AI Access Security Now Available
The rollout of our Secure AI by Design product portfolio has begun. And now, the journey continues.
Today, we’re pleased to announce the general availability of AI Access Security, an innovative offering that addresses the unique security challenges posed by generative AI and large language models in corporate environments. AI Access Security empowers organizations to harness the power of GenAI technologies while maintaining robust protection for sensitive data and ensuring compliance with security policies.
GenAI apps have become an indispensable tool, revolutionizing how we work and creating unprecedented opportunities for innovation and productivity. However, the rapid proliferation of GenAI apps, coupled with their unique characteristics and evolving AI ecosystems have introduced new security challenges.
AI Access Security provides real-time visibility into what GenAI apps are being used and by whom, with the ability to set up robust application access controls. What’s more, it provides comprehensive data protection, AI posture management and security controls for both sanctioned and shadow AI apps.
See how AI Access Security prevents unauthorized use of GenAI tools.
Discover and Monitor Your GenAI Application Footprint
Gain immediate visibility with an up-to-date catalog of 600+ GenAI applications mapped over 60 AI-specific attributes (i.e., input/output modes and whether data is used in training models) to discover GenAI apps, monitor usage and assess risks.
Empower your IT security teams to not only keep pace with the latest GenAI apps but make informed risk-based decisions about which apps to sanction or tolerate.
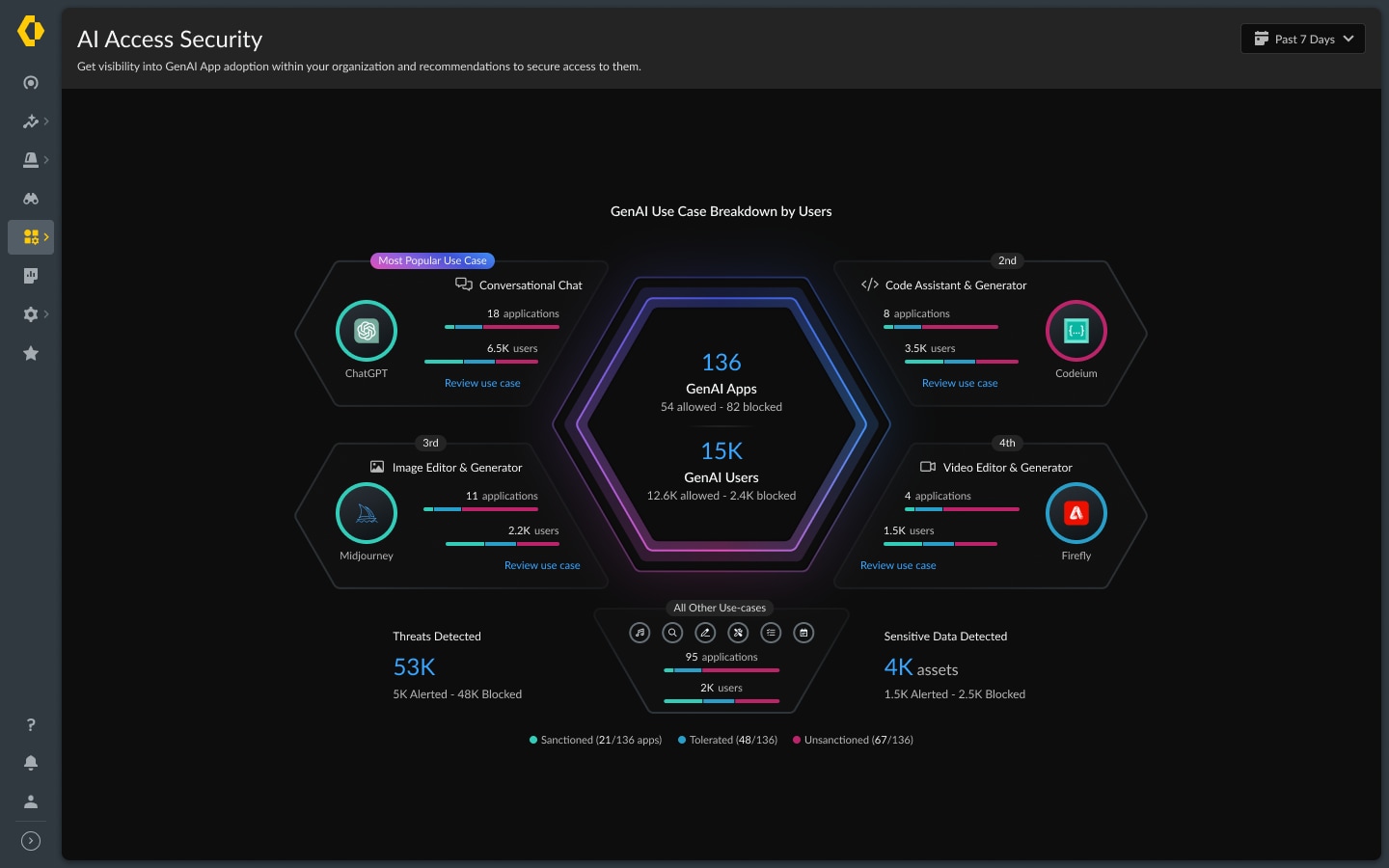
Don’t Just Block GenAI, Take Back Control
AI Access Security allows you to create and enforce granular policies for GenAI usage. These policies can be customized based on user roles, departments or specific data uploads, helping ensure that AI apps are used in compliance with your organization’s security and governance standards.
