) performance.
It gives organizations the ability to securely connect users, applications and data across multiple locations. Plus, it improves performance, reliability and scalability.
SD-WAN also simplifies WAN management by providing centralized control and visibility over the entire network.
What created the need for SD-WAN?
Businesses need SD-WAN because traditional wide area networks can’t keep up with how modern organizations operate, connect, and use applications.
More specifically:
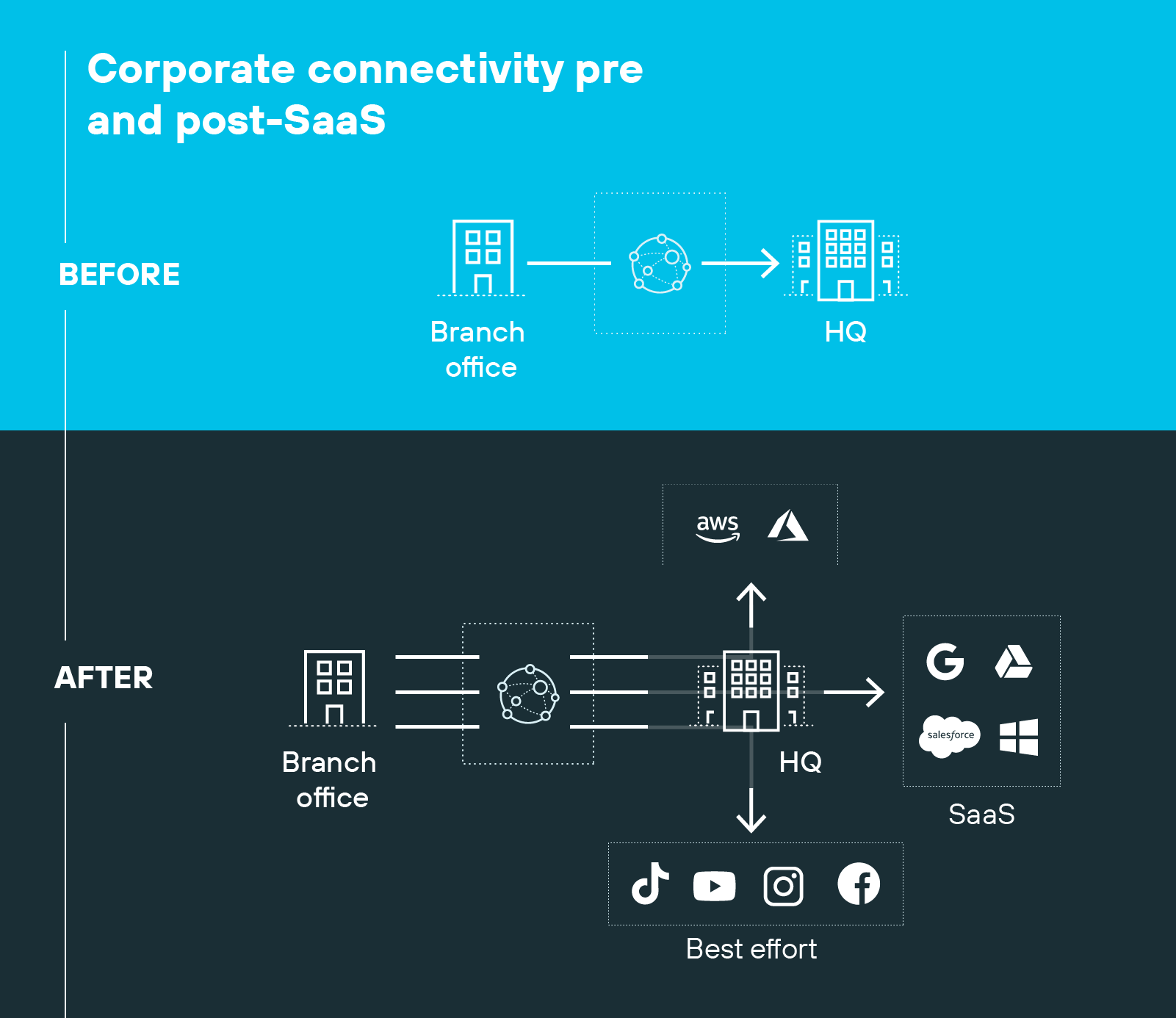
The way businesses operate—and where their applications live—has changed. Most organizations no longer rely solely on centralized data centers to host their systems. Instead, applications are now distributed across public cloud platforms, SaaS environments, and hybrid infrastructures.
That shift has made it harder for traditional WAN architectures to keep up.
Here’s why.
Legacy WANs were designed around predictable traffic patterns. They assumed most application traffic would flow between branch offices and a main data center. So they centralized connectivity and security.
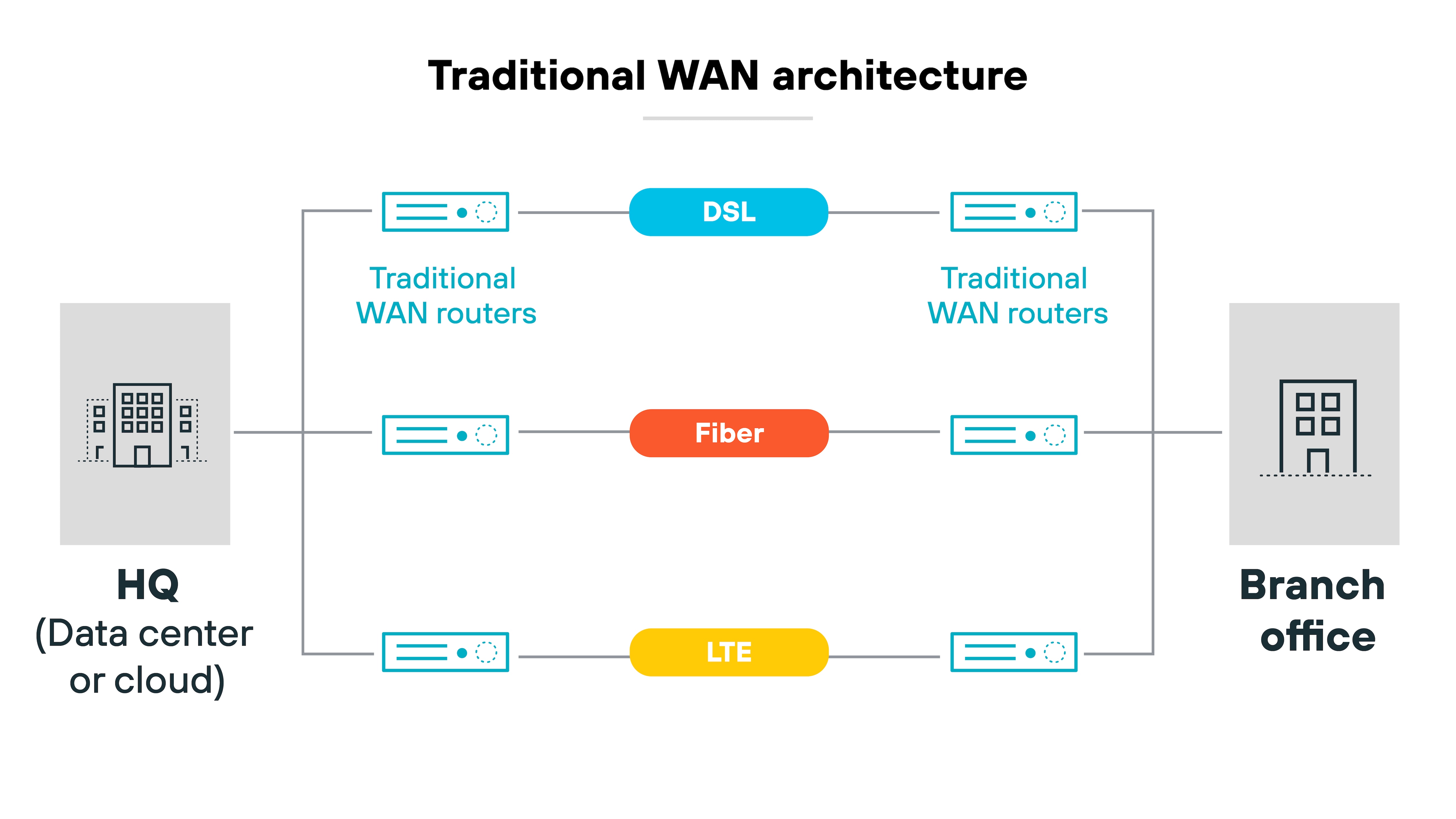
That worked when applications and data mostly lived in one place. But it creates challenges when applications are hosted in multiple clouds and users work from anywhere.
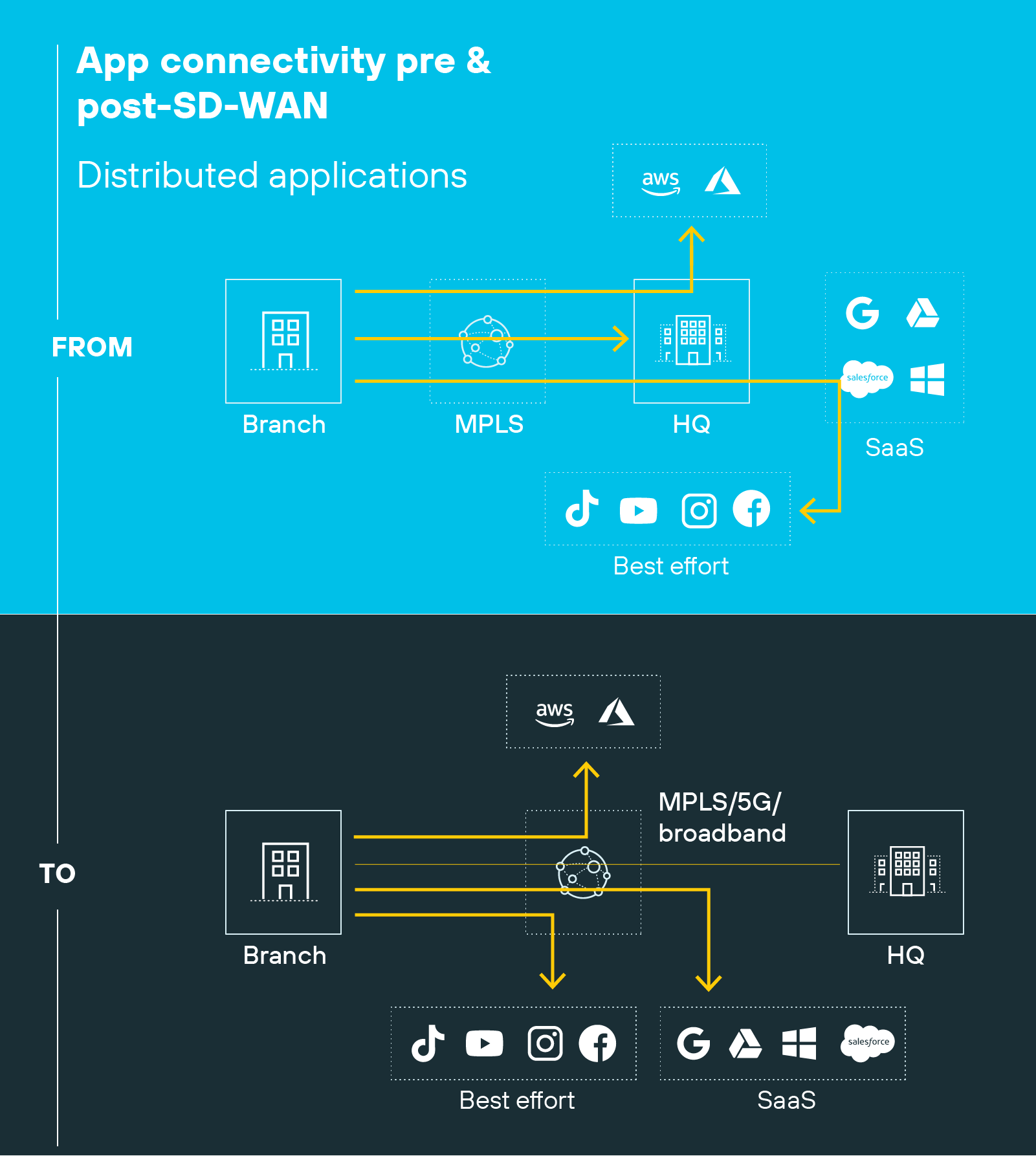
At the same time, internet usage has surged. Branches and remote locations now rely heavily on cloud-based apps and services. This results in more direct-to-internet traffic, which doesn’t align well with older WAN models that route everything through a central hub. The result is often unnecessary delays, congestion, and cost.
Another factor is workforce distribution. Hybrid work has become standard in many industries. Employees connect from offices, homes, shared spaces—even while traveling. These patterns demand more flexible connectivity across varied locations, networks, and devices. Traditional WANs aren’t built for that level of dynamism.
The increase in applications and endpoints has also made networks more complex. IT teams are expected to maintain visibility and control across a broader attack surface. That becomes harder when network traffic is scattered and legacy infrastructure lacks centralized insight.
