Introduction
Anonymizing networks like Tor are commonly used to mask user identities and bypass security measures. While Tor has legitimate uses, attackers frequently exploit it to conduct unauthorized access attempts, particularly against software-as-a-service (SaaS) applications. To counteract this threat, Cortex XSIAM’s Response and Remediation Pack includes the Suspicious SaaS Access From a Tor Exit Node playbook, designed to detect and remediate such suspicious access attempts.
Threat Overview
Attackers often leverage Tor exit nodes to conduct reconnaissance, attempt credential stuffing, or gain unauthorized access to SaaS environments without revealing their true locations. This playbook is triggered by the following alerts:
- Suspicious SaaS API call from a Tor exit node
- Suspicious SaaS API call from a Tor exit node via a mobile device
- Suspicious API call from a Tor exit node
- Suspicious Kubernetes API call from a Tor exit node
Purpose of the Playbook
The Suspicious SaaS Access From a Tor Exit Node playbook automates the detection and remediation of unauthorized access by:
- Identifying user sessions originating from Tor exit nodes
- Evaluating the legitimacy of the associated user agent
- Assessing the user’s risk level based on behavioral analytics and advanced AI logic
- Enforcing early containment by revoking active sessions
- Providing remediation options for blocking suspicious accounts and Tor-related IPs
Stages of the Playbook
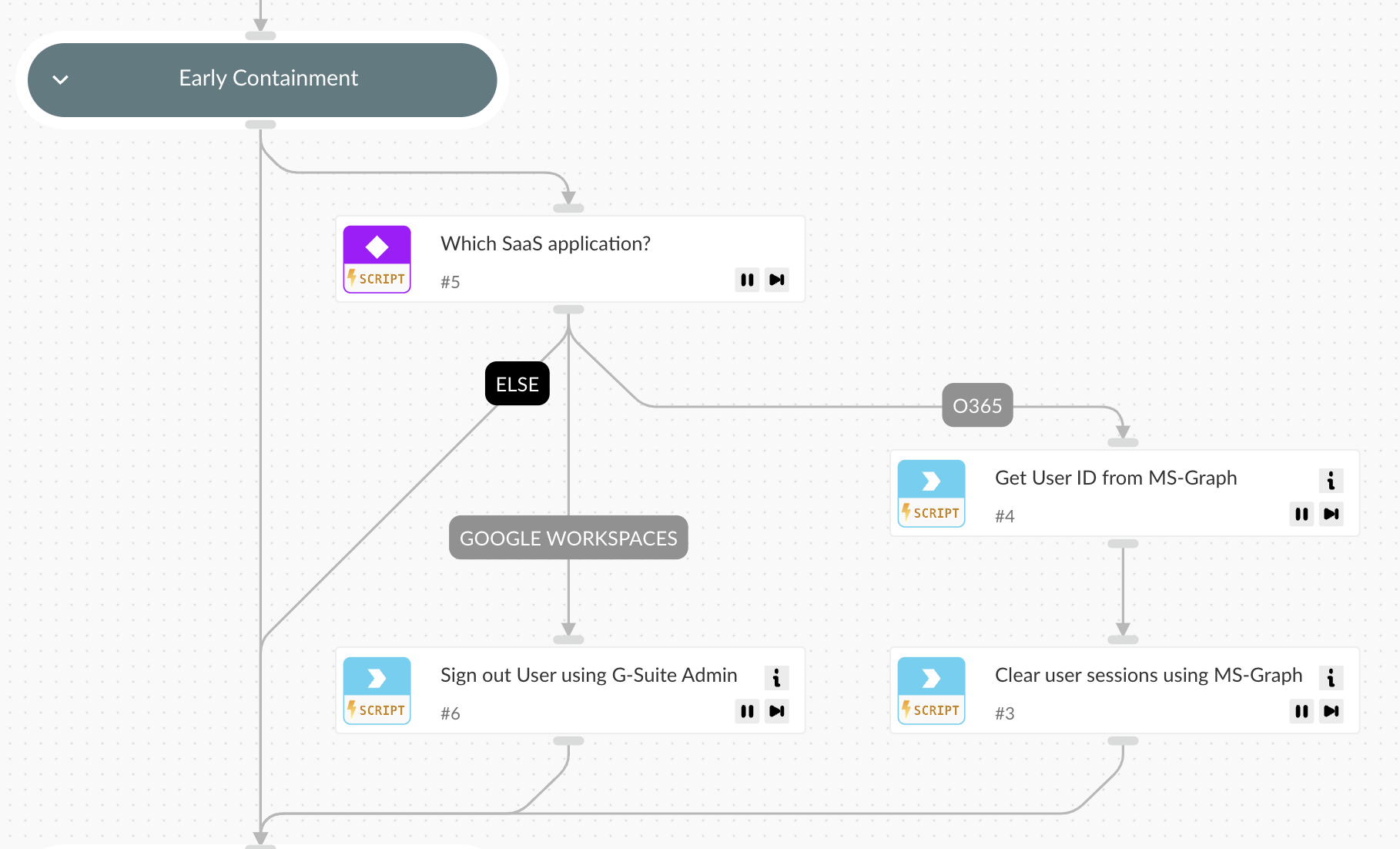
Early Containment
- The playbook promptly clears or revokes the user’s active sessions and forces re-authentication.
