Executive Summary
Threat hunting is the niche skill set coveted by all cyber practitioners for its unique capability to find threats before they cause harm to an organization. Thus, its ability to impact organizations is profoundly significant.
The problem: A good threat hunter is difficult to come by. The barrier to entry for acquiring these skills is just as high as the value organizations can gain from them.
The solution: Cortex Copilot closes the skill gap, enabling any organization, regardless of its size or security maturity, to perform advanced threat hunting with ease and confidence.
Cortex Copilot is an advanced security operations assistant designed to transform how organizations approach cybersecurity. It empowers security analysts by providing context and step-by-step guidance throughout their day-to-day work, enabling them to move faster, resolve incidents sooner, and stay ahead of emerging threats. Since the announcement of Cortex Copilot’s general availability, it has been instrumental to numerous organizations in speeding up investigations, and democratizing threat hunting like no other solution before.
If incident response analysts are like first responders to a crime scene, threat hunters are like detectives. They gather clues to find the root cause of the crime when it’s not blatantly present at first glance - asking and answering the bigger questions. A threat hunter’s clues are assets and artifacts. They use these clues to form hypotheses, pivoting from asset to artifact, and artifact to asset - until the larger picture becomes clear revealing the root cause or mastermind of the crime scene. For threat hunters and incident responders alike, assets and artifacts are the categorized IOC’s (indicators of compromise) that are related to the incident - or picked up along the way for threat hunters.
Through Cortex Copilot, threat hunters can gauge assets and artifacts through a whole new view, immediately gaining:
- Enriched insights
- Tailored investigation paths
- Response options AKA remediation suggestions
- Embedded access to the help center documentation
This blog demonstrates Cortex Copilot’s capacity to leverage these operational pillars to turn anyone with a keen mind into an efficient threat hunter by leveling up their abilities.
Use Case Introduction
Imagine yourself on a threat hunting team that received an escalated incident with the objective of finding the root cause. The incident? A malicious resume with a malicious macro was saved to disk and executed on a workstation by a user with low privileges. The analysts already contained the threat, isolated the host, and closed the incident. Now the organization leaves you with the objective of answering:
- How did the malicious resume get into the organization?
Let’s take Cortex Copilot on a ride and democratize this hunt. We’re going to follow Mark - a new threat hunter who got this case as an escalation to find the root cause. Let’s see how he fares wielding Cortex Copilot to his advantage.
The Beginning - A Malicious Hash
Mark, a new threat hunter, begins hunting for larger threats surrounding the incident beginning with the hash that Wildfire flagged as malicious.
He first confirms that the hash has been prevented to mitigate any immediate risks. This sets the scene for the hunt. Mark then leverages Cortex Copilot's capabilities to scope out where else this hash was used in his organization.
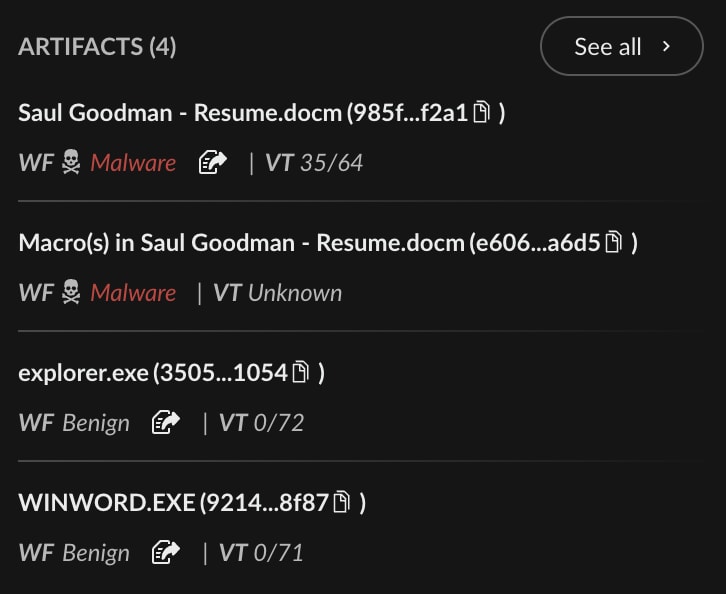
Mark opens the incident’s overview page in XSIAM and sees the malicious hash:
Saul Goodman - Resume.docm
Knowing .docm file extensions are Microsoft Word files with macros in them, or code executables that are often leveraged for attack vectors, Mark begins there.
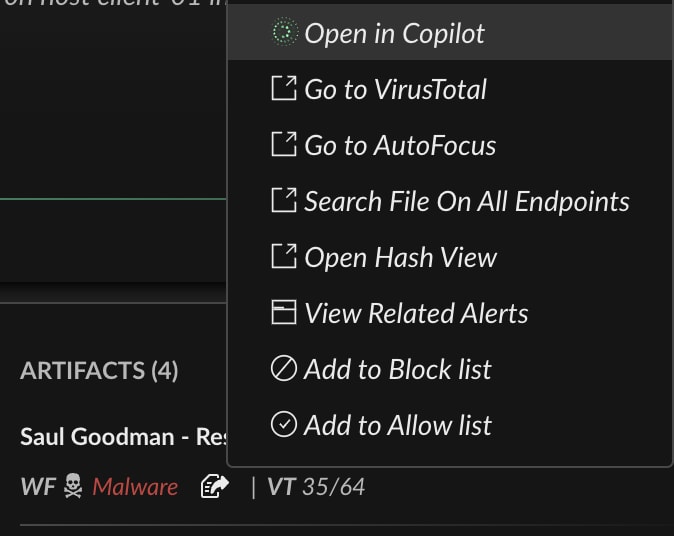
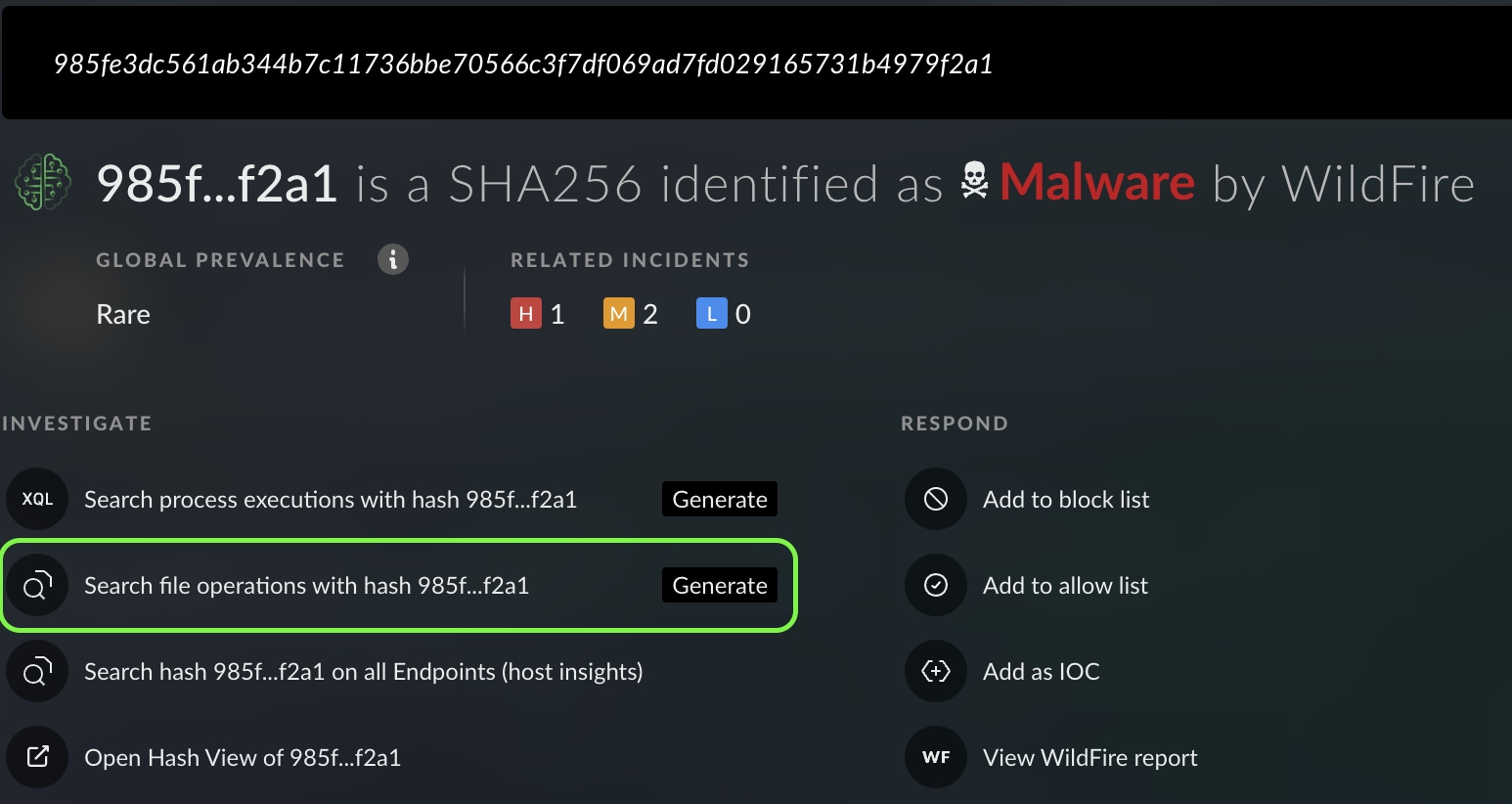
Just by clicking the hash’s menu, Mark opens the artifact in Cortex Copilot.