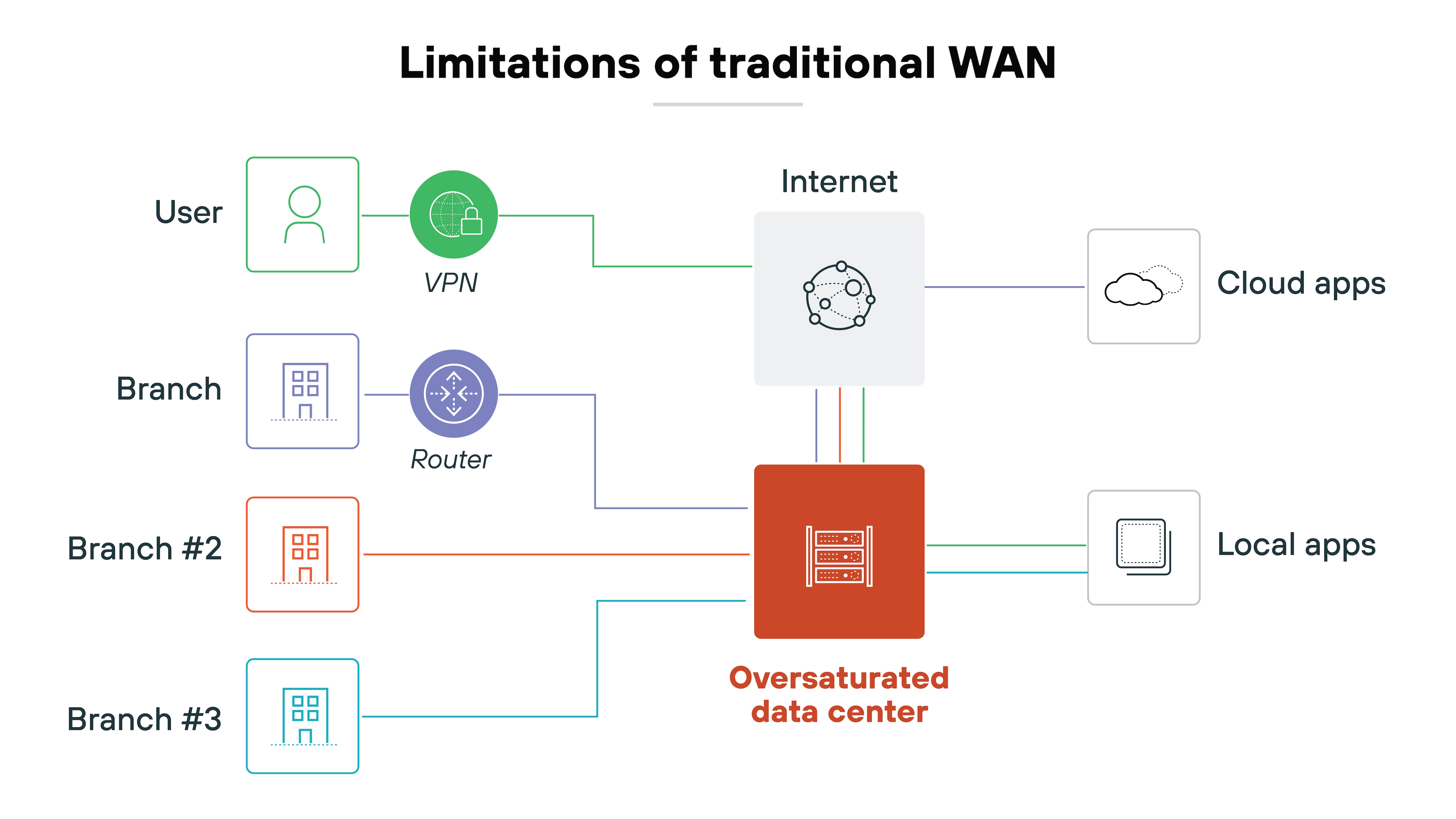
In short:
The combination of decentralized applications, distributed users, and growing network complexity has created a gap that traditional WANs can’t easily fill. That gap is what led to the need for SD-WAN.
Businesses needed a new way to support modern workflows, without relying on outdated assumptions about how and where people connect.
How does SD-WAN work?
SD-WAN is a virtualized networking approach that extends enterprise connectivity across multiple sites.
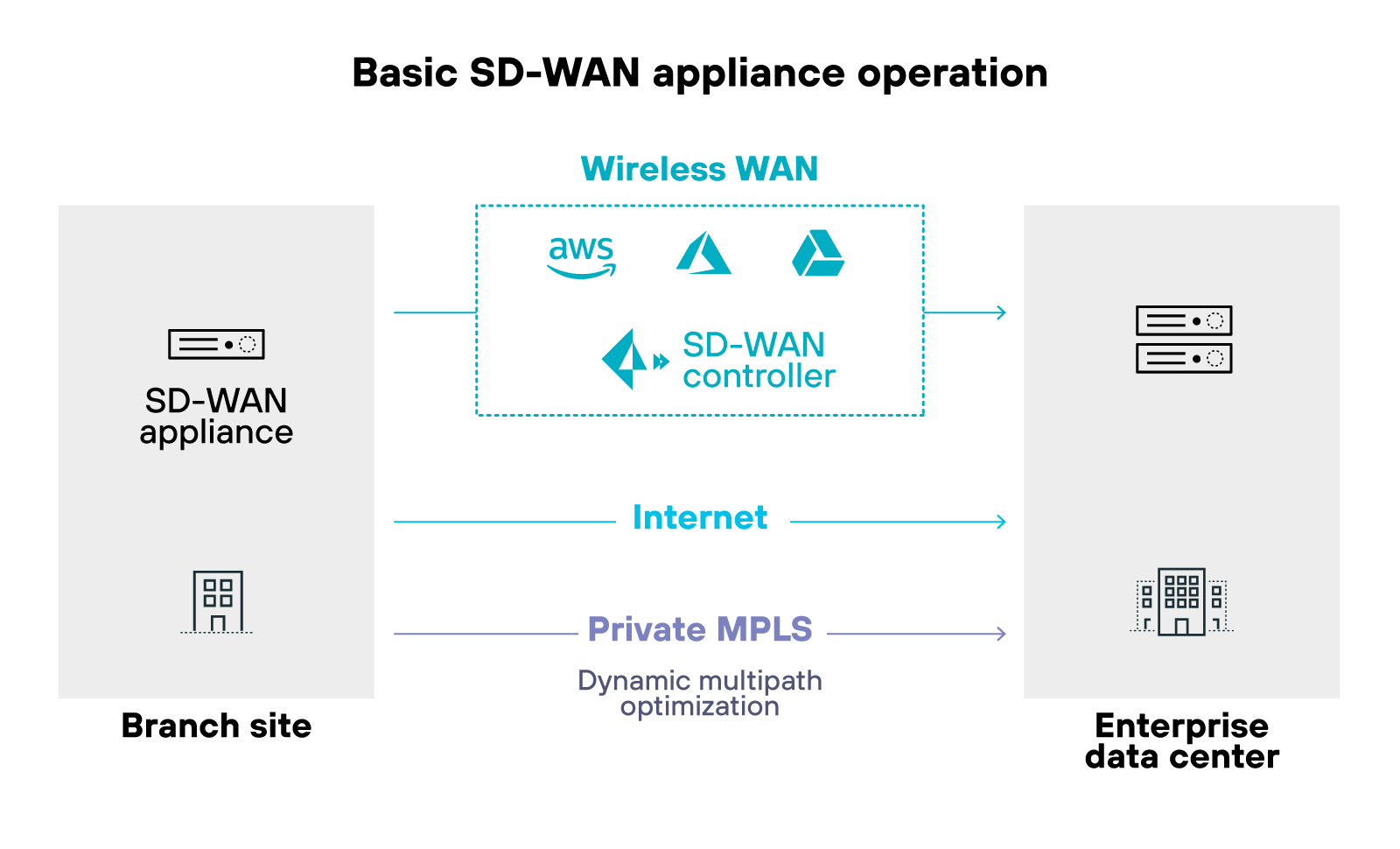
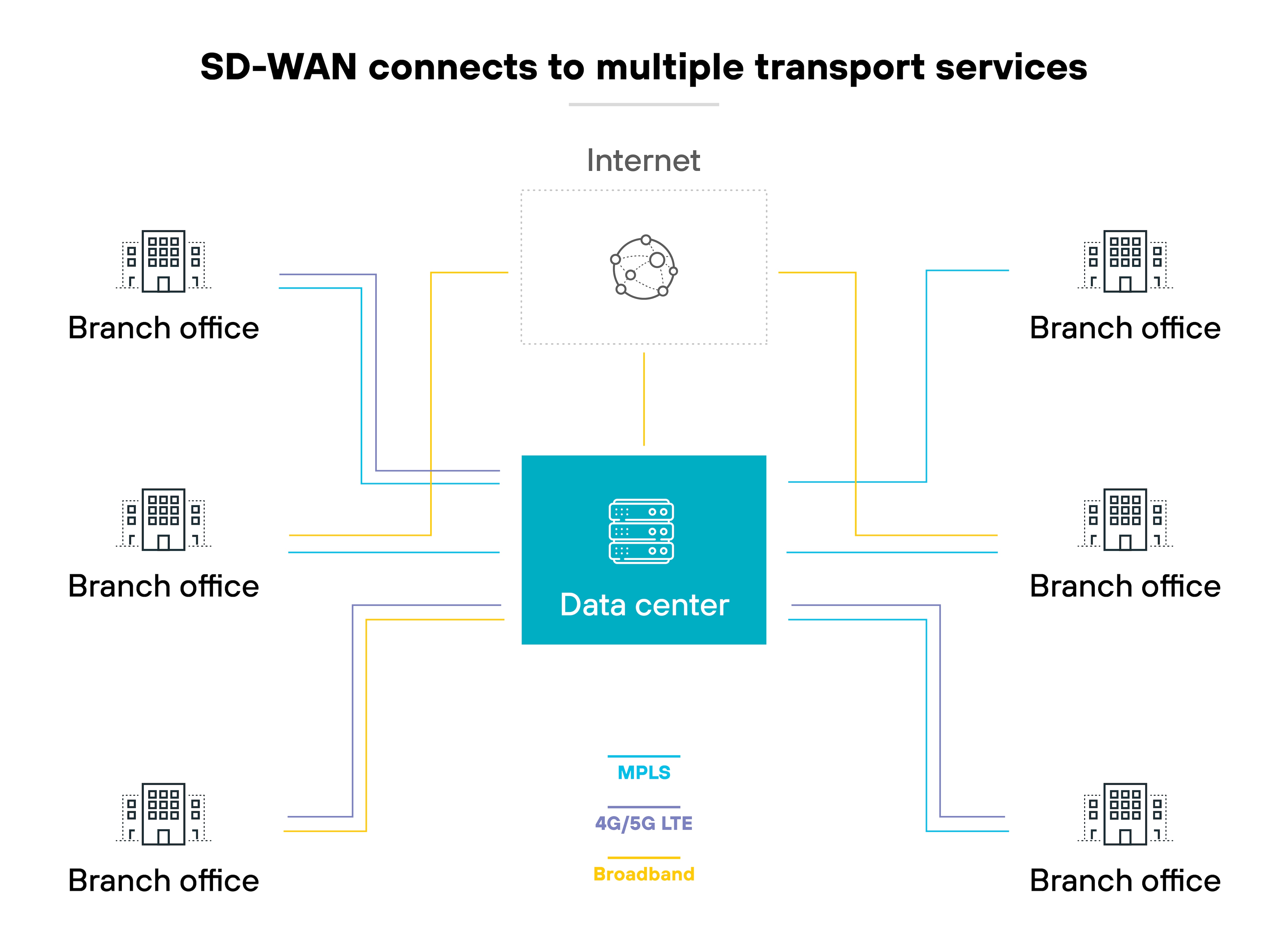
It works by using different types of connections. For example: MPLS, broadband, wireless links, VPNs, and public internet. This allows users at branch locations and remote sites to reach enterprise applications and systems. Which supports work from anywhere without needing a centralized access point.
Here’s how it manages traffic:
SD-WAN constantly checks the performance of each WAN link. It monitors for things like latency, jitter, and packet loss. Then it uses that information to decide how traffic should flow—based on current network conditions.
Like this:
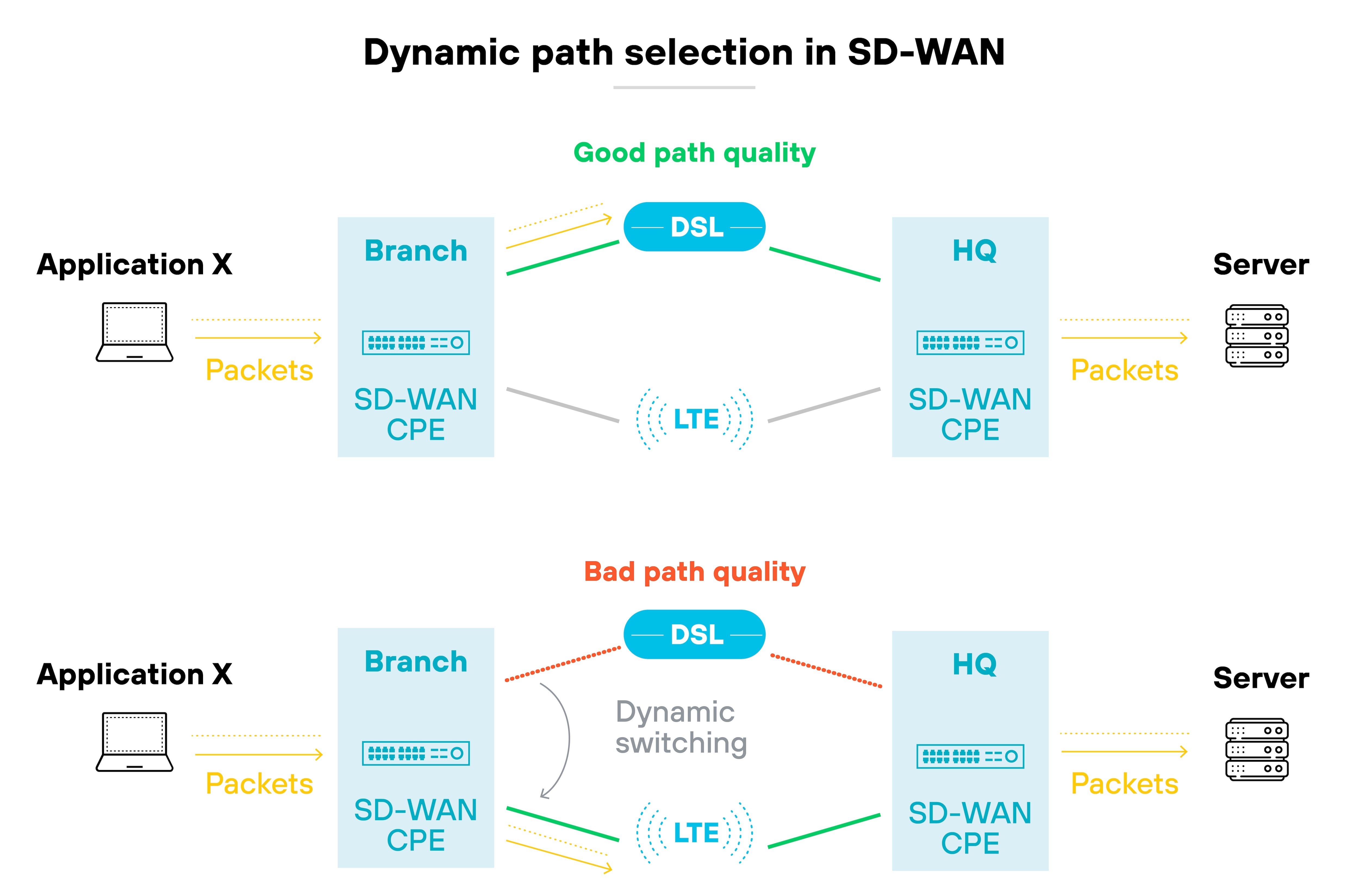
SD-WAN manages routing through software instead of relying on static device configurations.