- Depending on the SaaS platform, the playbook utilizes Microsoft Graph or G-Suite Admin to enforce session termination.
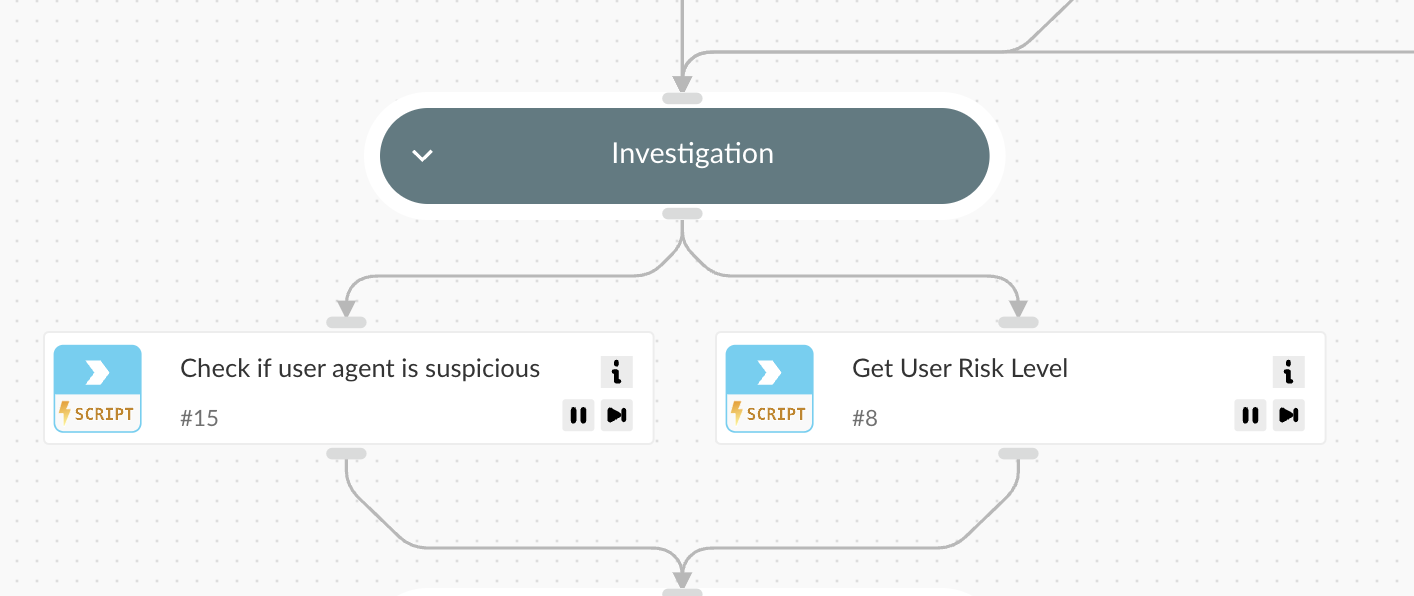
Investigation
- The playbook retrieves the risk score of the user associated with the access from a Tor exit node.
- It inspects the user agent to determine if the access is legitimate or indicative of the use of a malicious attack tool or automated behavior.