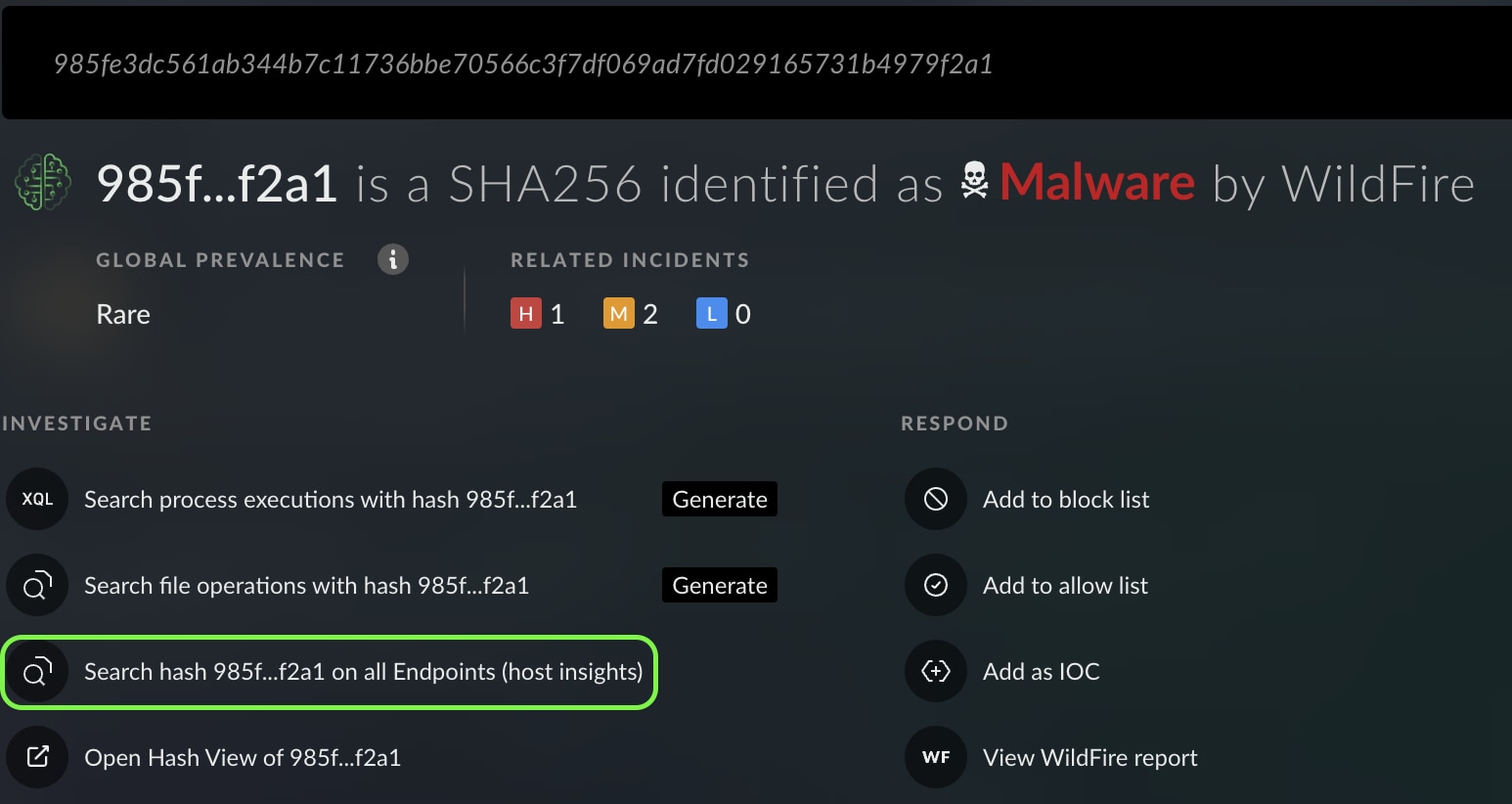
Right away, Mark is gifted with enriched insights and tailored “investigate” and “respond” recommendations through Cortex Copilot - all surrounding this hash!
Mark follows the right “investigate” recommendation and searches for this hash across all endpoints in the organization with just one click.
