Phishing attacks have come a long way since their inception. Initially, cybercriminals relied on mass email campaigns, hoping to trick unsuspecting users into revealing sensitive information. However, attackers have adapted their tactics as email security and user training continue to improve and user preferences shift to more modern communication formats.
With phishing as the most common type of social engineering attack, accounting for 15% of data breaches, we're now witnessing a new era of phishing tactics that are starting to exploit collaboration SaaS applications like Microsoft Teams, Slack and Zoom. Cybercriminals exploit these apps to deliver malicious links, harvest credentials, and spread malware.
Why Collaboration Apps Are Attractive to Attackers
Collaboration SaaS apps have become prime targets for several reasons. First, users often lower their defenses when accessing links shared through collaboration platforms, primarily due to two key factors:
Implicit User Trust
Many users have integrated multiple SaaS applications into their daily workflows. These apps are seen as trustworthy with corporate single sign-on and other security checks, leading to an assumption that all messages and any URLs shared within these platforms are also inherently secure.
Lack of Specialized Training
Identifying malicious content in a Teams or Slack channel presents a more significant challenge for end users than spotting suspicious emails. While extensive training programs have educated users about email-based threats, similar comprehensive initiatives for SaaS application security are still lacking. This gap in awareness can leave users ill-equipped to recognize and respond to threats in these collaborative environments.
The integrated nature of SaaS ecosystems also enables attackers to move laterally across multiple applications once they gain access to one. High levels of complexity, deep integration and vulnerable human factors create a landscape where users may unknowingly expose themselves and their organizations to sophisticated phishing attempts within trusted SaaS ecosystems.
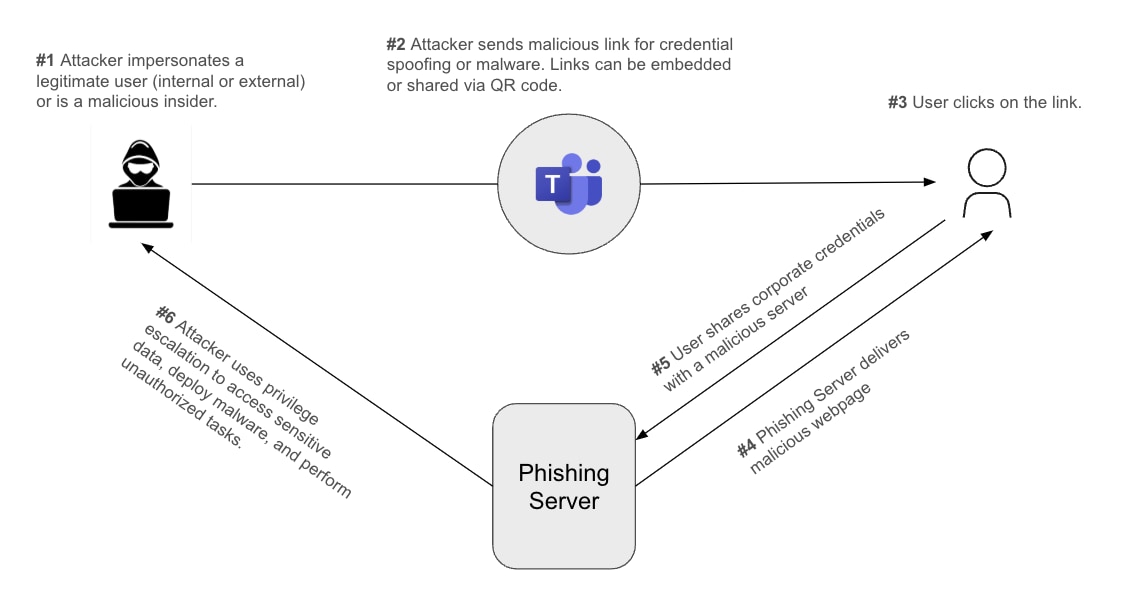
Figure 1: Stages of a phishing attack conducted via a SaaS collaboration app.
Witnessing an Alarming Trend in the Wild
The APT29 Phishing Campaign
APT29 (also known as Cozy Bear, a Russian state-sponsored group) carried out a phishing campaign targeting government and corporate entities via Microsoft Teams. They used compromised accounts to send phishing messages directly through Teams.
