Introduction
Credential-based attacks remain a persistent threat in modern cybersecurity. One of the most effective yet insidious techniques used by attackers is password spraying—attempting a few common passwords across many accounts to evade detection. To combat this threat, Cortex XSIAM’s Response and Remediation Pack includes the SSO Password Spray playbook, designed to detect, investigate, and contain password spraying attacks while minimizing disruption to legitimate users.
Threat Overview
Password spraying attacks exploit weak authentication policies by using a small number of common passwords against multiple accounts, bypassing traditional account lockout protections. In environments utilizing single sign-on (SSO), this method can be particularly effective as many users may reuse simple passwords across multiple services.
The SSO Password Spray playbook responds to the following alerts:
- SSO Password Spray Threat Detected
- SSO Password Spray Activity Observed
- SSO Password Spray Involving a Honey User
Purpose of the Playbook
The SSO Password Spray playbook automates the detection, triage, and remediation of password spraying incidents by:
- Checking the reputation of IPs involved in login attempts.
- Fetching related login event data for further investigation.
- Analyzing user risk levels and login behavior to detect anomalies.
- Verifying MFA configurations to identify vulnerable accounts.
- Clearing active sessions for compromised accounts to prevent misuse.
- Blocking suspicious IPs to mitigate further attacks.
- Forcing password resets for users without multifactor authentication (MFA).
Stages of the Playbook
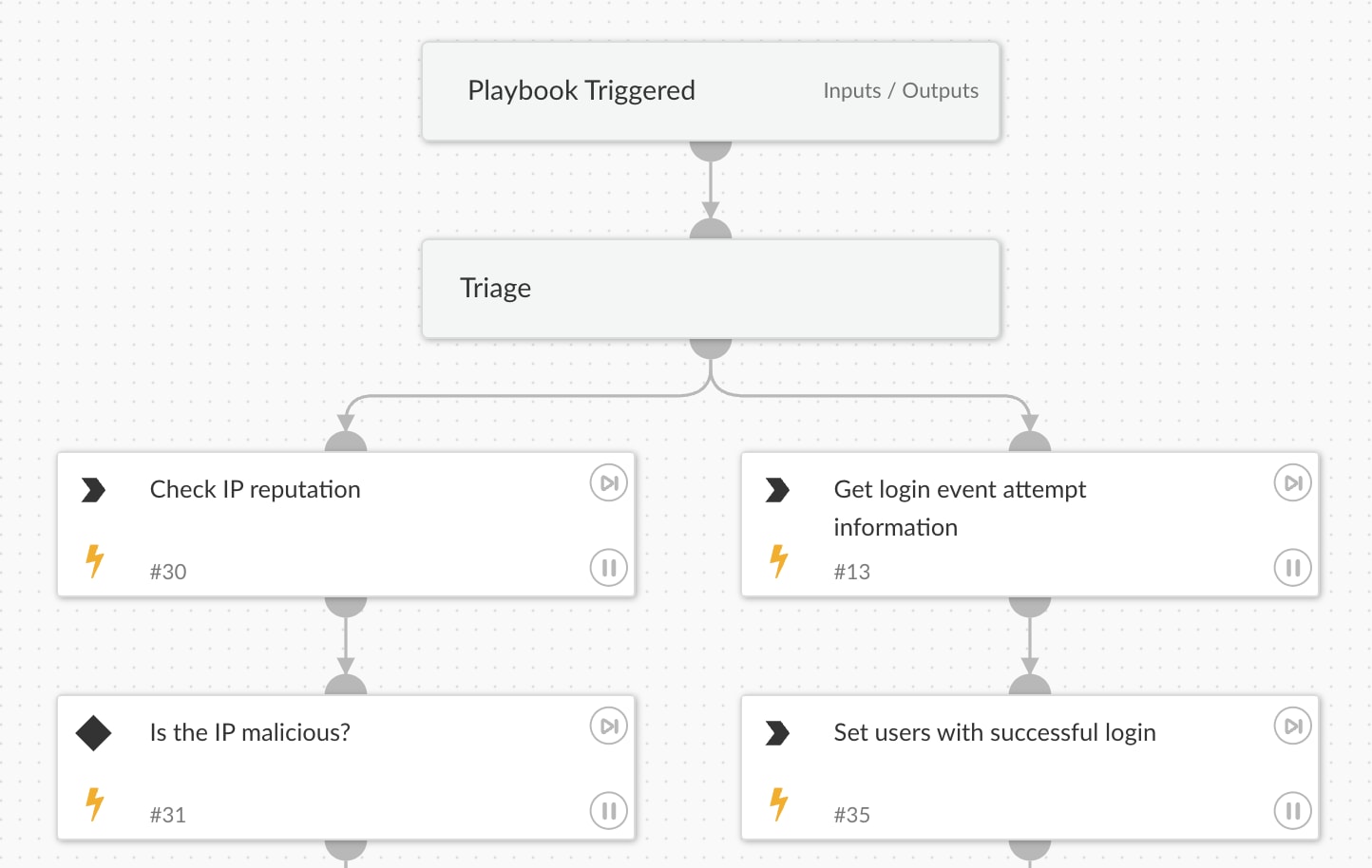
Triage
The playbook starts by collecting key information:
- IP Reputation Check: Determines whether the login attempt originated from a suspicious or malicious IP.
- Event Correlation: Fetches logs and details of recent login attempts to assess potential compromise.
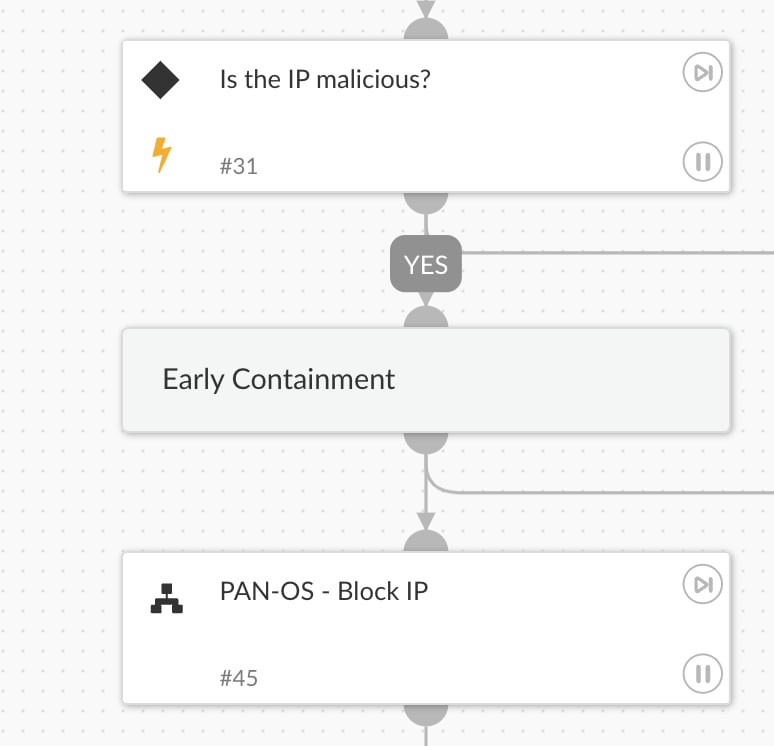
Early Containment
- If the detected IP is flagged as suspicious, the playbook suggests blocking it to prevent further attacks.