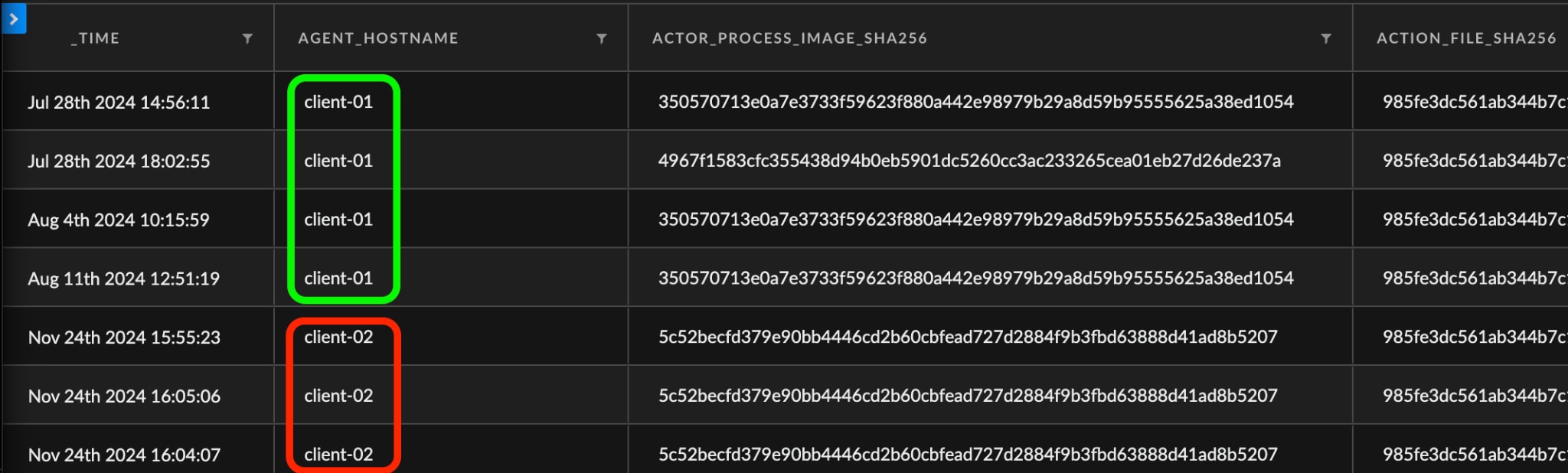
Mark notices that the hash was also seen on host:client-02 and decides to continue exploring the hash entity. This time he aims to see file activities involving this hash, hoping to expand the hunt to other entities and develop a threat hunt hypothesis.
Hypothesis Side Note:
“Threat hunters are often like detectives at the crime scene. Once the SOC analysts closed the incident much like first responders to criminal activities, threat hunters ask the bigger questions and form a hypothesis using clues. This hypothesis helps them get to the bottom of what they’re searching for.”
Digging Deeper - Where Has This Hash Been Used?
Having established that the threat involved other hosts in the organization, and the file hash execution was not prevented, Mark expands the hunt to understand which users were involved with the hash execution on the newly discovered asset: client-02.
Knowing that file activities often contain wide-ranging parameters, such as users and endpoints, he wastes no time and uses Cortex Copilot to see which file activities were observed with this hash. Through this, Mark wants to gain key insights on users and file paths to pivot his threat hunt towards fruitful findings - one step closer to building a hypothesis.
Pivoting Side Note:
“Using the detective analogy, before the hypotheses can be accurately made, there needs to be enough evidence to connect the dots and form a concrete idea.
Pivoting is when one dot leads to another, contextualizing the assets and artifacts into enough material to begin hypothesizing towards a threat hunt victory.”
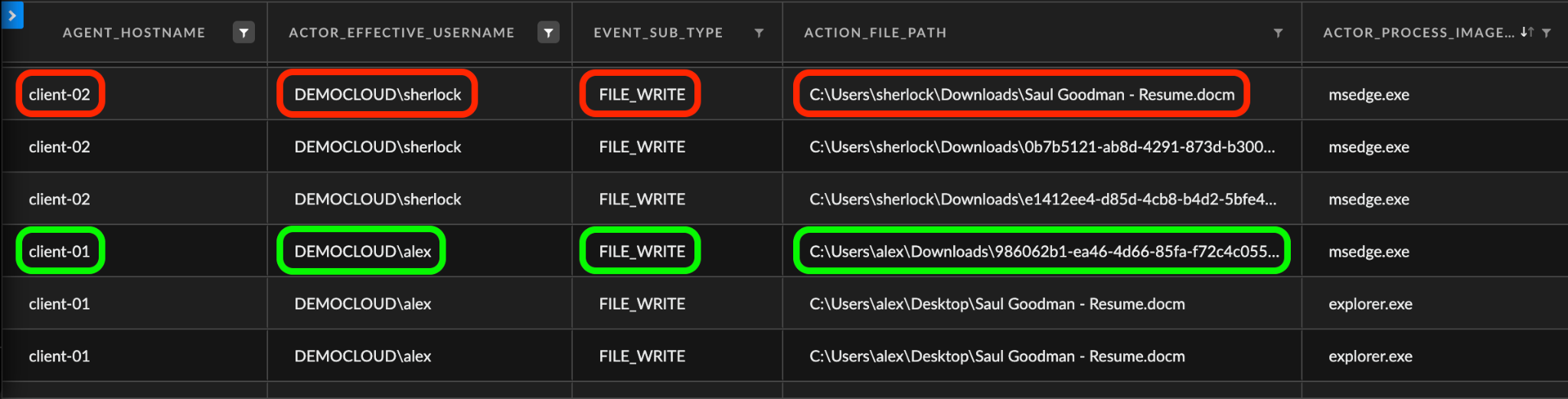
Mark sees that the main users and assets involved in the incident were:
- User: alex
- Host: client-01
He sees user:Sherlock and host:client-02 involved in file-writing activities, downloading the file with the malicious hash from the original incident.
Noting a worthy discovery, Mark now pivots towards this new entity - user:Sherlock
The Revelation - Who is User:Sherlock and How Strong Are Their Privileges?
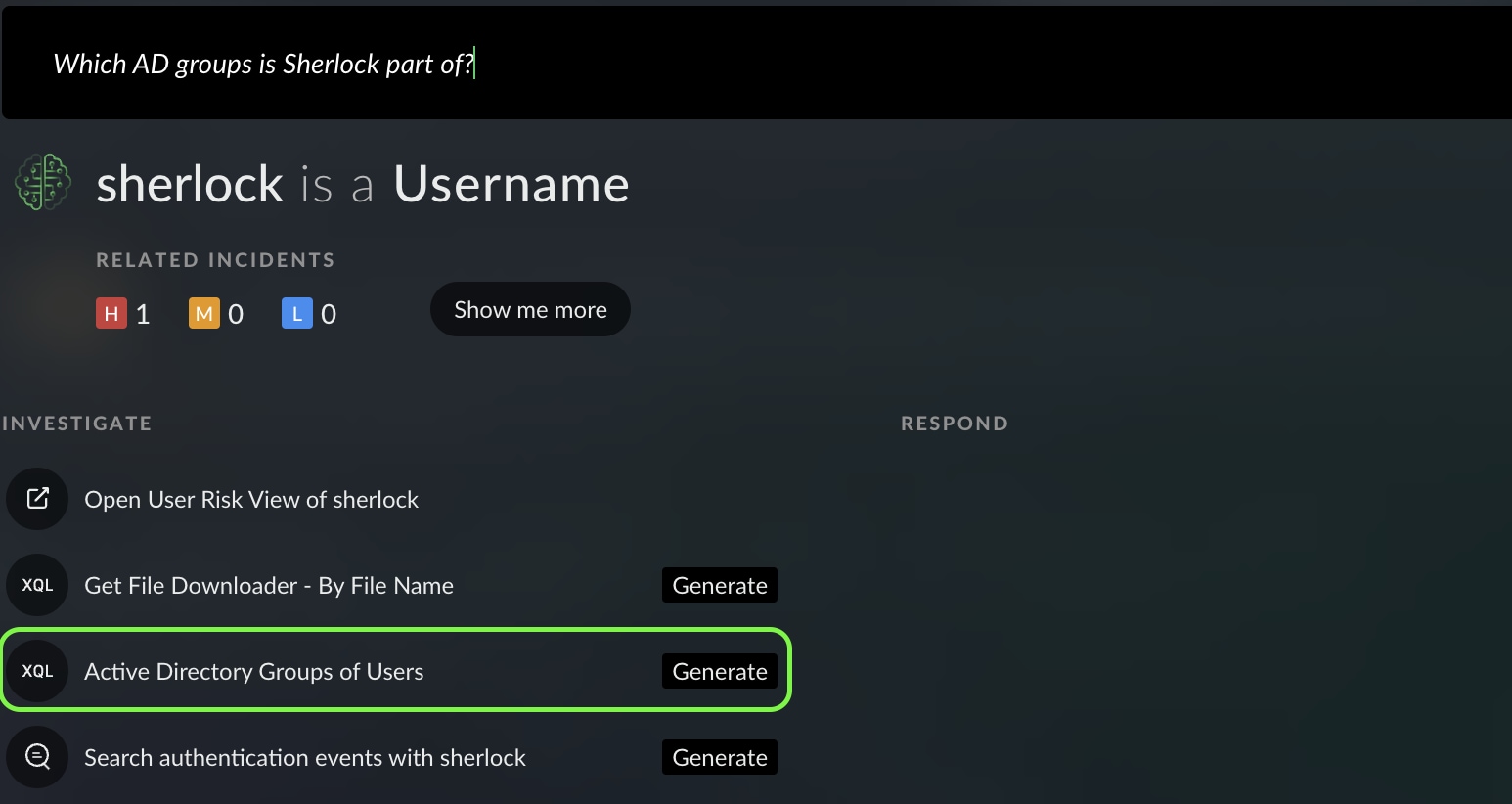
Pivoting towards this new artifact, user:Sherlock, Mark first wants to identify the privileges of the user to know what to expect from them. The higher the privileges, the more endpoint and network execution abilities the user has. As quickly as Mark found Sherlock, he assesses their privileges by asking Cortex Copilot: “Which AD groups is Sherlock part of?”
