Cloud-native application protection platforms (CNAPPs) excel at identifying, prioritizing and remediating cloud risks, but organizations must also be equipped to respond to threats in real time. Prisma Cloud integrates advanced threat detection capabilities that, unlike basic CNAPP offerings, enable organizations to not only manage critical risks but also combat emerging threats. What exactly does this mean?
Detecting Threats Vs. Identifying Risks
Risks are the chances that something unfortunate could happen. If you leave a window open at night, for instance, there’s a risk that someone could enter your home, which could lead to problems like theft or damage. Threats, on the other hand, are the actual dangers that cause harm when given the chance. They’re the burglars looking for opportunities to break in through that open window.
Vulnerabilities and misconfigurations are typical indicators of risk in the cloud. For example, if a company misconfigures its cloud storage settings, it might accidentally expose sensitive information to the internet. This oversight creates a risk that a cybercriminal can take advantage of. Security teams that understand the difference between risks and threats can better protect their cloud environments by addressing vulnerabilities and remaining aware of potential threats that could exploit them.
If you’re a current or prospective CNAPP adopter, you’ll find the platform will help you detect and mitigate several threat vectors.
Network Attacks
Network and DNS threats pose significant risks that can compromise security and disrupt operations. Network-based anomalies often signal malicious activity, with unusual traffic patterns indicating unauthorized access attempts or data exfiltration that require immediate attention.
Malicious port scans enable attackers to identify open ports and services on a network, seeking vulnerabilities to exploit. These vulnerabilities can then be leveraged to launch distributed denial-of-service attacks, overwhelming the network with excessive requests from untrusted sources.
DNS rebinding attacks exploit how web browsers handle the same-origin policy, allowing attackers to bypass security controls and access sensitive resources on a local network, resulting in unauthorized access and data theft. Additionally, domain generation algorithm (DGA) attacks use algorithms to create numerous rapidly changing domain names for communication with compromised systems, making it difficult for security measures to effectively block them.
Before Prisma Cloud, threat visibility required the insertion of virtual appliances or agents to inspect network traffic. Prisma Cloud’s agentless approach analyzes the network flow logs, audit events and DNS logs from your cloud service providers and applies machine learning to detect evasive threats and anomalous behavior.
Malware Across Workloads
One of the biggest misconceptions about threats is that they only target your running cloud instances. In reality, threats can infiltrate your applications before deployment. Attackers poison container images and inject malware, which can spread across systems once deployed. It’s important for security measures to go beyond vulnerability management and detect threats across the workload lifecycle. To mitigate these risks, teams must detect and block threats before deploying container images.
Prisma Cloud secures workloads across the lifecycle, inspecting images and running instances for threats. The threat intelligence is backed by Palo Alto Networks Advanced WildFire, the industry’s largest malware prevention engine, enabling security teams to block 99% of known and unknown malware across cloud workloads. Prisma Cloud delivers malware detection and prevention controls for predeployed container images and running compute instances, providing full lifecycle protection.
Data Threats
Organizations today face a multitude of data threats that can impact their operations and reputation. “Roughly one-third of all breaches involved ransomware or some other extortion technique,” according to Verizon's 2024 Data Breach Investigation Report. One of the most notorious threats, attackers effectively hold your encrypted critical files ransom, demanding a payment for their release. Attacks of this nature disrupt business continuity and can lead to significant financial loss and damage to customer trust.
Another serious data threat is malware targeting data at rest. The attack involves malicious software infiltrating databases or storage systems, often to steal sensitive information or corrupt data. When attackers gain access to stored data, they can compromise everything from personally identifiable information (PII) to financial records, putting organizations at risk of compliance violations and legal repercussions.
In a data exfiltration scenario, attackers employ covert methods to move sensitive information out of an organization's network. They exploit system vulnerabilities or manipulate insider threats to achieve their objectives. Once exfiltrated, the data can be sold on the dark web or used for additional malicious purposes, leading to severe and long-lasting repercussions for the organizations.
Prisma Cloud’s Data Security Posture Management (DSPM) offers built-in data detection and response (DDR) to go beyond identifying sensitive data exposures. DDR continuously monitors data access patterns and user behavior, enabling organizations to swiftly detect and respond to potential breaches. By integrating DDR into their security strategy, organizations can enhance their ability to protect sensitive information against these evolving threats, ensuring a stronger security posture in their cloud environments.
Web Applications and APIs
Web applications and APIs are public-facing, making them prime targets for external threat actors. With the growing reliance on digital services, attackers continuously seek to exploit vulnerabilities in these critical components.
Injection attacks rank among the most prevalent threats. Here, malicious actors inject harmful code into applications, manipulating them to gain unauthorized access to sensitive data, leading to severe consequences like data breaches and financial losses.
Broken authentication poses another significant risk. When web applications lack robust authentication mechanisms, attackers can easily bypass security measures and access user accounts. Doing so not only compromises individual data but also allows attackers to manipulate application functionality.