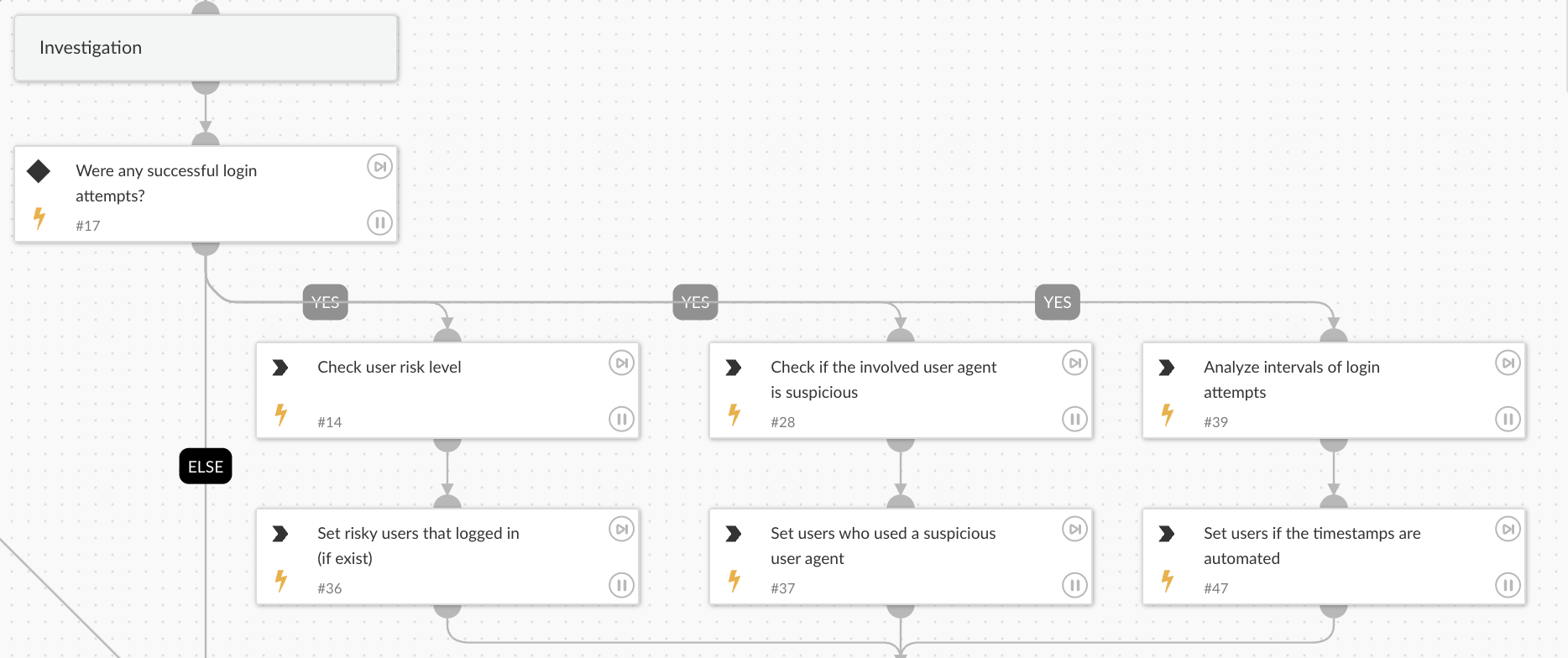
Investigation
- Risk Score Analysis: Evaluates the user’s risk level using advanced AI logic to determine if they are a likely target of an attack.
- User Agent Inspection: Examines the device and browser fingerprints to detect malicious automation.
- MFA Verification: Checks if the impacted user has multifactor authentication enabled.
- Time Interval Analysis: Analyzes login attempt timestamps to identify automated attack patterns.