In addition to robust access controls, it’s essential to educate your employees on AI-related risks, and then to guide them to approved apps or to corporate policies. With best practice recommendations, granular controls and employee coaching, we enable businesses to innovate with confidence.
Protect Your Sensitive Data from Un/Intentional Leakage
AI Access Security is specifically tailored to scan, detect and prevent sensitive information from being input into unauthorized AI tools. By leveraging LLM-powered and context-aware ML models, sensitive data is classified across 300+ predefined and custom categories with pinpoint accuracy to help ensure your organization’s sensitive data remains secure.
What’s more, you gain visibility into encrypted traffic directly through the Prisma Access Browser for an additional layer of control and enforcement. And, integration with ChatGPT Enterprise further extends visibility into ChatGPT workspaces.
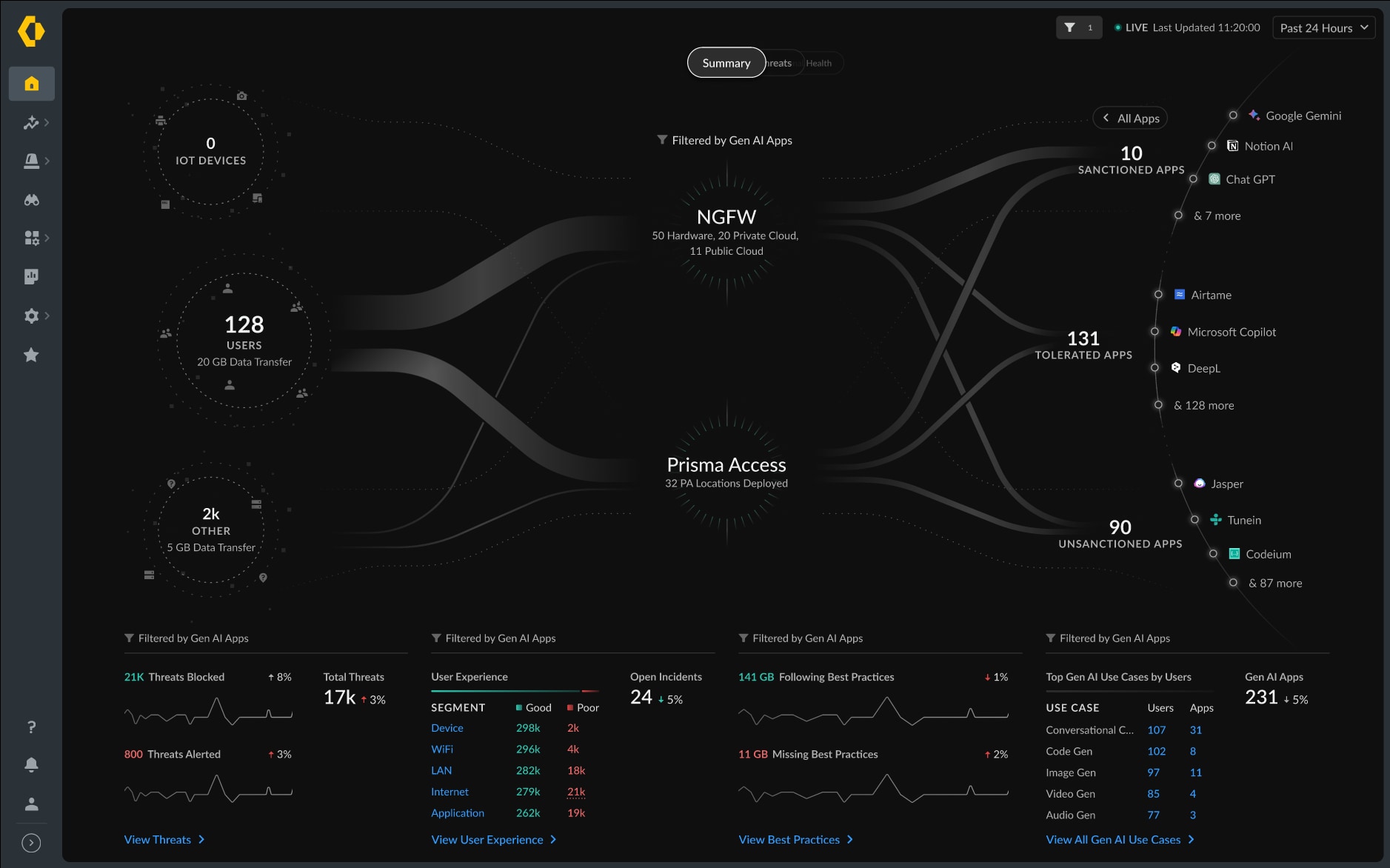
Continuous Data Risk Monitoring That Keeps Up With AI Threats
Protect your users from the latest threats in an ever-evolving AI landscape. AI Access Security enables your IT security teams to uncover interconnected GenAI applications within SaaS marketplaces, detect threats (malicious URLs, files) within AI responses, and maintain GenAI app posture for improved security hygiene and regulatory compliance.