It evaluates traffic conditions in real time. Then it makes decisions based on predefined rules and current network performance.
Policies are created centrally. Administrators use a controller to define how traffic should be handled across different paths.
Those policies are then pushed out to all sites. Which allows updates and changes to be applied consistently throughout the network. And that means no manual configuration needed at each location.
The result is dynamic, policy-based routing that adapts to changing conditions while staying aligned with business priorities.
Here’s how it works:
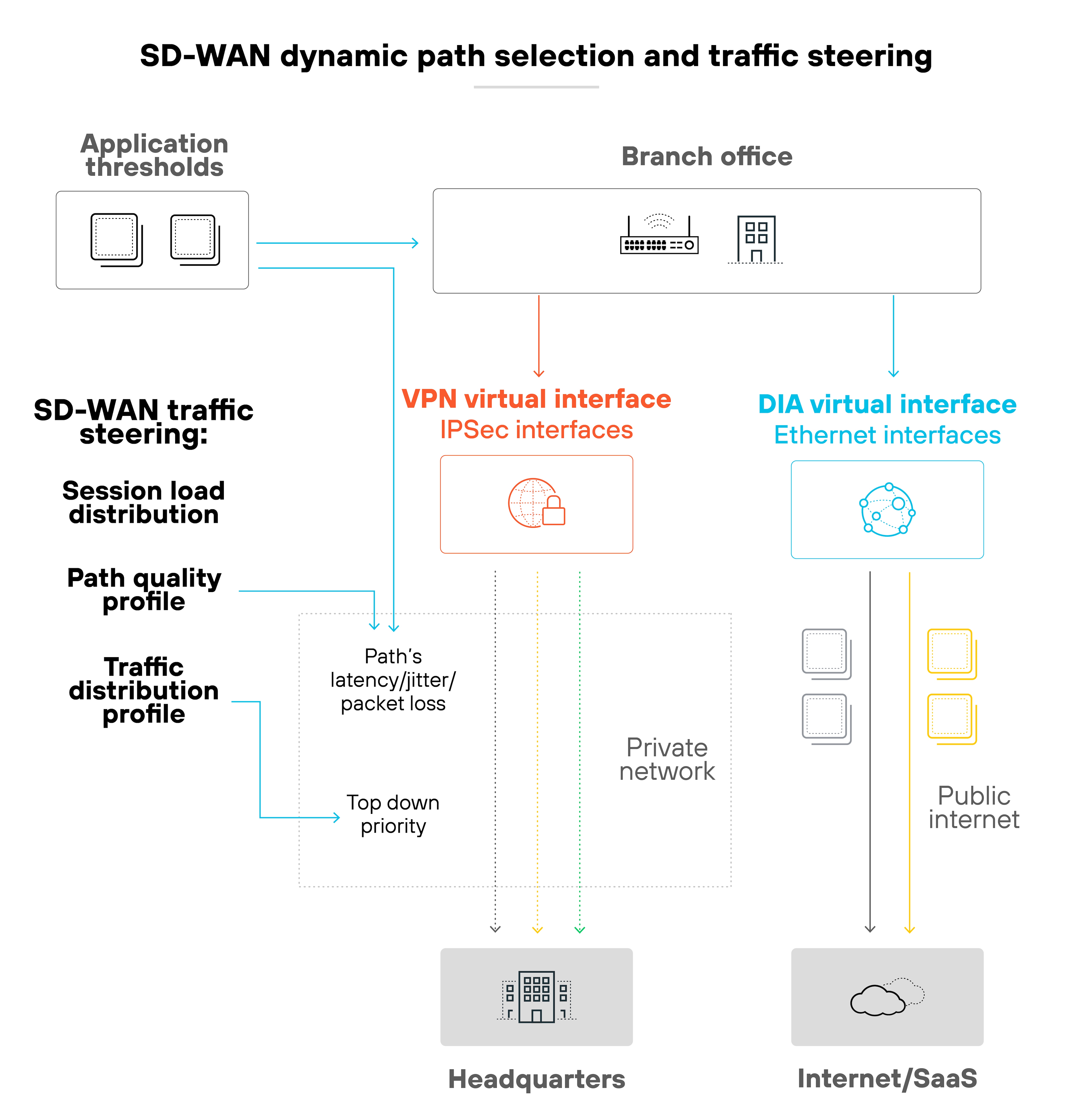
A single update can be pushed to all connected sites without manually touching every device. That saves time and reduces the chance of misconfiguration.
The architecture is based on a centralized control plane. The control plane manages how data is forwarded through the network. Local SD-WAN appliances follow instructions from this central controller. So instead of routing decisions being made locally, they follow global policies.
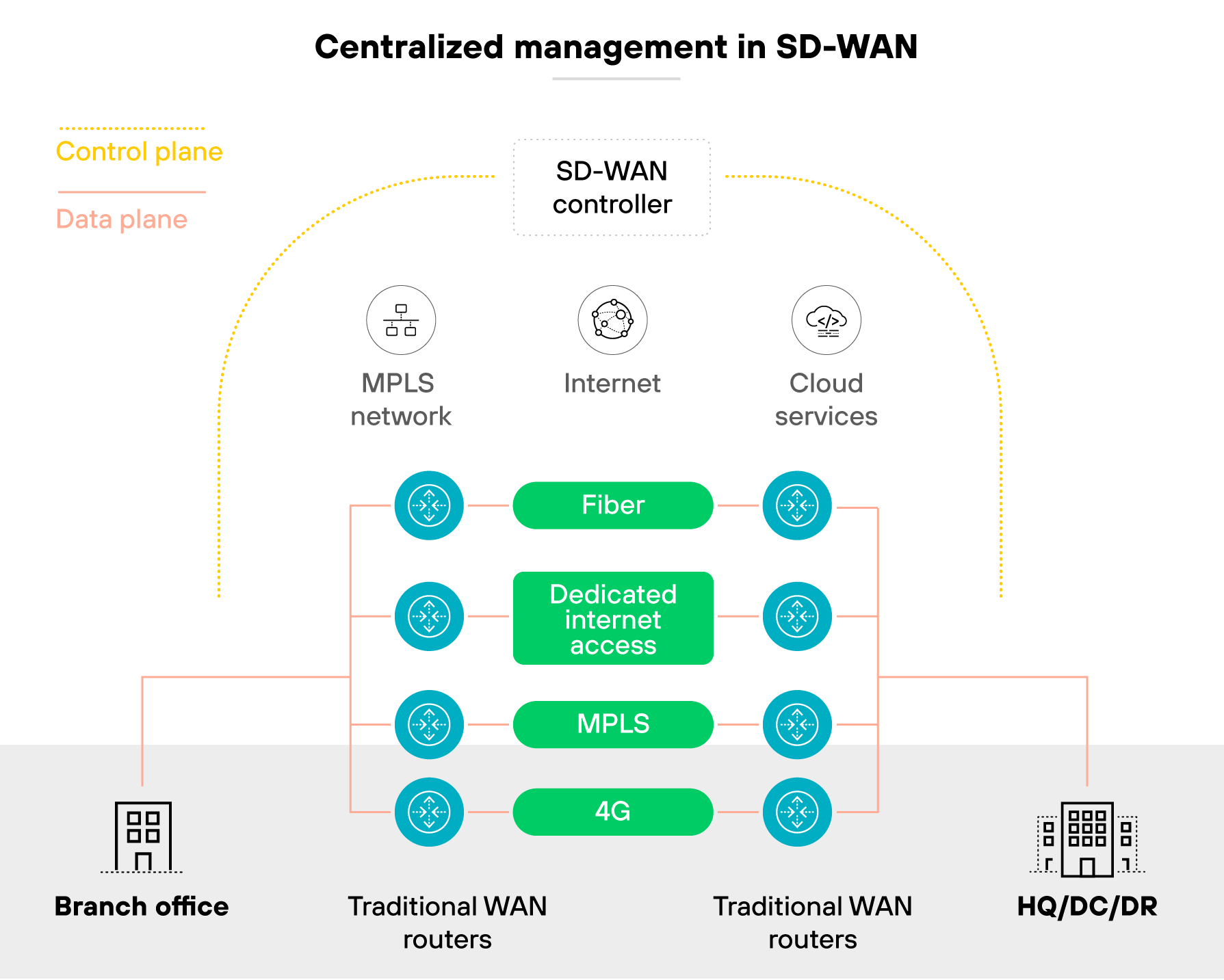
Decoupling of the control and data planes is what makes SD-WAN easier to manage. It also supports more consistent performance, especially as networks grow or change.
SD-WAN also helps address common WAN challenges. It can detect problems like congestion or degraded links. Then it automatically reroutes traffic to maintain service levels.
In other words:
It turns the WAN into a more adaptive, responsive part of the network. Without relying solely on physical infrastructure or static routing rules.
What is SD-WAN architecture?
The architecture of a software-defined wide area network is the conceptual structure and logical organization of SD-WAN.
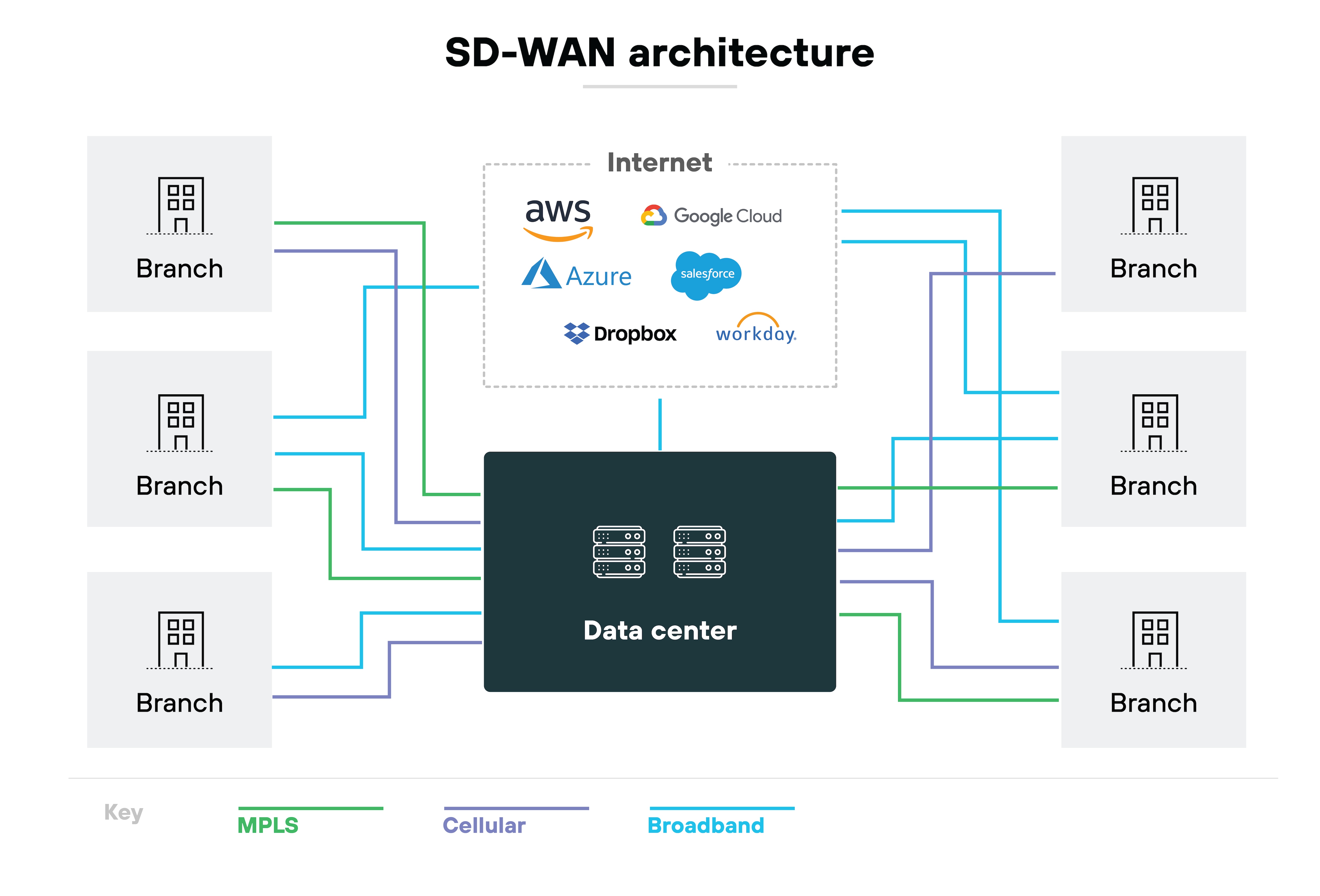
It defines how the system is built, how the different components interact, and how traffic is routed and managed across the network. Understanding the architecture helps clarify what SD-WAN does—and how it works behind the scenes.
Also, architecture isn’t just about the physical setup. It’s about how the SD-WAN solution is designed to support centralized control, dynamic traffic steering, and flexible deployment.
Let’s break it down:
This section explains both the key components that make up SD-WAN and the different architectural models used to deploy it.