Cross-site scripting (XSS) attacks further expose web application vulnerabilities. Attackers inject malicious scripts into webpages, executing harmful actions in the browsers of unsuspecting users, resulting in stolen credentials and session hijacking.
With Prisma Cloud, organizations can implement web application and API security (WAAS) to gain real-time attack detection and prevention. Prisma Cloud protects against the OWASP top 10 attacks for web applications, secures APIs and manages bot traffic. With virtual patching, security teams actively detect and block newly discovered exploits in situations where they can’t patch web applications.
Correlating Threats
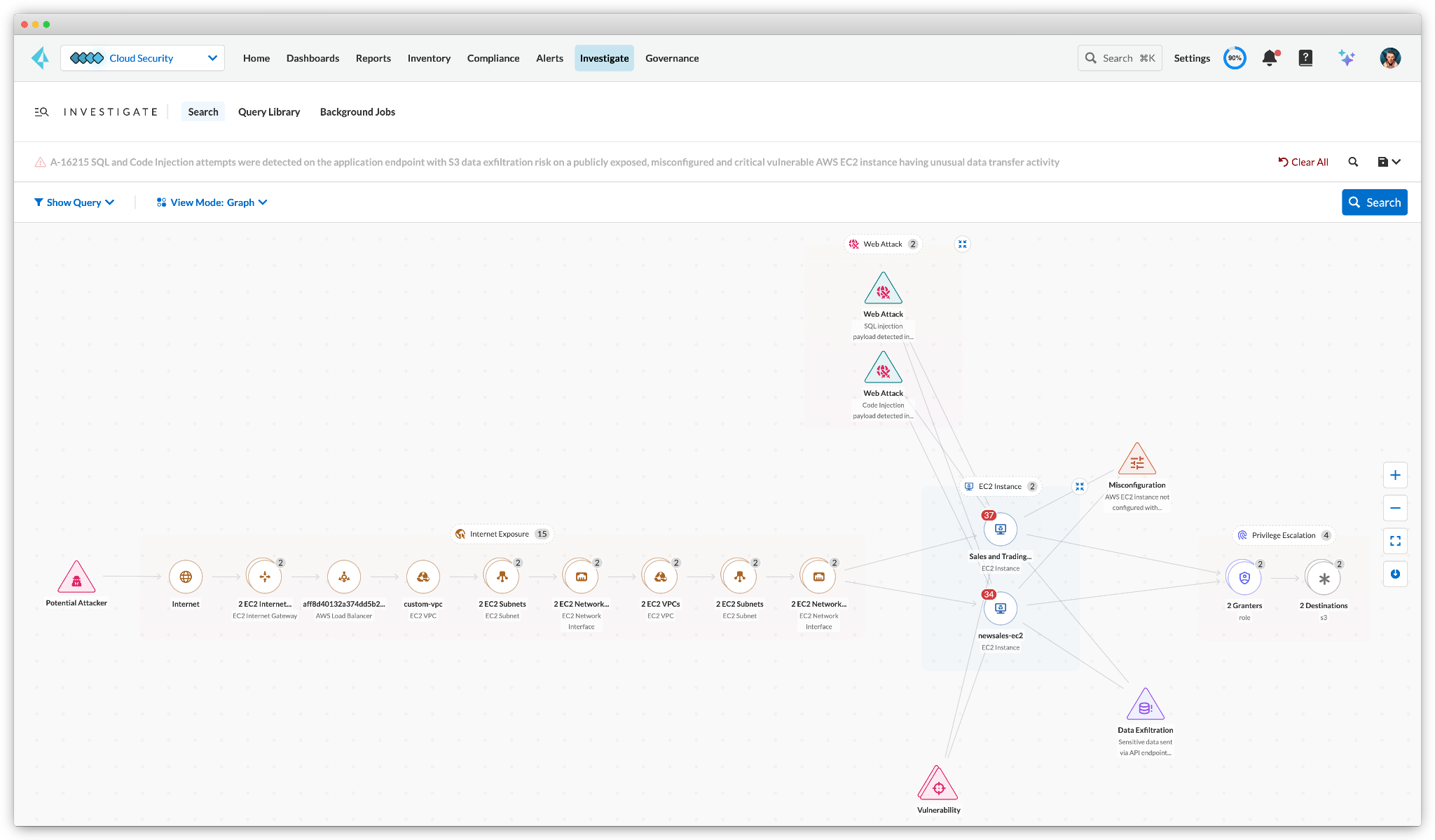
Detecting individual indicators of compromise is just the beginning. Prisma Cloud correlates signals across risks and threats to identify interrelated issues that together form potential and compromised attack paths. By bringing the data together into a graph, security teams can visualize an attacker’s steps such as initial compromise, lateral movement and exfiltration.
Backed by Precision AI, organizations can get an AI-generated summary to distill complex attack paths. The Prisma Cloud Copilot enables organizations to ask short and simple questions to quickly identify and act on their most critical security issues.
Learn More
Prisma Cloud is a CNAPP that reduces risks and prevents breaches from code to cloud. If you want to learn more about the platform, book a personalized demo with one of our experts.