As macOS grows in popularity with business users, cyberattacks are increasing in parallel. Today, macOS represents 15% of desktop operating systems, with Windows around 73%1. Given the smaller share, many security vendors have invested less or not at all in protecting macOS.
But it only takes a single compromised endpoint to gain initial access. So, it really doesn’t matter what the operating system is—everything running code can be vulnerable.
With Cortex XDR, we are investing even more in protecting macOS with updates to the XDR agent and detection analytics within the Cortex platform. Like every operating system we protect with Cortex–macOS, Windows, Linux, iOS, Android, and cloud-specific architectures like Kubernetes–we continuously assess how threat actors operate, and build adaptive defenses to stop them.
With macOS we’ve seen two prominent categories of threat activity:
- Infostealers: These focus on covertly extracting sensitive information like cookies, passwords, and certificates without the need for long-term presence, making them less persistent.
- AppleScript: Attackers widely leverage AppleScript due to its versatility in automation and inter-process communication, allowing execution of malicious actions such as accessing files, executing shell commands, interacting with services, manipulating remote applications, and setting/hooking browser activities.
In many cases, these activities will be prevented in real-time by the Cortex XDR agent. The Cortex XDR agent contains multiple layers of security, from exploit prevention, to local file analysis with AI, and behavioral threat protection which monitors processes on an ongoing basis.
In parallel, the Cortex XDR agent sends telemetry to the Cortex platform, where it is stitched with all other available data sources, like your identity providers, cloud infrastructure, or firewalls. Together, this data paints a comprehensive picture of the activity in your organization.
That picture is always being painted—it is a pipeline of data continuously flowing, and stitching. At the same time, thousands of machine learning models and analytics detectors evaluate the stitched data, looking for malicious activity.
In our February 2025 Cortex release, we’ve added several new detectors specifically focused on identifying macOS threat activity in this real-time data pipeline. That means security operations teams don’t have to hunt for these threats - we’ve built the detection rules for you and surface them immediately in your incidents. Let’s take a look at what’s new:
New MacOS Detectors for February 2025: Stealers
- Crypto stealing
- Notes stealing
- Web browsers history stealing
- Messaging apps stealing
- Web credentials grabbing
- Rare process touched Keychain
- Session cookies
- FTP credentials stealer
New macOS Detectors for February 2025: AppleScript
- Osascript executed with rare command line
- AppleScript executed rare process
- AppleScript executed secondary script
When one of these new detectors finds a threat, you’ll see an alert which will be grouped with all other alerts related to the same attack in a single incident. As you dive into your investigation, you can see the process chain that caused the alert, in the Cortex XDR Causality View.
In the following example, an infostealer accessed a Keychain file, which is used to store passwords on macOS. The detector, named “Rare process accessed a Keychain file"—saw this happen in real time. We give this detector the knowledge of all the processes we see accessing Keychain files worldwide, so it knows what to look for. Now, as an analyst, you can use this detection to shut down the process and stop the infostealer attack in its tracks.
