
Having spent the last few days pretty immersed in the world of Conti, I detonated some samples that I have been assured are part of the recent attacks that have hit the press, the fact that I was not under attack, meant that the full chain and the extent cannot be realised in my little lab on the fringe, I guess the cyber gang are not too interested in taking my little home lab down and staging a ransom. Before I get into the tech, let's take a moment to discuss Ransomware and a bit of history; and so not to keep everybody waiting I found that prevention is possible.
Cybercriminals Are Making, and Demanding, More Money Than Ever. The average ransom paid for organizations increased from US$115,123 in 2019 to $312,493 in 2020, a 171% year-over-year increase. Additionally, the highest ransom paid by an organization doubled from 2019 to 2020, from $5 million to $10 million. From 2015 to 2019, the highest ransomware demand was $15 million. In 2020, the highest ransomware demand grew to $30 million. Of note, Maze ransom demands in 2020 averaged $4.8 million, a significant increase compared to the average of $847,344 across all ransomware families in 2020.
Cybercriminals know they can make money with ransomware and are continuing to get bolder with their demands.
Healthcare Organizations in the Crosshairs
The world changed with COVID-19, and ransomware operators took advantage of the pandemic to prey on organizations particularly the healthcare sector, which was the most targeted vertical for ransomware in 2020. Ransomware operators were brazen in their attacks in an attempt to make as much money as possible, knowing that healthcare organisations which needed to continue operating to treat COVID-19 patients and help save lives couldn't afford to have their systems locked out and would be more likely to pay a ransom.
Ryuk Ransomware Stood Out From the Pack
In October 2020, a joint cybersecurity advisory was issued by the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS), warning healthcare organizations against Ryuk attacks.
The Rise of Double Extortion
A common ransomware attack consists of the ransomware operator encrypting data and forcing the victim to pay a ransom to unlock it. In a case of double extortion, ransomware operators encrypt and steal data to further coerce a victim into paying a ransom. If the victim doesn’t pay the ransom, the ransomware operators then leak the data on a leak site or dark web domain, with the majority of leak sites hosted on the dark web. These hosting locations are created and managed by the ransomware operators. At least 16 different ransomware variants are now threatening to expose data or utilizing leak sites, and more variants will likely continue this trend.
The ransomware family that leveraged this tactic the most was NetWalker. From January 2020 to January 2021, NetWalker leaked data from 113 victim organizations globally, far surpassing other ransomware families. RagnarLocker was second, leaking data from 26 victims globally. It’s worth noting that the US Department of Justice announced in January 2021 it had coordinated international law enforcement action to disrupt the NetWalker ransomware gang. The dark web domain managed by the NetWalker operators, which hosted leaked data is no longer accessible.
Since August 2018, numerous industries, including government, healthcare, energy, and high tech, have been targeted by Ryuk ransomware. Throughout 2020, we saw a significant increase in Ryuk ransomware attacks targeting education, healthcare, and government/military organizations primarily within the US, but also in the UK and Canada.
A heavy focus was put on hospital systems, likely due to the necessity for uptime, as these systems were overwhelmed with handling the ongoing COVID-19 pandemic. We observed initial Ryuk ransom requests ranging from US$600,000 to $10 million across multiple industries. Most often, these payments were communicated using a ProtonMail account and requested in the form of bitcoin.
To gain access to a target system, Ryuk has successfully compromised hosts through malicious macros in phishing documents, utilized commodity malware such as Trickbot, BazaLoader, and Emotet, and used exploit techniques that allow malicious software to evade endpoint security products. In some cases, Ryuk was installed weeks or even months after backdoor malware, such as Trickbot, was observed on that victim’s host. In at least one instance, it was deployed after business hours using backup service accounts.
Once they gain access to a system, Ryuk operators will leverage RDP connections to deploy the Ryuk payload or move laterally through the network. During active infection, Ryuk will close and encrypt all files, including their own malicious document that resulted in the initial download. A file named “RyukReadMe” is placed onto the system, and tools such as PowerShell and Windows Management Instrumentation (WMI) are used to enumerate the network while evading detection. Ryuk ransomware is believed to be associated with the threat group Wizard Spider.
Credit to John Davis (Retired US Army Major General, VP of Public Sector at Palo Alto Networks) and Unit42 and their 2021 Ransomware Threat Report for the above introduction and statistics.
