New capabilities safeguard OT remote operations, mitigate risks for critical, hard-to-patch assets, and extend protection into harsh industrial environments.
As operational technology (OT) environments undergo rapid digital transformation, so do their security risks. Protecting industrial setups, especially those with legacy systems, distributed operations, and remote workforces, requires an innovative approach that prioritizes both uptime and safety. We’re pleased to announce new advancements in our OT Security solution designed to address these evolving risks.
Our latest solution enhancements are designed to help customers address critical risks and threats by mitigating vulnerabilities in hard-to-patch OT assets, safeguarding remote operations and extending security into harsh industrial environments. These advancements ensure seamless security while minimizing the risk of disruption.
Mitigate OT Vulnerabilities Without Disruption — Powered by Precision AI
Introducing the industry's only fully integrated, risk-based Guided Virtual Patching solution for OT environments, designed to protect unpatched legacy OT assets at scale. Powered by Precision AI™ – our proprietary AI system – this solution combines machine learning, deep learning and generative AI to deliver advanced, real-time protection.
Machine learning analyzes historical data for accurate threat detection, while deep learning builds predictive models that detect security issues in real time. Generative AI enhances the user experience with a natural language interface, making the system more intuitive and intelligent.
With products powered by Precision AI, your organization gains comprehensive asset visibility, risk assessment, vulnerability prioritization, virtual patching and seamless threat prevention, all without downtime.
By leveraging the Palo Alto Networks Industrial OT Security solution, we're able to get a very accurate and up to date real-time inventory of all of our assets on the floor and manage the risk of each device.
– Mark Williams, director, Network Engineering, BorgWarner
Guided Virtual Patching is part of a new end-to-end risk management workflow that starts with a comprehensive risk assessment and attack surface mapping, enabling the quick identification and prioritization of critical vulnerabilities. By recommending threat prevention profiles and least privilege policies, Guided Virtual Patching reduces exposure and effectively secures hard-to-patch OT assets. Customizable risk scores allow you to adjust for asset criticality with confirmed compensating controls, giving you full control and audit trails over how risks are managed across your OT environment.
The end-to-end workflow helps cut through the noise, allowing you to focus on top-priority vulnerabilities and manage risks more efficiently, ensuring your mission-critical systems remain secure and fully operational without disruption.

Operational technology environments are becoming increasingly complex and interconnected, making them more susceptible to cyberthreats. The ability to deploy AI-powered tools, like guided virtual patching, is a game-changer for industrial cybersecurity. It enables organizations to address vulnerabilities in real-time without the costly and often disruptive downtime that traditional patching methods would require. This approach not only reduces risks but also enhances the overall resilience of OT infrastructures.
– Sid Snitkin, vice president, Cybersecurity Services, ARC Industrial Cybersecurity
Protect Remote Operations with Enterprise-Grade Security, Optimized for OT
As remote operations expand, securing them is essential. With the introduction of the new Prisma Access Browser and its Privileged Remote Access feature, Zero Trust network access (ZTNA) is now extended to OT environments. These OT-specific workflow capabilities ensure secure, seamless access to IT, OT and cloud applications for your distributed workforce across employees and partners.
With the rise of remote operations in industrial settings, secure remote access has become an essential component of OT security. Implementing Privileged Remote Access allows organizations to achieve secure connectivity without compromising operational efficiency. These innovations are critical in providing remote workers with the access they need while maintaining the integrity of OT networks.
– Hollie Hennessy, Principal Analyst, Omdia
Our remote access solution features a simple, browser-based architecture with an integrated jump server that reduces deployment complexity, making secure remote access management easier for both users and administrators. Tailored specifically for OT, it supports unique workflows and security compliance requirements, offering just-in-time access for OT administrators and session recording for audit and regulatory needs.
With end-to-end security powered by Precision AI, protection extends from the host to the network. Prisma Access Browser has over 20 capabilities to secure the host environment, such as host posture check, CDSS security services to secure file transfers, session recording and detailed audit trails. It additionally provides over 20 last mile and identity controls, such as JIT session provisioning, screenshot/sharing control, clipboard control and watermarks. Centralized management through Strata Cloud Manager further enhances operational efficiency, delivering consistent, secure remote access across IT and OT environments.