Components of SD-WAN architecture
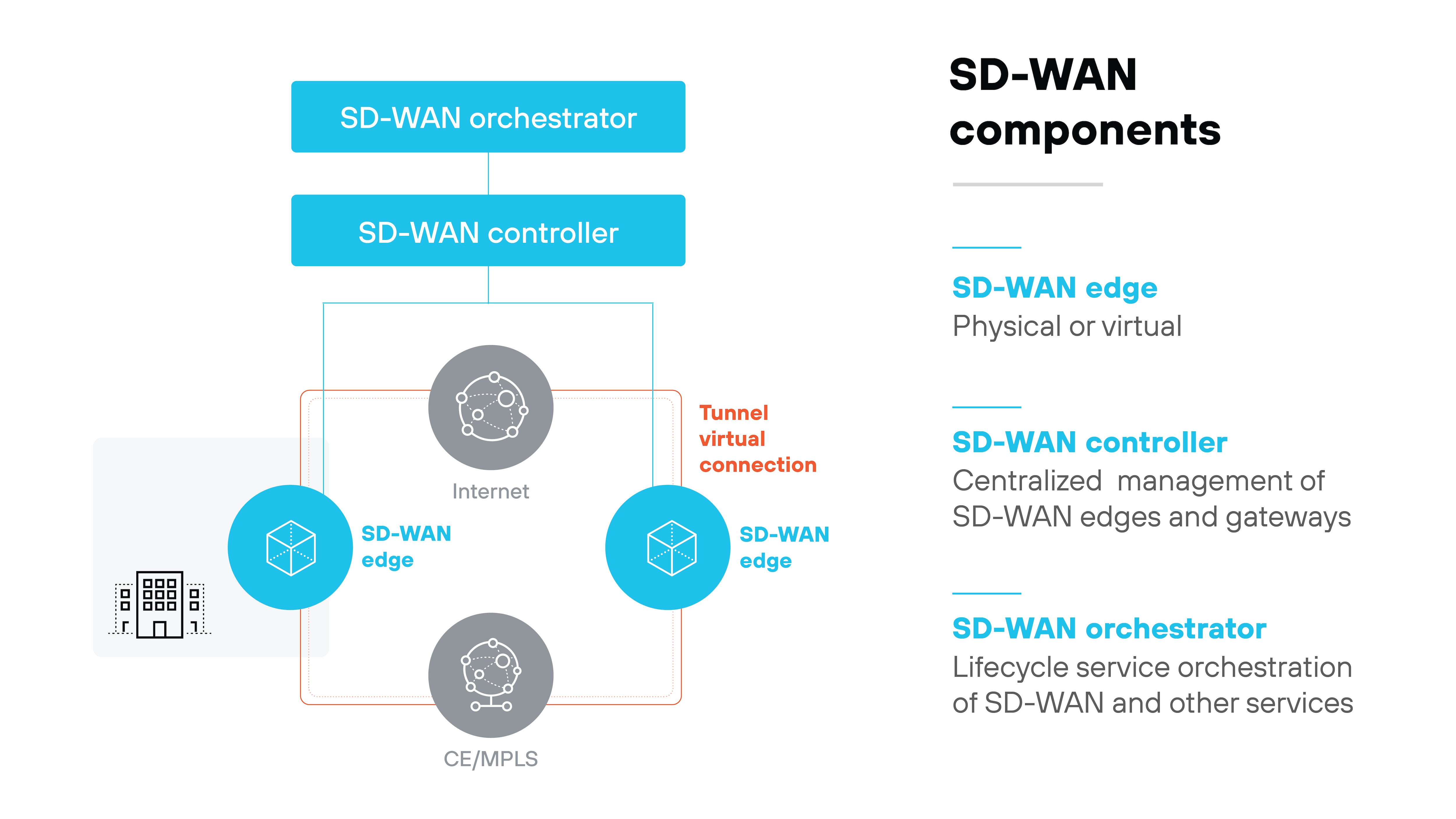
SD-WAN is made up of several core components that work together to provide centralized control, efficient traffic routing, and flexible deployment across locations.
SD-WAN edge
The edge is where the SD-WAN connects to the physical network. It typically sits at branch offices, remote sites, or cloud environments. This is the point where data enters and exits the SD-WAN fabric. It handles traffic forwarding and enforces policies locally, based on instructions received from the controller.
SD-WAN orchestrator
The orchestrator provides centralized coordination for the SD-WAN environment. It applies configuration templates, manages updates, and ensures policies are pushed out across all sites. This component simplifies operations by reducing manual effort and allowing administrators to manage the network through a single interface.
SD-WAN controller
The controller is responsible for centralized policy and control decisions. It maintains visibility across the network and communicates with edge devices to distribute instructions. Operators use the controller to define how traffic should be treated, and which paths should be used based on application requirements or network conditions.
Virtual or physical nodes
Some SD-WAN architectures include additional nodes deployed at specific points in the network. These can be either virtual or physical. They help extend coverage, add capacity, or introduce specialized capabilities. In some environments, these nodes support scalability by helping route traffic more efficiently between key locations.
Types of SD-WAN architecture
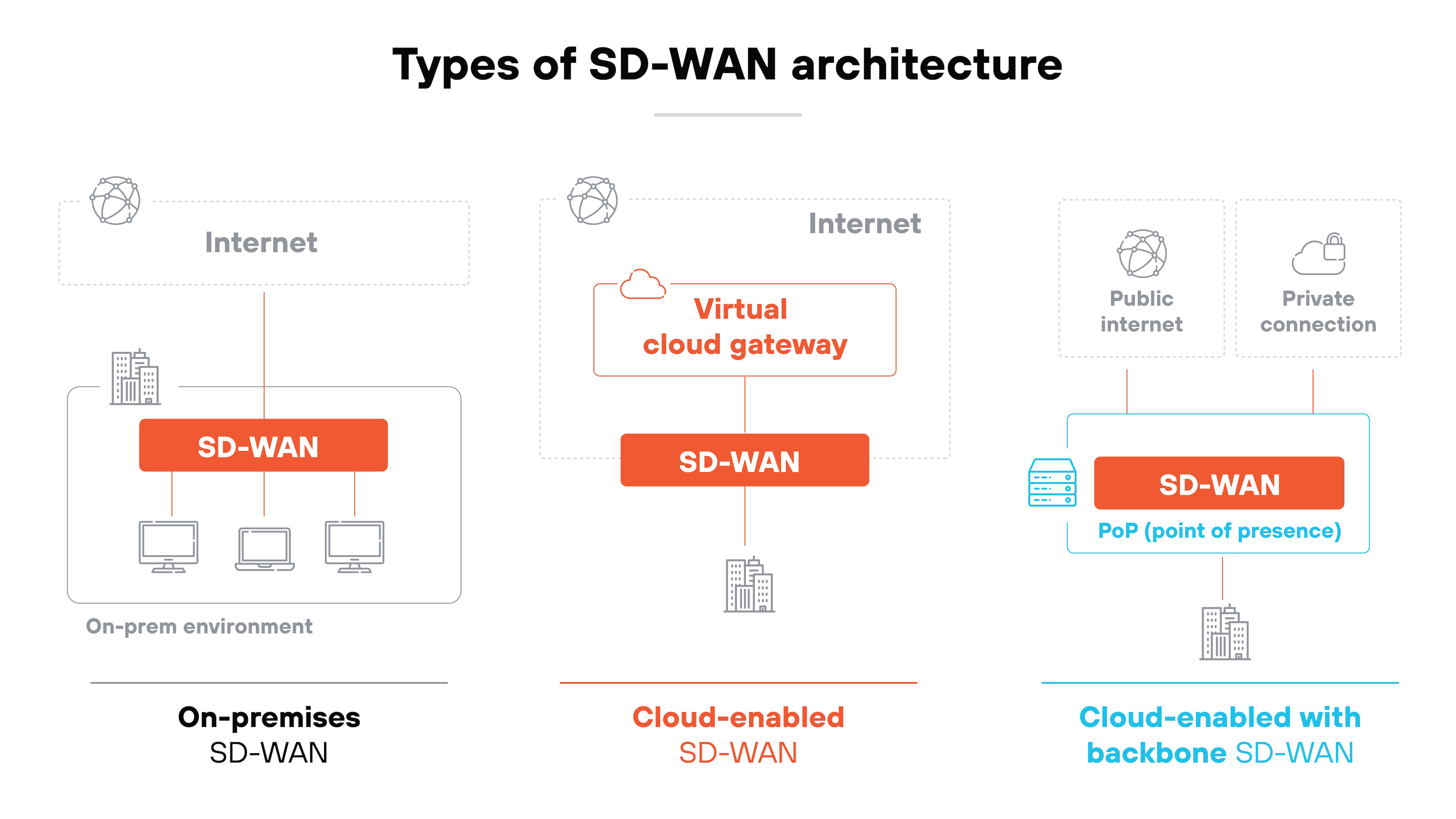
SD-WAN can be deployed in different ways depending on how the network is built and what requirements it needs to meet.
Each type offers a different approach to routing, control, and cloud integration.
On-premises SD-WAN
This deployment places the SD-WAN appliance directly at each site. It operates locally and gives network teams direct control over the device. The configuration and policy enforcement happen within the site itself. This setup can support more control over traffic handling and may be preferred when data sensitivity is a primary concern.
Cloud-enabled SD-WAN
In this architecture, the SD-WAN connects through a virtual gateway hosted in the cloud. The connection happens over the public internet. This allows branch locations to reach cloud services more efficiently. It can also help improve how traffic is routed to applications that are hosted in distributed environments.
Cloud-enabled SD-WAN with backbone
This model adds a regional point of presence—or PoP—between the branch and destination. Traffic is first sent to the nearest PoP, where it can then be routed over a private backbone instead of relying entirely on the public internet. This setup can help reduce latency, improve reliability, and support failover if a direct connection is degraded or unavailable.
- What Is SD-WAN Architecture?
- What Is an SD-WAN Gateway? | Definition, Explanation, Use Cases
- What Is Next-Generation SD-WAN?
- What Is the Cloud-Delivered Branch?
What are the benefits of SD-WAN?
Operational simplicity: SD-WAN centralizes network management through a single controller. This enables zero-touch provisioning, automated configuration, and policy enforcement across all sites. By reducing manual work, it shortens deployment times and lowers the risk of misconfigurations. The result is a more efficient way to maintain and scale distributed networks.
Transport flexibility and cost efficiency: Again, SD-WAN supports a mix of public and private connections, including broadband, 5G, and satellite. This allows organizations to select the most cost-effective provider at each site without sacrificing performance. SD-WAN also helps reduce vendor lock-in by supporting a range of transport providers, which can simplify procurement and improve pricing leverage across locations. These capabilities often lead to reduced operating costs and better return on investment.
Improved security: As discussed, SD-WAN provides encrypted connectivity between sites and enables centralized policy enforcement across the network. It can also integrate with advanced security services such as secure web gateways and cloud access security brokers. This flexibility helps extend consistent security policies to remote locations and cloud environments. With growing use of IoT and distributed users, SD-WAN helps maintain visibility and control across the expanding attack surface.
Enhanced application performance: As explained earlier, SD-WAN uses real-time traffic monitoring and application-aware routing to maintain consistent performance for critical applications. Since it adjusts paths dynamically, applications that require low latency—such as voice or video—can be prioritized to ensure reliable delivery. This reduces disruptions and supports a better experience for users.
Cloud optimized routing: Like we outlined above, traditional WAN architectures often backhaul traffic through a central data center, increasing latency for cloud-based applications. SD-WAN enables direct access to cloud services from branch locations. It selects the best available path in real time, based on current network conditions. This helps improve performance for SaaS and cloud-hosted workloads.
Supports SASE adoption: SD-WAN provides the connectivity layer for secure access service edge (SASE) architectures. As organizations move toward cloud-based security models, SD-WAN helps ensure reliable, policy-driven traffic handling. Its centralized control and cloud integration capabilities align with SASE principles. This makes SD-WAN a foundational part of long-term network and security convergence.
- What Are the Benefits of SD-WAN?
- What Is Application Acceleration?
- What Is WAN Optimization (WAN Acceleration)?
- What Is SD-WAN Multicloud?
- How SD-WAN Helps Today’s IoT
What are the challenges associated with SD-WAN?
Finding the right vendor: With many SD-WAN providers on the market, it can be tough to evaluate offerings that look similar on the surface. Organizations need to align vendor capabilities with specific network goals, infrastructure requirements, and long-term support expectations.
Determining underlay provisioning needs: The underlay directly impacts SD-WAN performance and reliability. Choosing between public internet, MPLS, or hybrid approaches requires a careful evaluation of application demands, geographic needs, and provider service levels.
Navigating cloud connectivity options: SD-WAN solutions offer varying levels of integration with public cloud providers. Selecting the right model—native, vendor-provided, or self-managed—requires balancing performance, cost, and operational complexity.
Quantifying cost reduction accurately: While SD-WAN can reduce network costs, measuring ROI isn't always straightforward. Organizations must consider not just circuit savings but also factors like downtime reduction, feature consolidation, and operational efficiency.
Troubleshooting issues: SD-WAN environments can be difficult to troubleshoot due to dynamic routing, policy complexity, and vendor-specific implementations. Without sufficient visibility and monitoring tools, pinpointing the root cause of an issue is often challenging.
Addressing security and visibility limitations: Decentralized traffic and internet breakouts at branch sites can increase the attack surface. Maintaining end-to-end visibility and consistent security enforcement requires proper planning and integration with other tools or frameworks like SASE.
Choosing the right management model: SD-WAN deployments can be fully managed, co-managed, or DIY. Each model offers different levels of control, complexity, and support—so organizations need to assess internal capabilities before deciding.
What are the different types of SD-WAN deployment models?
Different SD-WAN deployment models offer varying levels of control, flexibility, and operational responsibility.
Choosing the right one depends on your organization’s internal capabilities, resources, and business goals.
DIY SD-WAN
DIY, or do-it-yourself, SD-WAN puts full control of the SD-WAN infrastructure in the hands of your internal IT team. You handle everything from design and implementation to monitoring and ongoing management.
This approach typically involves deploying SD-WAN appliances at each site and configuring them to support the desired traffic flow, security policies, and performance needs. The team manages policies, optimizes performance, and integrates the SD-WAN with any existing technologies.
DIY SD-WAN offers maximum flexibility. But it also requires deep expertise and significant internal resources. It’s generally best suited for larger organizations with strong network teams and complex customization needs.