Other advisors and articles of interest that have interested me:
- Advisory October 28, 2020 https://us-cert.cisa.gov/ncas/alerts/aa20-302a
- Advisory Aug 22, 2018 https://digital.nhs.uk/cyber-alerts/2018/cc-2627
- Advisory Nov 06, 2020 https://www.computerweekly.com/news/252491686/NHS warned-over-Ryuk-spreading-through-Trickbot-replacements
- Article Oct 29 2020 https://www.wired.com/story/ransomware-hospitals-ryuk-trickbot/
- Wizard Spider https://attack.mitre.org/groups/G0102/
- How conti works Jan 14 2021 https://www.bankinfosecurity.com/how-contiransomware-works-a-15763
Conti is a Targeted version of Ryuk, which comes from Trickbot and Emotet which we've been monitoring for some time. Unit 42 lays out the preventions quite well here and align them to MITRE:
- ryuk https://unit42.paloaltonetworks.com/atoms/ryuk-ransomware/
- ryuk https://unit42.paloaltonetworks.com/ryuk-ransomware/
- emotet https://unit42.paloaltonetworks.com/emotet-command-and-control/
- trickbot https://unit42.paloaltonetworks.com/atoms/trickbot/
Testing the Most Interesting Variant - Conti Payload
My environment consists of a Windows 10 Pro (Version 20H2) OS Build 19042.985, (updated May 16th 2021) in an isolated network behind a firewall.
The Windows Endpoint is running Cortex XDR from Palo Alto Networks and is isolated in a networks behind a Palo Alto Networks Firewall (the policy on the firewall is report only, so as not to prevent the infection).
The variants I tested were downloaded from Virustotal:
- d21c71a090cd6759efc1f258b4d087e82c281ce65a9d76f20a24857901e694fc
- 234e4df3d9304136224f2a6c37cb6b5f6d8336c4e105afce857832015e97f27a
- 1429190cf3b36dae7e439b4314fe160e435ea42c0f3e6f45f8a0a33e1e12258f
- 1429190cf3b36dae7e439b4314fe160e435ea42c0f3e6f45f8a0a33e1e12258f
- a390038e21cbf92c36987041511dcd8dcfe836ebbabee733349e0b17af9ad4eb
The decryption policy on the firewall ensured that Virustotal was not decrypted and the above were downloaded in an encrypted zip format
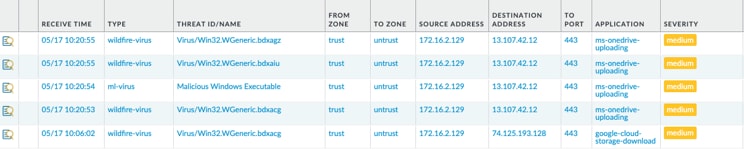
I then extracted the zips and renamed those downloaded files to .exe and uploaded them to OneDrive (which is decrypted) - to test firewall detection
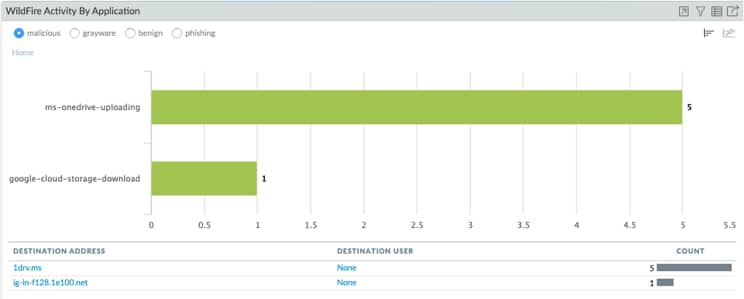
Good news, I saw them being detected as malicious by Wildfire.
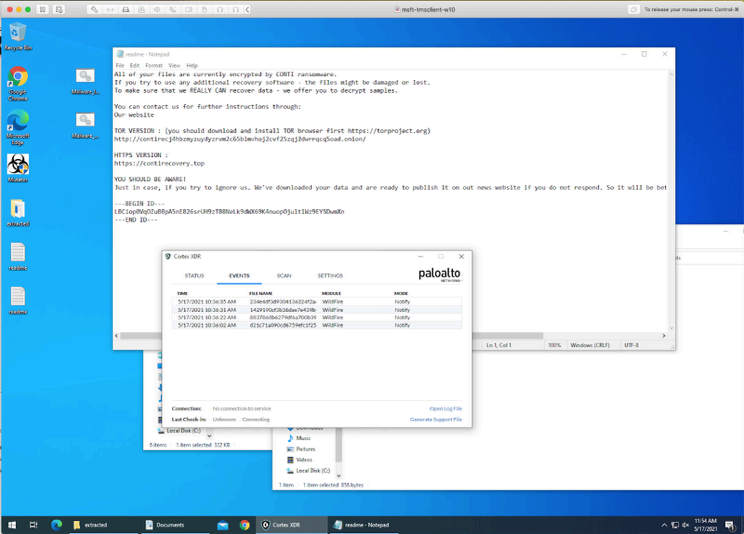
First things first, let's make sure that the malware actually is the malware by detonating it on the endpoint - Successful Conti Infection with Monitor only Policy - I say successful but nothing was encrypted - however I did see the readme file placed in a number of key locations.