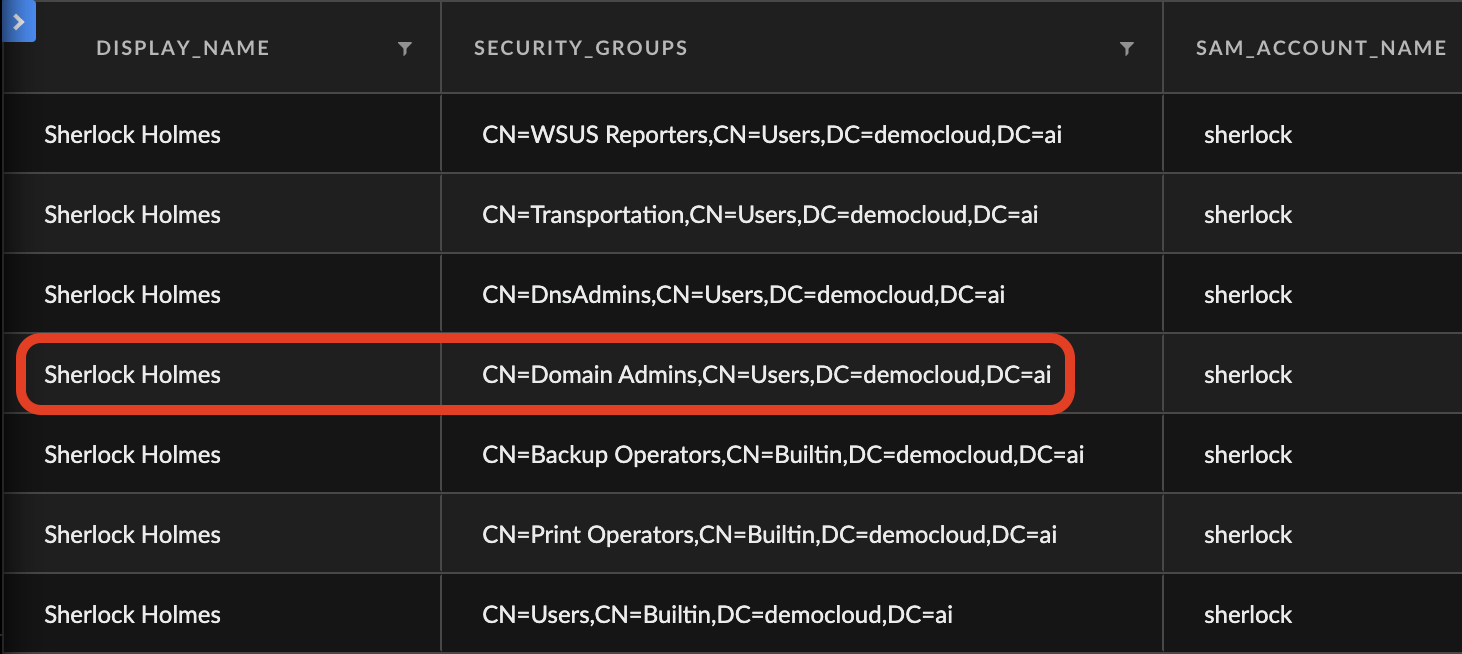
Cortex XQL provides the relevant XQL query and in a matter of seconds, Mark discovers that User:Sherlock is part of domain admins, which allows for special privileges in his organization, including proxy and firewall exceptions. Understanding this, Mark begins to hypothesize that the original malware hash was brought into the organization by User:Sherlock, despite being alerted by User:Alex and having ran on Host:Client-01
Molding his hunt towards this new hypothesis, Mark attempts to prove this by keying in on network metrics. He believes it was Sherlock who brought the file into the organization.
The Hypothesis - Was User:Sherlock Responsible for Bringing in the Malicious Resume?
Mark hopes to prove his hypothesis that the larger threat surrounding this incident is a part of loose networking exception rules in the firewall and proxy for privileged users. He tests this on the latest artifact that he found by pivoting through Cortex Copilot - User:Sherlock.
Mark asks Cortex Copilot which files did User:Sherlock download and right away gets recommended the perfect query for the job.