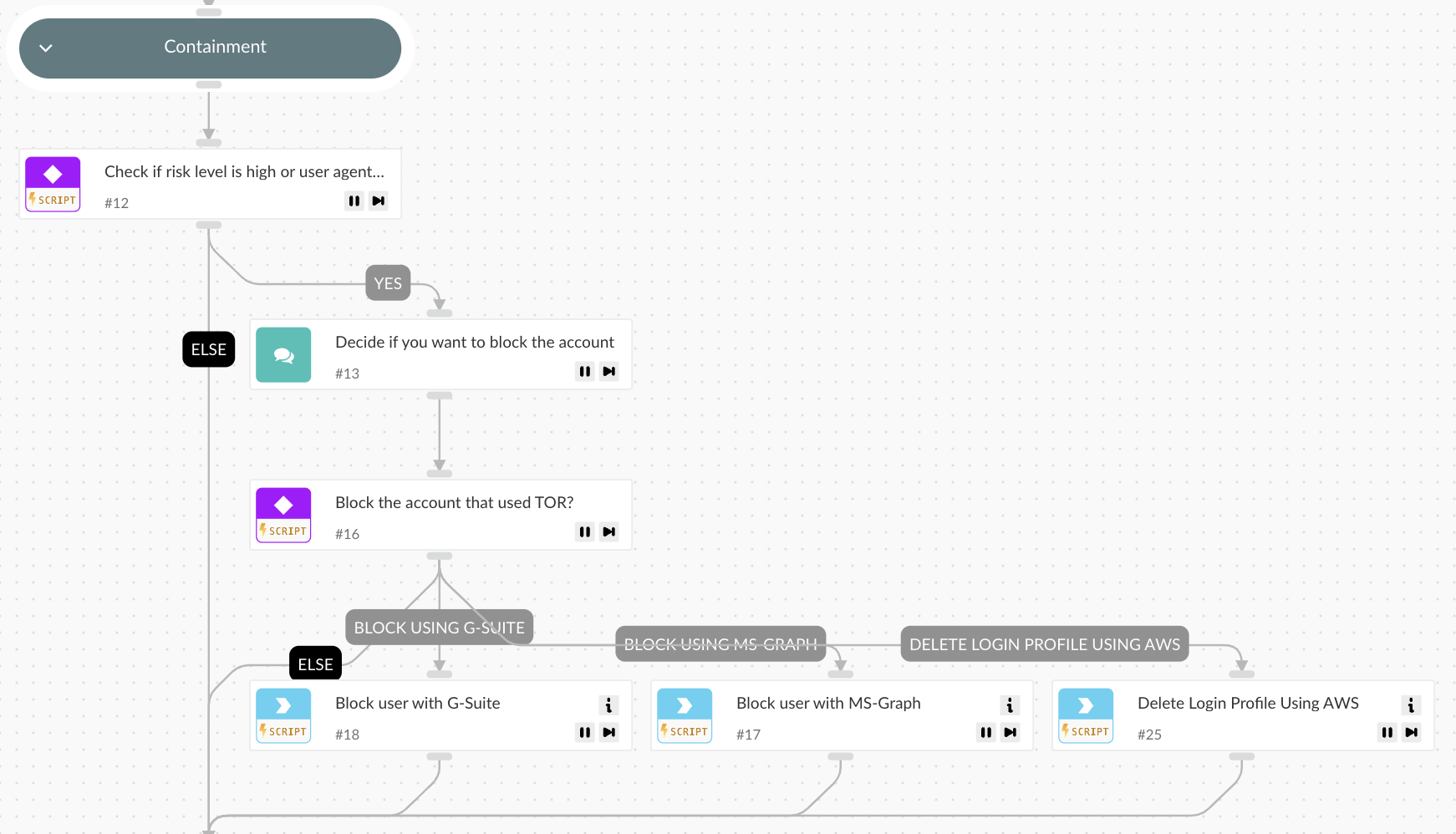
Containment
- If the user’s risk score is high or the user agent is flagged as suspicious, the playbook recommends blocking the account.
- The account can be blocked through Microsoft Graph, G-Suite Admin, or AWS IAM, depending on the cloud provider.
