When a security incident is detected, analysts and incident responders must have immediate access to the information required to efficiently and effectively scope, investigate, and contain the incident.
With these challenges in mind, let’s take a look at a few ways the Tufin Orchestration Suite, combined with Cortex™ XSOAR, can enable incident response teams to work more efficiently when faced with a potential security incident.
SOC Teams’ Context-Rich Analysis & Visibility With Tufin SecureTrack
When a potential incident is initially detected, it may arrive in the form of a single endpoint detection or IDS alert with very minimal information. A single alert is probably one of tens, hundreds, or even thousands of alerts routinely received. Organizations must quickly triage and prioritize each alert, as a single overlooked alert has the potential to manifest itself into a full-blown security incident.
The first steps in a successful response are to determine if the alert is in fact an incident, and if it is, then to begin enriching the initial alert data with additional context. Analysts and incident responders must be able to trust that the data used to make response-related decisions is accurate and up to date. Gathering this information is frequently a manual process, taking precious minutes or hours of triage time. This problem is compounded by the fact that analysts, network security teams and responders must often work in silos. They have to manually query multiple data sources to gather all the network intelligence required to effectively triage an alert, in an uncoordinated and asynchronous manner.
Context is the key. Without the proper context, it’s impossible to determine the potential risk to your organization and therefore, the appropriate response. Absent, incorrect, or obsolete network information leads to incorrect conclusions regarding the context of the incident, which can lead organizations to misjudge and mishandle their response to an incident.
Tufin SecureTrack delivers real-time network intelligence gathered directly from multi-vendor network security devices. This information includes network objects, security policies, routes, and more. SecureTrack automatically queries this information in real time, and doesn’t require manual input from network admins when a change is made.
SOC and network teams can also benefit from Tufin SecureTrack’s unified visibility to gain intelligence on network security posture, connectivity, path traversal, and hybrid network topology. Cortex XSOAR playbooks that extract this information can be used to automate everyday tasks, which may help to enhance incident response time-to-detection. See the figure below illustrating a sample workflow using Cortex XSOAR playbooks enriched with Tufin SecureTrack information.
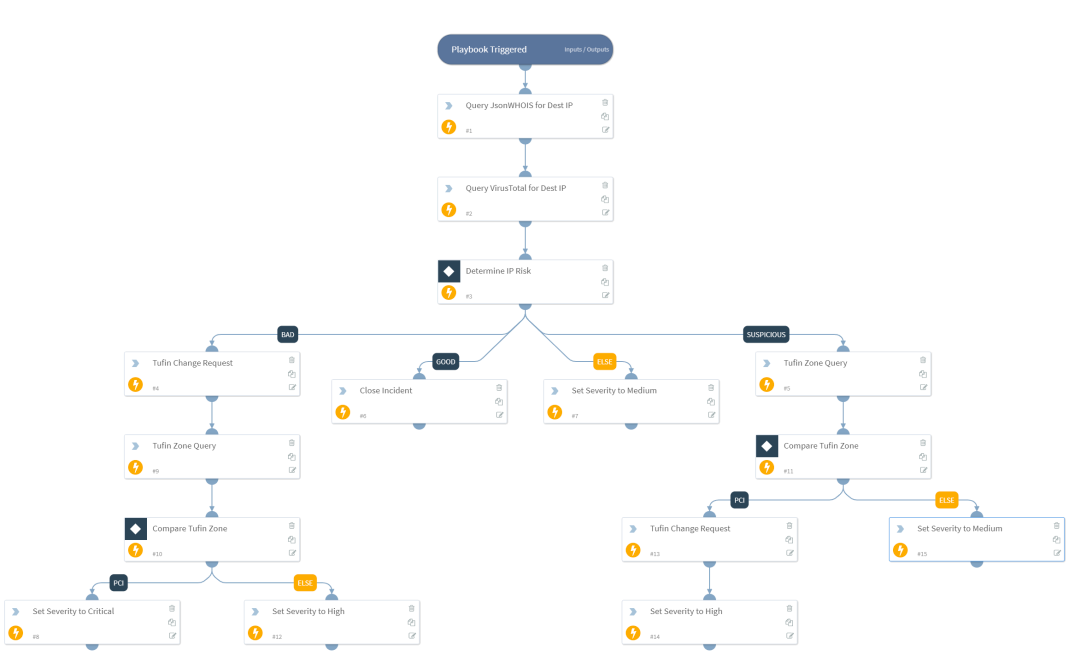
Containment and Remediation with Tufin SecureChange
Once a security incident has been identified, one of the primary goals of the incident response process is comprehensive and coordinated incident containment with accurate records of the information. Frequently described as “stopping the bleeding,” the focus of containment is to put immediate measures in place to contain the incident while further investigations can take place, and permanent remediation measures can be deployed. Often, incident containment includes blocking certain hosts, ports, or services by implementing new/changed network security policies to quarantine traffic or as a pass-through for obfuscation while the investigation continues.
Applying new security policies for incident containment poses two problems: First, designing and implementing these changes takes time and a thorough understanding of network topology, two things which analysts and incident responders often lack. In an enterprise network, blocking a new host, port, or service can impact business continuity due to the domino effect on underlying infrastructure.
Second, changes made during incident containment are frequently made outside of the organization’s normal change control process to expedite desired results. While the urgency of the incident may require going outside normal change control processes, bypassing the safeguards of the change control process may result in additional risk being inadvertently introduced to the network, critical services unintentionally being taken offline, or compliance violations, as changes are not properly recorded.
Tufin SecureChange has visibility into the entire network topology, whereby analysts and incident responders can block a host, port, or service by simply submitting a change request with a source and destination. Based on this information, SecureChange can then automatically design and provision the required change on the relevant network devices to ensure effective containment. Tufin’s playbook for Cortex XSOAR provides comprehensive actions that can be taken by the incident response team with the confidence that the impact of such a change is evaluated against your company’s security policy, and vetted out by all stakeholders for a synchronized response. See below for the sample ticket that can be created for incident response.

Enforcement and Assurance With Tufin and Cortex XSOAR
Accurate information for analysis and remediation is a hallmark of successful incident response. The Tufin Orchestration Suite provides responders with critical network information which is accurate, up to date, and actionable. Multi-vendor support enables visibility and control across a heterogeneous environment, serving as a single source of truth for the entire network. With these benefits, integrating Tufin with the native threat intelligence platform of Cortex XSOAR can significantly reduce the time to triage an alert and the mean time to respond (MTTR) to an incident.