As organizations shift to cloud-based environments, security concerns grow, especially around protecting user accounts and sensitive data. The "Impossible Traveler" detection method, a key feature of Cortex XDR, is vital for spotting login attempts from distant locations in a short time. This blog explores the core detection opportunities, advanced techniques, and challenges in Impossible Traveler Detection.
What is Impossible Traveler Detection?
Imagine this: Richu, a financial analyst based in New York, logs into their company’s secure portal at 9:00 AM. Just 45 minutes later, a login attempt is detected from Tokyo using Alex’s credentials. Unless Alex has access to a teleportation device, it’s physically impossible for them to have traveled across the globe in such a short time. This discrepancy raises a red flag: an Impossible Traveler alert.
Impossible Traveler Detection is designed to identify these anomalies—situations where a user appears to log in from two geographically distant locations within an unrealistically short time. By analyzing the time, geography, and login patterns, the system detects potentially compromised accounts and helps security teams respond swiftly.
In today’s increasingly complex network environments, where remote work and global operations are the norm, this capability is more essential than ever. In another example, Jamie, a sales executive, frequently logs in from different countries due to work travel. The system should learn Jamie’s behavior while flagging unexpected or unusual patterns—like a simultaneous login from a region they have never visited.

Basic Detection Logic using XQL
A simple XQL query can identify cases where users log in from multiple countries within a single session by detecting two logon attempts from the same user within a one-hour window. While this approach provides a basic mechanism for flagging Impossible Traveler scenarios, its limited refinement can generate anywhere from hundreds to thousands of alerts daily, depending on the environment's size and activity levels. The Impossible Traveler - SSO XQL query can be found alongside a wide range of additional use cases in the XQL Query Library. An example of this XQL query is provided in the Appendix.
To refine detection accuracy and filter out alert fatigue, let's dive into the real-world challenges of VPNs, border geolocation, and evolving user travel patterns.
Navigating Complex Networks: Unraveling False Positives Beyond Geography
In today’s interconnected world, the widespread use of VPNs and the constant need for continuous connectivity present real challenges to accurate geolocation. Let’s explore how these challenges manifest in practice:
VPN Failover, Routing, and Geolocation Challenges
In real life, VPN gateways often change due to load balancing, redundancy, or failover setups for optimal performance, presenting risks for false positives in behavioral detection. These changes can instantly alter a user's IP address, making valid logins appear from different locations—such as shifting from Canada one moment to the U.S. the next. In this example, the system might mistakenly flag a valid login as an “Impossible Traveler” alert simply due to the nature of VPN configurations.
Border Geolocation and Its Impact
IP addresses near borders can be particularly problematic. Due to the overlapping and fluid nature of IP address allocation, an IP might map to Canada on one day and to the neighboring U.S. on another. This scenario can result in a valid login being flagged as suspicious.
Alert Key Factors and Features
Understanding the factors that impact whether an alert is triggered is vital for reducing false positives and improving alert fidelity. This section will explore key features such as identifying rare login locations, analyzing user travel patterns, and contextualizing origin IPs.
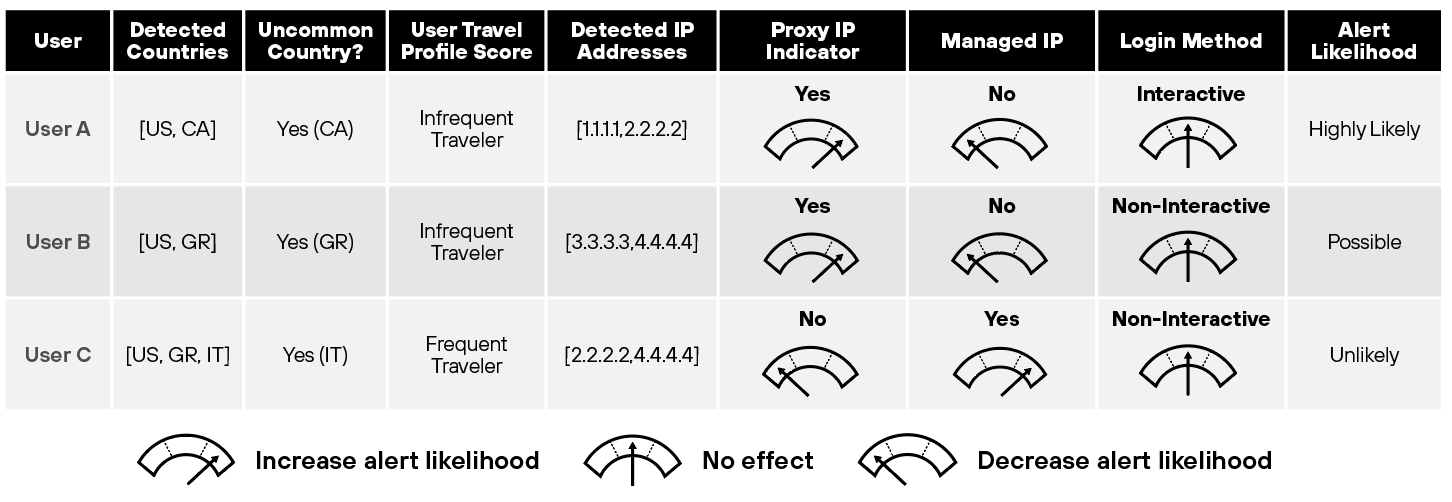
Rare vs. Common Countries
To improve the accuracy of impossible traveler alerts, it’s crucial to determine whether any country observed in a session is unusual for both the user and the organization. The system maintains dynamic profiles based on typical login patterns and thresholds. For example, if a user who normally logs in from North America suddenly appears in a rare location such as Madagascar, where the organization has no presence, the system flags this anomaly as suspicious and increases the alert’s severity.