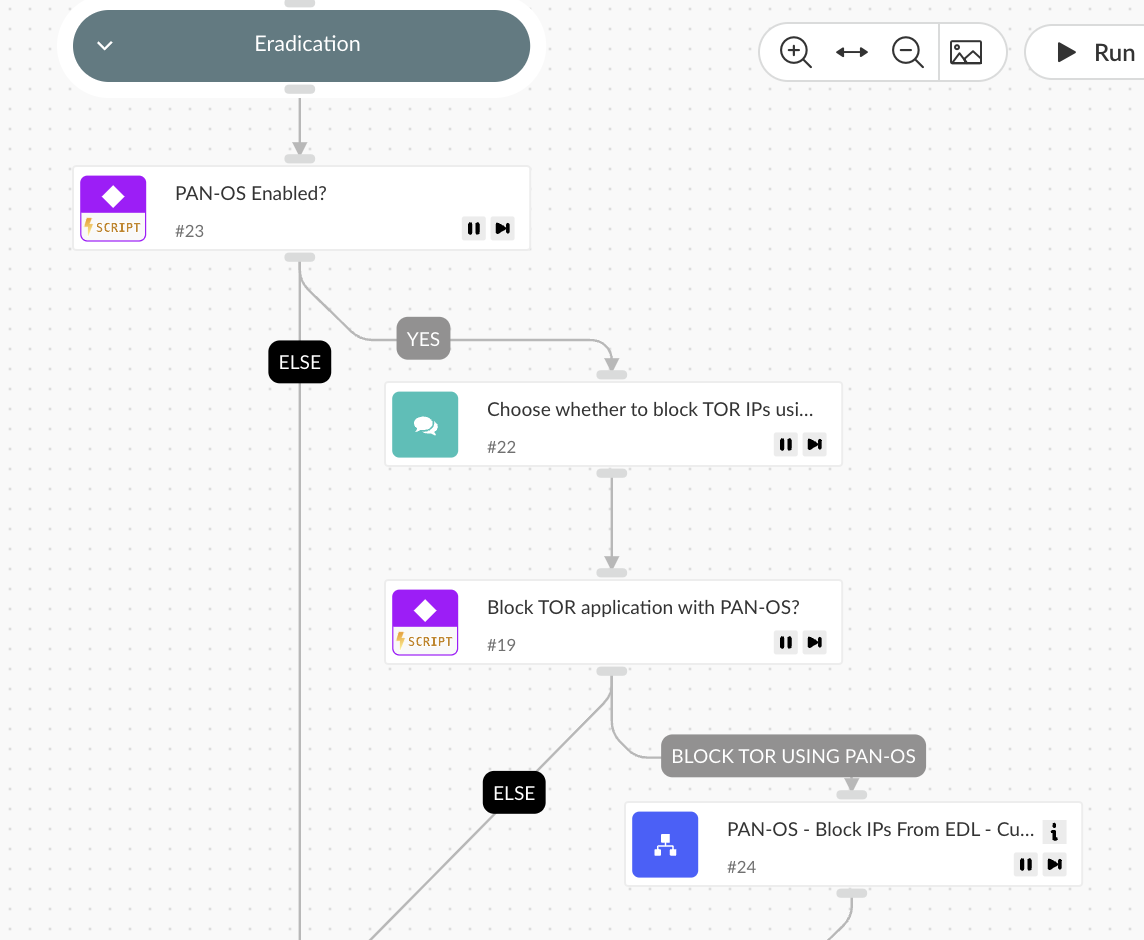
Eradication
- If Palo Alto Networks PAN-OS is enabled, the playbook suggests blocking Tor exit node IPs using the predefined External Dynamic List (EDL) feature, preventing further anonymous access attempts.
Integration Requirements
To enable automated containment and remediation, the necessary integrations should be configured based on the log source that generated the alert:
- Microsoft Graph User – Required for alerts originating from Azure, enabling response actions for Microsoft SaaS accounts.
- Google Workspace Admin – Required for alerts from GCP, allowing administrative actions within Google Workspaces.
- AWS IAM – Required for alerts from AWS, managing cloud infrastructure-related access attempts.
- PAN-OS – Required for network-wide Tor exit node blocking, ensuring threat actors cannot use anonymized traffic to evade detection.
Security Challenges Addressed
- Detecting Anonymized Access: Identifies unauthorized access attempts originating from Tor exit nodes.
- Mitigating Unauthorized API Calls: Prevents attackers from exploiting SaaS API endpoints for malicious activities.
- Session Revocation for Suspicious Users: Immediately disrupts potential account takeovers by revoking user sessions.
- Enforcing Adaptive Access Control: Adjusts security controls based on the assessed risk level of the user.
Conclusion
The Suspicious SaaS Access From a Tor Exit Node playbook offers a structured approach to identifying and remediating unauthorized Tor-based access attempts. By leveraging automated session revocation, risk assessment, and adaptive containment measures, security teams can effectively mitigate threats posed by anonymized connections.
Learn More
For more details on the Cortex XSIAM Response and Remediation Pack, visit: Cortex Response and Remediation Pack.