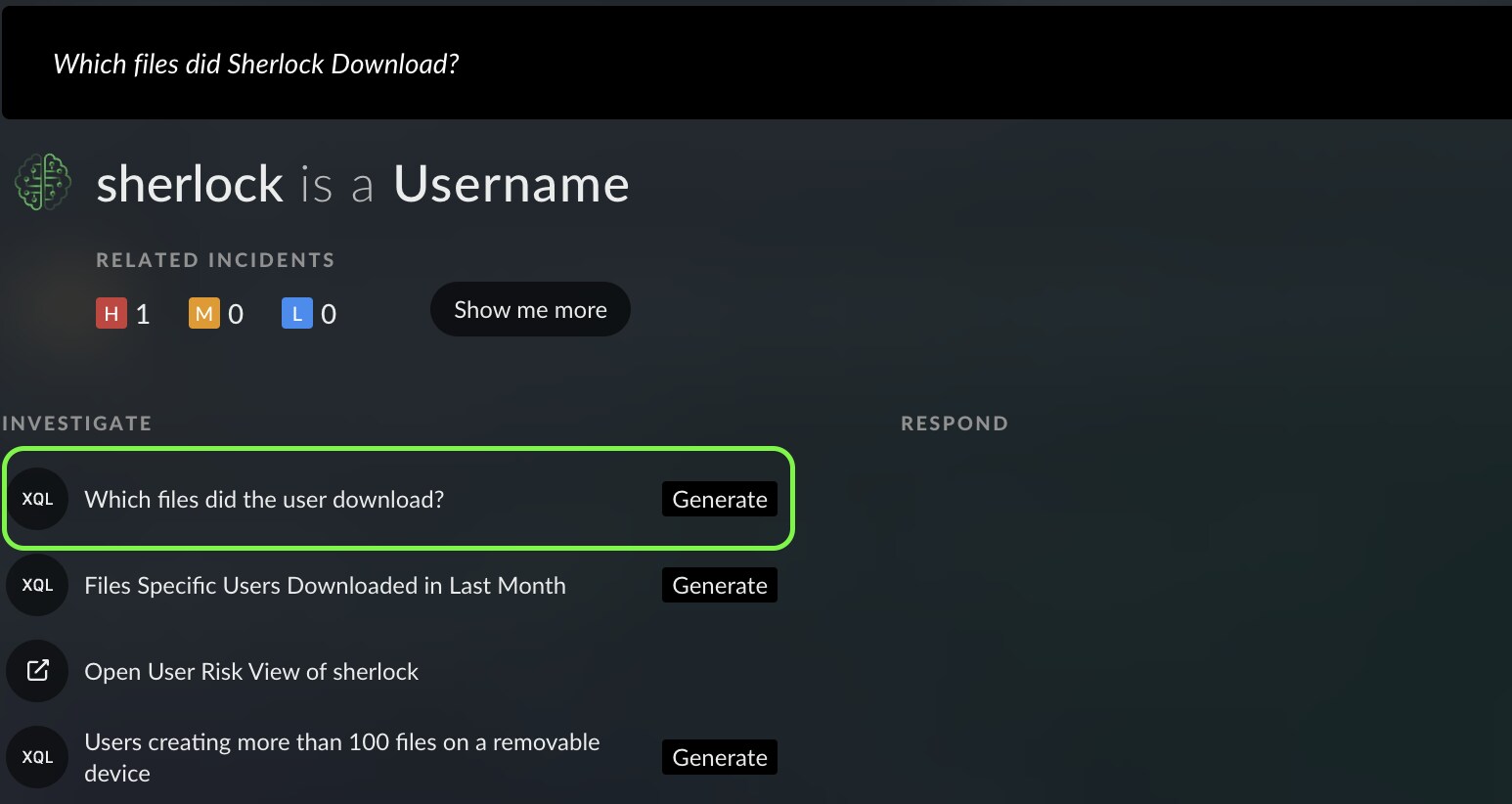
Mark’s hunt has now taken shape and evolved beyond the hash, endpoint, and user scopes - it now involves the networking scope as well.
Through the last Cortex Copilot query, Mark finds a key insight in his evolved threat hunt that adds major weight toward his hypothesis. He sees that User:Sherlock was indeed making suspicious requests to download a malicious Powershell file - inject.ps1.
Mark now makes his second pivot, this time from entity User:Sherlock to entity URI:Github.com to hunt for more details regarding this new URI artifact. So far Mark zoomed through his threat hunt leveraging Cortex Copilot; collecting artifacts, pivoting between them and even forming a hypothesis.
The Finale - Can Mark Leverage Cortex Copilot to Prove the Hypothesis?