Fully managed SD-WAN
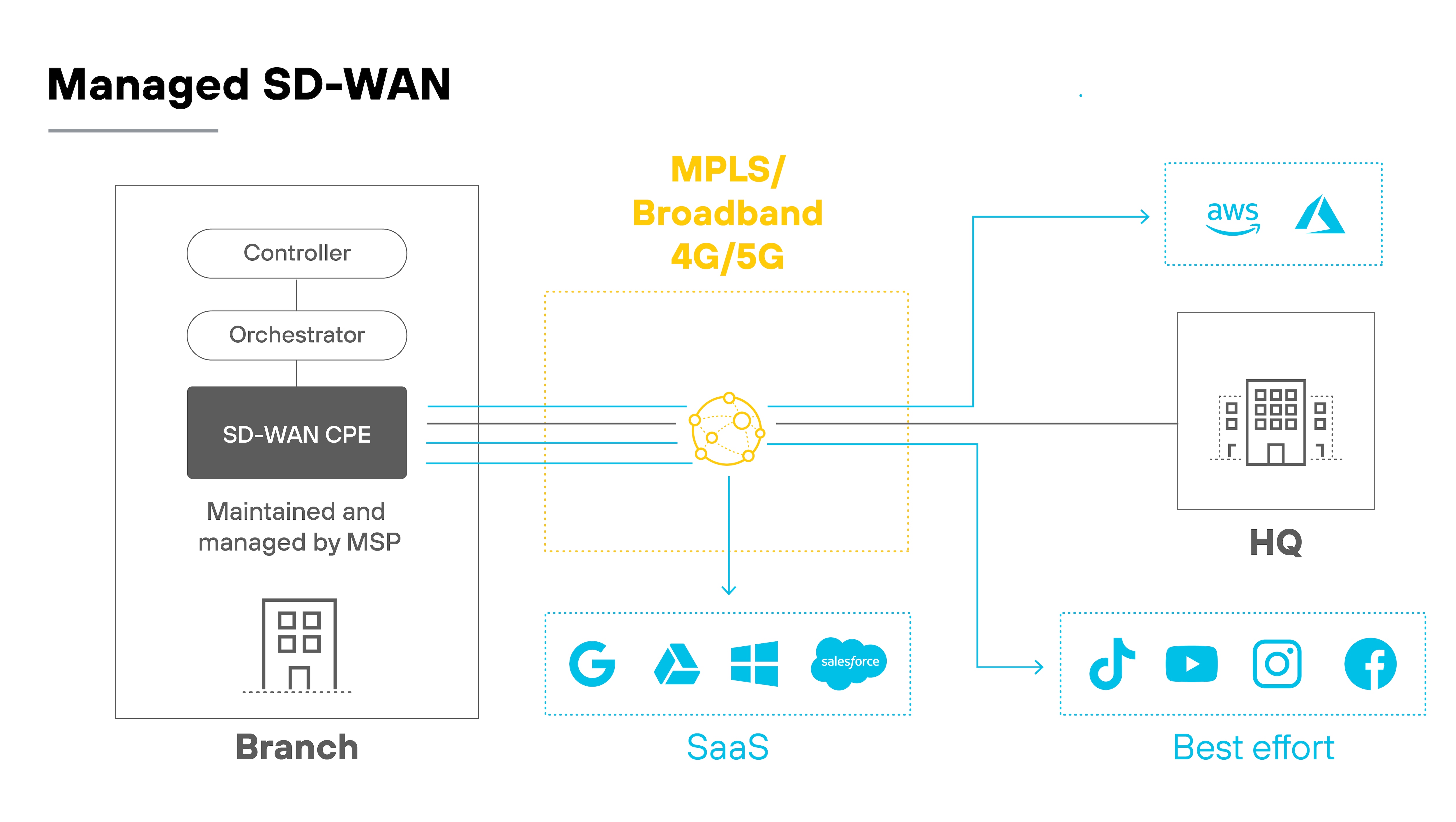
Fully managed SD-WAN outsources all aspects of network management to a service provider. The provider takes care of initial deployment, configuration, monitoring, troubleshooting, and optimization.
In this model, your organization relies on the provider to maintain uptime, enforce policies, and keep the SD-WAN functioning smoothly. It usually includes performance SLAs, centralized visibility, and expert support.
Fully managed SD-WAN is a good fit for organizations with limited IT resources or those looking to simplify operations. It offloads the day-to-day responsibility and provides access to expert help.
Co-managed SD-WAN
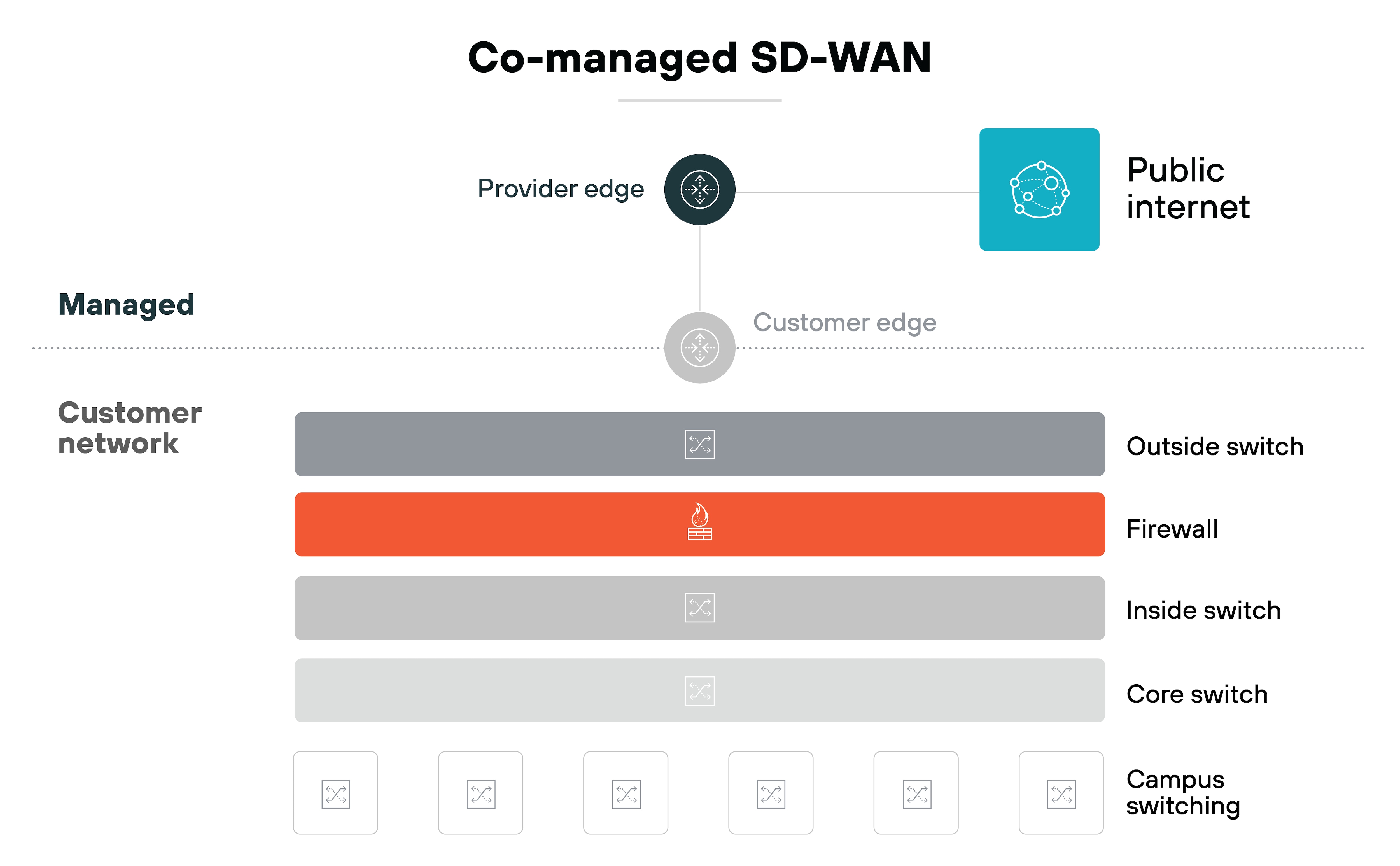
Co-managed SD-WAN is a shared responsibility model. Your internal team handles some aspects of the network, while a provider manages others.
For example: The provider may oversee initial deployment, major updates, and proactive monitoring. Your team may retain control of policy updates or site-specific changes. This gives you access to expert support without giving up visibility or oversight.
Co-managed SD-WAN is ideal for organizations that want a balance between control and external assistance. It works well when internal resources are available, but not sufficient to manage everything alone.
Managed CPE SD-WAN
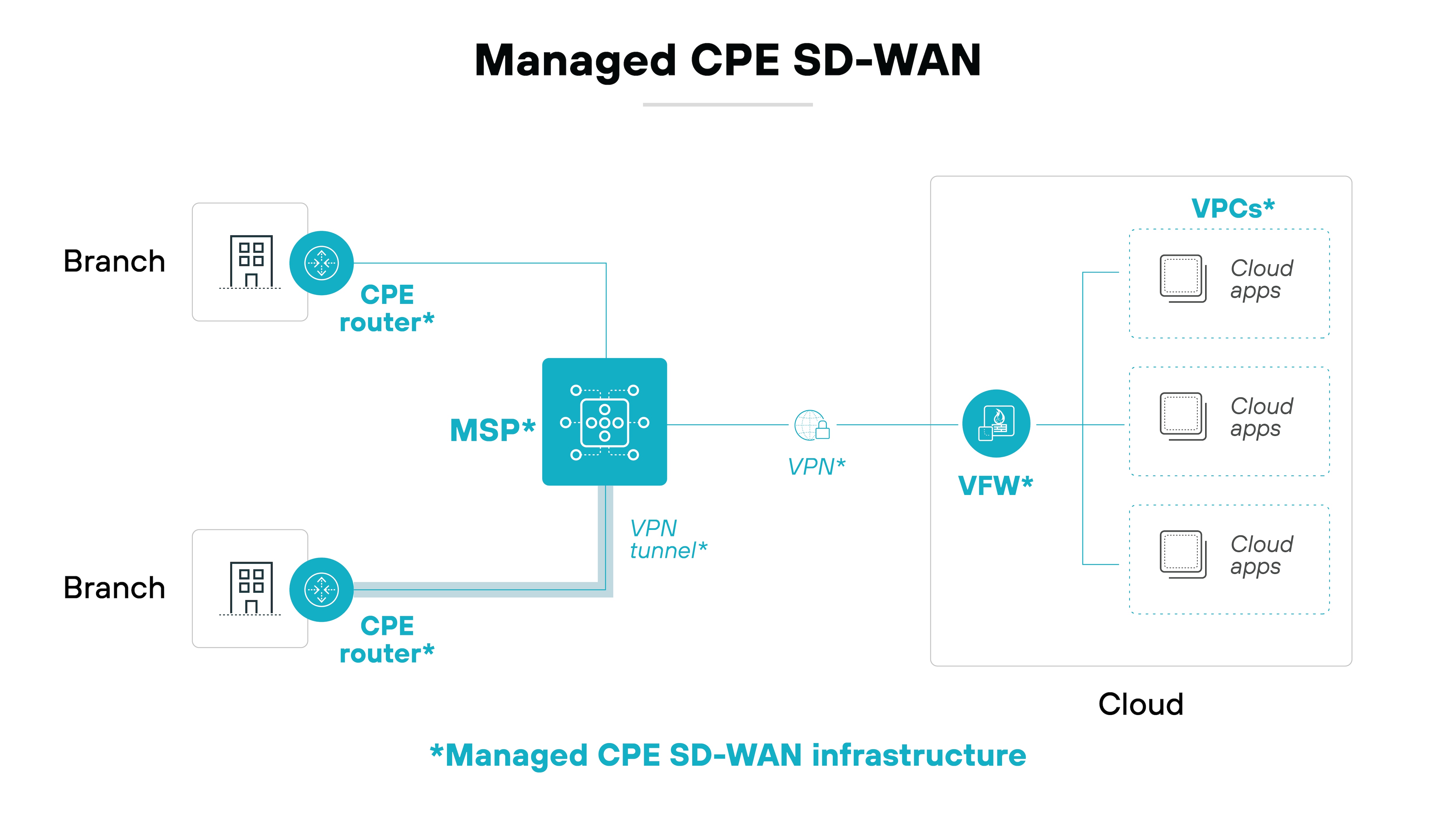
Managed CPE SD-WAN focuses on the physical devices deployed at your locations. In this model, a provider manages the customer premises equipment (CPE), including configuration, updates, and troubleshooting.
Your internal team might still define policies or handle other parts of the network, but the provider takes responsibility for keeping the edge hardware running smoothly.
This model is a good option when you need physical SD-WAN appliances for compliance or performance but want to offload the hardware lifecycle management.
SD-WAN as a service (SD-WANaaS)
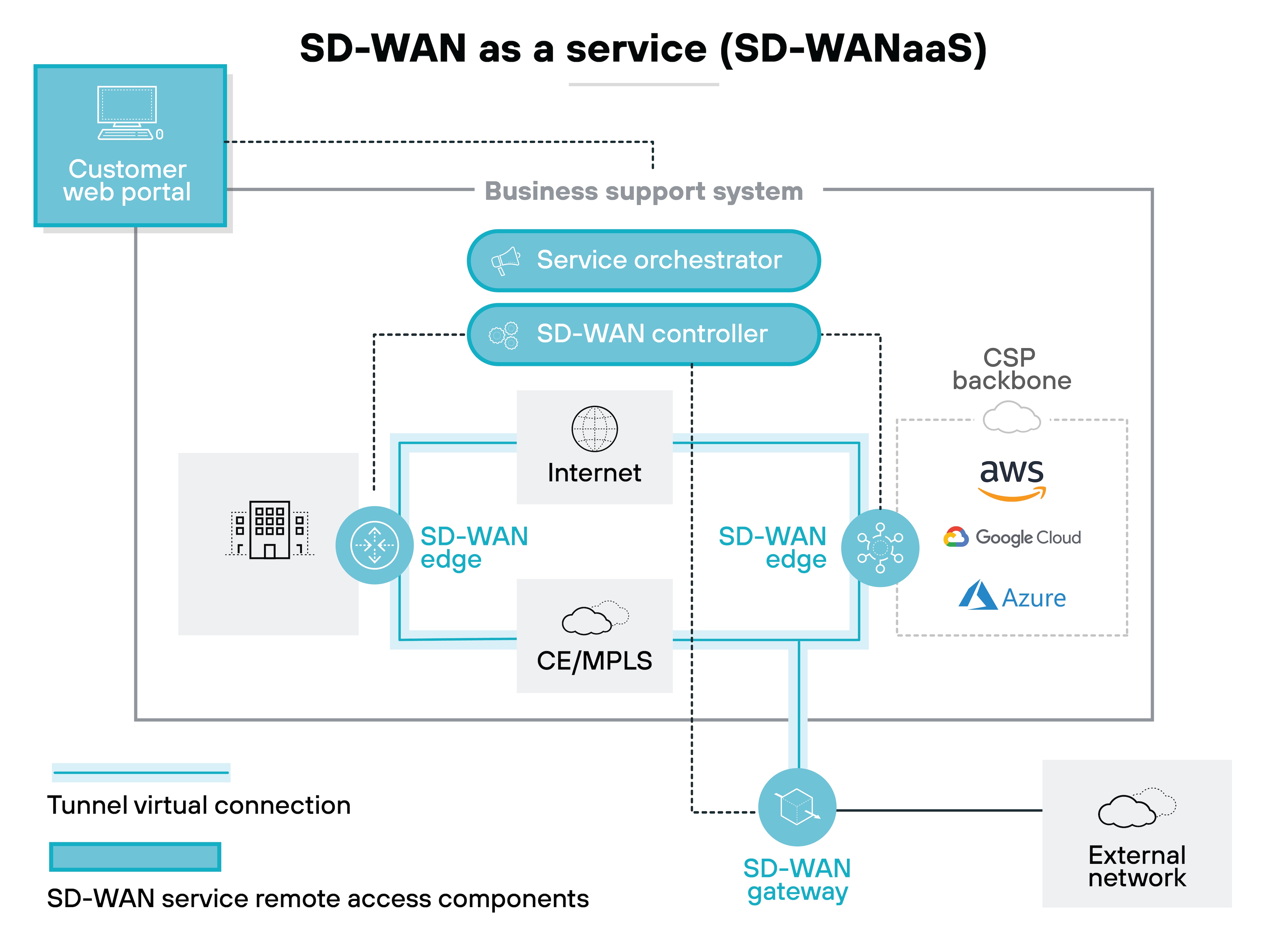
SD-WANaaS delivers SD-WAN capabilities as a cloud-based service. The provider hosts the infrastructure and manages core operations. Your team accesses and controls the network through a centralized, cloud-delivered interface.
