- What Is the Difference Between IoT and OT Security?
- What is OT security?
-
What Is IT/OT Convergence?
- What Is OT?
- What Is the Difference Between IT and OT?
- How and Why IT and OT Are Converging
- Types of IT/OT Convergence
- The Role of IoT and IIoT in IT/OT Convergence
- IT/OT Security Convergence
- Impacts of IT/OT Convergence on ICS Security
- IT/OT Convergence Benefits
- IT/OT Convergence Challenges
- IT/OT Convergence Use Cases and Examples
- IT/OT Convergence Best Practices
- IT/OT Convergence FAQs
- What Is Critical Infrastructure? Why Does Critical Infrastructure Security Matter?
-
The Impact of IT-OT Convergence on ICS Security
-
Building Secure Smart Cities in the Age of 5G and IoT
- What Are the Differences Between OT, ICS, & SCADA Security?
- What Is the Difference Between IT and OT? | IT vs. OT
-
How to Secure IoT Devices in the Enterprise
-
What Is 5G Security? A Primer on 5G Network Security
- What is the difference between 4G and 5G security?
- What makes 5G networks harder to secure?
- What exactly needs protecting in a 5G network?
- What are the biggest 5G security risks?
- What security features are built into 5G?
- Who's responsible for keeping 5G secure?
- Which environments demand the strongest 5G security?
- What's next for 5G security?
- 5G security FAQs
-
What Is ICS Security? | Industrial Control Systems Security
- What is an ICS?
- Why is ICS security important?
- How does ICS security work?
- What is the role of IT/OT convergence in ICS security?
- What kinds of cyberthreats commonly impact ICSs?
- What are the main ICS security challenges?
- What are the primary ICS protocols?
- How to achieve ICS security step-by-step
- 10 ICS security best practices
- What are the primary ICS security frameworks, standards, and regulations?
- What is ICS supply chain security?
- 2025 ICS security market and trends
- What are the different types of industrial control systems?
- What are the components of an industrial control system?
- What are the differences between OT, ICS, SCADA, and DCS?
- How does ICS security compare with OT and SCADA security?
- What is the history of industrial control systems?
- ICS security FAQs
-
What Is the Purdue Model for ICS Security? | A Guide to PERA
- How does the Purdue Model for ICS Security work?
- What are the Purdue Model layers?
- What are industrial control systems?
- What are the main ICS architecture security challenges?
- What kinds of cyberthreats commonly impact ICS?
- What is the history of the Purdue Model?
- Examining the Purdue Model’s role in modern ICS security
- Purdue Model for ICS Security FAQs
IT vs. OT Security | What Are the Differences?
The differences between IT and OT security include security priorities, systems protected, threat response process, regulatory and compliance issues, and rates of technological change.
IT security focuses on protecting data confidentiality, integrity, and availability. OT security emphasizes the safe and continuous operation of physical processes and requires careful planning for system updates.
What is OT security?
OT security is concerned with protecting operational technology (OT) systems, such as supervisory control and data acquisition (SCADA) systems and industrial control systems (ICS), which are crucial in industries like manufacturing, utilities, and transportation.
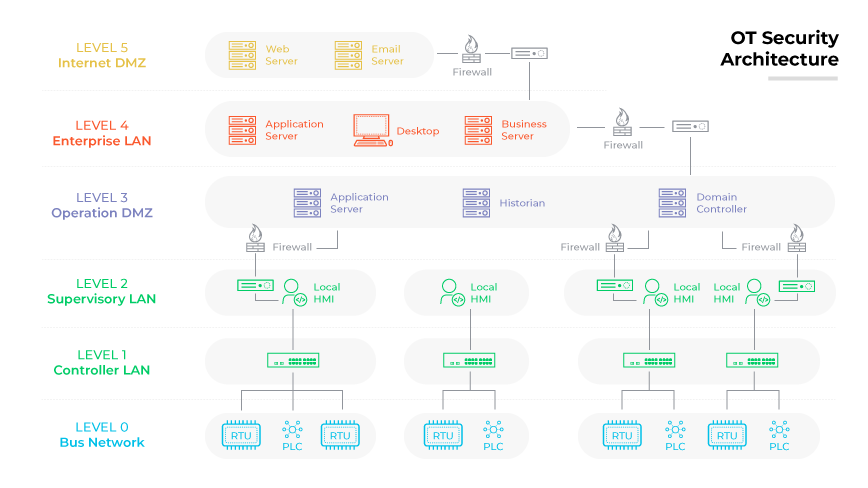
OT systems are responsible for controlling and monitoring industrial processes. Given the increased connectivity proliferating globally, the protection and integrity of OT systems have become even more essential. Strong security measures are critical to defending against a range of cyber threats and vulnerabilities.