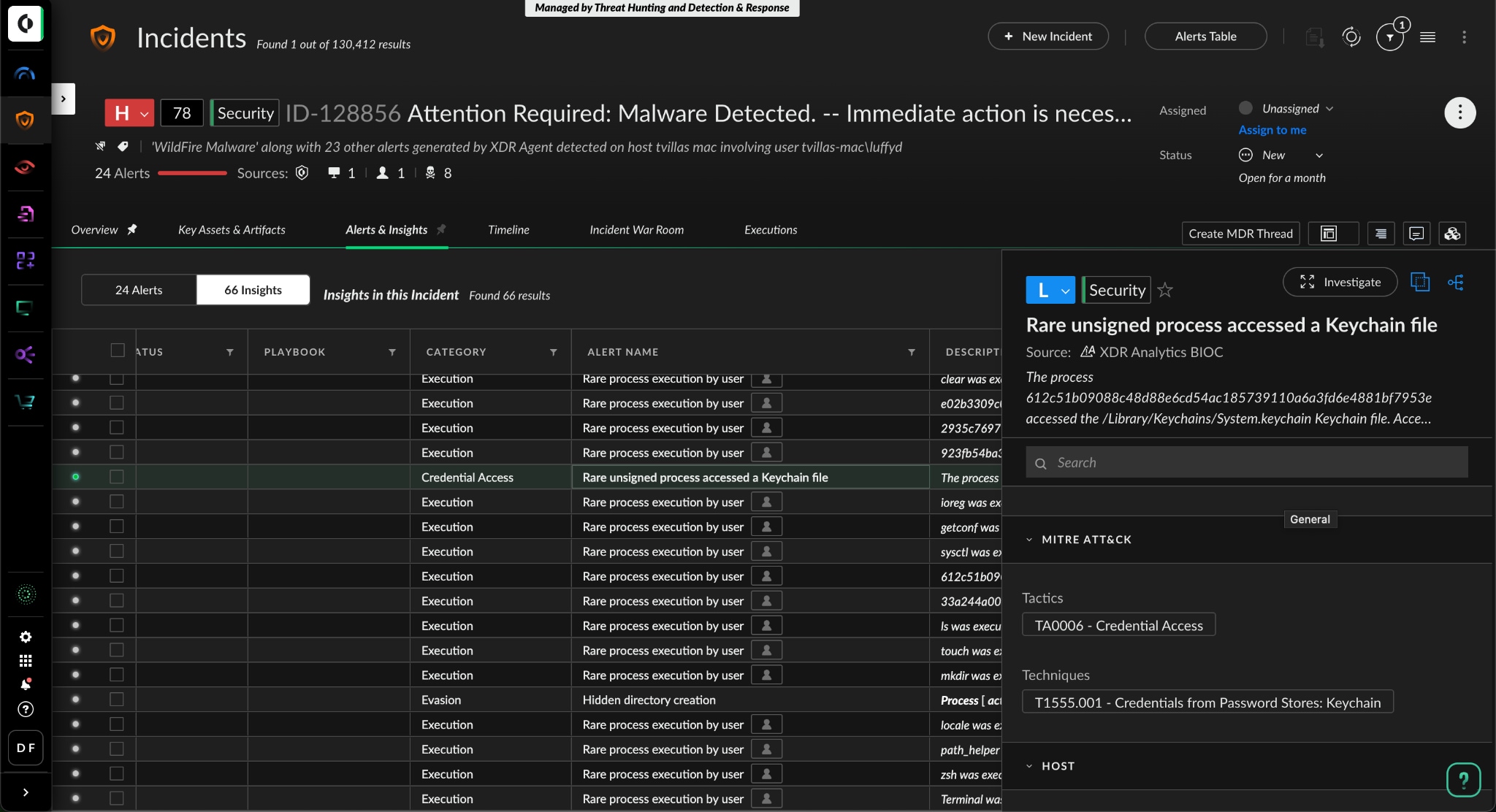
Now, AppleScripts have legitimate uses. Like with Keychain access, we need to look for anomalous or known malicious behaviors to delineate from benign activity. In the following example, an AppleScript process executed with a rare command line: osascript /tmp/down.script. This was a malicious script, and one of many pieces Cortex XDR detected as part of the attack.