The provider handles performance optimization, routing, and security services. No on-premises controller is needed, and updates happen in the cloud.
SD-WANaaS is useful for organizations with limited IT resources, multi-site environments, or cloud-first strategies. It offers scalability and simplicity with minimal hardware requirements.
How secure is SD-WAN?
Traditional SD-WAN isn’t inherently secure. It improves performance and routing efficiency–and does include some basic security features–but doesn’t offer the advanced protections needed to guard against today’s cyber threats.
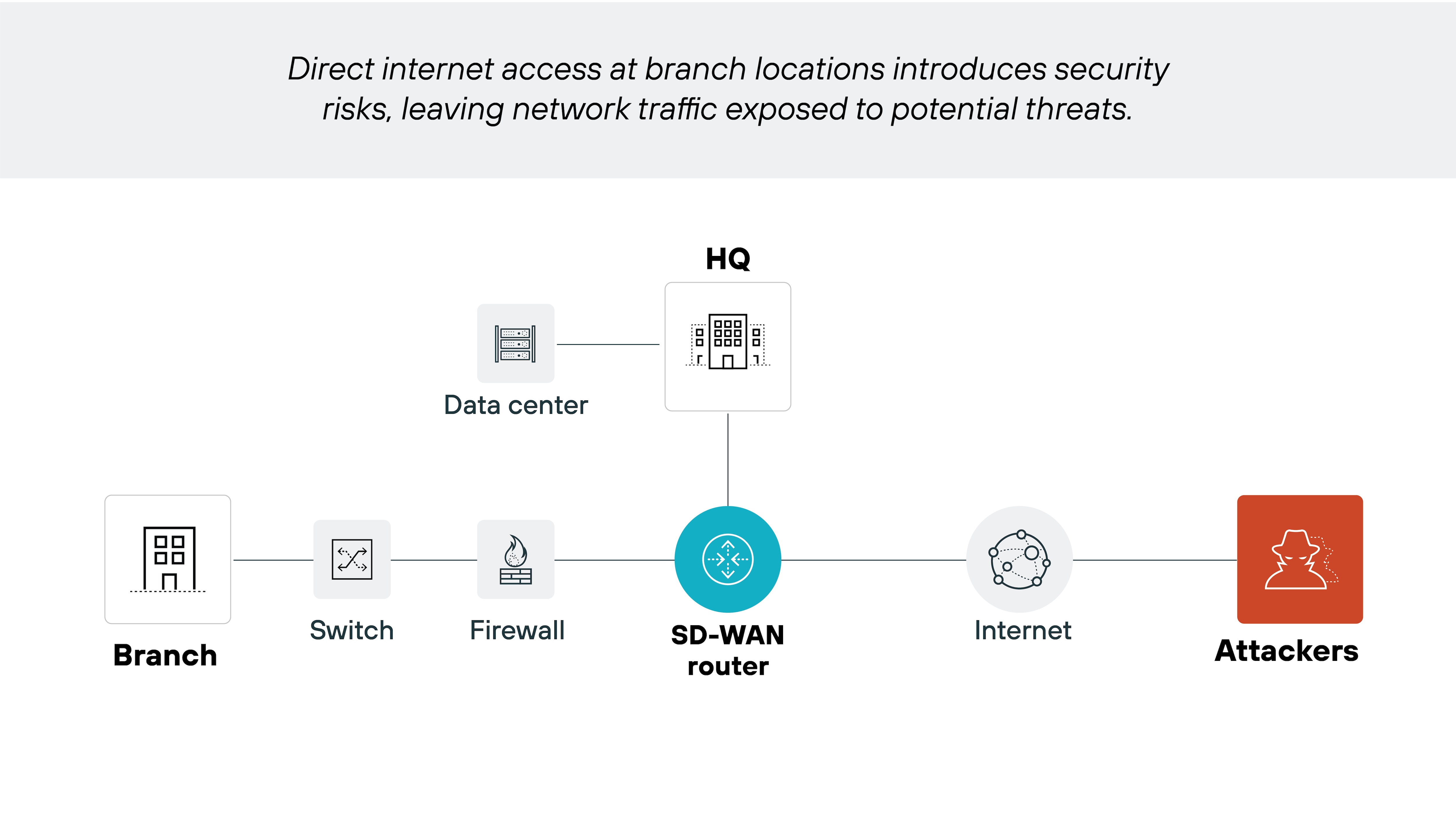
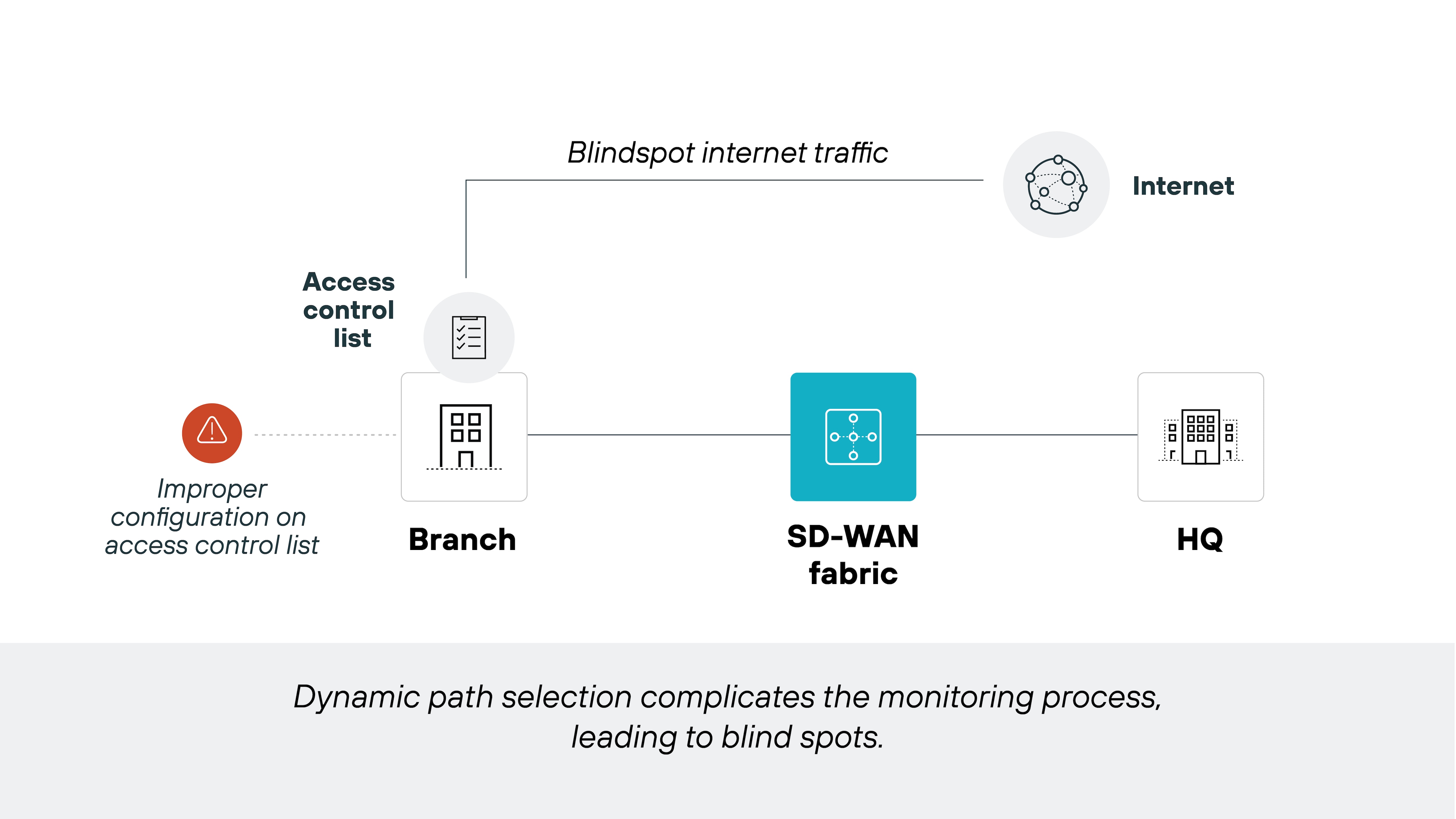
With that said, the security level of an SD-WAN solution depends on how it’s designed and deployed. That’s why many organizations either layer in security tools separately or adopt secure SD-WAN solutions that integrate them by default.
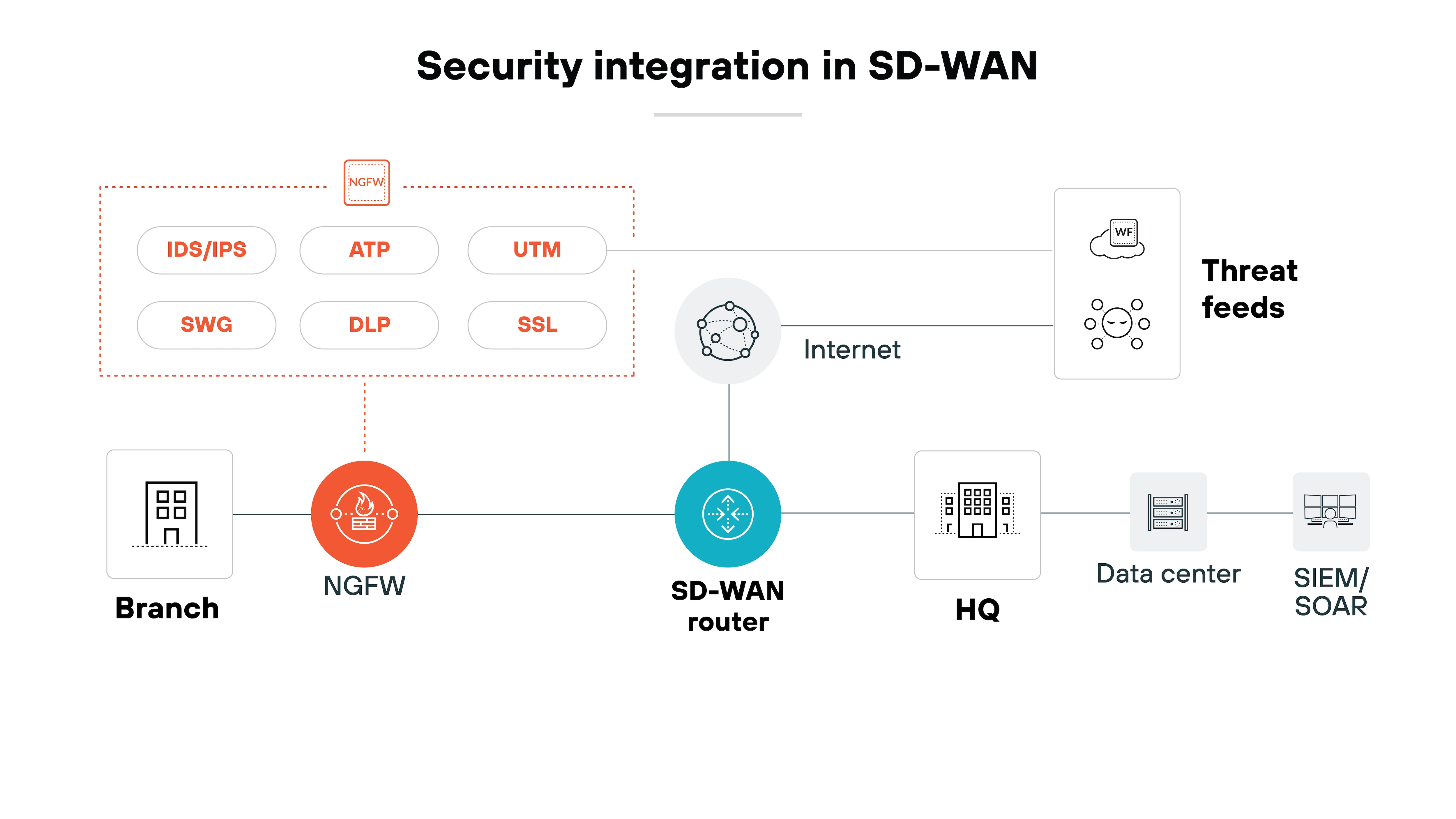
Secure SD-WAN includes features like next-generation firewalls, intrusion prevention, and SSL inspection—built directly into the SD-WAN infrastructure. It also enables centralized policy management, which reduces the risk of configuration errors across distributed locations.
Ultimately, with the right security measures in place, SD-WAN can support strong, consistent protection across the WAN. It just doesn’t qualify as a security solution on its own.