OT security measures tackle unique challenges found in industrial settings. Unlike IT systems, OT systems prioritize operational efficiency and safety above all.
More specifically, OT security is dedicated to protecting physical systems that oversee and manage operations.
For example: In an electric utility company, OT security protects systems like supervisory control and data acquisition (SCADA), which control power grid functions. A cyberattack on SCADA could disrupt electricity distribution, leading to widespread outages and physical damage.
The objective is to ensure physical systems are secure from unauthorized access and cyber threats while preserving operational continuity.
What is IT security?
Information technology (IT) security, commonly known as IT security, involves protecting an organization's IT assets—such as computer systems, networks, digital devices, and data—from unauthorized access, data breaches, cyberattacks, and other malicious activities.
The scope of IT security is extensive and typically involves a combination of technologies and security solutions. These work in tandem to mitigate vulnerabilities in digital devices, computer networks, servers, databases, and software applications.
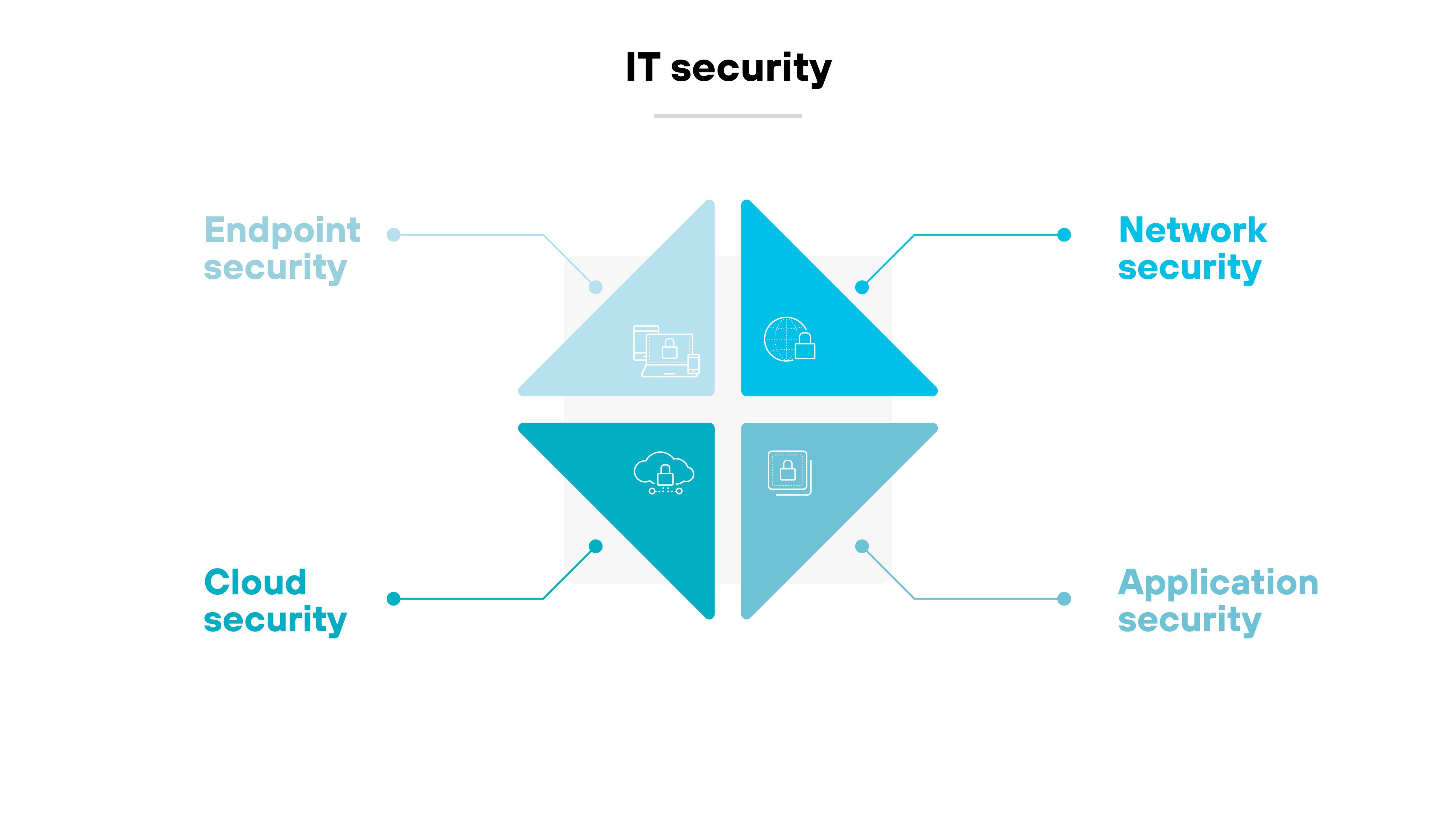
IT security can be further broken down into:
- Endpoint security
- Cloud security
- Network security
- Application security
IT security also encompasses physical security measures—like locks, ID cards, and surveillance cameras—that are crucial for protecting the facilities and devices housing data and IT assets.
