Introduction
Hidden user accounts can be a significant security risk, as attackers often create them to establish persistence within an environment. These accounts may be used to escalate privileges, execute malicious activities, or evade detection. To combat this threat, Cortex XSIAM’s Response and Remediation Pack includes the Suspicious Hidden User Created playbook, designed to identify, investigate, and remediate unauthorized hidden user account creation.
Threat Overview
The creation of hidden user accounts is a known tactic used by adversaries to maintain access to an organization’s infrastructure. Such accounts may be configured with privileges that allow them to bypass security policies, making them difficult to detect through conventional monitoring tools.
This playbook responds to the following alert:
- Suspicious Hidden User Created
Purpose of the Playbook
The Suspicious Hidden User Created playbook is designed to streamline incident response for potential unauthorized account creation by:
- Retrieving event details related to the created user.
- Determining whether the user is local or domain-based.
- Fetching Active Directory (AD) attributes and checking password expiration state for domain users.
- Running PowerShell commands to verify the local user’s password expiration state.
- Evaluating the risk level of the affected host using advanced AI logic.
- Identifying related alerts involving suspicious script execution.
- Providing remediation recommendations, including disabling the hidden user and terminating associated malicious processes.
Stages of the Playbook
Triage
- The playbook retrieves key information about the created user account from event logs.
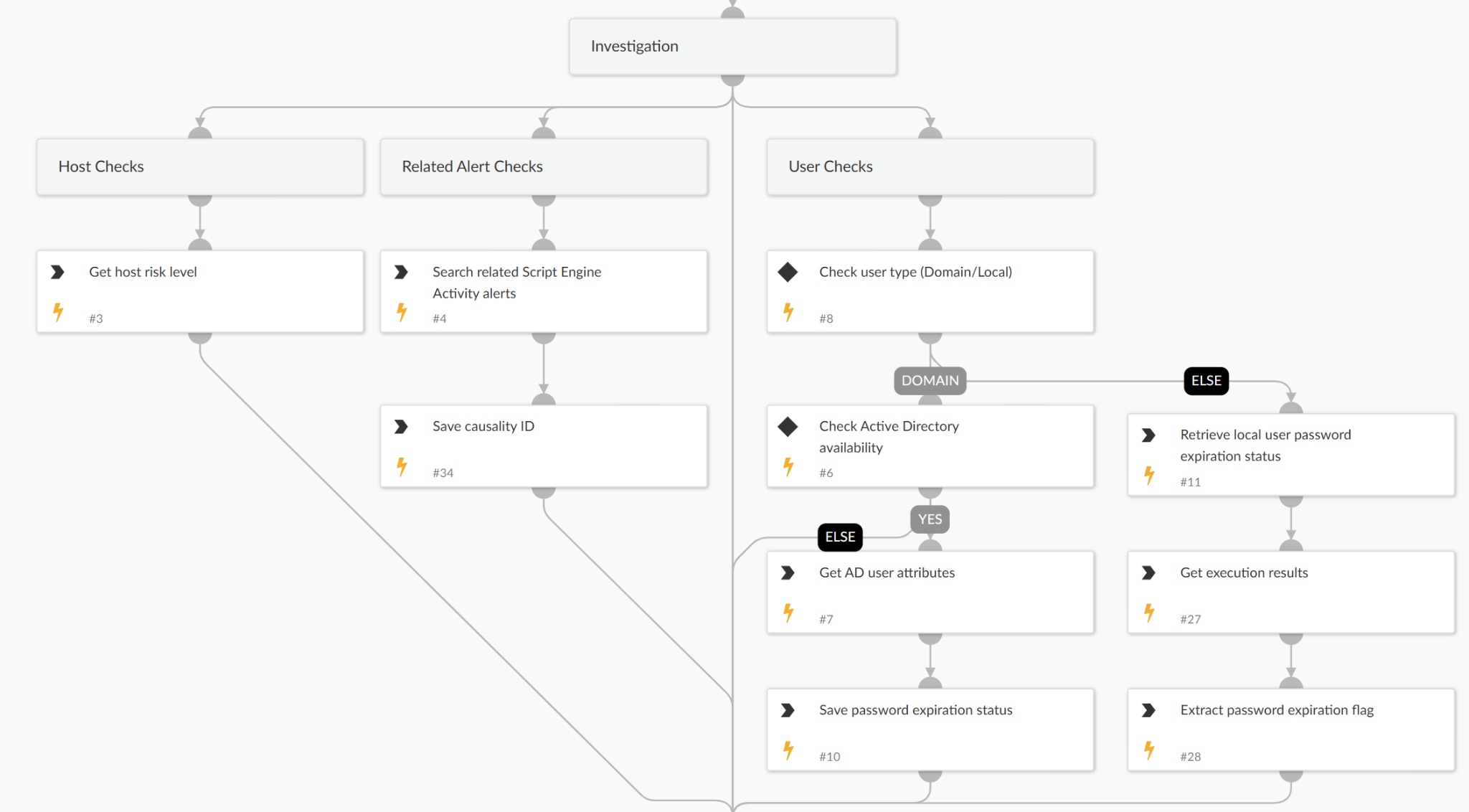
Investigation
- User Type Identification: Determines whether the suspicious account is a domain user or a local user.
- For Domain Users:
- Retrieves Active Directory attributes, including password expiration status.
- For Local Users:
- Executes a PowerShell command to check if the password expiration policy is configured.