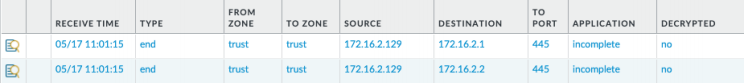
After the host is infected I saw it start to beacon out on port 445 which is expected given the nature of this malware, of note this firewall is perimeter only.
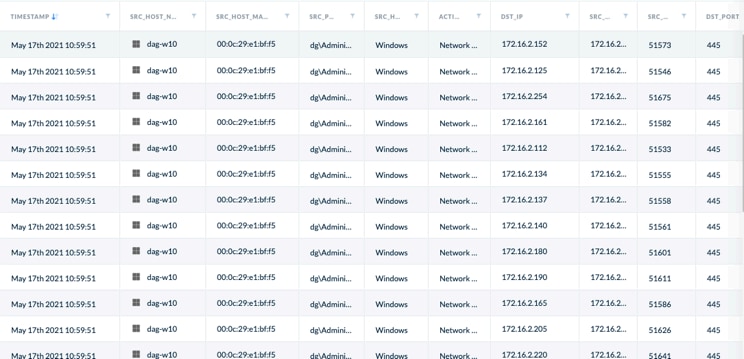
Above further beaconing can be see from the XDR console, we can see the extent of the attempt at a lateral movement, whereby the malware is attempting to find adjacent hosts on port 445.
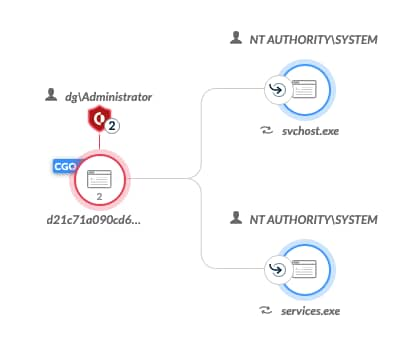
Above you can see that "d21c*.exe" is the CGO (Causality Group Owner), really that is expected seeing as I simply "right-clicked&run-as-admin" the file, it has spawned two subordinates, also of note that shield icon highlights that execution could have been prevented (with the default policy) by 2 separate distinct modules (Wildfire & Anti Ransomware Protection). In my opinion in the actual case of the attack we would expect to see a differing CGO, as this (d21c*.exe) would be the payload being delivered by another process, as such during such an actual attack "d21c*.exe" would not detonate it would beprevented by BTP or similar.
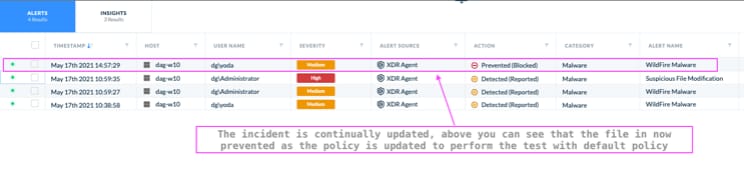
Below you see the one of the prevention events associated with the highlighted alert above.
Prevention is possible.
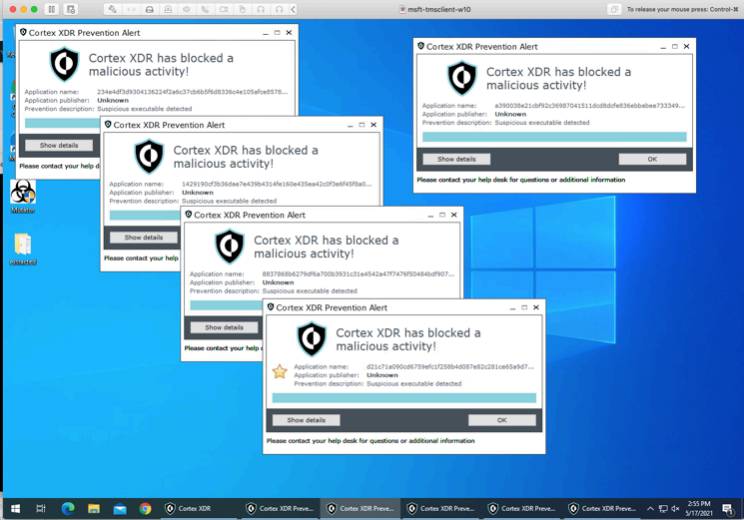
By reverting and applying the Default policy from XDR, Prevention is possible - the intelligence highlighted here is in the product and does not come from any change to the default out of the box policy. In fact the only changes made throughout the test is to turn prevention modules to report only and to turn on the XDR telemetry features.
While most of this attack will feed into the next round of MITRE ATT&CK evaluations, the current testing results from the latest round can be found here MITRE Round 3