IT security extends to safeguarding the entire technical infrastructure of an organization, including hardware systems, software applications, and endpoints such as laptops and mobile devices.
It protects both the company network and its components, like physical and cloud-based data centers. But it also ensures operational continuity by maintaining the integrity of these systems.
What are the differences between IT and OT security?
Information technology (IT) and operational technology (OT) security have distinct roles and challenges. While they both aim to shield assets from threats, the nuances in their functions and methods are significant.
Let’s delve into the differences to understand how IT and OT security each uniquely contribute to organizational safety.
Security priorities
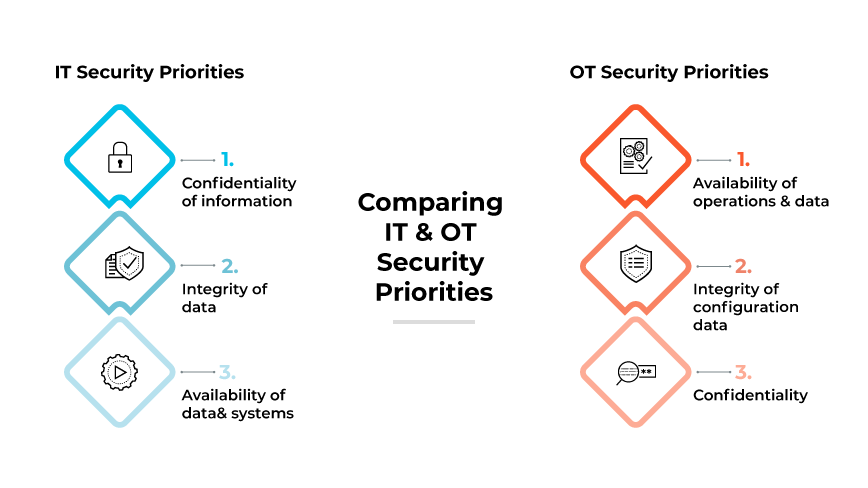
IT security focuses on safeguarding data confidentiality, integrity, and availability—often summarized as the CIA triad.
The main goal here is to protect the data from unauthorized access. And ensure that the systems delivering this data are always available and operate without tampering.
On the other hand, OT security prioritizes system availability and physical safety over confidentiality.
OT systems are designed to ensure continuous industrial operations and physical processes. Disruptions in OT can lead to direct physical harm to the operational environment or even catastrophic failures affecting human safety.
