In most cases, SlackAsk does not provide enough information suitable for analyst investigations, as it focuses mainly on binary “yes/no” questions. Creating independent SlackAsk tasks used to require a very steep learning curve for SOC engineers, who would have to create manual playbooks to collect all the information needed for incident handling. Because of this, it became fairly common for SOC engineers to use the SlackV3 content pack purely as a notification utility.
However, you shouldn’t have to be a Slack power user to utilize all that Slack blocks are capable of providing. Data collection is critical during the incident response process, and Slack blocks can provide SOC teams with truly useful and interactive workflows to utilize.
Introducing the Slack Content Pack
The Slack V3 content pack allows you to interact with the Slack API by collecting logs and sending messages and notifications to your Slack team. It integrates with Slack's services to investigate failed login events and execute, create, read, update, and delete operations for employee lifecycle processes.
This pack is designed to help increase communications and collaboration throughout your SOC team. It includes the ability to mirror the investigation between Slack and the Cortex XSOAR War Room, so security analysts are able to work on their platform of choice and have all actions mirrored on the other platform. It also allows for the administration and management of Slack channels, including creating and archiving channels, setting the topics, inviting, and removing users. It even retrieves details about a specified user and returns the integration context as a file for debugging purposes.
The automations found within the Slack integration include SlackAsk, which sends a message or question to a user in a direct message or to a channel. The message includes predefined reply options, as well as closing a conditional task found within a playbook.
Another automation included in this pack is the new SlackBlockBuilder, which will re-format a Slack Block into a format readable by the SlackV3 integration. The script will also send the block to the given destination. SOC engineers can design their own messages using Slack’s Block Kit Editor and simply save the payload as an XSOAR list item. The SlackBlockBuilder will take care of the rest to help eliminate all of the guesswork.
The Cortex XSOAR Slack Integration is a powerful tool for SOC engineers that gives organizations the ability to have full control over their own Slack app. With the introduction of the SlackBlockBuilder, teams can bring a whole new level of interactivity to incident response. With new features and customizations released regularly, this content pack provides everything that you need to make the most out of Slack’s services.
See It In Action
Let’s build a block to handle a common task: Triaging incidents.
Using the Slack Block Kit Builder, we designed the following message to send to a team member and all we have to do is copy the payload JSON, which looks like this:
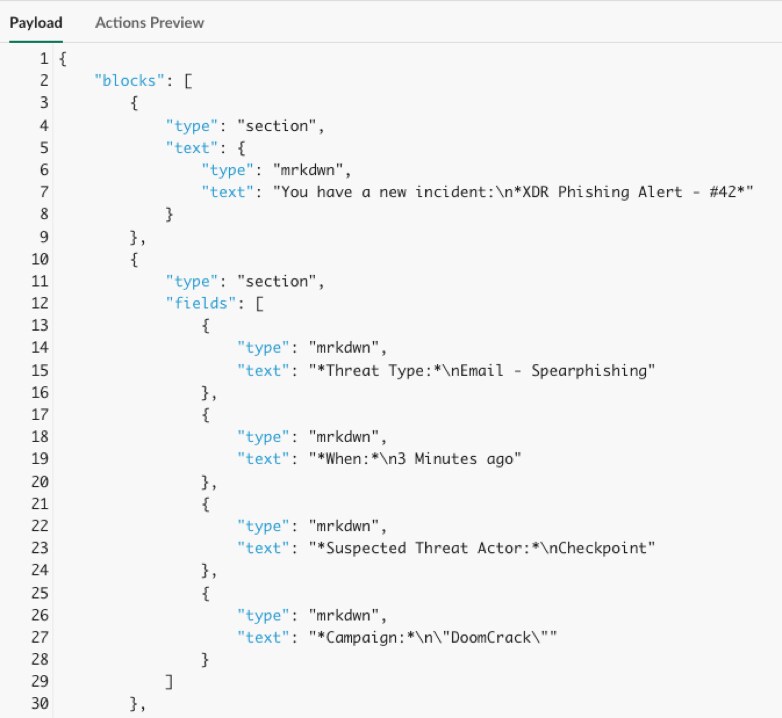
We can then paste the JSON into a new XSOAR list. We will give the list an easy to remember name like “SpearphishingAsk '' and set the Content Type to “JSON”.