- Host Risk Assessment: Analyzes the risk level of the machine where the user was created using advanced AI logic.
- Related Alert Correlation: Searches for additional indicators of compromise, such as script execution activities that could signal malicious behavior.
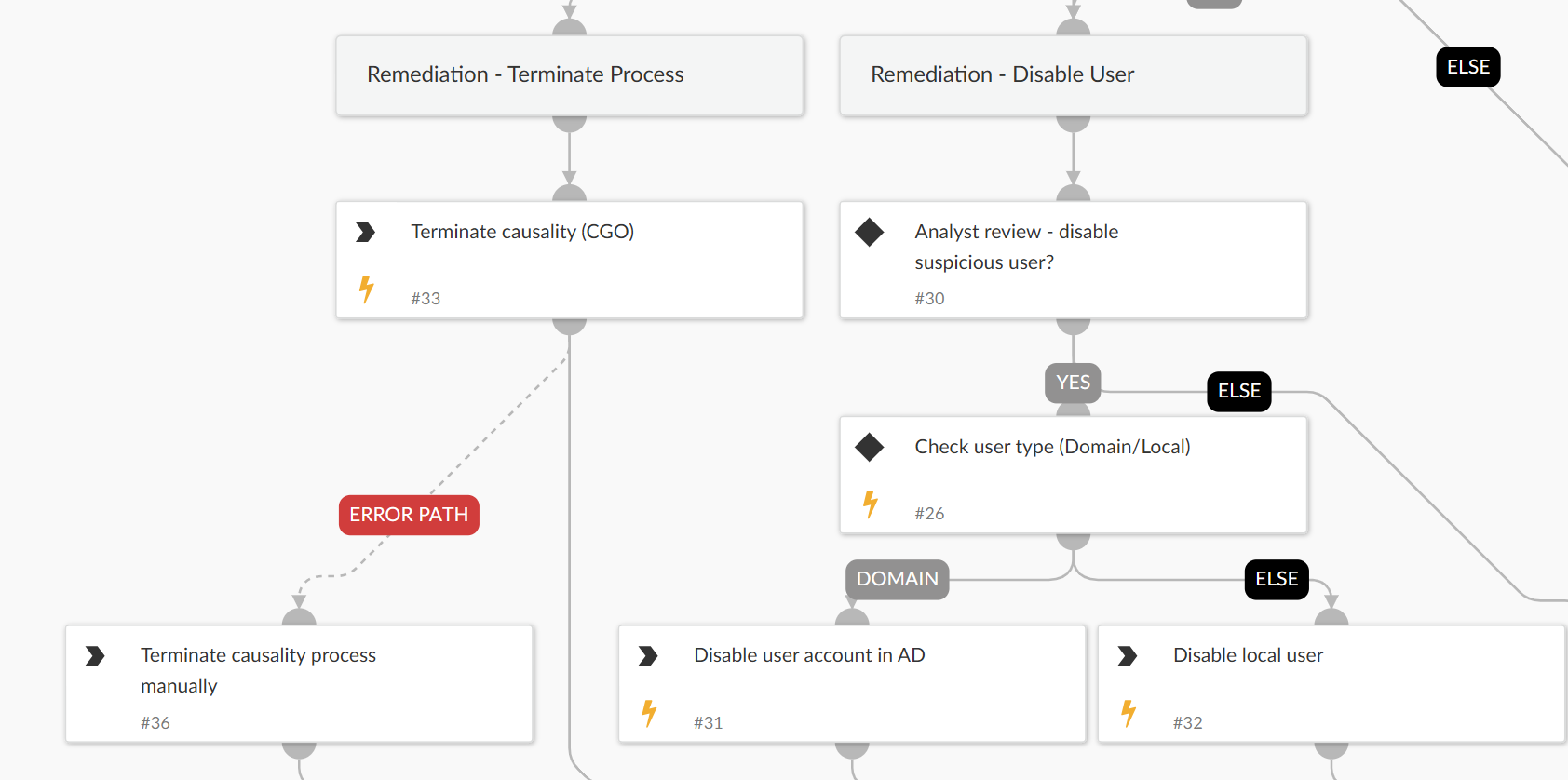
Containment
- If the alert is confirmed as a true positive, the playbook suggests disabling the hidden user account.
- Upon analyst approval, the playbook:
- Disables the user (whether domain or local).
- If a related alert identifies malicious script execution, the playbook terminates the Causality Group Owner (CGO) process responsible for creating the account.
Integration Requirements
To enable automated remediation, the following integrations must be active:
- Cortex Core - Investigation and Response (for alert analysis and process termination).
- Active Directory Query v2 (for domain user actions).
Security Challenges Addressed
- Detecting Hidden Persistence: Automatically identifies unauthorized user account creation attempts.
- Reducing Manual Investigation Time: Provides analysts with structured data, including risk scores and related alerts.
- Immediate Containment Actions: Allows security teams to disable suspicious accounts and terminate malicious processes.
- Context-Enriched Decision Making: Correlates multiple signals to determine the likelihood of a compromised system.
Conclusion
The Suspicious Hidden User Created playbook is a powerful tool for detecting and responding to unauthorized account creation attempts. By integrating Active Directory monitoring, behavioral risk analysis, and real-time containment actions, security teams can quickly neutralize threats and prevent persistent access by adversaries.
Learn More
For a deeper dive into the Cortex XSIAM Response and Remediation Pack, check out the full documentation here: Cortex Response and Remediation Pack.