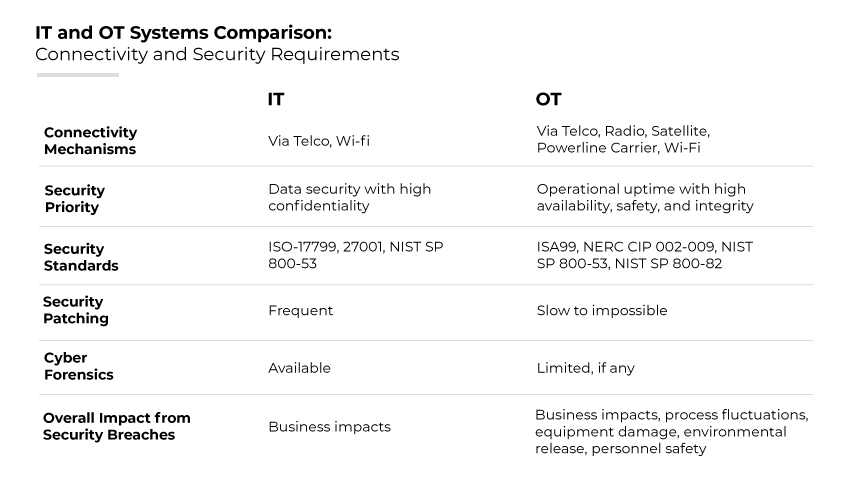
Systems protected
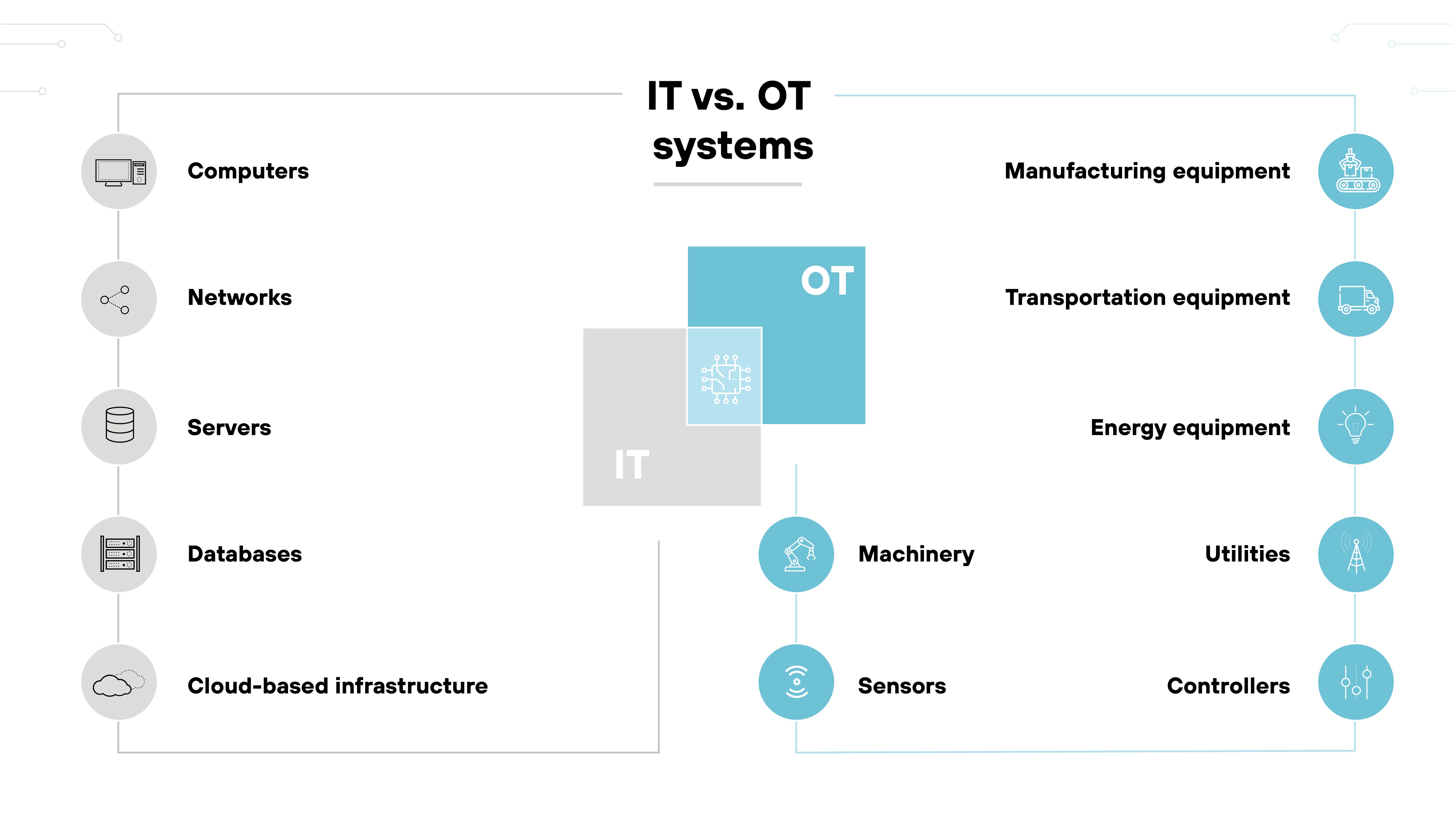
IT systems are dynamic, with data flows and connectivity designed to support organizational operations through communication and data processing. These systems are regularly updated and patched to defend against evolving cyber threats.
