Cybersecurity threats are rapidly evolving. The battle feels endless, and AI has changed the game for both the attacker and the defender. The 2024 Unit 42 Incident Response Report is chock-full of details illustrating exactly how threats have evolved in recent years. Let's look at the situation from the lens of a cloud security profession and explore some of the most important findings.
Here are the top takeaways from the report:
No 1: Because attackers are moving faster than ever, security needs to move even faster. In just two years, from 2021 and 2023, the median time between initial compromise and data exfiltration has slimmed from nine days to two — a time reduction of 78%, according to the report. In almost 45% of Unit 42 cases last year, attackers exfiltrated data in less than a day after compromise. At best, organizations have only hours to respond to ongoing attacks.
No 2: Software vulnerabilities are the primary entry point for attackers. To stay ahead, shift-left and set up guardrails to prevent vulnerabilities from being introduced. For those that reach production, prioritize and quickly fix exposed vulnerabilities on your most critical assets.
No 3: Threat actors are more organized and sophisticated than ever. They’re even using security tools as offensive weapons.
No 4: On top of all that — we have entered the age of AI, a double-edged sword. Although attackers are benefitting from AI, stand strong. Security teams are as well.
Factors That Contribute to Successful Attacks
The threat report calls out three commonalities between attacks: unpatched vulnerabilities, inconsistent security coverage and weak identity and access management (IAM). In the framework of an attack, these factors are rarely the sole cause of a breach, but you’ll almost always see one, if not all, in the path leveraged by the threat actor. Lock these down so your organizations can break up attack paths to your crown jewels.
- Internet-exposed vulnerabilities are the dominant entry point and threat actors move fast. We see that hackers start exploiting new vulnerabilities within 15 minutes after they’re announced. If you leave the door open, they will enter. Simply patching vulnerabilities in runtime isn't enough. By tracing and fixing them in code, organizations can stop chasing their own tails and prevent them from being reintroduced.
- Don’t leave blind spots in your defenses. Unit 42 incident responders found that organizations with partial or incomplete deployment of security controls allowed attackers to operate in areas that weren’t defended. The best approach to cloud security starts at the first line of code, goes through runtime and is everywhere.
- Identities are the web that attackers move along within cloud environments. Overly permissive IAM is a killer, allowing privilege escalation and lateral movement. Enforcing least privilege can limit the blast radius of an attack where a threat actor is exploiting an identity's credentials.
Vulnerabilities Are the Tip of the Spear
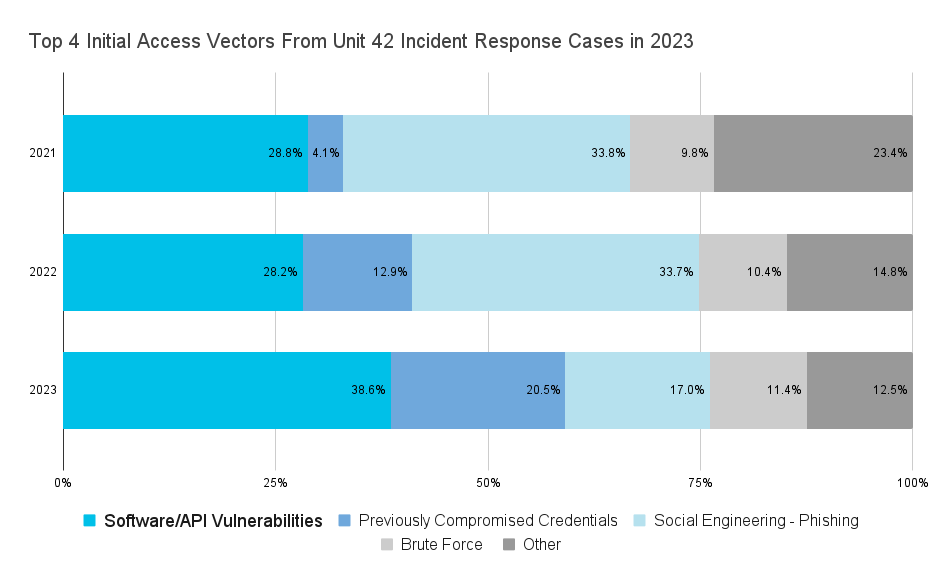
Where is the entry point adversaries use to infiltrate your environment? Last year, phishing was overtaken as the top entry method by software vulnerabilities. The report found that in 2023, threat actors exploited vulnerabilities as the initial access point 38.6% of the time, up from 28.2% in 2022.
Over 29,000 Common Vulnerabilities and Exposures (CVEs) were reported in 2023, and 2024 is on track to surpass that number. While not all were critical, the top exploited vulnerabilities in 2023 were:
- CVE-2023-3519 (Citrix NetScaler ADC/Gateway)
- CVE-2023-22952 (SugarCRM)
- CVE-2021-44228 (Apache Log4j)
- CVE-2023-34362 (MOVEit)
- CVE-2020-14882 (Oracle WebLogic)
Highlighting the challenge of dealing with vulnerabilities Log4j, one of the most prolific vulnerabilities ever, discovered over 2 years ago, is still haunting organizations.
Also of note, there also was a significant uptick in compromised credentials being the initial entry point for threat actors, growing from 12.9% to 20.5%. Five times more prevalent than it was in 2021. Protecting credentials is as important as ever. Yet, complicated cloud and multicloud architectures have not made it any easier on security teams — especially when users are accessing the cloud through different sources and the number of machine identities has skyrocketed.
Data Is Under Attack
Threat actors are going after your data. The report shows that data theft has more than doubled in prevalence, from 40% incidents in 2021 to 82% in 2023. The tactics have changed, too. Attackers are opting for more of a grab-and-go approach, where they take all the data they can access with plans to figure out what they have after the fact. The less targeted approach has certainly contributed to the decrease in mean time to exfiltrate.
When 63% of publicly exposed storage buckets contain personally identifiable information (PII), financial records or intellectual property, it's paramount that organizations focus on securing these crown jewels. Failure to do so can lead to large financial and reputational losses.
Both Sides Are Leveraging AI
What’s the impact of AI so far? For threat actors, AI is a multiplying force, making it faster to execute simultaneous multi-pronged attacks. On the opposite side, security experts note that “An AI could theoretically engage in a long, slow-burn operation aimed at eventually finding a way into an organization — perhaps over a period that a human would be unlikely to sustain.” Additionally, with the advent of large language models comes the concern that threat actors could compromise these tools, leading to data leaks or manipulated outputs.
Now for the good news. Security companies are now using AI to combat AI-driven threats. AI is highly effective at detecting malicious activity patterns. By deploying AI-powered security solutions, defenders can outpace attackers in terms of speed and scale.
Best Practices
When it comes to addressing today’s threats, we recommend 5 best practices to implement for better security:
- Secure identities: Enforce MFA to protect identities from being compromised and implement least-privilege access to limit the amount of damage that can be done with a compromised identity.
- Classify and protect data: Understand where your sensitive data lives and safeguard it from exposure.
- Monitor everywhere: Continuously monitor your cloud infrastructure, CI/CD environments, runtime deployments and detect malicious behavior
- Automate responses to react quickly: Threat actors are moving faster than ever. Manual response won’t be quick enough. Leverage automation to stop attacks.
- Manage your attack surface: Identify and secure internet exposed cloud assets. Leverage cloud discovery and exposure management to scan environments from the outside in to locate unmanaged cloud assets that are exposed to the internet.
Learn More
Read the full Unit 42 Incident Response Report.
If you’d like to see how Prisma Cloud can help your team employ these best practices, consider booking a personalized demo or registering for a free 30-day Prisma Cloud trial.