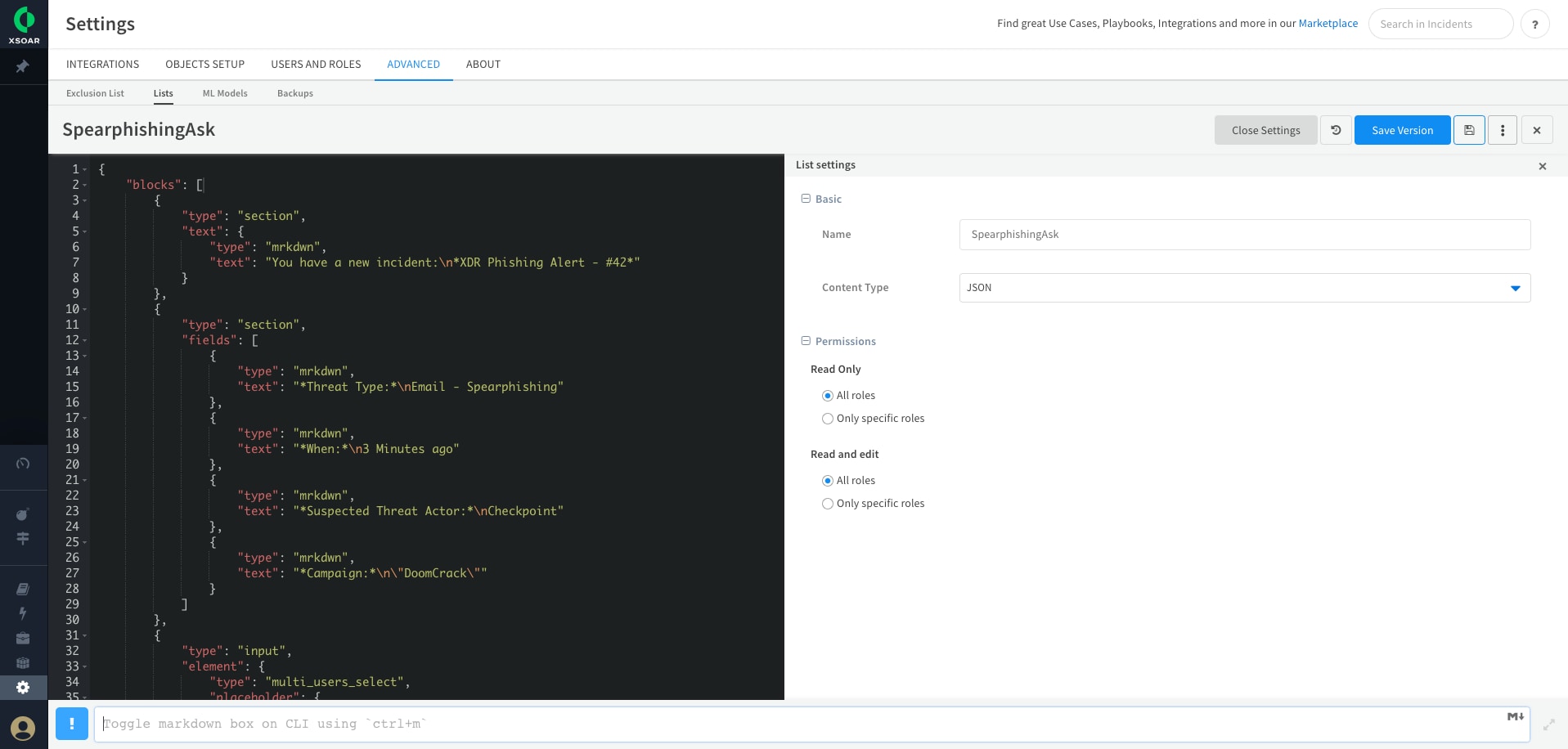
That’s all we need to do to create an interactive message for Slack. Firing the !SlackBlockBuilder list_name=SpearphishingAsk channel=Random command in an incident will send off our message and SlackV3 will then wait for a response to the message.