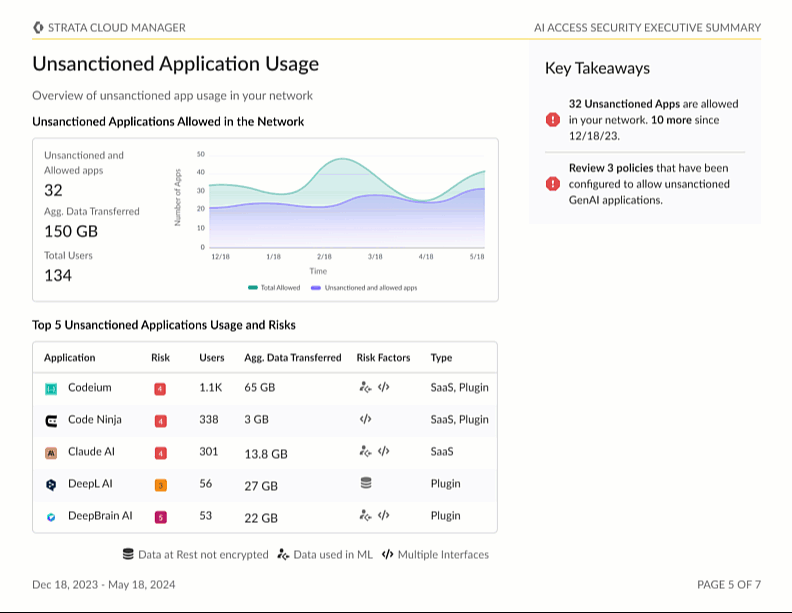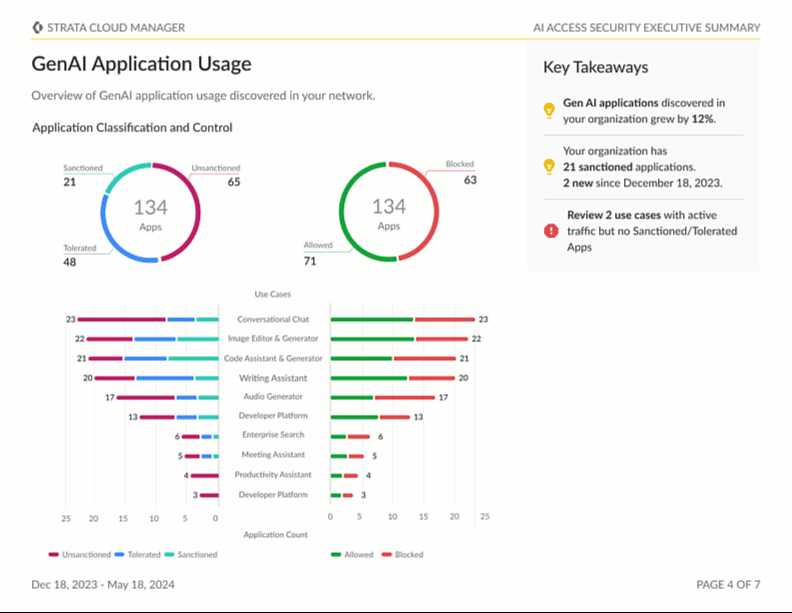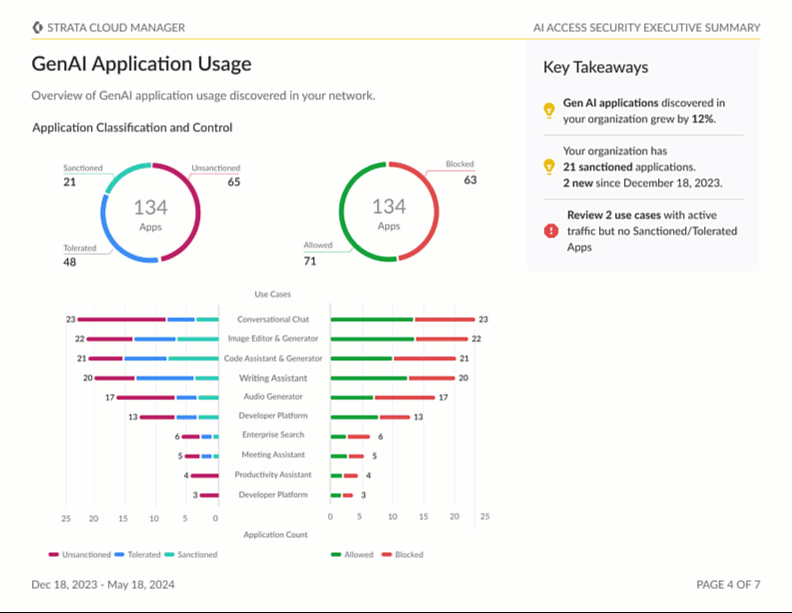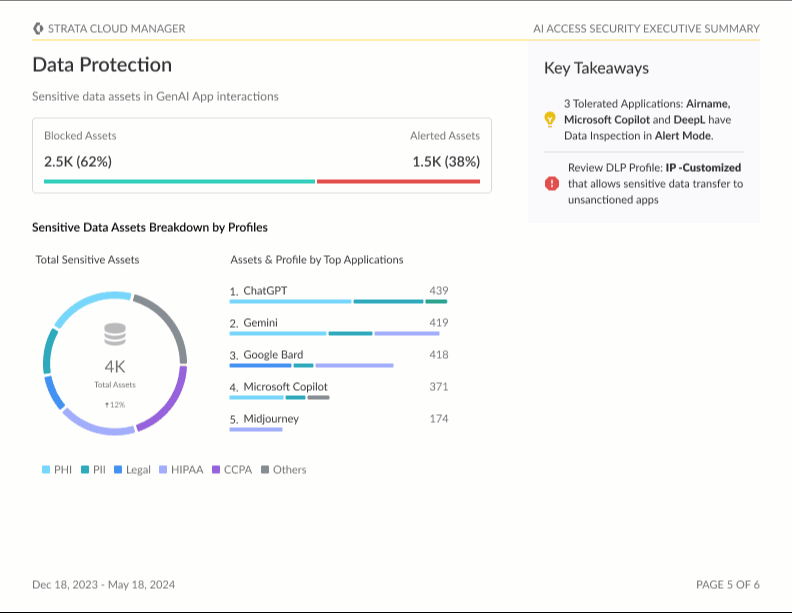
Stay tuned as we continue to innovate and enhance AI Access Security with upcoming features, such as executive reports. You can view and download these reports with full observability and explainability of your organization’s GenAI usage and its associated risks. Detailed audit trails and reporting of AI interactions are crucial for continuous risk monitoring and maintaining compliance with data protection regulations, such as GDPR, CCPA and other industry-specific standards.
Safely Harness the Power of GenAI, Today
As AI continues to evolve, so too will the security challenges it presents. The launch of AI Access Security marks a significant milestone in enterprise cybersecurity. It empowers your workforce with the latest AI tools while maintaining the highest standards of data security and organizational integrity.
We invite enterprise organizations to join us in shaping a future where the transformative power of AI can be harnessed safely and responsibly.
See why AI Access Security has been recognized by Tech Ascension Awards as the Best AI/ML Powered Solution in 2024. Learn more on our AI Access Security page or contact our sales team for a personalized demonstration.
Related reading:
- A Brand New Fight: Securing Your AI-Powered Applications
- Strata Network Security Platform
- Precision AI, the future of AI & Cybersecurity
This blog contains forward-looking statements that involve risks, uncertainties and assumptions, including, without limitation, statements regarding the benefits, impact, or performance or potential benefits, impact or performance of our products and technologies. These forward-looking statements are not guarantees of future performance, and there are a significant number of factors that could cause actual results to differ materially from statements made in this blog. We identify certain important risks and uncertainties that could affect our results and performance in our most recent Annual Report on Form 10-K, our most recent Quarterly Report on Form 10-Q, and our other filings with the U.S. Securities and Exchange Commission from time-to-time, each of which are available on our website at investors.paloaltonetworks.com and on the SEC's website at www.sec.gov. All forward-looking statements in this blog are based on information available to us as of the date hereof, and we do not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.