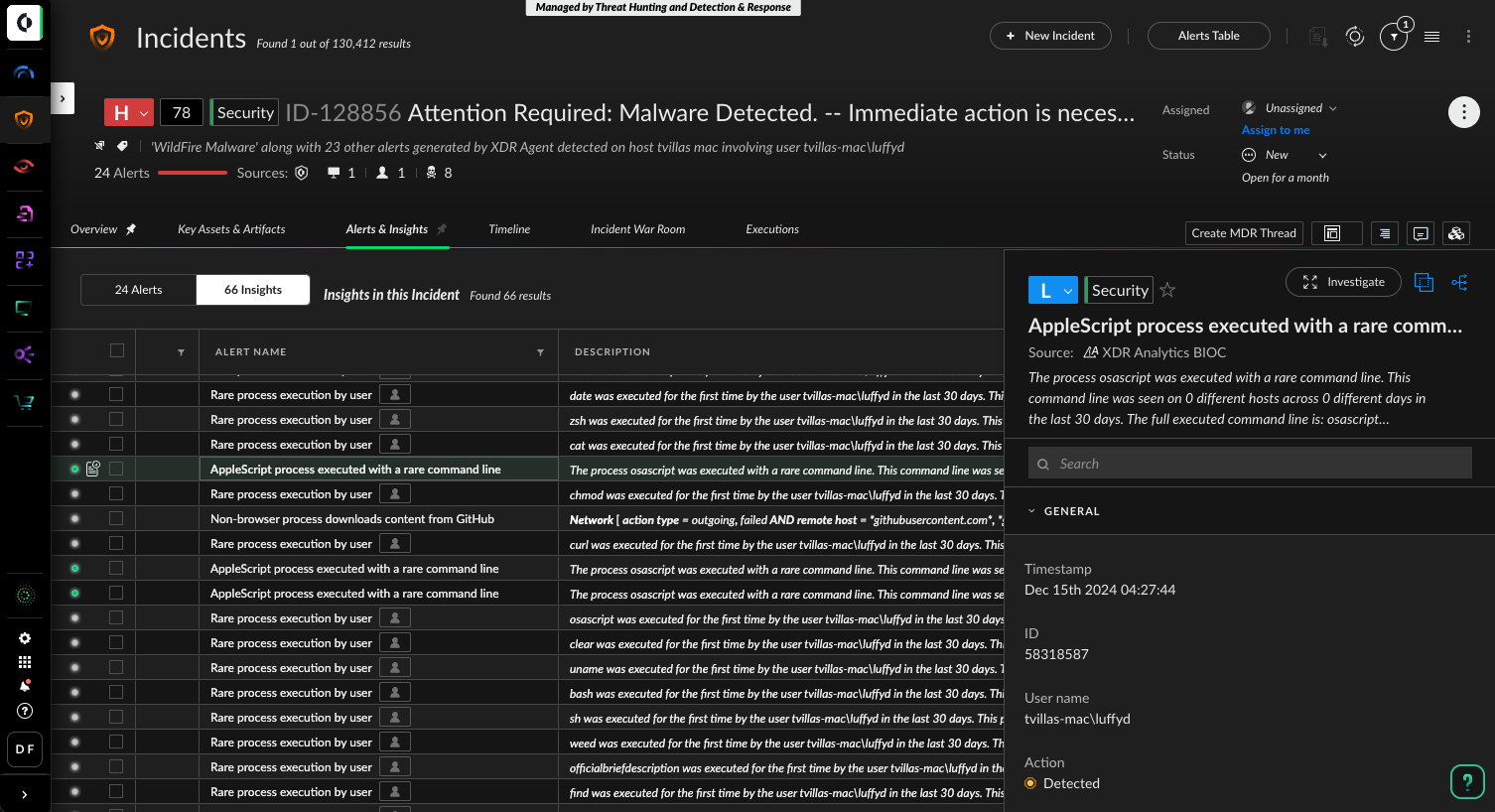
Transitioning from these highlighted AppleScript cases, the Apple Script Process Executed with Rare Command Line and the Unusual Process Accessed Web Browser Credentials and Executed by a Terminal Process playbooks quickly detect key indicators - such as the script’s origin, malicious command line patterns, and potentially compromised credentials - streamline the analysis, investigation and response phases by automatically collecting crucial context, correlating data, and guiding the analyst through the containment and remediation steps if needed.
- AppleScript Process Executed With Rare Command Line
- Unusual process accessed web browser credentials and executed by a terminal process
So what’s next for macOS? Our Unit 42 team has been documenting the latest macOS threat activity, which you can read in the following posts:
- Stealers on the Rise: A Closer Look at a Growing macOS Threat
- Threat Assessment: North Korean Threat Groups
Head over to our February release roundup post for more new features and innovation in Cortex, and reach out to us for a demo anytime.
1https://gs.statcounter.com/os-market-share/desktop/worldwide/2023