Introduction
Scheduled tasks are a common mechanism for automating processes on sensitive servers, but they can also be exploited by attackers to execute malicious payloads. A suspicious process execution triggered by a scheduled task on a critical server warrants immediate investigation and remediation to prevent potential compromise.
The "Suspicious Process Execution by Scheduled Task on a Sensitive Server" playbook in the Cortex XSIAM Response and Remediation Pack. automates the detection, investigation, and response to such threats. Leveraging advanced analytics and Cortex XDR® integrations, this playbook ensures swift remediation of suspicious scheduled task executions.
Threat Overview
Attackers exploit scheduled tasks on sensitive servers to:
- Execute malware persistently.
- Establish footholds for lateral movement.
- Automate execution of unauthorized commands.
This playbook is triggered when an alert is generated for a suspicious process execution via a scheduled task on a sensitive server. It systematically analyzes, investigates, and remediates the detected threat.
Purpose of the Playbook
The "Suspicious Process Execution by Scheduled Task on a Sensitive Server" playbook follows a structured workflow to identify and mitigate potential threats.
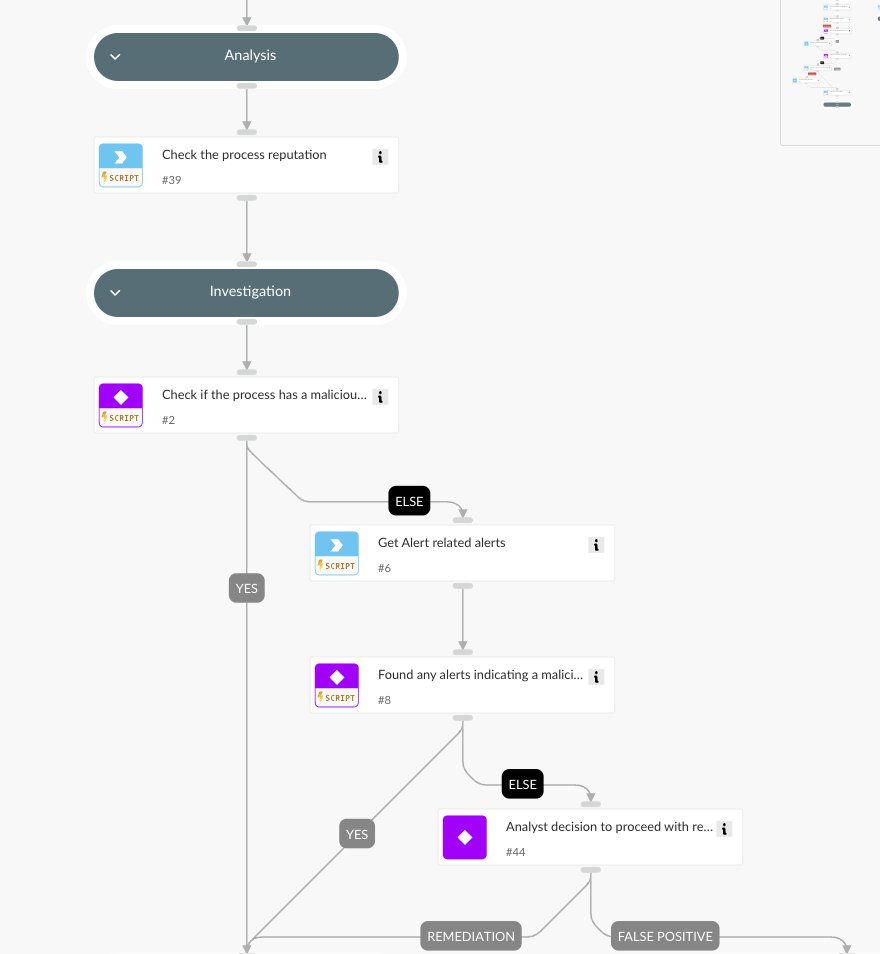
1. Analysis
- Assesses the reputation of the suspicious process using threat intelligence sources.
- Flags the process for further investigation if it has a bad reputation.
2. Investigation
The playbook conducts an in-depth analysis by:
- Searching for related Cortex XSIAM® agent alerts on the server.
- Identifying indicators of malicious activity associated with the executed process.
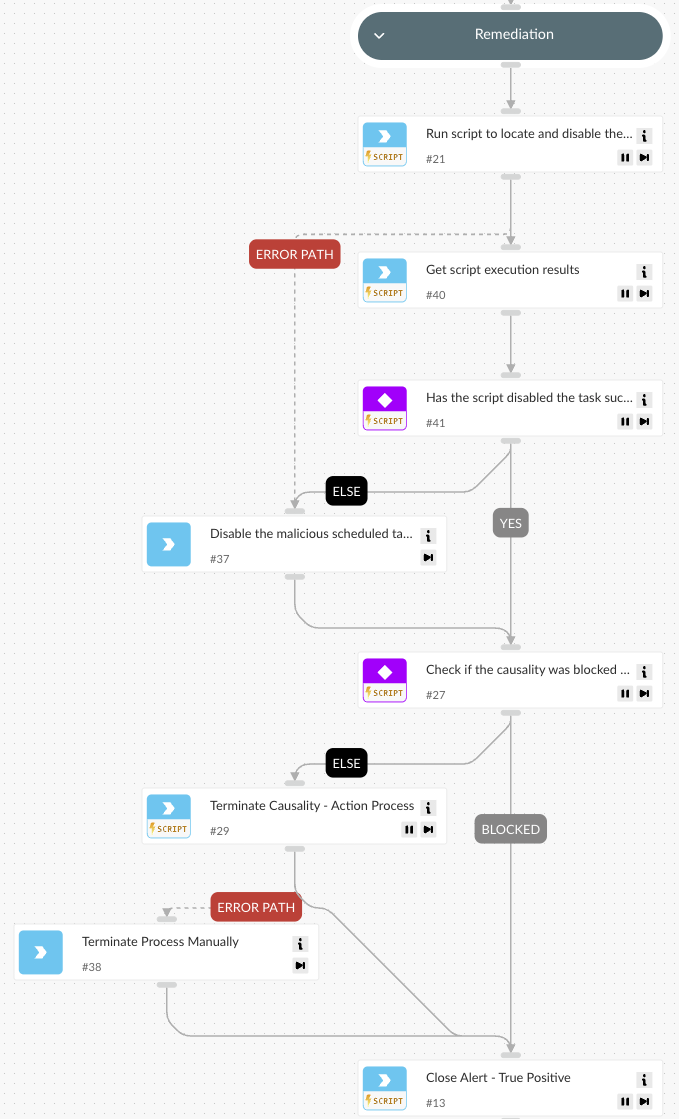
3. Remediation
If the process is confirmed as malicious based on its reputation or related alerts indicating malicious activity, the playbook automatically:
- Disables the scheduled task responsible for executing the process.
- Terminates the suspicious process to prevent further execution.
- Closes the alert once remediation steps are completed.
This structured approach ensures rapid containment and minimizes the risk of further compromise.
Conclusion
The "Suspicious Process Execution by Scheduled Task on a Sensitive Server" playbook enhances security automation by swiftly identifying and mitigating threats associated with scheduled task abuse. By leveraging Cortex XSIAM’s advanced analytics, organizations can ensure proactive defense against unauthorized executions on critical infrastructure.
For more details about this playbook and related automation use cases, visit the Cortex XSIAM Response and Remediation Pack.
To learn more about how you can transform your SOC through automation, schedule a personal demo for Cortex XSIAM.