Founded by Jeff Moss as a gathering that delved into the hacker mindset, to its current stature as a global industry-leading cybersecurity conference, Black Hat has been a beacon for both the establishment and underground innovators. As a longstanding partner, Palo Alto Networks is proud to play a critical role in securing Black Hat Asia 2025. Our engagement at the Network Operations Center (NOC) and Security Operations Center (SOC) ensures that the conference not only operates without disruption to you, the attendees, but also remains a step ahead of emerging cyberthreats. By providing advanced network security services and cutting-edge AI-driven security operations, we bolster the conference's defenses, embodying the spirit of innovation that Black Hat champions for participants around the world.
The network and security operations center (NOC/SOC) at the Black Hat Asia Conference serves the critical role of helping ensure that the conference's entire network is running smoothly and efficiently, as well as detecting and responding to any security threats. Black Hat deploys its own bespoke network and infrastructure per event, instead of using the venue’s infrastructure. This allows the NOC/SOC to have full visibility into the network. Black Hat can be an attractive target for threat actors looking for the infamy associated with disrupting the conference or stealing personally identifiable information (PII) from attendees.
To thwart attacks from both internal attendees and external actors, Black Hat partners with a select group of cybersecurity organizations. The partners are selected on merit and do not pay to be involved in the conference. Each partner serves a different function, providing solutions that work together to establish and defend a stable and well-protected network. In addition to leading cybersecurity products, each partner provides a crew of experts to operate and work in lock-step with the Black Hat team.
Trusted Partner of Black Hat
As a trusted partner, Palo Alto Networks has officially supported Black Hat 23 times over the last eight years at their conferences around the world. At this year’s Black Hat Asia, we are providing three functions within the NOC/SOC:
- We will provide the NOC with network security services, including next-generation firewall capabilities, full Layer 3 dynamic routing, comprehensive network segmentation/isolation and protection of the Black Hat owned infrastructure from network attacks.
- We will provide the SOC with our AI-driven security operations platform to automate and integrate with the different products used by Black Hat.