Here is what the response looks like:
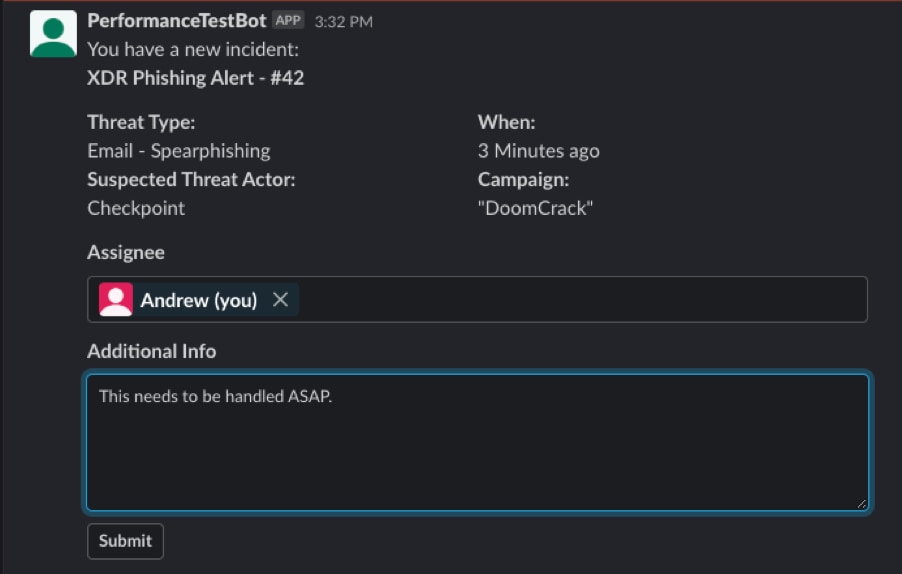
Looking at the context of our incident we can see that the Assignee was “Andrew” and the Additional Info indicates “This needs to be handled ASAP.”
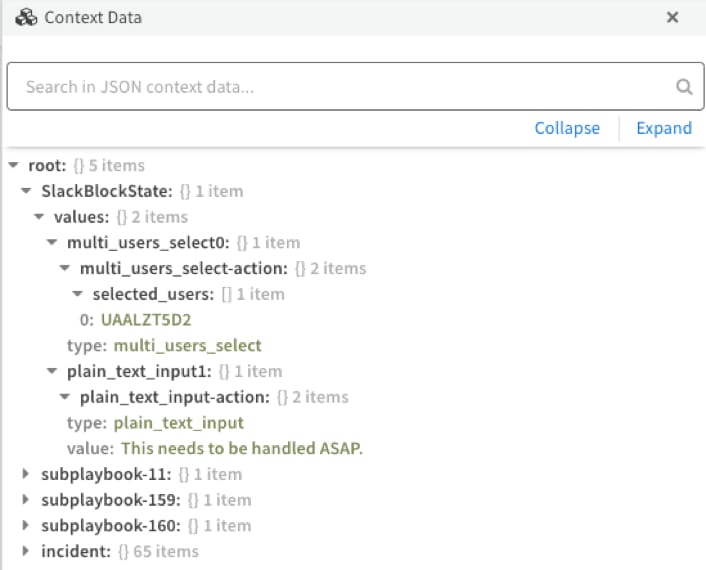
Now that we have all of the information that is needed from the user, we can use the context data in subsequent playbook tasks.
For more information on the Slack Content Pack and other XSOAR packs and playbooks, visit our Cortex XSOAR Developer Docs reference page.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.