Dynamic Learning Through User Travel Profiles
To enhance detection accuracy and reduce false positives, it is crucial to consider each user's travel profile. By building dynamic travel profiles, the system learns and recognizes consistent login patterns. For example, a frequent traveler like Jamie—a salesperson who regularly logs in from multiple international locations. The detector understands that his logins from several countries within a short timeframe are part of his regular behavior. This dynamic approach not only improves the fidelity of the alerts by differentiating between legitimate and suspicious activities but also minimizes false positives that might otherwise be triggered by an atypical login pattern.
Contextualizing Origin IP, Managed IPs, and Device Context
To reduce false positives in impossible traveler detection, exclude connections from managed devices. This includes office NAT IPs or employee host IPs verified by trusted sources like endpoint detection and response (EDR) systems. By confirming the IP is linked to a corporate device, organizations can better identify legitimate activity, ensuring valid logins are not mistakenly flagged as suspicious and improving detection accuracy.
Analyzing Authentication Methods: Interactive vs. Non-Interactive Logins
Yet another important factor that determines whether an alert will fire is the type of login used for a session. Different types of logins, such as when a user manually logs onto his/her account, known as 'interactive logins', versus automated system processes or applications, known as 'non-interactive logins', may involve different risk levels. Interactive logins are increasingly used by attackers this makes them more relevant when classifying behavior as suspicious in impossible traveler alerts, since they are more likely to be associated with potential security threats.
Impossible Traveler Alert Scenarios Explained
The table below illustrates scenarios highlighting features discussed in this blog, such as observed countries, rare locations, and user travel profiles. Each row represents a user scenario affecting alert triggers or severity. Note: This is a high-level, simplified example of the detector's logic.
Beyond Detection: Investigation Actions for Better Alert Triage
When investigating impossible traveler alerts, enriching the detection process with additional context is crucial for reducing false positives and improving overall security. By applying best practices, such as leveraging device context and analyzing prior authentication attempts, organizations can better distinguish between legitimate user behavior and potential threats.
1. Maintaining Corporate VPN IP Lists
To improve detection accuracy, maintain a list of known IP ranges for your corporate VPN solution. By identifying logins from trusted IPs, you can reduce alert severity and filter out legitimate activity, ensuring only true threats trigger high-severity alerts.
2. Device Context and Fingerprinting
Understanding device context is essential for reducing false positives and identifying suspicious behavior. Device fingerprinting compares the device used for login against the user’s profile, improving the precision of identifying legitimate or suspicious logins.
3. Analyzing Prior Authentication Attempts
Reviewing previous login attempts, especially during impossible traveler alerts, can reveal attack techniques like MFA fatigue or brute-force attacks. Monitoring failed sign-in attempts versus average attempts can help detect these suspicious activities early.
4. Resource Access Post-Authentication
Logging the resources accessed after authentication can highlight unusual behavior. If a user accesses resources they haven't used in a long time, alongside triggering impossible traveler criteria, it can signal a higher level of threat and warrant further investigation
Final Thoughts
As cloud adoption accelerates, detecting unauthorized access becomes increasingly critical. Impossible Traveler Detection plays a vital role in identifying anomalous logins, but factors like VPN usage, dynamic IP allocation, and global workforce mobility introduce complexities that can lead to excessive false positives. To enhance detection accuracy, Cortex XDR refines alerting mechanisms by incorporating behavioral analytics, contextual device data, and adaptive risk-based assessments. The ultimate goal is to strike a balance between security and operational efficiency—effectively identifying real threats without burdening SOC analysts with excessive alert volume.
For Impossible Traveler Cortex XDR reference check out Impossible Traveler alert reference
Appendix
An XQL query detects successful logins from different countries by the same user within a one-hour timeframe.
preset = authentication_story
|alter hour = extract_time(_time, "Hour")
| alter day = extract_time(_time, "DAYOFYEAR")
| filter action_country != "" and action_country != "-" AND auth_outcome = "SUCCESS" AND action_country != null
| comp values(action_country) as countries by auth_identity
| alter count_distinct_action_country = array_length(countries)
| filter count_distinct_action_country > 1