Conversely, OT systems manage direct monitoring and control of physical devices and processes in industries such as manufacturing, energy, and utilities.
These systems often run on legacy software that can’t be frequently updated or patched due to the risk of disrupting continuous operations. Which means they operate with a set configuration over an extended period.
Threat response process
In IT security, the threat response process can involve immediate software updates, patches, and system modifications to address vulnerabilities. Adaptability is crucial for defending against cyberattacks that exploit software flaws.
However, in OT security, the response often requires a more measured approach. Since OT systems are critical for ongoing physical operations, any changes must be carefully tested to avoid impacting the physical processes they control.
This leads to substantially longer periods between updates. Not to mention a heavier reliance on preventive measures—and robust monitoring to catch issues before they cause harm.
Regulatory and compliance issues
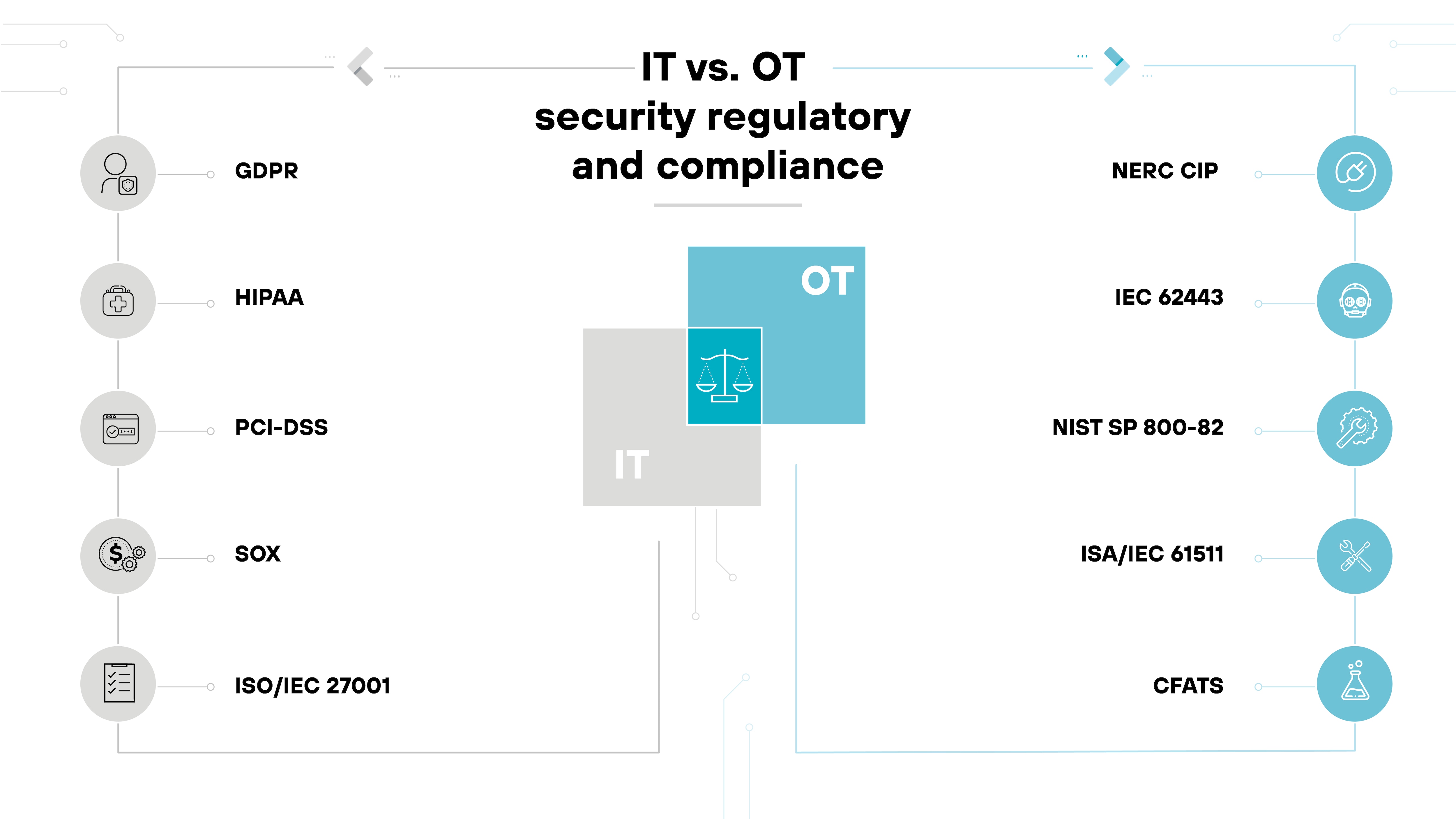
IT security is governed by a variety of standards and regulations that dictate how data should be handled and protected. Compliance with laws like GDPR for privacy, HIPAA for healthcare information, and others are central to IT security efforts.