Testing his hypothesis, Mark uses one last Copilot query to see which users connected with Domain:Github.com found in the previous step to see if there was malicious download action done beyond inject.ps1.
He hopes to find detailed proof of User:Sherlock's network logs to validate that Sherlock was the original, larger threat that brought the hash malware into the organization. Specifically, Mark believes this was accomplished through exploiting loose FW/proxy policies for privileged AD accounts. Finding evidence of this claim would validate his threat-hunting hypothesis - and put the case to rest.
He asks Cortex Copilot: Who connected to Github.com?
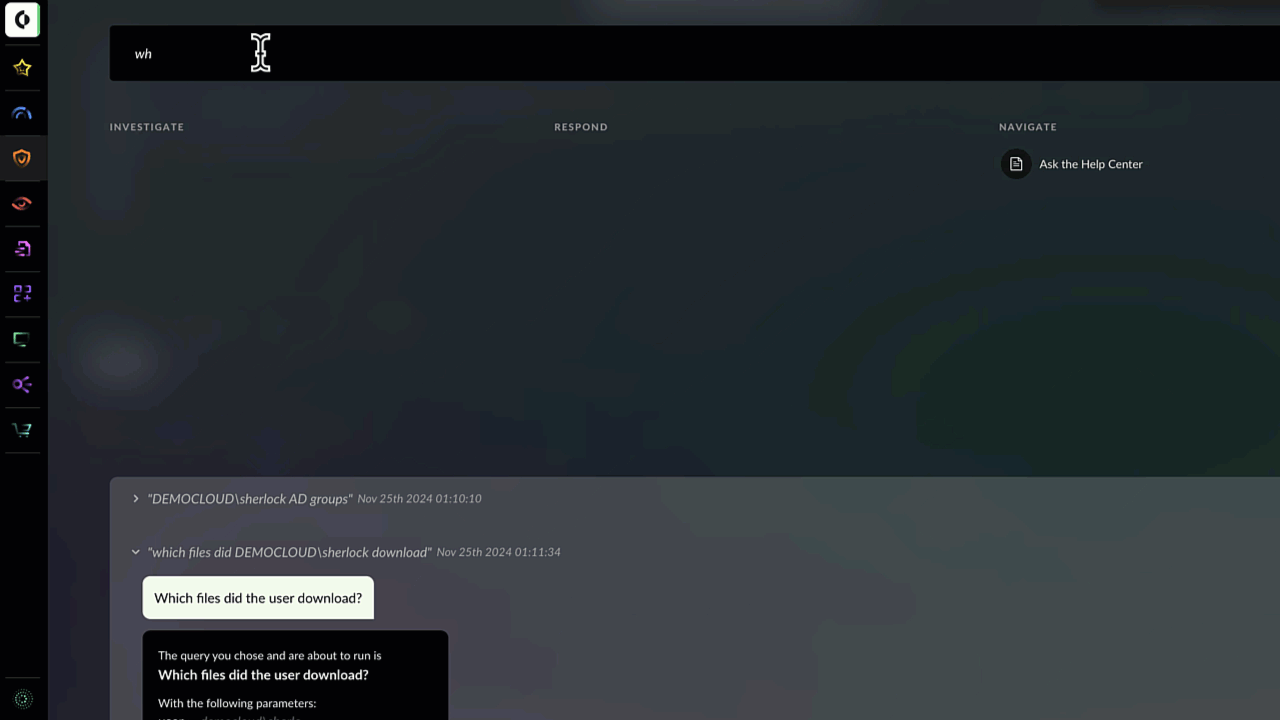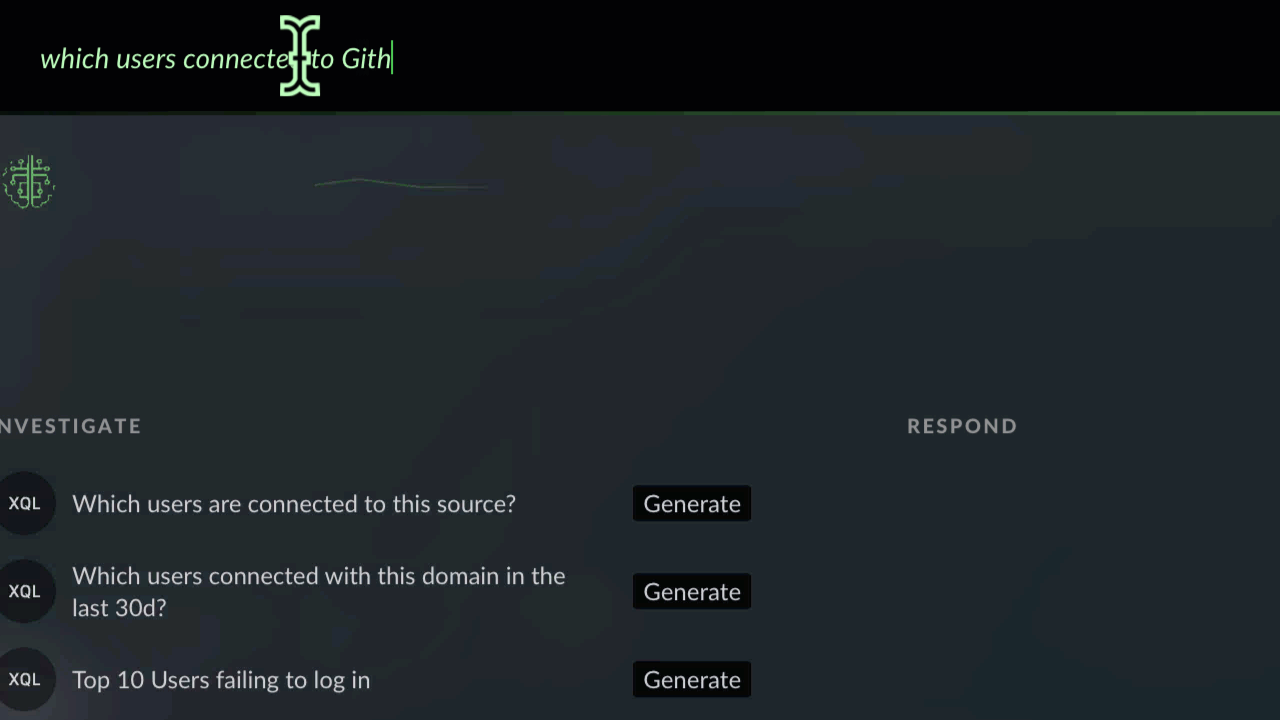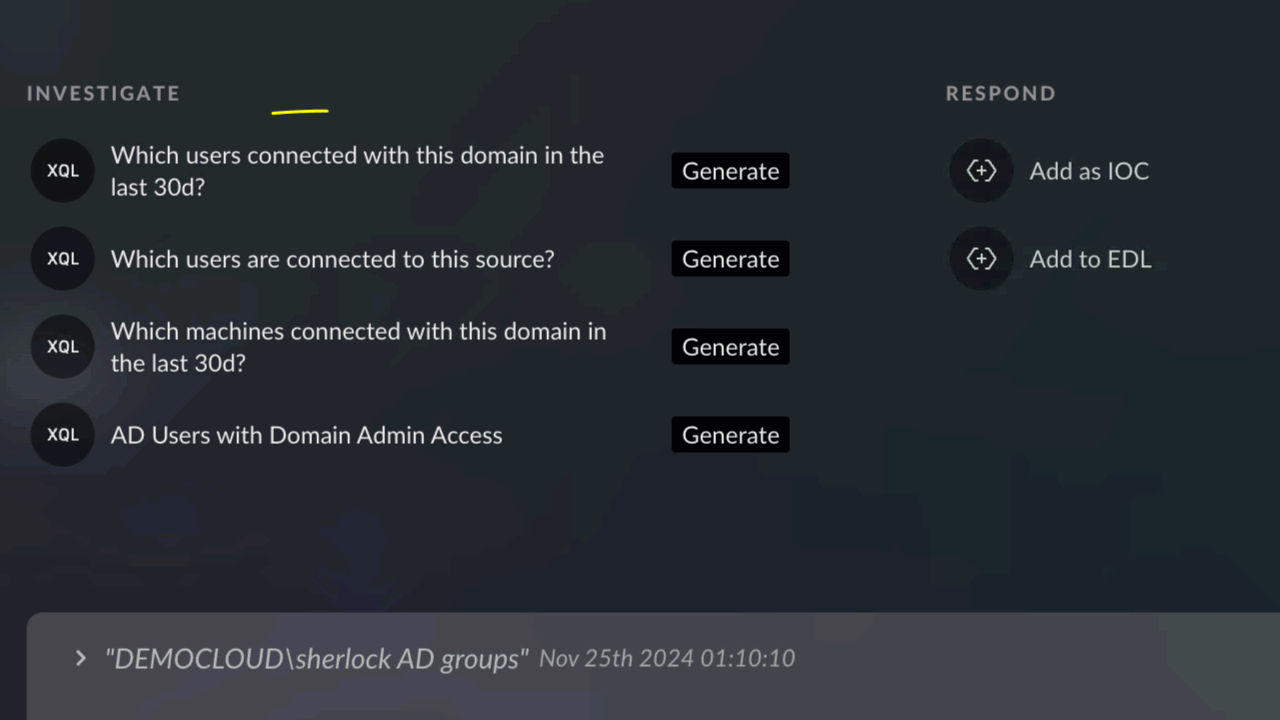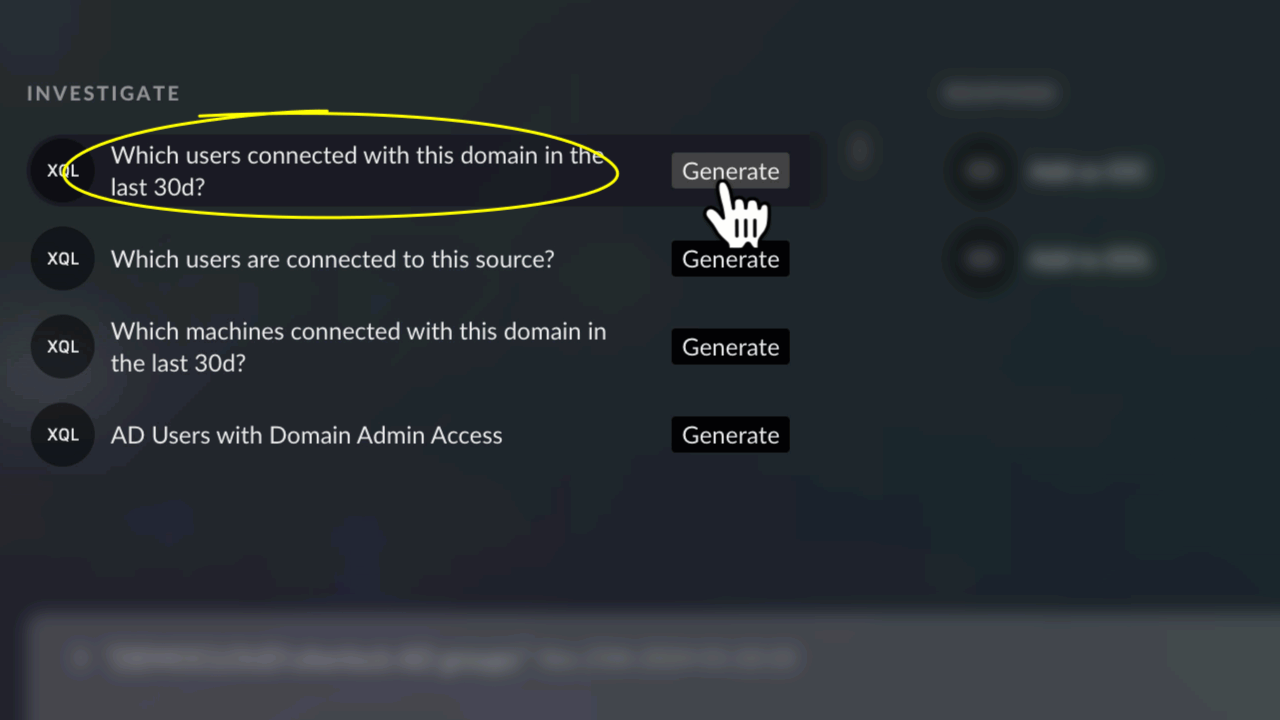
Within seconds, the “investigate” option recommended by Cortex Copilot reveals a list of all users making connections to Github.com.