APT29 sent messages within Teams that contained malicious links, leading victims to credential-harvesting sites designed to resemble legitimate Microsoft login pages. This campaign demonstrates how malicious actors can use internal communication platforms to distribute phishing links effectively.
The DarkGate Malware Campaign
The DarkGate malware campaign has adopted a sophisticated approach that leverages Microsoft Teams as its primary delivery vector. This attack unfolds in several stages:
- Initial infiltration: Malicious actors gain access to corporate Teams environments, often by compromising legitimate user accounts.
- Phishing messages: Using these compromised accounts, attackers send deceptive messages containing malicious links or attachments to unsuspecting users within the organization.
- Malware deployment: When a victim clicks on the link or opens the attachment, the DarkGate malware is covertly downloaded.
- Exploitation: Once installed, the malware initiates its malicious activities, which may include data theft, further system exploitation, or serving as a gateway for additional attacks.
This method of attack is particularly insidious as it exploits the trust users place in their familiar collaboration tools, making detection and prevention challenging for many organizations.
Black Basta Ransomware via Microsoft Teams Chat
Attackers have devised Black Basta Ransomware, an approach that targets users through Microsoft Teams. They initiate communication by adding targeted users to chat groups, including external participants who operate from fake Entra ID tenants, carefully crafted to appear legitimate. Posing as support staff, administrators or help-desk personnel, these external users utilize convincing display names to impersonate genuine help-desk accounts.
By mimicking trusted identities, they aim to gain the confidence of their targets, making them more susceptible to further manipulation. This multilayered tactic exploits the inherent trust users place in internal communication channels, creating significant challenges in distinguishing between legitimate requests and malicious attempts at deception.
Palo Alto Networks SaaS Security
SaaS Security scans for malicious URLs, documents, and attachments shared within Microsoft Teams. Organizations will gain immediate visibility into messages, generate security incidents, and trigger automated responses to remove malware and malicious URLs proactively.
Safeguard Traffic on SaaS Collaboration Apps
Our protection for Microsoft Teams directly scans and secures URLs shared within the platform. This network-agnostic approach ensures users remain protected regardless of where they access the app without requiring a specific network setup. Additionally, SaaS Phishing Protection notifies users when malicious URLs or attachments are shared, helping to educate end users and improve security outcomes over time.
SaaS Phishing Protection uses a multifaceted approach that leverages advanced SaaS Security and end-user education.
1. Detects and Analyzes URLs
SaaS Phishing Protection will:
- Ingest and scan every message shared within Microsoft Teams
- Extract URLs shared within these messages
- Forward URLs to Advanced URL Filtering
2. Remediates Risk
Organizations can proactively delete malicious URLs to mitigate risk and limit damage.
3. Coaches End Users
Enhanced monitoring capabilities should educate users when they detect malicious URLs within messages. End-user notifications will help avoid violations and security incidents.
Proactive Phishing Remediation
SaaS Security calculates a “phishing exposure score” for each link based on the number of exposed users for enhanced risk remediation. For instance, links shared within a channel typically have a much higher exposure score than those shared via direct message. This scoring system helps administrators prioritize manual remediation efforts when automation is not feasible.