What Is SD-Branch | Centralized Security for Branch Office Networks
Branch Network Security | Securing Branch Networks with SD-WAN
How to choose the best SD-WAN vendor for your business (and what to look for)
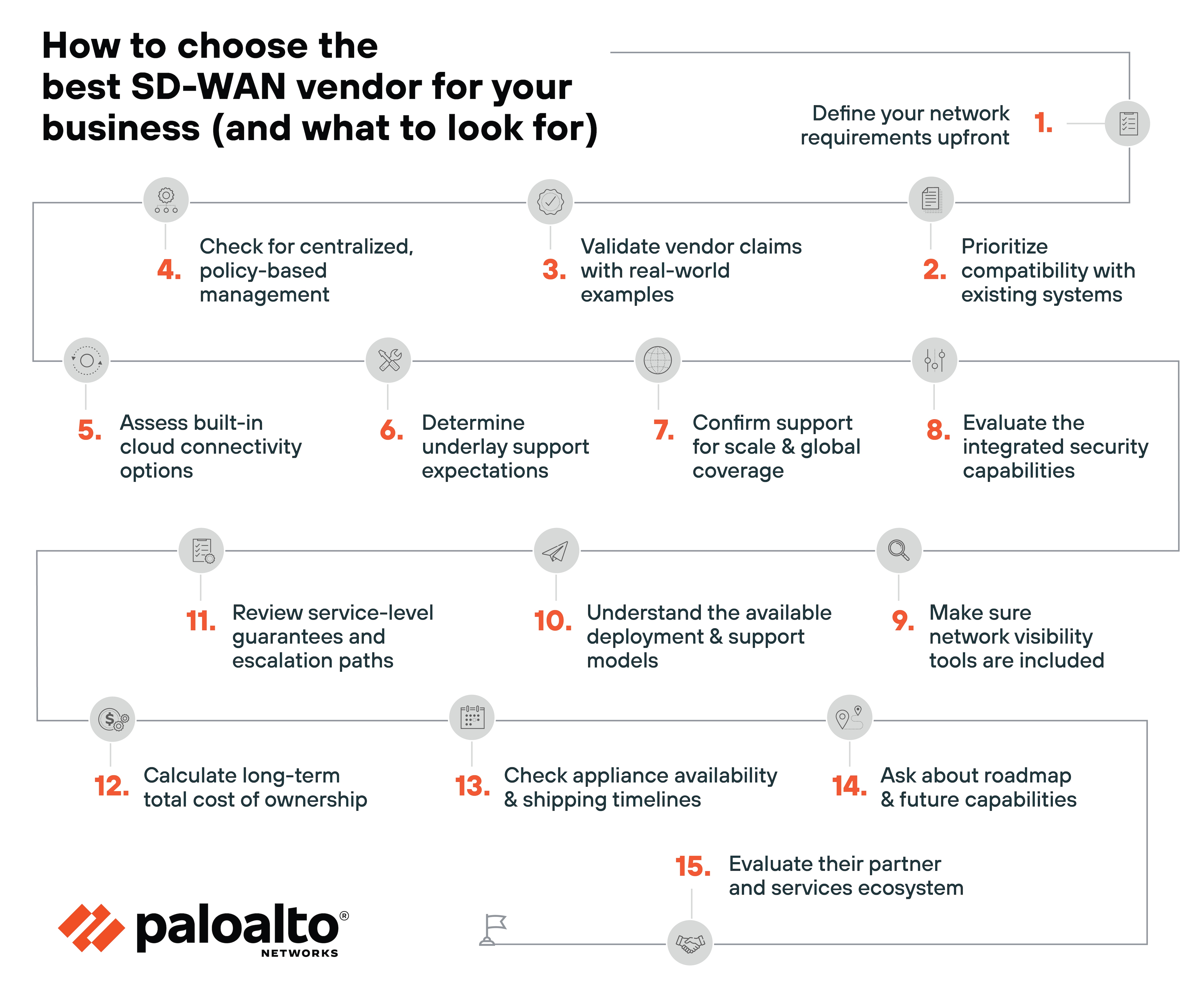
Choosing the right SD-WAN vendor involves more than just comparing features. It requires evaluating how well a vendor aligns with your network goals, architecture, and support needs.
Here are the top recommendations to guide your evaluation:
- Define your network requirements upfront: Identify your existing challenges, architecture, and business goals. This sets the baseline for evaluating whether a vendor can meet your needs.Tip:Include non-technical stakeholders early. Business unit input can surface priorities IT might otherwise miss.
- Prioritize compatibility with existing systems: Ensure the vendor supports your current security stack, cloud platforms, and underlay providers to avoid unnecessary replacement or complexity.Tip:Some vendors advertise “universal compatibility,” but that often comes with limitations. Dig into version-level and feature-specific support to confirm.
- Validate vendor claims with real-world examples: Review case studies or independent evaluations—ideally from organizations with similar environments—to assess how the solution performs in practice.Tip:Request a customer reference call. Direct conversations can reveal insights not covered in formal case studies.
- Check for centralized, policy-based management: A good SD-WAN platform should allow you to manage configurations and performance from one interface across all locations.
- Assess built-in cloud connectivity options: Look for native integration with major cloud providers or direct cloud gateways to support high-performance access.
- Determine underlay support expectations: Some vendors manage the underlay network. Others expect you to. Be clear on who handles what.
- Confirm support for scale and global coverage: Vendors should offer global reach, middle-mile optimization, and scalable design options if your network is distributed or growing.Tip:Some vendors rely on third-party PoPs for global reach. Check how much of the infrastructure they actually operate—and where.
- Evaluate the integrated security capabilities: Look for features like traffic segmentation, encrypted internet breakout, and support for your existing security controls.
- Make sure network visibility tools are included: Choose a vendor that offers clear telemetry and diagnostics for application performance and troubleshooting.Tip:Test the troubleshooting flow in a live demo or POC. Seeing how quickly you can isolate a real issue can reveal a lot about the product's usability.
- Understand the available deployment and support models: Whether DIY, managed, or co-managed, the vendor should offer a model that fits your team's capabilities and staffing.
- Review service-level guarantees and escalation paths: Look for SLAs that address uptime, latency, and response time, backed by a clear support structure.Tip:Ask to see a sample escalation workflow. It helps to know what to expect before an incident occurs.
- Calculate long-term total cost of ownership: Consider hardware, licensing, support, and connectivity costs—not just the platform itself.
- Check appliance availability and shipping timelines: Especially for larger rollouts, make sure the vendor can deliver hardware without supply chain delays.
- Ask about roadmap and future capabilities: Ensure the vendor is actively evolving their product, especially around automation, application awareness, and hybrid work support.Tip:Find out what percentage of the roadmap is driven by customer feedback. Vendors that truly listen often iterate faster and more usefully.
- Evaluate their partner and services ecosystem: A strong vendor ecosystem can simplify deployment, integration, and ongoing operations.
Top 10 SD-WAN best practices, tips, and tricks
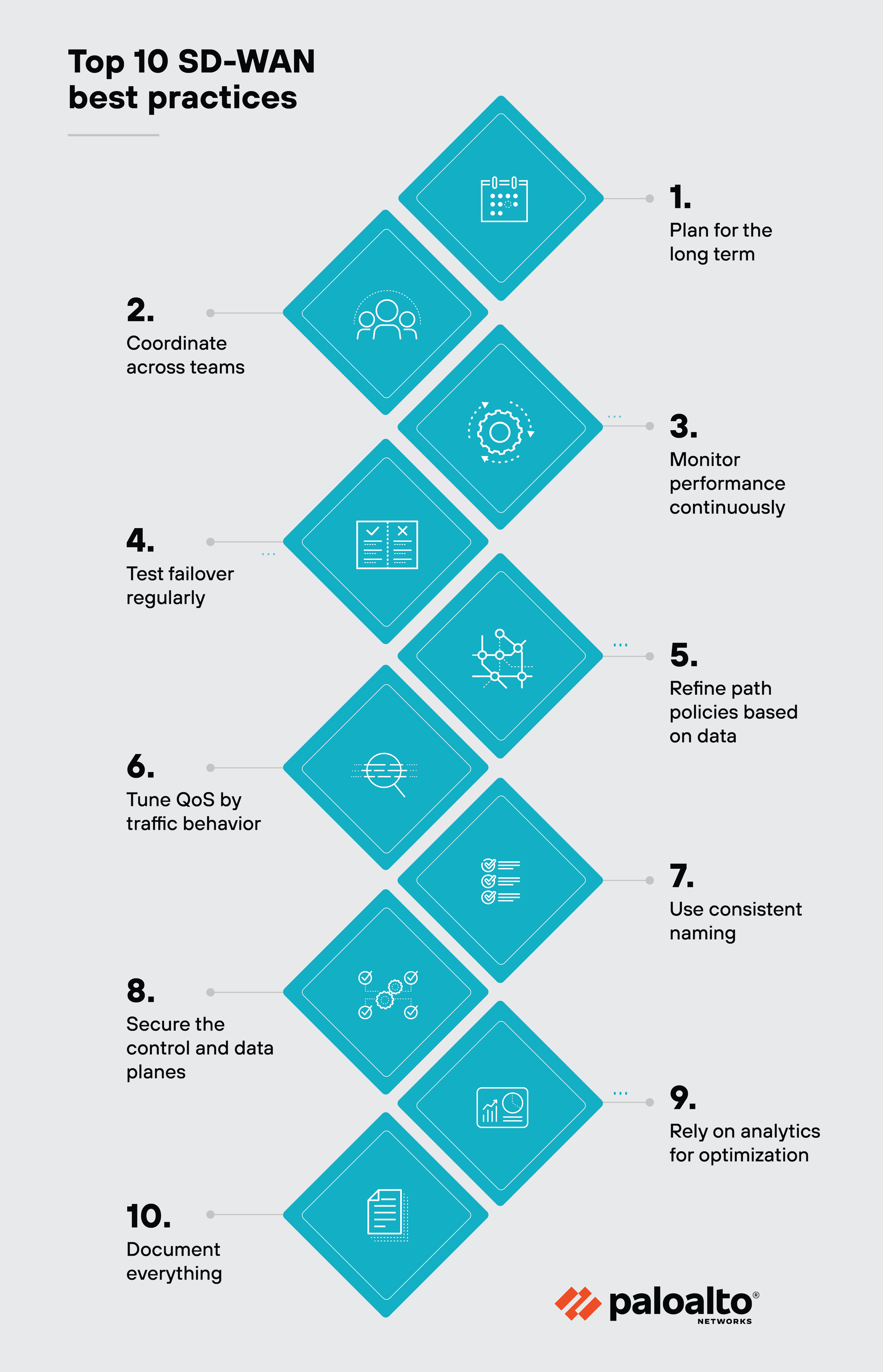
Once SD-WAN is up and running, keeping it optimized takes ongoing work.
Here are ten key best practices to help you get the most out of your SD-WAN deployment:
- Plan for the long term: Design your SD-WAN to support future growth. Anticipate changing traffic patterns and evolving business needs so your architecture stays relevant.
- Coordinate across teams: Make sure networking, security, and application teams stay aligned. This ensures policies don't conflict and changes don't break something unexpected.Tip:Create a change control process that includes stakeholders from each team. This reduces the risk of policy conflicts.
- Monitor performance continuously: Watch metrics like latency, jitter, and packet loss in real time. Visibility into both the overlay and underlay helps pinpoint problems faster.Tip:Use synthetic probes or telemetry from multiple perspectives (user, app, path) to get a fuller picture of performance.
- Test failover regularly: Failover only helps if it actually works. Simulate outages and link failures to confirm automatic rerouting performs correctly.Tip:Include cloud-hosted apps in your failover tests—not just connectivity to other sites.
- Refine path policies based on data: Don't set and forget your routing logic. Review policies periodically to reflect how applications behave and where performance matters.Tip:Use flow analysis to identify applications that are misclassified or not being routed optimally.
- Tune QoS by traffic behavior: Use real usage patterns—not just static app types—to decide which traffic gets priority. Accurate QoS improves application performance.Tip:Validate your QoS effectiveness by monitoring real-time queuing and drop rates under load.
- Use consistent naming: Label circuits, tunnels, and sites clearly and uniformly. This avoids confusion during troubleshooting and policy updates.
- Secure the control and data planes: Lock down access, rotate credentials, and enforce segmentation. Proper zoning and rule enforcement keep your network harder to attack.Tip:Rotate credentials and API tokens on a defined schedule. Automate this if possible.
- Use analytics for optimization: Look at trends in historical traffic and performance data. Use those insights to adjust routing, allocate bandwidth, and plan upgrades.
- Document everything: Keep detailed, up-to-date records of your configuration and changes. It helps with audits, onboarding, and troubleshooting later on.
What is the role of SD-WAN in SASE?
SD-WAN is a core component of secure access service edge (SASE). It provides the networking layer that connects users, devices, and locations across multiple WAN links.
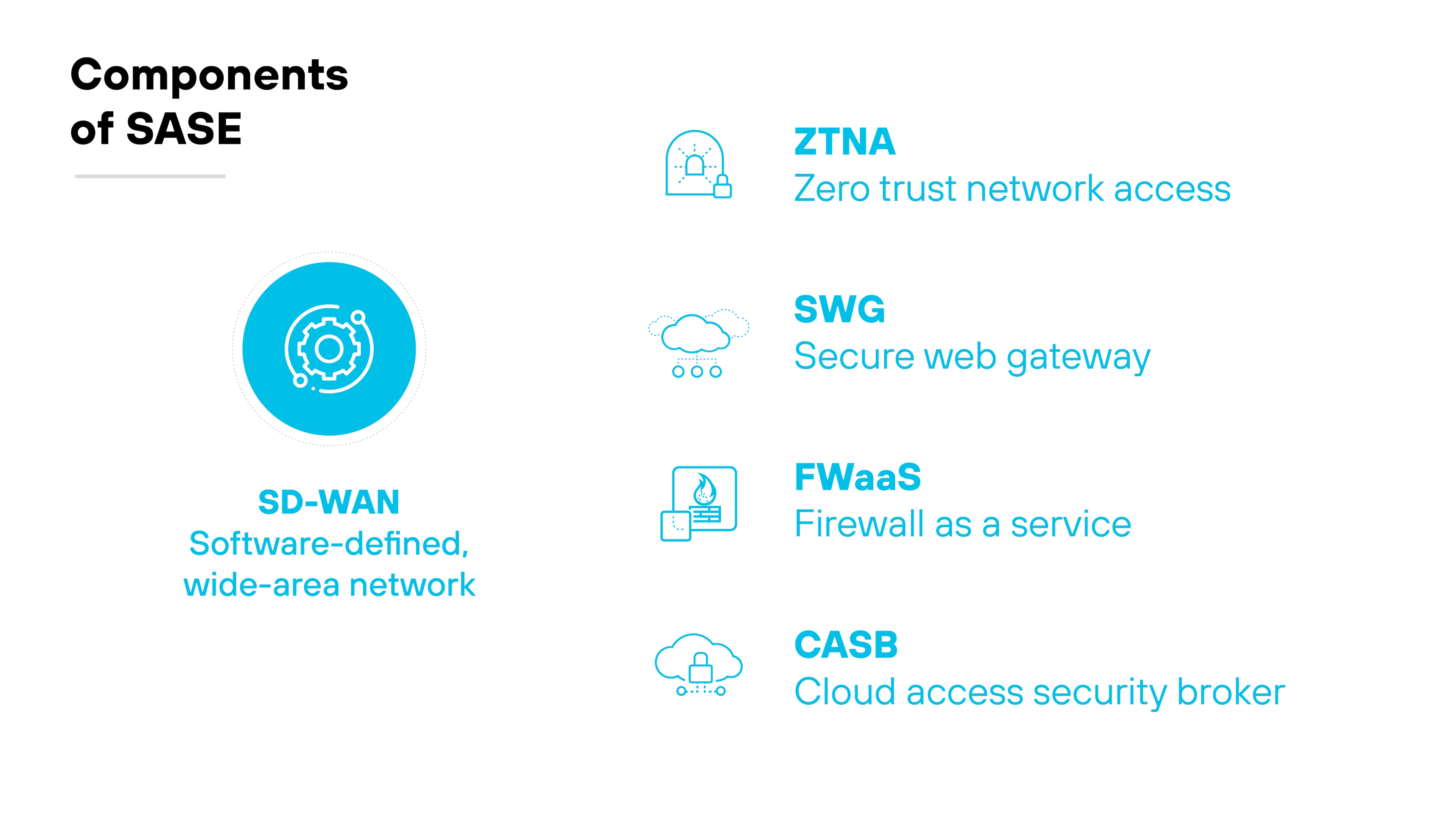
In a SASE architecture, SD-WAN manages how traffic flows between endpoints and cloud applications, ensuring efficient and policy-based routing.