OT security, while also subject to regulatory standards, often faces different compliance challenges centered around environmental safety and quality controls—such as those found in the critical infrastructure sectors.
Compliance here focuses on protecting information and maintaining system integrity to prevent failures that could lead to environmental or human harm.
Rates of technological change
IT security evolves fast, driven by changes in technology and cyber threats. New defensive technologies and strategies are being developed around the clock to protect against a constantly growing array of cyberattacks.
OT security evolves differently.
Changes are often driven by the need to integrate more advanced IT technologies into operational systems while still maintaining the uptime, reliability, and safety of control systems. The evolution here is cautious, balancing innovation with the imperative to protect critical physical operations.
What are the similarities between IT and OT security?
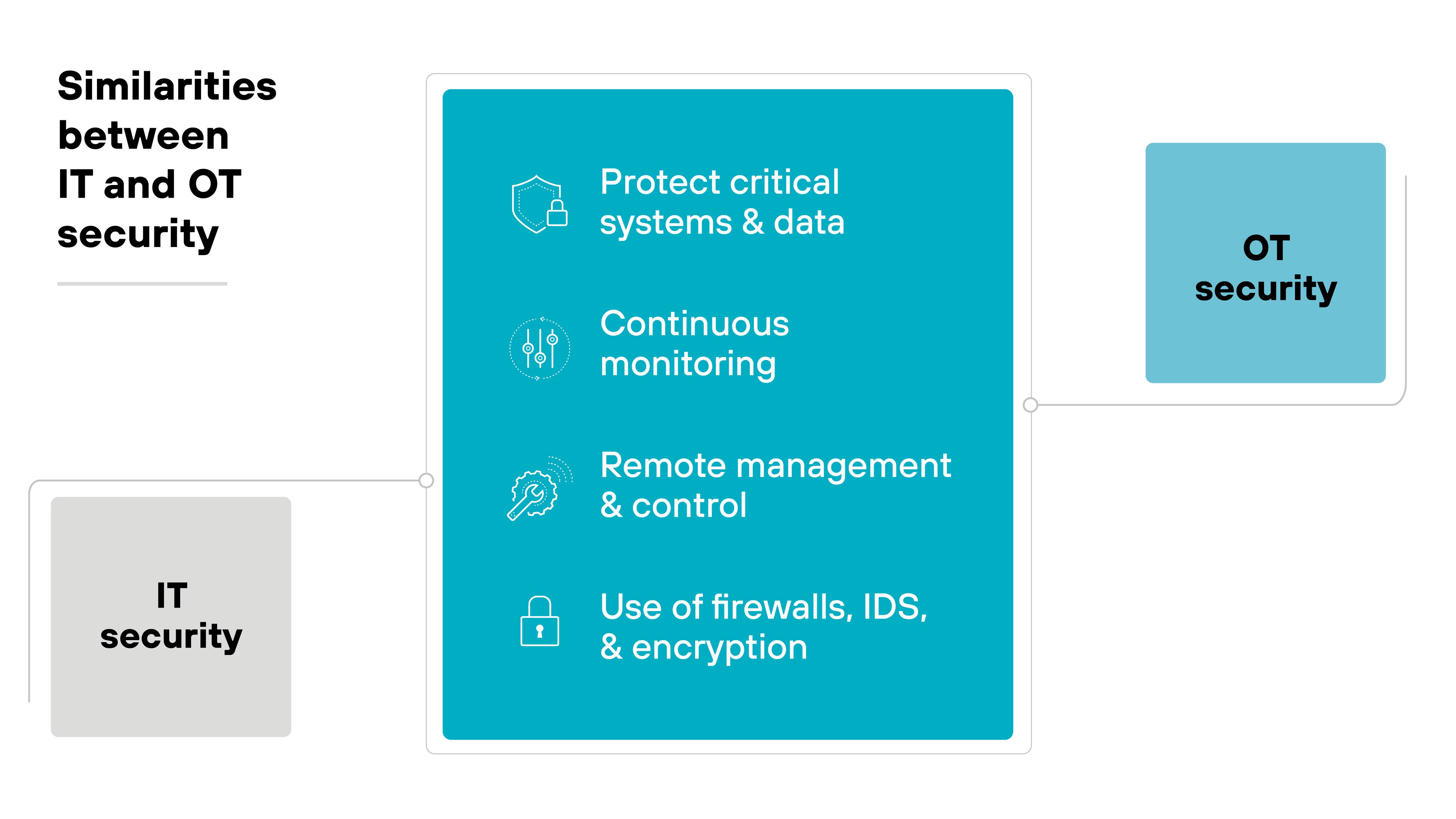
Despite their distinct roles, IT and OT security do have a few things in common, especially as the two areas increasingly overlap.
Both fields aim to protect critical systems and data from unauthorized access, cyberattacks, and operational disruptions.
This shared objective drives the implementation of security protocols and tools designed to identify and mitigate threats across digital and operational environments.
Another key similarity is the growing need for continuous monitoring.
Both IT and OT environments benefit from real-time insights into system performance and security status.
This allows for early detection of potential issues, whether they are network vulnerabilities in IT or operational malfunctions in OT systems. In both cases, this proactive approach helps maintain the integrity and functionality of the systems. And prevents larger problems from developing.
Additionally, IT and OT security now both rely heavily on remote management and control.
In the past, OT systems were largely isolated, accessible only on-site. But as connectivity has advanced, both IT and OT systems can be managed remotely, often through shared infrastructures.
The integration not only improves efficiency but also requires unified security measures to protect these increasingly interconnected networks.
Finally, both IT and OT security use common technologies like firewalls, intrusion detection systems, and encryption to secure their respective environments.