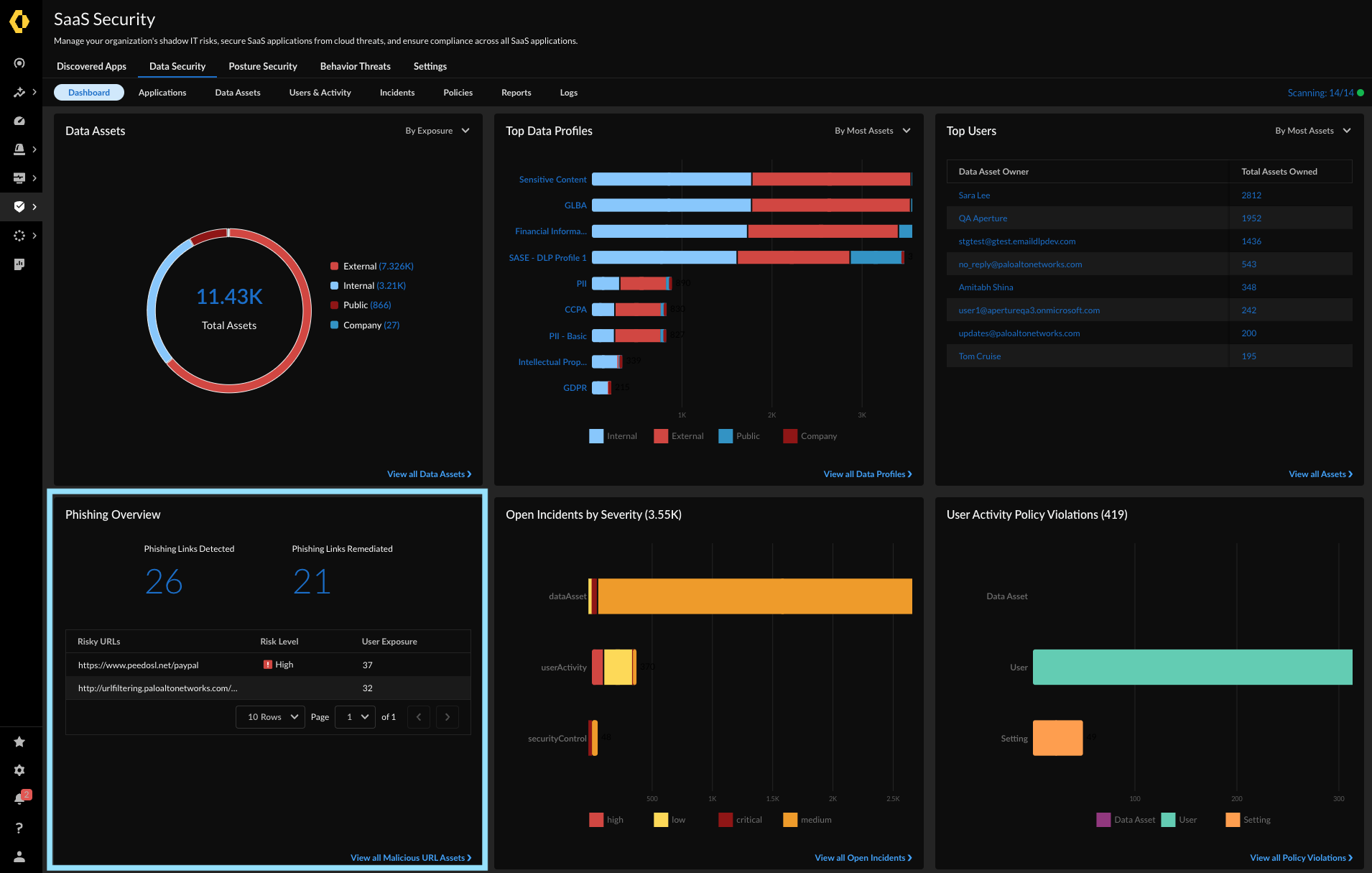
Figure 2: Summary of links shared and remediated with the associated level of risk and user exposure.
Administrators can access messages containing malicious URLs directly within Microsoft Teams through the Strata Cloud Manager. This functionality allows them to make informed decisions regarding the deletion or restoration of messages directly from the application, which is particularly beneficial for addressing false positives.
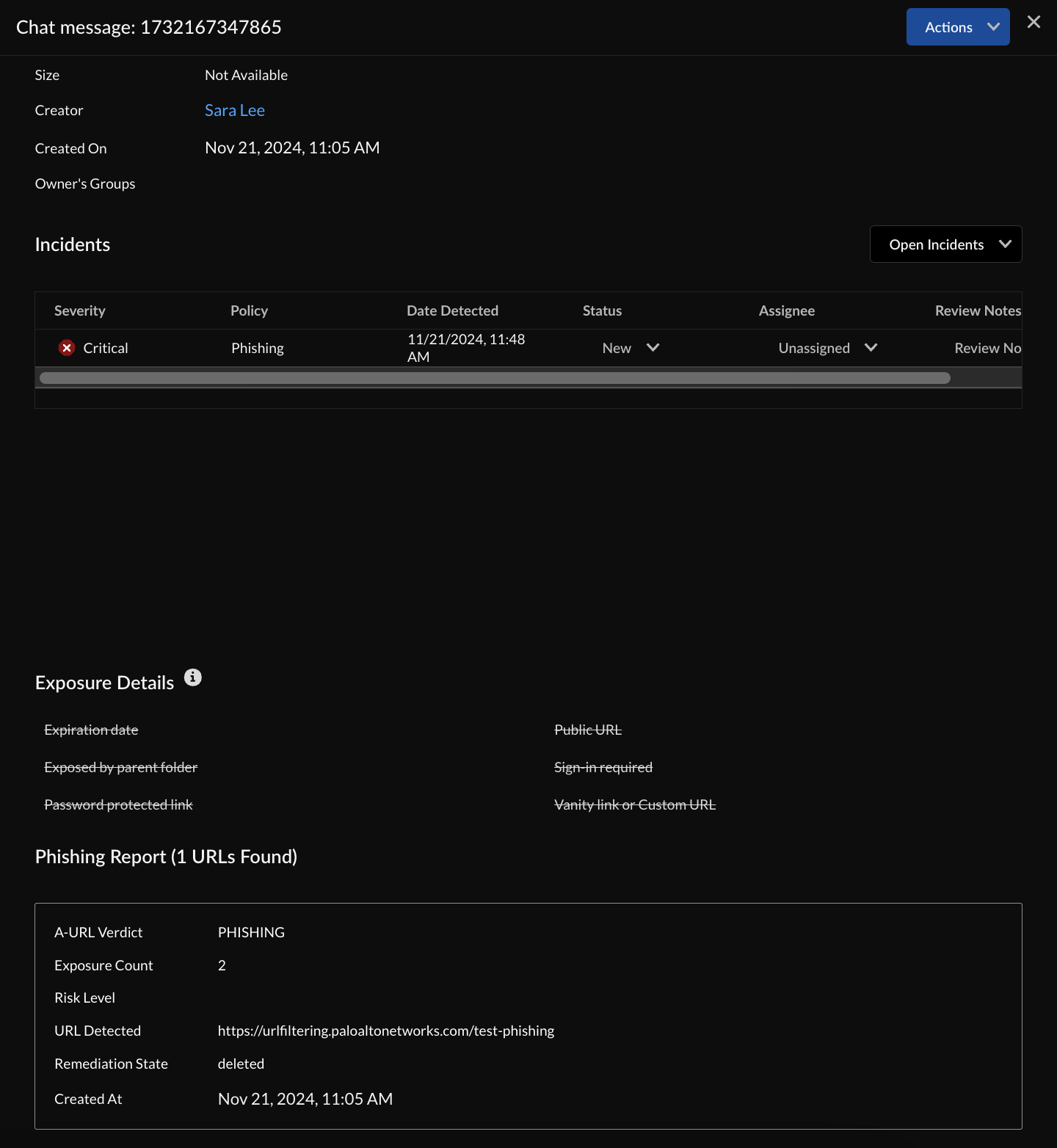
Figure 3: Phishing report with an analysis of the shared URL.
Adapting to a New Era of Phishing Threats
The evolution of phishing from email to SaaS collaboration apps represents a significant shift in cybersecurity. As attackers continue exploiting the trust in legitimate SaaS platforms, security teams must remain vigilant and adaptive.
By understanding the mechanics of SaaS phishing, implementing advanced security measures and fostering a culture of cybersecurity awareness, organizations can better protect themselves against this emerging threat. The battle against phishing is far from over, but security teams can stay one step ahead with the right strategies and tools.
We have enabled this feature for all existing Palo Alto Networks SaaS and Data Security customers to enhance the visibility and security of their Microsoft Teams environment. Stay tuned as we continue to innovate by expanding these innovations to other collaboration platforms. Other upcoming improvements include forwarding unknown or high-risk URLs to Palo Alto Networks Remote Browser Isolation.
Contact your representative to explore how SaaS Security can empower your business to thrive in today’s dynamic digital landscape. Together, we’ll shape the future of SaaS security and enable you to stay ahead of emerging threats.
This blog contains forward-looking statements that involve risks, uncertainties and assumptions, including, without limitation, statements regarding the benefits, impact or performance or potential benefits, impact or performance of our products and technologies. These forward-looking statements are not guarantees of future performance, and there are a significant number of factors that could cause actual results to differ materially from statements made in this blog. We identify certain important risks and uncertainties that could affect our results and performance in our most recent Annual Report on Form 10-K, our most recent Quarterly Report on Form 10-Q and our other filings with the U.S. Securities and Exchange Commission from time-to-time, each of which are available on our website at investors.paloaltonetworks.com and on the SEC's website at www.sec.gov. All forward-looking statements in this blog are based on information available to us as of the date hereof, and we do not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.