Introduction
Credential dumping is a technique commonly used by adversaries to extract account credentials from a compromised system. Attackers leverage well-known tools like Mimikatz, LaZagne, and hashcat to obtain passwords and hashes, which can then be used for lateral movement, privilege escalation, or persistence. To counteract this threat, Cortex XSIAM’s Response and Remediation Pack includes the Credential Dumping using a Known Tool playbook, designed to detect, contain, and remediate credential dumping activity.
Threat Overview
Credential dumping attacks allow adversaries to retrieve stored credentials from operating system memory, security account managers, or other authentication databases. These techniques can be used to bypass security controls, escalate privileges, and gain unauthorized access to sensitive resources. In many cases, stolen credentials obtained through credential dumping tools or password crackers are used for lateral movement and privilege escalation, allowing attackers to infiltrate systems further and compromise additional accounts.
This playbook responds to the following alerts:
- Command-line arguments match Mimikatz execution
- Mimikatz command-line arguments
- Credential dumping via wce.exe
- Credential dumping via gsecdump.exe
- PowerShell runs with known Mimikatz arguments
- Hash cracking using hashcat tool
- Credential dumping via fgdump.exe
- Credential dumping via LaZagne
- Credential dumping via pwdumpx.exe
- Dumping lsass.exe memory for credential extraction
- Memory dumping with comsvcs.dll
Purpose of the Playbook
The Credential Dumping using a Known Tool playbook automates the detection and containment of credential dumping threats by:
- Identifying processes and command-line executions associated with credential dumping tools.
- Enforcing early containment by terminating suspicious processes.
- Offering remediation actions such as endpoint isolation.
Stages of the Playbook
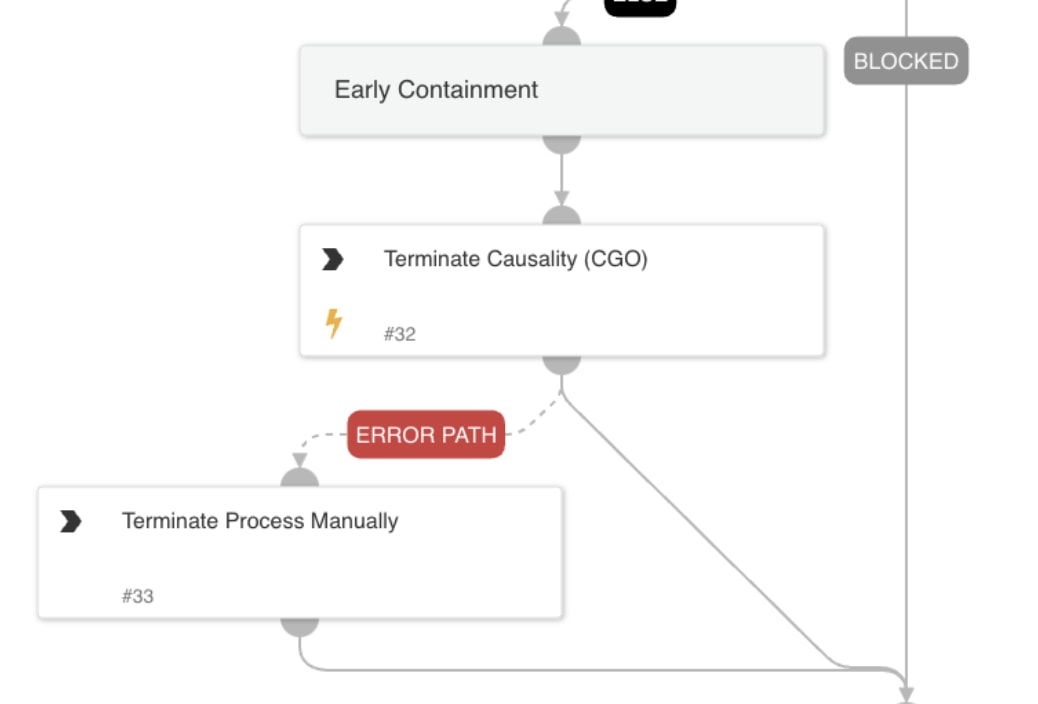
Early Containment
- The playbook checks for malicious execution patterns and terminates the causality process.