Extend ML-Powered Security Into Harsh Industrial Environments
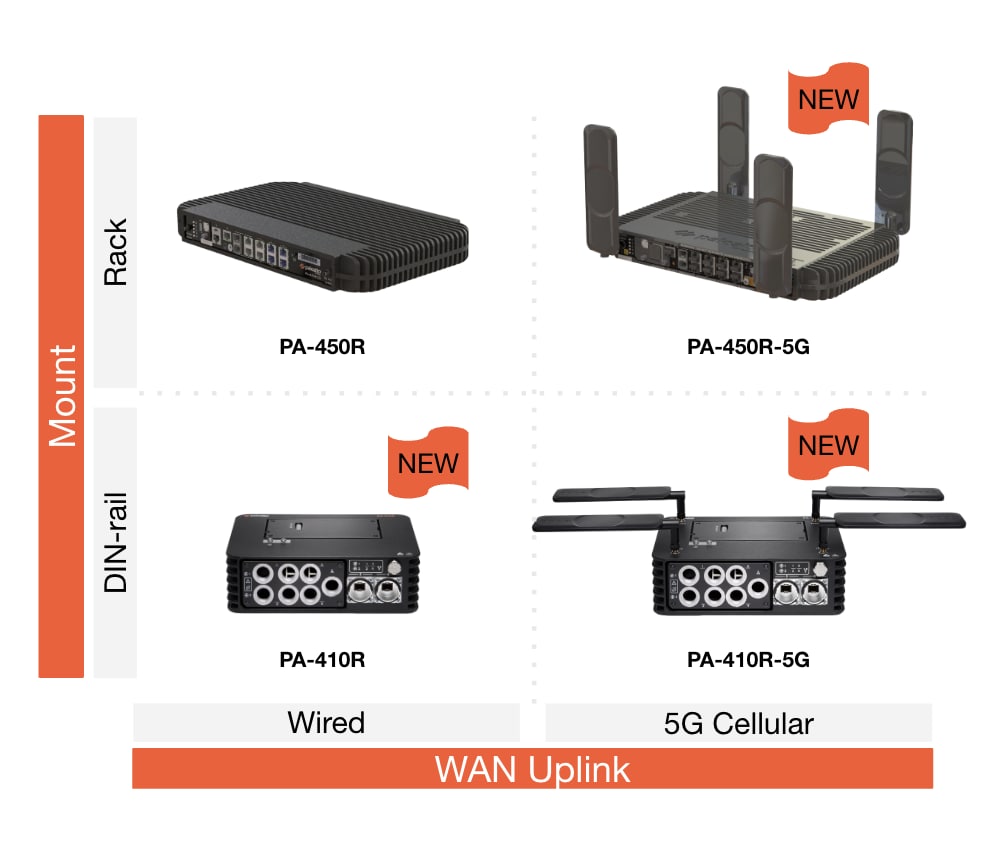
We offer a suite of ruggedized NGFWs tailored to meet a range of industrial needs. The PA-400R Series is engineered for demanding environments, like utility substations, factory floors and renewable energy sites, with high IP ratings for durable protection.
Both the PA-450R and PA-410R models offer 5G-ready form factors with native 5G WAN uplink capabilities, making them ideal for distributed operations and remote site monitoring. The PA-410R features a DIN-rail mount for easy installation in industrial setups. Both models include a built-in modem with dual SIM support, simplifying deployment and saving space. This flexible and scalable suite of NGFWs is designed to effectively secure critical infrastructure and industrial assets.
Strengthen OT Monitoring and Compliance with Advanced Asset Discovery and Analytics
Strengthen visibility and simplify compliance reporting across your OT environment with the advanced asset discovery and analytics enhancements in our Industrial OT Security service. Our flexible asset discovery techniques, including both active and passive methods, as well as the Virtual Metadata Collector enable you to map all your assets, even in remote or hard-to-reach locations. With enriched OT asset contexts and advanced insights into Programmable Logic Controllers (PLCs), you gain granular visibility into asset behaviors and control systems, helping you detect vulnerabilities early and respond proactively.
To streamline compliance, our out-of-the-box NIST Cybersecurity Framework (CSF) compliance reporting reduces the time and effort required for audits, making adherence to industry standards more manageable. Seamless integrations with existing systems ensure these enhancements fit smoothly into your current infrastructure, enhancing efficiency without adding complexity.
OT-Specific Reference Architectures for Enhanced Security
We're also introducing new OT-specific reference architectures, complete with design and deployment guides. These include Securing OT Services Using an Industrial DMZ, which establishes best practices for creating a secure demilitarized zone in OT environments, and Securing OT Infrastructure with Plant Segmentation, which provides strategies for segmenting plant operations to enhance security and reduce risk.
Comprehensive Security for Every OT Environment
The Palo Alto Networks OT Security solution is built to protect every aspect of your OT environment, from networks and assets to remote operations and 5G infrastructures. Tailored to meet the unique needs of OT systems, it empowers organizations to safeguard personnel, applications, devices and data. By delivering a consistent user experience across all deployments, this solution simplifies OT security management while ensuring robust protection for critical operations.
Join Us at the Industrial Control Systems (ICS) Cybersecurity Conference
Explore the future of OT security with us at Security Week’s ICS Cybersecurity Conference in Atlanta, Georgia, October 21st - 24th. Stop by our conference room or attend one of our expert-led sessions to gain insights into how we're advancing protection for critical industrial environments.
To see firsthand how these innovations can help you navigate the growing challenges of securing complex OT systems, start your free trial of Industrial OT Security today.