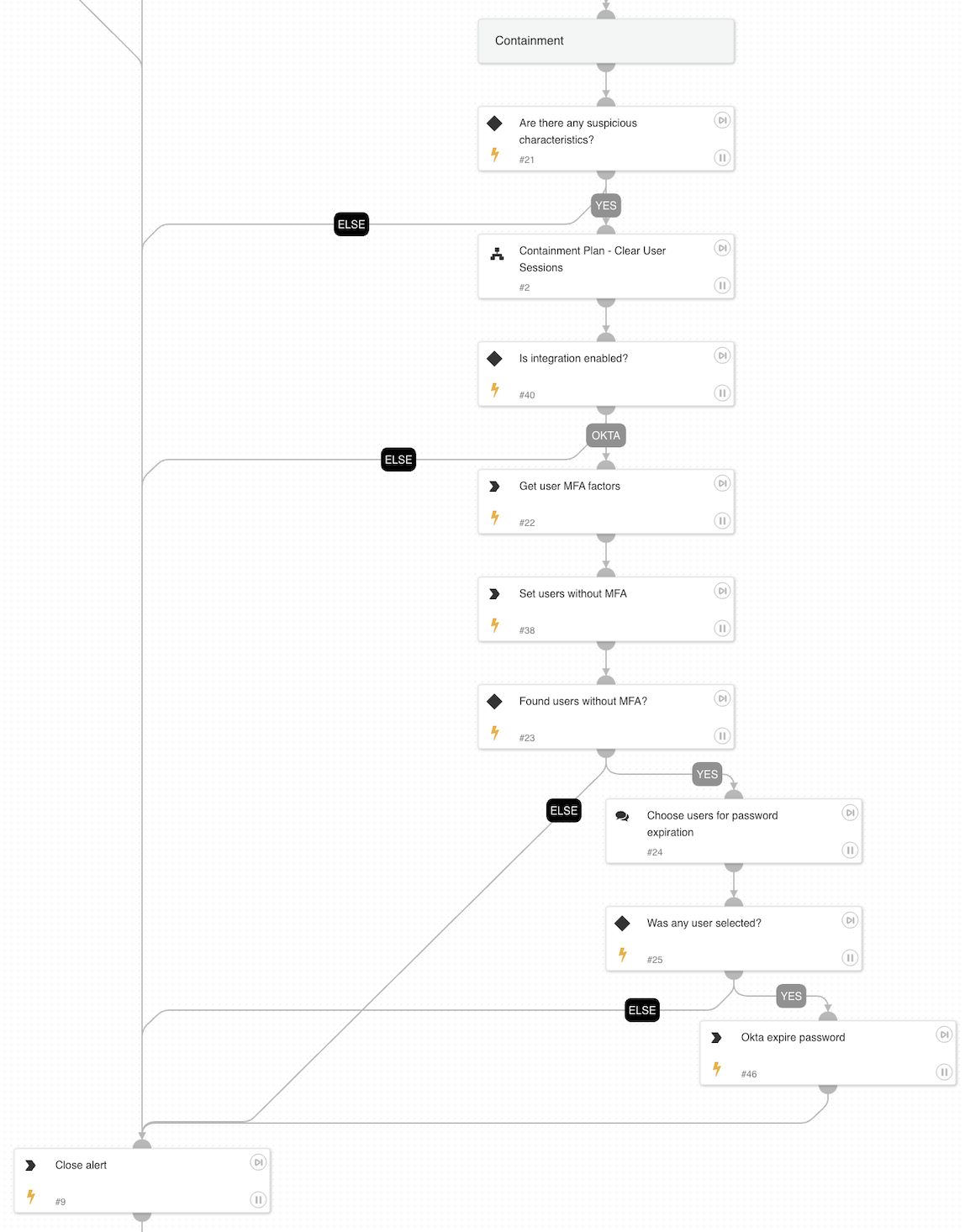
Containment
- If a successful login was detected:
- Clears user sessions to revoke potential attacker access.
- If the risk score is high or suspicious activity is detected, the playbook recommends password expiration for users without MFA.
Integration Requirements
To execute remediation actions, at least one of the following integrations must be enabled:
- Microsoft Graph User
- Okta
These integrations allow the playbook to clear user sessions and enforce security policies dynamically.
Security Challenges Addressed
- Minimizing False Positives: By analyzing behavioral patterns and risk scores, the playbook ensures legitimate users are not disrupted unnecessarily.
- Automated Response: Immediate remediation actions such as session termination and password resets prevent attackers from exploiting compromised credentials.
- Threat Intelligence Integration: Using IP reputation services and behavioral analysis to enhance detection capabilities.
- MFA Enforcement: Encouraging MFA adoption by detecting and flagging users who lack it.
Conclusion
The SSO Password Spray playbook is a critical asset for security teams looking to automate response to password spraying attacks while ensuring minimal disruption to legitimate users. By leveraging threat intelligence, behavioral analysis, and real-time remediation actions, organizations can fortify their authentication security and prevent credential-based breaches.
Learn More
For a deeper dive into the Cortex XSIAM Response and Remediation Pack, check out the full documentation here: Cortex Response and Remediation Pack.