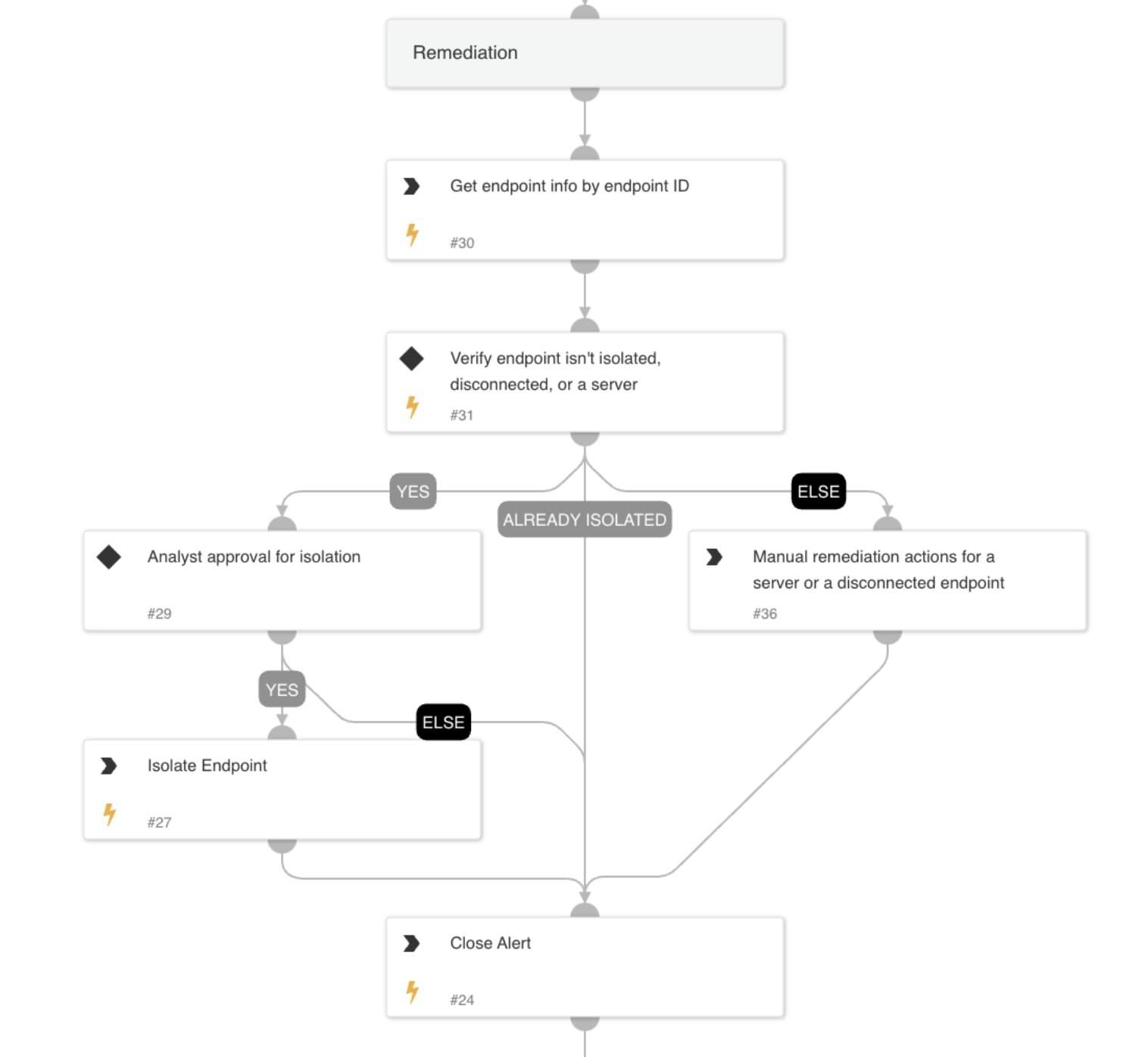
Remediation
- The playbook recommends isolating the affected endpoint to prevent credential theft and limit further compromise.
- An analyst is prompted to approve the endpoint isolation action before execution.
Integration Requirements
To fully leverage the playbook’s capabilities, the following integrations should be enabled:
- Cortex Core - Investigation and Response (for process termination and endpoint isolation).
Security Challenges Addressed
- Preventing Credential Theft: Automatically detects and halts credential dumping activities.
- Reducing Response Time: Provides a structured workflow for immediate containment and remediation.
- Limiting Lateral Movement: Prevents attackers from leveraging dumped credentials to access additional systems.
- Automating Manual Tasks: Reduces the workload on analysts by enforcing rapid response actions.
Conclusion
The Credential Dumping using a Known Tool playbook provides a proactive response to credential theft attempts. By integrating automated process termination and endpoint isolation, security teams can quickly mitigate credential dumping attacks and prevent unauthorized access to critical systems.
Learn More
For more details please visit the Cortex XSIAM Response and Remediation Pack.