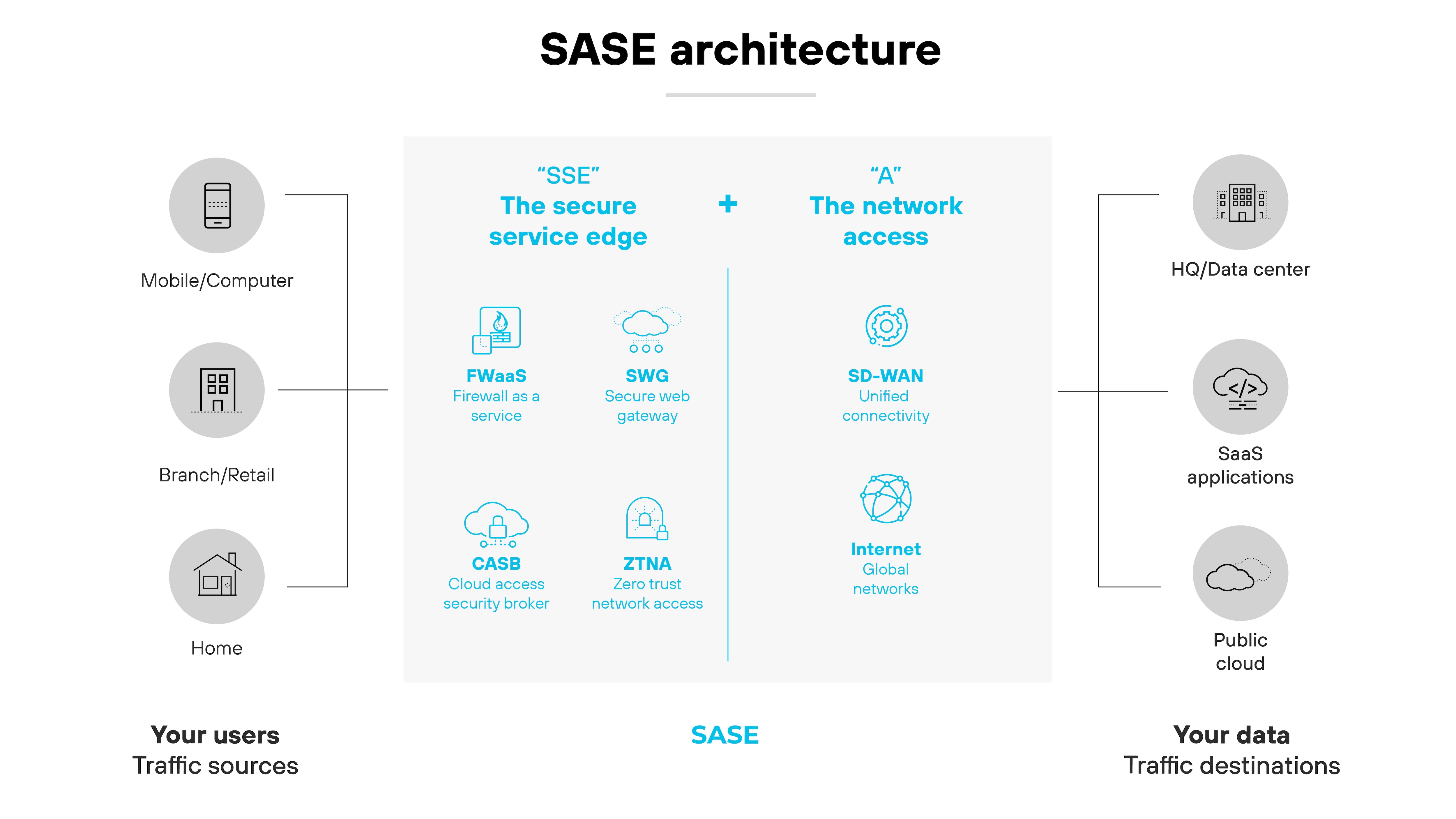
Functionally, SASE depends on SD-WAN to deliver application-aware connectivity across distributed environments.;
While SASE unifies networking and security in the cloud, SD-WAN handles the transport—making it a foundational part of SASE infrastructure. Without SD-WAN, SASE lacks the dynamic, software-defined routing needed to optimize network traffic.
The combination allows organizations to shift away from data center–centric designs. It supports direct-to-cloud access, enhances scalability, and helps enforce consistent security policies at every edge.
How is AI used in SD-WAN?
Artificial intelligence (AI) is becoming a core capability in SD-WAN solutions. It's being applied across the full network lifecycle—from initial setup to long-term management. And it's not just a bonus feature anymore. AI is starting to shape how SD-WAN is configured, maintained, and optimized.
AI and machine learning (ML) are already being used to simplify configuration, automate routine tasks, and reduce operational overhead. That includes things like dynamic traffic routing, intelligent alerting, and faster problem resolution. These capabilities can reduce the time it takes to deploy, adjust, and troubleshoot the network.
AI is also helping improve visibility and performance. Some solutions now offer AI-driven analytics to detect anomalies, recommend policy changes, and predict potential issues before they affect users. This shift toward self-healing and self-optimizing networks is aimed at reducing manual intervention and improving end-user experience.
Longer term, AI is expected to play an even greater role in how SD-WAN evolves. Many organizations will lean on AI not just for efficiency, but also to support broader shifts like hybrid work, multicloud environments, and integrated security. The challenge will be balancing automation with trust—and ensuring AI adds value without introducing new risks.
- Machine Learning (ML) and Artificial Intelligence (AI) Are Key Technologies for SD-WAN
- How Does SD-WAN Automation Simplify Network Operations?
How SD-WAN works with complementary technologies
SD-WAN is designed to work alongside other technologies to deliver both performance and security.
Let's take a closer look at how SD-WAN interacts with two key technologies: firewalls and 5G.
SD-WAN and firewalls
Firewalls and SD-WAN serve different functions but can work together as part of a unified solution. SD-WAN focuses on optimizing and routing network traffic, while firewalls inspect and enforce policies to protect that traffic.
The two are commonly integrated to secure distributed environments without compromising performance.
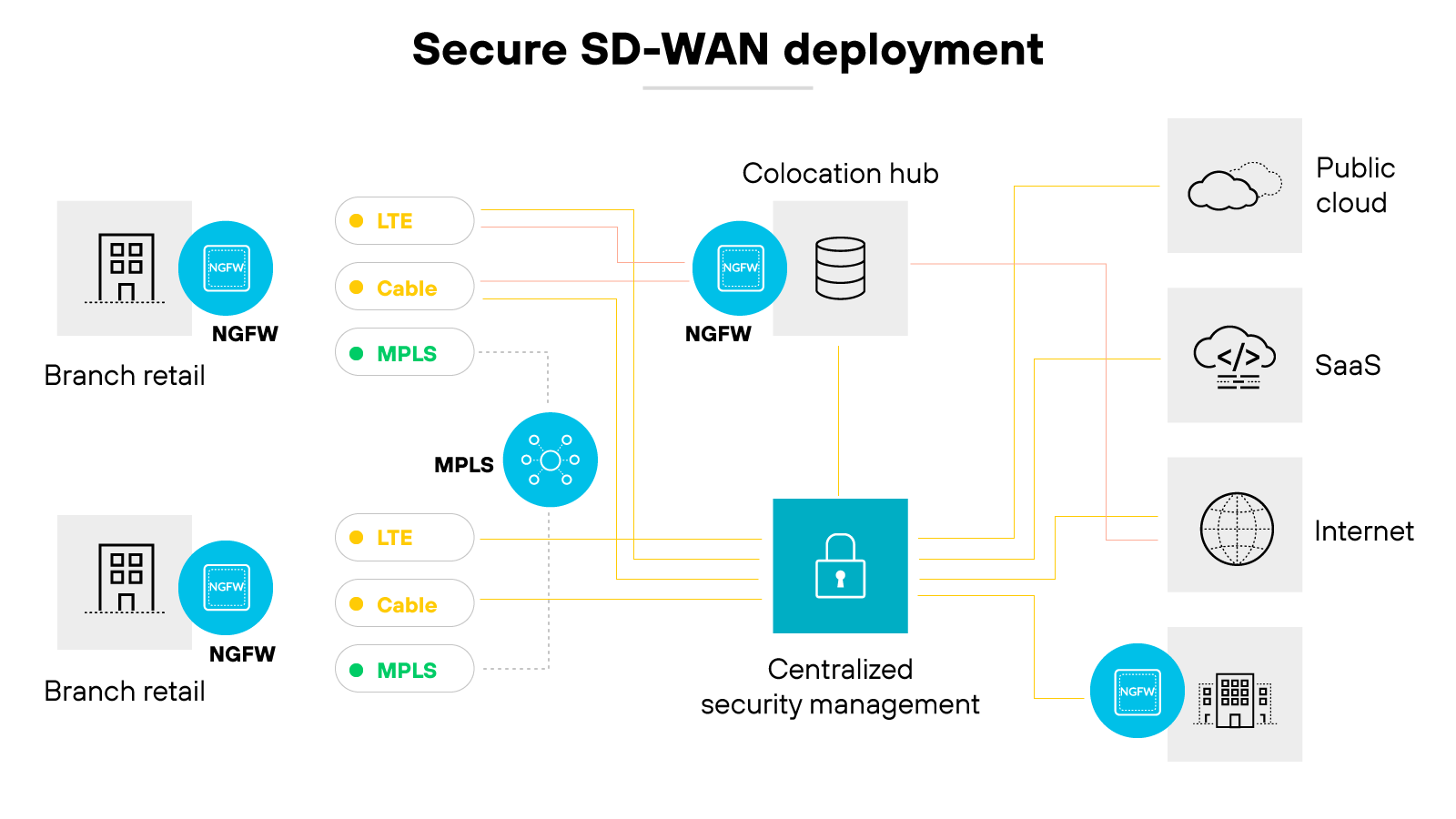
When firewalls are built into or deployed alongside SD-WAN, organizations gain centralized control over both routing and security. That means consistent policy enforcement across all sites, better protection against threats, and simplified management.
It also reduces the risk of misconfigurations that can happen when networking and security tools operate separately.
SD-WAN and 5G
The relationship between SD-WAN and 5G is still evolving. SD-WAN is well positioned to make use of 5G as an additional transport option—just like broadband or MPLS. The idea is to dynamically steer traffic across all available connections, including 5G, to improve performance and redundancy.
However, the pairing is still in its early stages. 5G infrastructure is still being built out, and practical enterprise use cases are limited.
That said, SD-WAN's ability to manage multiple links could help businesses experiment with 5G connectivity, especially in mobile, remote, or temporary environments where wired options aren't viable.
Comparing SD-WAN with other security and technology solutions
SD-WAN doesn't operate in isolation. It overlaps with—and is often compared to—a range of networking and security technologies.
Understanding how SD-WAN stacks up across key categories like performance, scalability, and security can help clarify its role in modern infrastructure.
Below is a side-by-side breakdown to help distinguish where SD-WAN fits and how it differs from other solutions.
| Feature | SD-WAN | MPLS | VPN | SSE | SDN | NaaS | Traditional WAN |
|---|---|---|---|---|---|---|---|
| Network architecture | Software-defined overlay across multiple WAN links (MPLS, broadband, LTE) | Private circuit-based WAN using label switching | Encrypted tunnels over public internet | Cloud-delivered security without network transport | Control plane separated from data plane for LAN/DC networks | Network delivered as a service via cloud provider | Point-to-point circuits, hardware-based routing |
| Traffic management | Dynamic path selection and application-aware routing | Static routing with QoS for guaranteed paths | Single-path static routing | Secures user-to-app traffic via PoPs | Central controller programs switches | Managed service provider handles traffic policies | Static routes; traffic flows to central data center |
| Performance | Low latency and optimized for cloud apps | High performance, but limited cloud optimization | Performance varies by internet conditions | Improves app access without SD-WAN path control | Optimized within data centers or telco networks | Performance varies by provider SLAs | Latency-prone for cloud apps |
| Security | Integrated security (NGFW, encryption, SASE-ready) | Private but lacks built-in threat prevention | Encrypts data but limited inspection or segmentation | Zero Trust, SWG, CASB, DLP, FWaaS | Requires integration with external security | Provider-managed security policies | Separate firewalls and security layers needed |
| Cost structure | Reduces costs by leveraging cheaper connections | Expensive circuits with higher operational costs | Low-cost, suitable for simple remote access | Subscription pricing; no network components | CapEx-driven; savings in operational agility | Subscription-based with flexible pricing | Costly MPLS; complex to maintain |
| Scalability | Highly scalable with centralized policy deployment | Scaling requires provisioning new circuits | Basic scalability; adds complexity at scale | Scales by adding users/apps; no physical constraints | Highly programmable, abstracted infrastructure | On-demand scale via service catalog | Difficult to expand and scale quickly |
| Management and visibility | Centralized control with visibility into app and network performance | Limited visibility; managed by service providers | Minimal monitoring; limited visibility | Centralized cloud-based security visibility | Deep visibility into network flows | Visibility limited to provider dashboard | Low visibility; fragmented management |
| Deployment flexibility | Physical, virtual, and cloud-based deployment | Physical links managed by telcos | Client-based or site-to-site configurations | Requires integration with existing network | Software-based control of physical/virtual devices | No hardware required; fully cloud-delivered | Physical site installs, centralized topology |
| Primary use cases | Cloud access, branch connectivity, app performance, security | Private WAN connectivity, real-time app SLAs | Remote access and secure point-to-point connections | Secure web access, cloud security, ZTNA | Data center automation, service provider core | Outsourced network ops, remote work enablement | Hub-and-spoke networks, site-to-site connectivity |
- What Is the Difference Between SD-WAN and MPLS?
- SD-WAN vs. VPN: How Do They Compare?
- What are the differences between SD-WAN and SDN?
- SD-WAN vs. NaaS: What Are the Differences?
- Traditional WAN vs. SD-WAN: What Are the Differences?
- SD-WAN vs MPLS vs Internet: What’s the Difference? Which is Right for Your Organization?