- We will collaborate with Black Hat and the other partners to provide threat hunting and threat context of traffic, to help the SOC team determine appropriate courses of action.
Significant portions of the Palo Alto Networks product portfolio are used to provide these services. Cortex XSIAM® unifies all the data collected by the tools Black Hat has available, to quickly provide visibility and reporting for threat hunters and NOC guests. Our PA-5430 NGFWs will be deployed in high availability, protecting Black Hat owned systems and internal infrastructure. The firewalls also provide network App-ID visibility and the full suite of our Cloud-Delivered Security Services on the entire network.
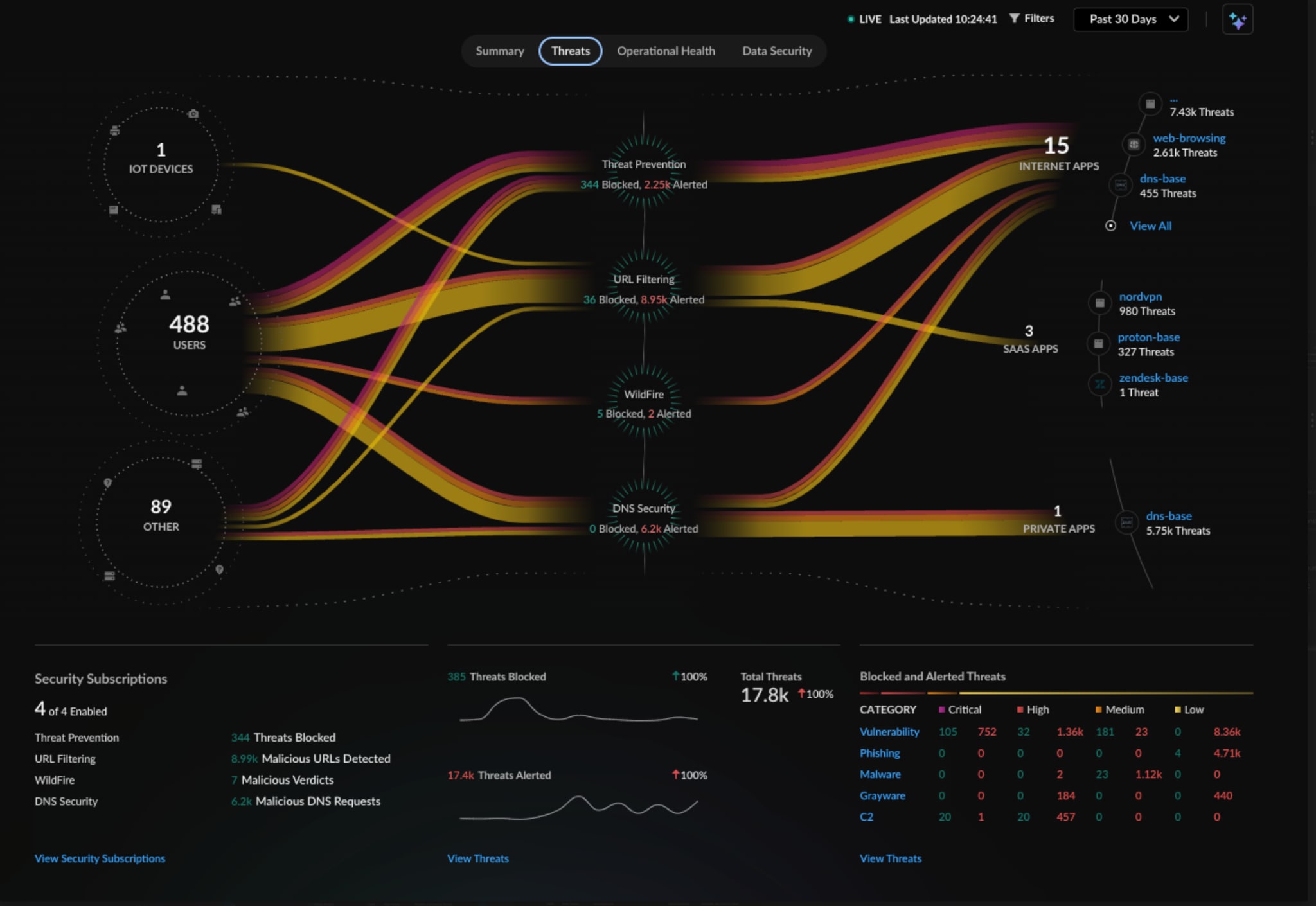
- Advanced Threat Prevention to detect network attacks, defend against vulnerabilities, detect malleable C2 and zero day SQLi, as well as CMDi attacks.
- Advanced DNS Security to identify bad domains and detect threats, which leverage DNS as a vector.
- Advanced URL to identify malicious URLs and detect web-based threats.
- Advanced WildFire to identify malicious files.
- Enterprise IoT Security to identify device information which is helpful in incident response.
All the NGFWs and services will be monitored by Strata® Cloud Manager’s AIOps capabilities for assessing the network security platforms’ health, operational readiness and configuration best practice.
The core of the security operations at Black Hat is Cortex XSIAM.
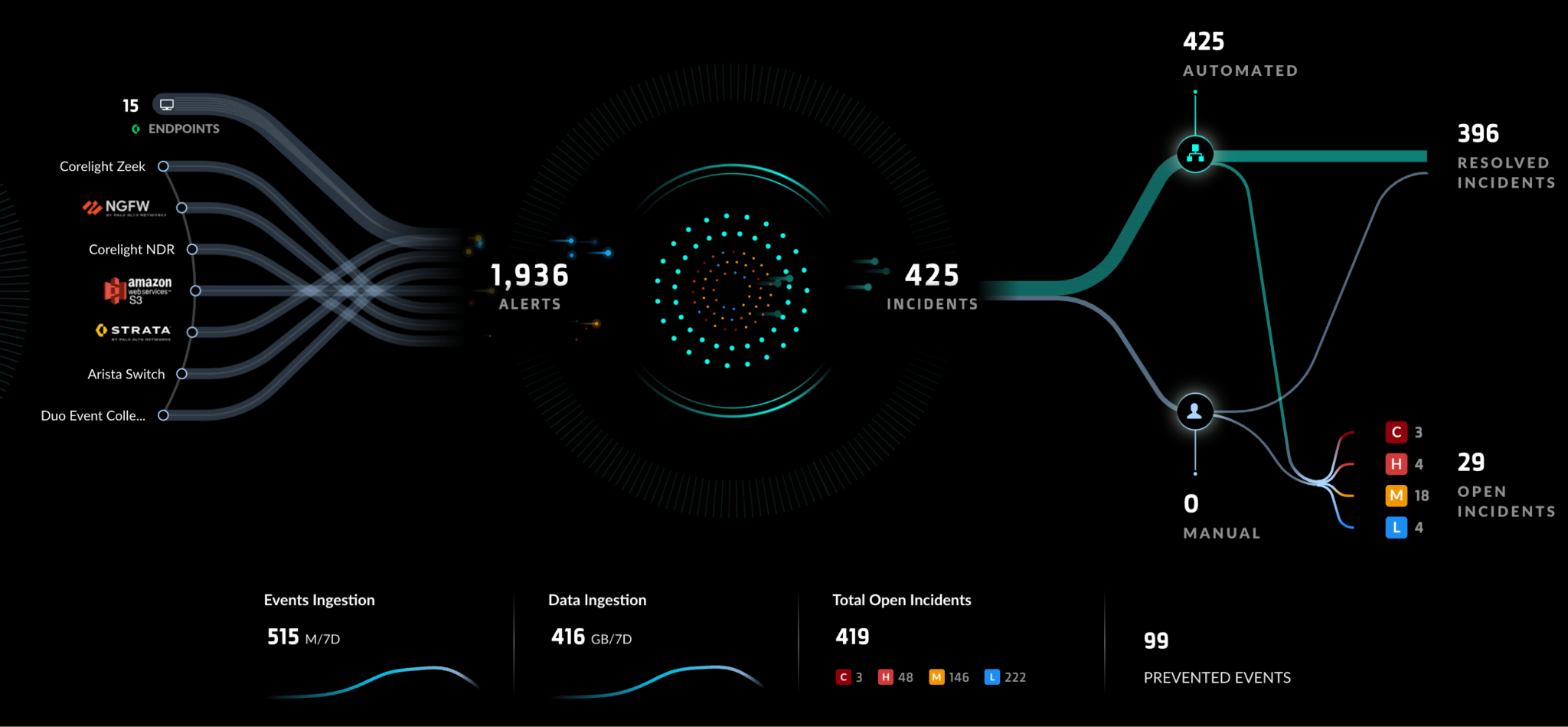
XSIAM is key to the SOC, consolidating data and logs from all the tools leveraged by Black Hat, including products from the other partners invited to the NOC. The platform helps streamline threat hunting and incident investigation through an automation first approach, utilizing playbooks and integrations to interact with all the products supporting the Black Hat infrastructure. Combined with out-of-the-box AI models, XSIAM is able to prioritize events and give the threat hunters a single place to perform investigations with all the data easily available at their fingertips.
We leverage and inform investigations with threat intelligence sources from Palo Alto Networks Unit 42® and the other partners in the SOC. XSIAM playbooks are used to automatically provide context and enrichment to any incident that occurs, then progress the incidents to investigation and closure. Cortex XDR® agents are deployed on the Black Hat infrastructure to provide OS-level protections and visibility, streaming endpoint telemetry directly into XSIAM.