Unsurprisingly, he sees Sherlock again.
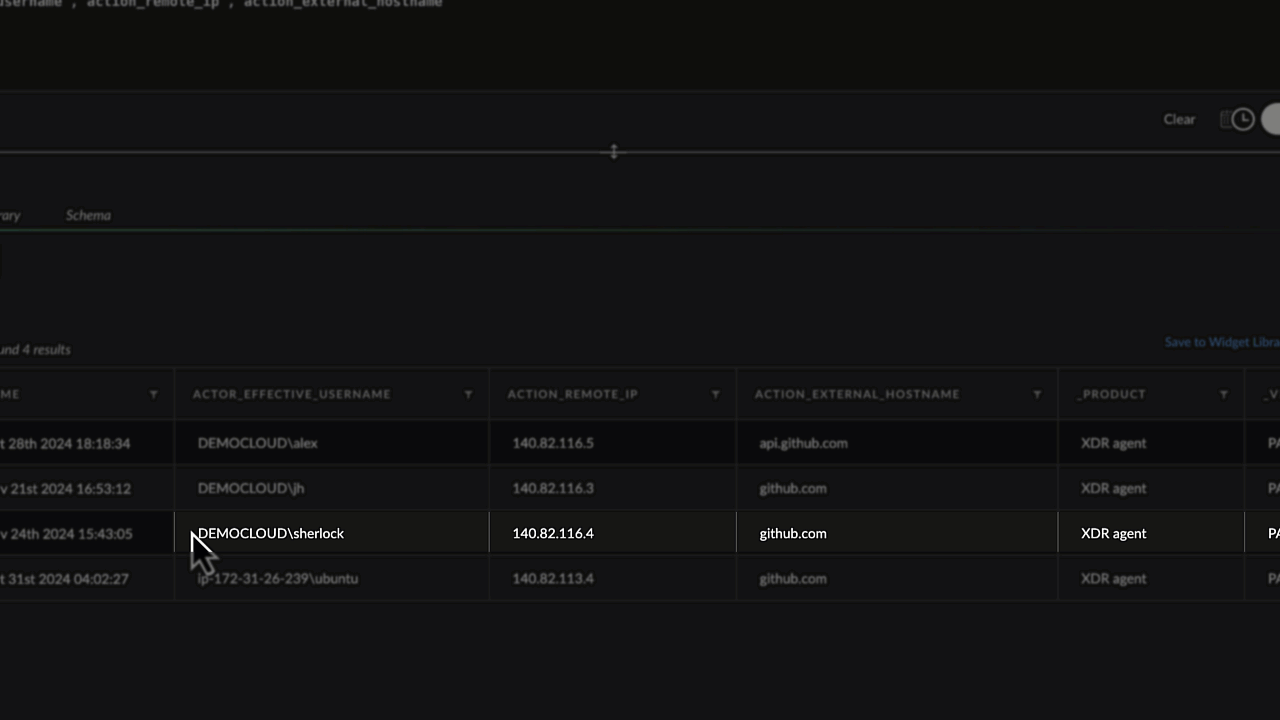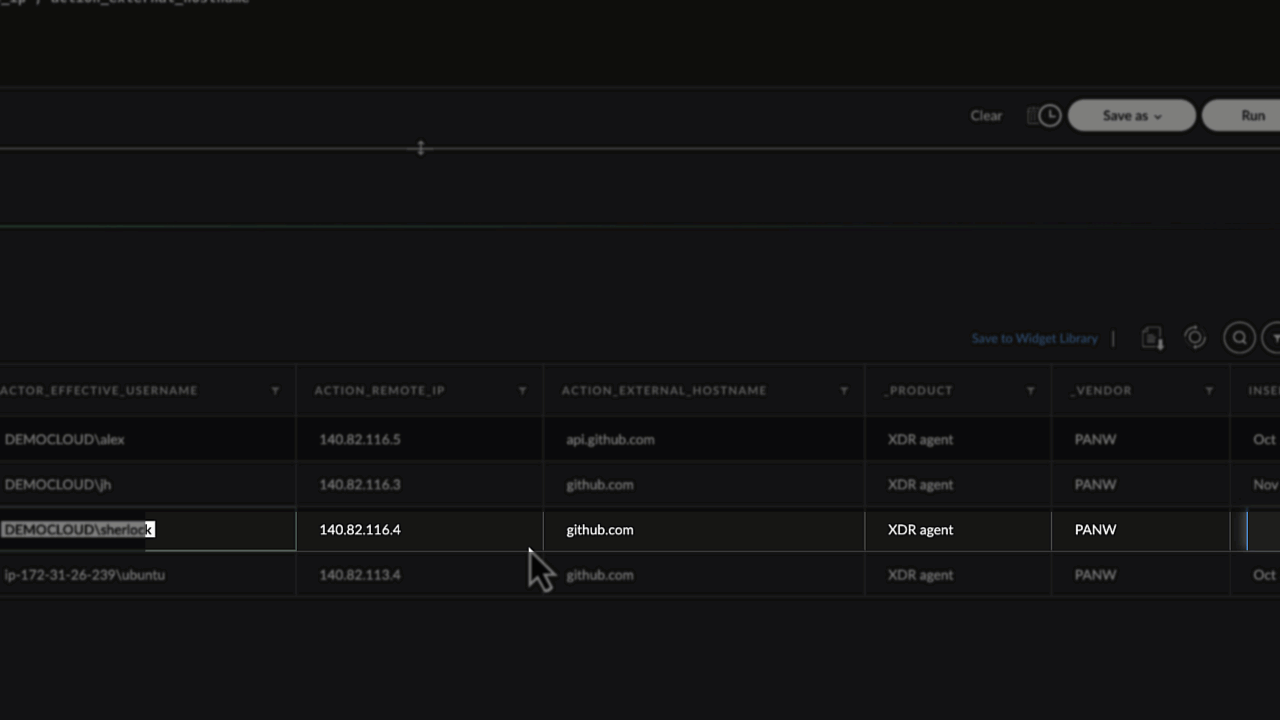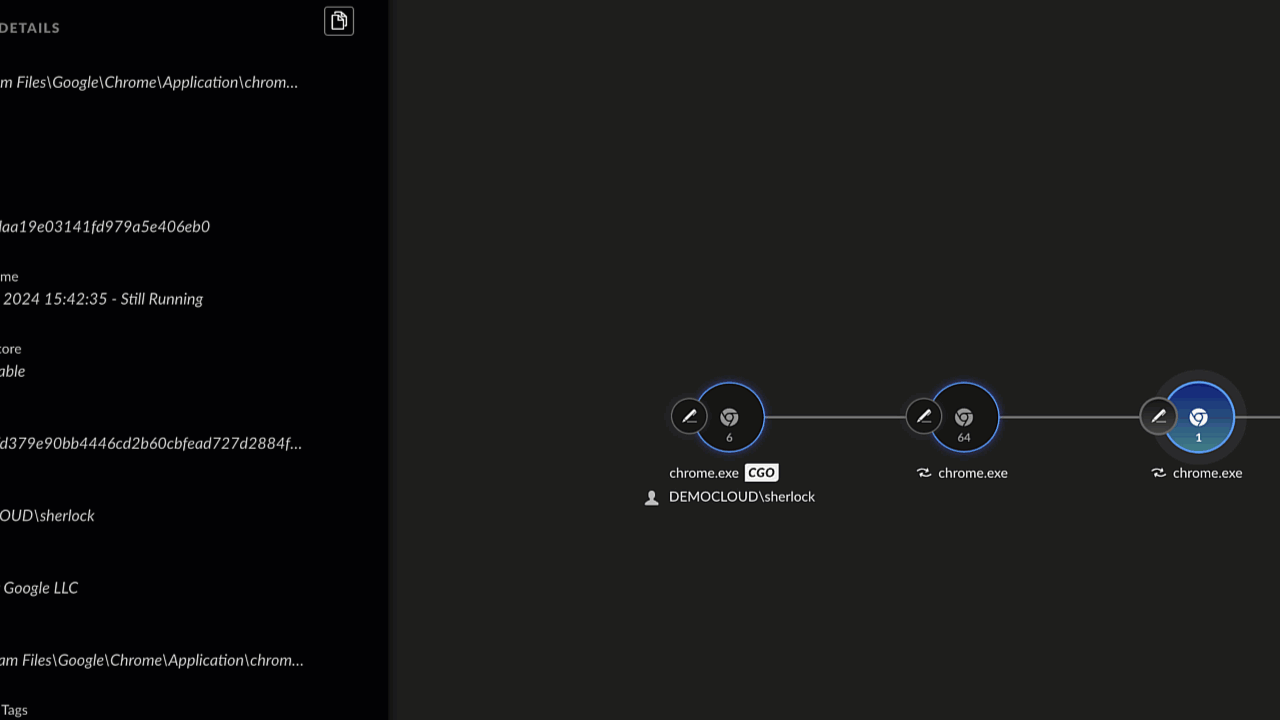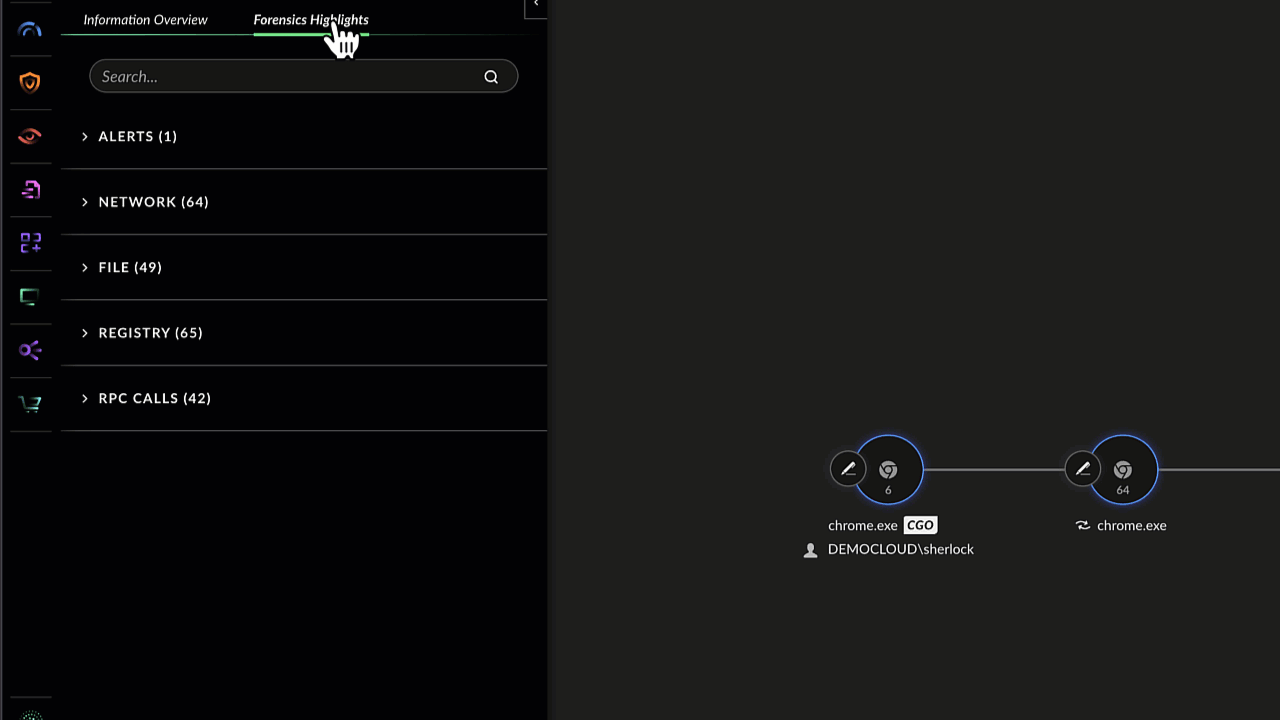
A key benefit of leveraging Cortex Copilot’s “tailored investigate options” is the visibility and explainability of the enriched causality cards they provide.
Causality Card Side Note:
“Cortex provides causality cards for events, showcasing process trees to enrich analysts and threat hunters with cause-effect relationships at process level granularity. This provides maximum visibility and explainability as users gain an information overview and forensics highlights of every individual process node.”
Having already linked inject.ps1 to User:Sherlock, Mark wishes to prove this user brought Saul Goodman - Resume.docm into the organization. After entering the causality card and pivoting to forensics highlights, Mark enters “C:\users\Sherlock\Downloads” and instantly sees User:Sherlock downloaded both:
He further hovers over the file origin of the malicious resume and gains clarity in regards to where it came from - a Github repository.
Confirming his hypothesis, Mark finds actionable proof that User:Sherlock, being a domain admin, was the culprit that brought this malicious hash into his organization.
The Remediation - Mark Finds the Root Cause and Hardens Policies as a Solution
Summary
Beginning from the initial artifact of the closed incident, Mark expanded the scope of the hunt by searching for file activities of the hash across the organization. He did this in an effort to gain more and pivot beyond the details he currently had, connecting relevant dots to form a hypothesis.