While the specific applications may differ, the underlying tools and principles of cybersecurity apply to both. The convergence of technologies has led to more integrated security strategies across organizations.
Why is it important that IT and OT security collaborate?

Collaboration between IT and OT security is becoming more important as the boundaries between these two domains blur.
Industries are continuing to embrace more interconnected, data-driven systems.
Which means that IT and OT are increasingly dependent on each other for maintaining security. By working together, IT and OT teams can bridge the gap between protecting digital assets and physical operations.
It's important for IT and OT teams to work together to create a security strategy that covers both areas effectively.
Which is why one of the primary reasons for collaboration is security itself.
OT systems that used to be isolated from the internet and external threats are now connected through technologies like the industrial internet of things (IIoT).
The increased connectivity introduces new vulnerabilities. IT teams bring valuable experience in cybersecurity, helping to secure these OT environments against cyberattacks that could disrupt operations.
When IT and OT teams collaborate, they can design and implement security measures that protect both physical systems and digital infrastructures.
Collaboration also facilitates far better use of data.
OT systems generate vast amounts of real-time data from industrial processes. However, without IT's capabilities in data analytics, much of this data remains untapped.
IT’s ability to process, analyze, and derive insights from OT data can lead to improvements in operational efficiency, predictive maintenance, and overall performance. When security teams from both domains work together, they can work together to make certain that data remains secure throughout its lifecycle—from collection to analysis.
It’s worth noting: Integrating IT and OT systems comes with a whole host of major, but manageable technical challenges.
Ensuring that they work seamlessly together requires expertise from both sides. IT can help OT transition to newer technologies while maintaining cybersecurity. OT can focus on keeping physical operation efficient and uninterrupted.
Ultimately, when IT and OT security align strategies, the result is a more secure, compatible infrastructure that supports business goals.