XSIAM automation processes dynamically change based on how the Black Hat infrastructure is segmented. Incidents originating from training classrooms are handled with lower priority due to the known malicious nature of the training traffic. Live attacks from the internet toward the external perimeter of the environment or the registration network are given much higher priority.
The Black Hat Infrastructure Is a Target
As one of the largest cybersecurity conferences in the world, Black Hat has some of the most talented researchers attending and speaking about their projects, who oftentimes highlight new attack techniques and vulnerabilities. Over the years, we have seen attendees immediately test these new attacks on the network. They even attempt to attack fellow attendees or the conference infrastructure. This is an excellent example of what organizations face today: Attackers don't need much time to find ways to abuse a software bug or vulnerability.
The conference focuses on the learning and education of advanced attack and defense techniques. With the partners in the NOC, this can happen without being disruptive to all the attendees, allowing people to focus on learning and networking without worrying about their cybersecurity.
The Palo Alto Networks Unit 42 Threat Hunting team is in the NOC, actively reporting credible threats to the Black Hat team, specifically attacks that are against the registration and internal infrastructure. Based on this threat intel, the Black Hat staff is able to leverage Cortex XSIAM integrations to instantly block bad actors through address tagging on the firewall. The team works in close collaboration with the other NOC/SOC partners: Arista, Cisco, Corelight and MyRepublic.
To see the team in action, the Black Hat NOC will be streamed live via the conference Twitch channel, or you can visit and tour the NOC on-site. The partners also give NOC presentations in the Business Hall and Briefings Pass holders can attend the Black Hat Asia NOC Report on the last day of the conference.
Black Hat NOC Schedule
NOC Visiting Hours (Melati Jr. Ballroom 4110)
Tuesday, April 1 - Friday, April 4: 9:00 AM – 6:00 PM
Live Stream Hours
Tuesday, April 1 - Friday, April 4: 9:00 AM – 6:00 PM
NOC Presentations (Business Hall Theater A)
Thursday, April 3: 3:35 PM - 4:00 PM
Friday, April 4: 12:55 PM - 1:20 PM
The Black Hat Asia Network Operations Center (NOC) Report*
Friday, April 4: 3:20 PM - 4:00 PM
*Available to Briefings Pass holders only.