Finding a new user, Sherlock, after querying file activities, Mark pivoted towards Sherlock and found their privileges were very high - domain admin. From here, Mark began to form his hypothesis that Sherlock brought in the malware by exploiting loose FW/proxy policies via his privileged AD account.
Hunting for more clues regarding Sherlock’s network activity, Mark found connections made to Github and further pivoted to URI:Github.com, finally confirming his hunting hypothesis; confirming the metrics and ending the hunt!
Conclusion
Mark confirms his hypothesis that the WildFire malware used by user:alex on host:client-01 for the closed incident was brought into the organization by User:Sherlock via domain admin privileges that were bolstered by loose exception rules in the organization's firewall and proxy policies.
Mark brings these threat hunting findings to the SOC team and upper management. Together, they begin restructuring network policies surrounding firewall and proxy rules and enforce a rigid allow-list of approved domains for different user groups, taking away the excessive request privileges for certain user groups.
Additionally, a deeper examination of endpoint prevention policy groups takes place to eradicate lenient endpoint policies, mitigating runtime risks in the future.
Sherlock gets disabled, and a new MFA policy gets initiated for accessing domain admin accounts by approved users.
Through using Cortex Copilot, Mark was able to navigate his organization’s cyber terrain with ease and speed to find the root cause of the incident and contribute to his organization's policy hardening, completing the remediation for the threat hunt.
To learn more about how Cortex Copilot can help you on your threat hunting journey or discover other use cases, check out our Cortex Copilot page.