Introduction
The Cortex XSIAM Response and Remediation Pack delivers a powerful set of automated playbooks designed to streamline incident response and remediation. This blog highlights the Compromised Accounts - User Rejected Numerous SSO MFA Attempts playbook which addresses threats tied to repeated multi-factor authentication (MFA) rejection attempts.
Threat Overview
Repeatedly rejected MFA attempts can signify malicious activity, such as attackers attempting to gain unauthorized access to user accounts. This pattern is often associated with brute force or credential-stuffing attacks, where adversaries try multiple login attempts until successful. Moreover, such activity may involve suspicious IPs or geolocations, potentially indicating a compromised account or insider threat.
This type of behavior necessitates prompt investigation and remediation to safeguard sensitive organizational data and prevent unauthorized access.
Purpose of the Playbook
The "Compromised Accounts - User Rejected Numerous SSO MFA Attempts" playbook is designed to:
- Investigate alerts related to unusual MFA rejection patterns.
- Identify malicious intent through IP reputation analysis, risk scoring, and login behavior.
- Automate response actions to contain and remediate threats effectively.
Alerts Addressed by the Playbook
This playbook addresses the following alerts:
- "User rejected numerous SSO MFA attempts."
- "Multiple SSO MFA attempts were rejected by a user with suspicious characteristics."
Stages of the Playbook
The playbook comprises several stages to ensure thorough investigation and remediation:
Triage:
-
- Checks the reputation of the IP address associated with the MFA attempts.
- Gather related login events for further analysis.
![Fig 1: Sequence in playbook showing IP reputation checks and data collection]()
Fig 1: Sequence in playbook showing IP reputation checks and data collection
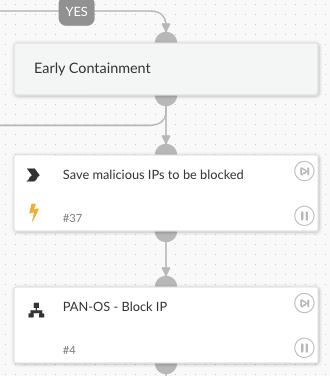
Early Containment:
-
- If the IP address is identified as malicious, blocks the IP to prevent further unauthorized activity.
- Continues with the investigation in parallel.
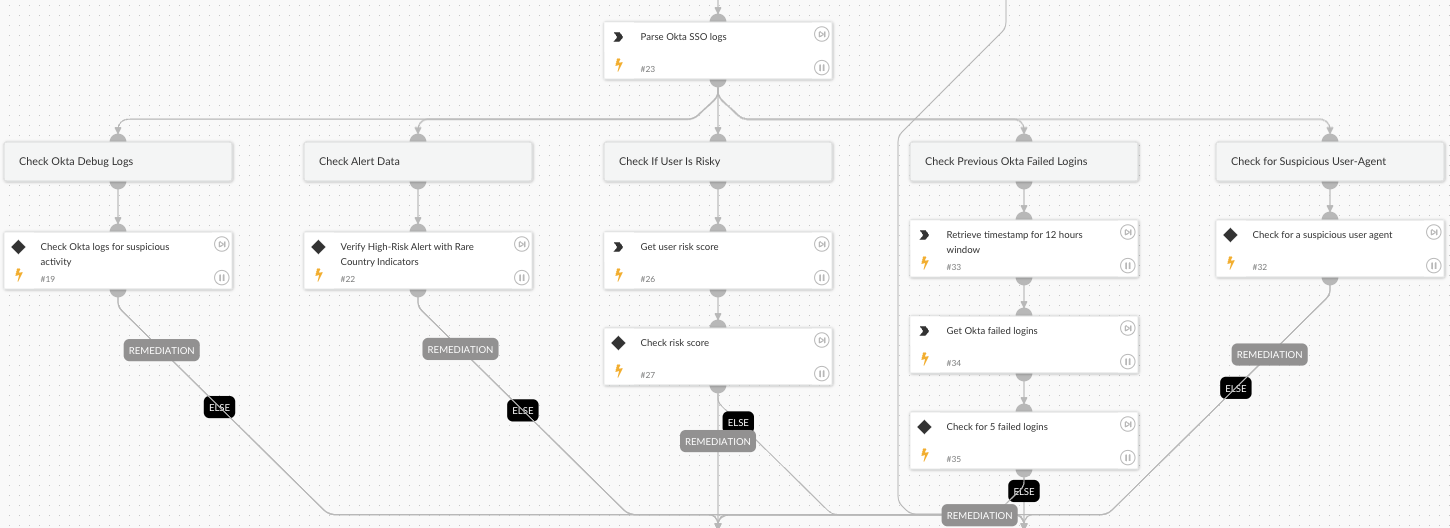
Investigation:
-
- Assesses the user’s risk score to identify potentially compromised accounts.
- Checks for excessive invalid credential attempts, indicating brute force or credential-stuffing activity.
- Analyzes Okta logs to verify whether the source IP is flagged as malicious by Okta’s threat intelligence.
- Reviews the number of MFA rejections to detect abnormal patterns.
- Identifies suspicious user agent behaviors, such as new or uncommon user agents, that may suggest malicious activity.
- Investigate previous failed Okta login attempts to uncover patterns of unauthorized access.
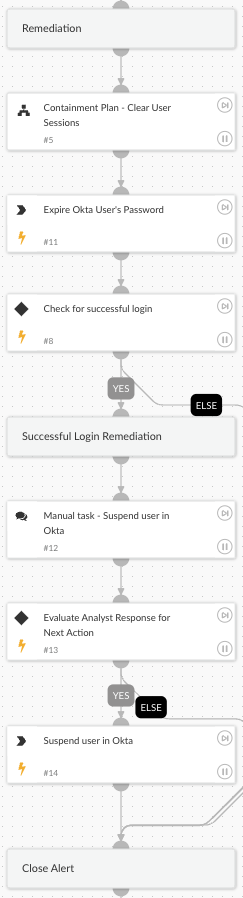
Containment:
-
- If suspicious activity is confirmed, perform the following actions:
- Clears the user’s active sessions and expires their password to prevent further unauthorized access.
- For confirmed successful login attempts, assign a manual task for an analyst to review and decide on additional actions.
- If suspicious activity is confirmed, perform the following actions:
Security Challenges Addressed
This playbook addresses key challenges in responding to suspicious MFA rejection patterns and speeds response times by automating actions and tasks:
- Early Threat Detection: Quickly identifies potential account compromise scenarios.
- Automated Containment: Blocks malicious IPs and clears user sessions to mitigate threats effectively.
- Comprehensive Investigation: Aggregates evidence and provides detailed insights into user behavior and associated risks.
- Adaptive Response: Combines automated and manual actions to ensure flexible and effective remediation.
Conclusion
Suspicious MFA rejection patterns demand immediate attention to prevent unauthorized access and potential data breaches. The "Compromised Accounts - User Rejected Numerous SSO MFA Attempts" playbook equips SOC teams with the tools to detect, investigate, and remediate these threats efficiently. By leveraging the Cortex XSIAM Response and Remediation Pack, organizations can enhance their incident response capabilities and protect sensitive resources.
Learn More
You might be interested in other playbooks in this pack such as Automating Response to Unauthorized Email Forwarding Activity in Google Workspace, Automate Response to Event Log Clearing Alerts with Cortex XSIAM, and Handling Successful SSO Sign-ins from Tor.
Explore more about the Cortex XSIAM Response and Remediation Pack and its advanced playbooks on the Cortex Marketplace.
