How We Got Here and Where We're Headed
Is XDR the future of detection and response? By looking at how cybersecurity has evolved, we can better predict where it's headed. It's easy to see the rapid changes that have already occurred because cybersecurity evolves quickly. The solutions that blocked attacks thirty years ago would wilt in the face of modern threats today.
In the never-ending cat-and-mouse game of security, adversaries keep creating new exploits and evasion methods as defenders devise innovative ways to stop them. New products emerge to tackle rising threats, while existing products adapt, merge or fade away.
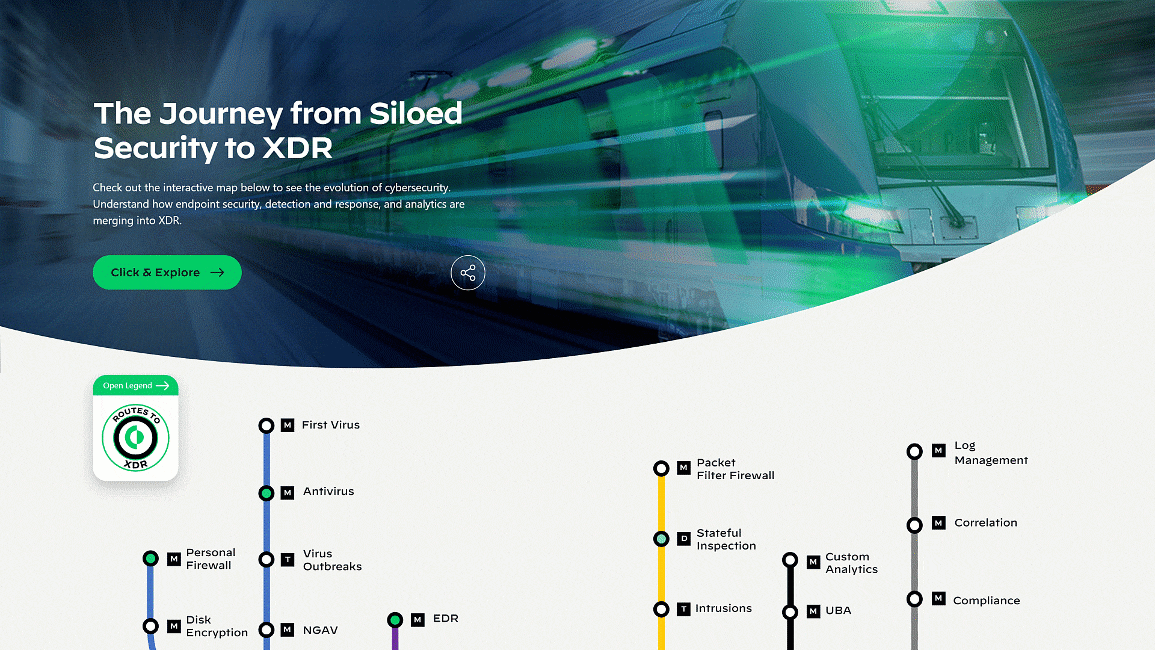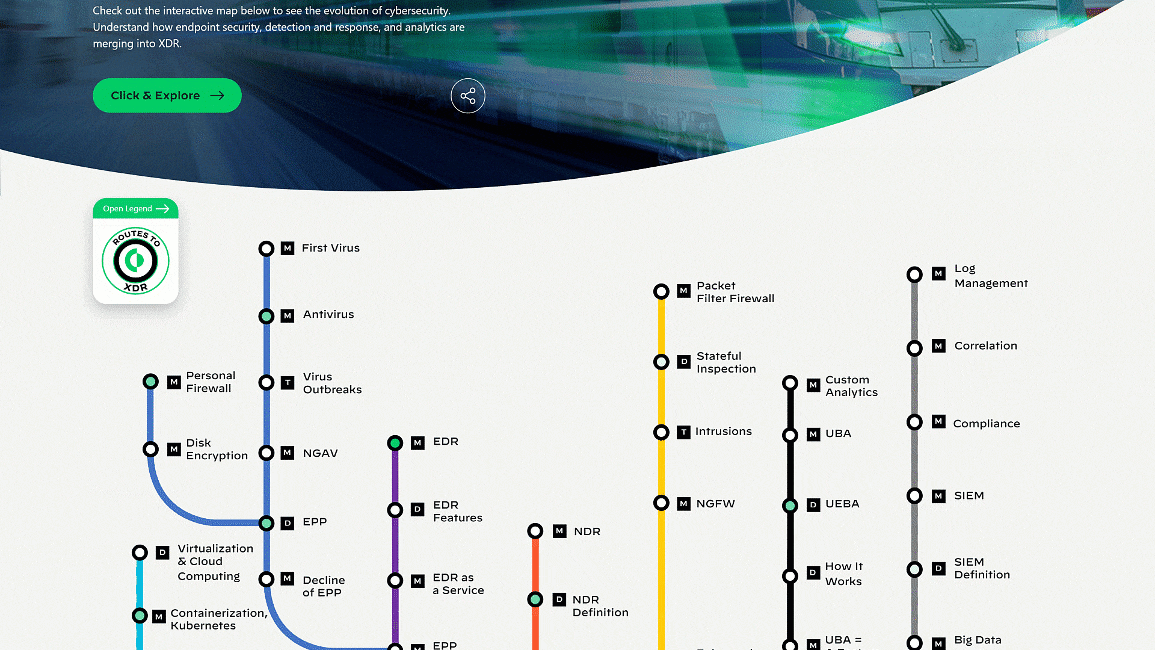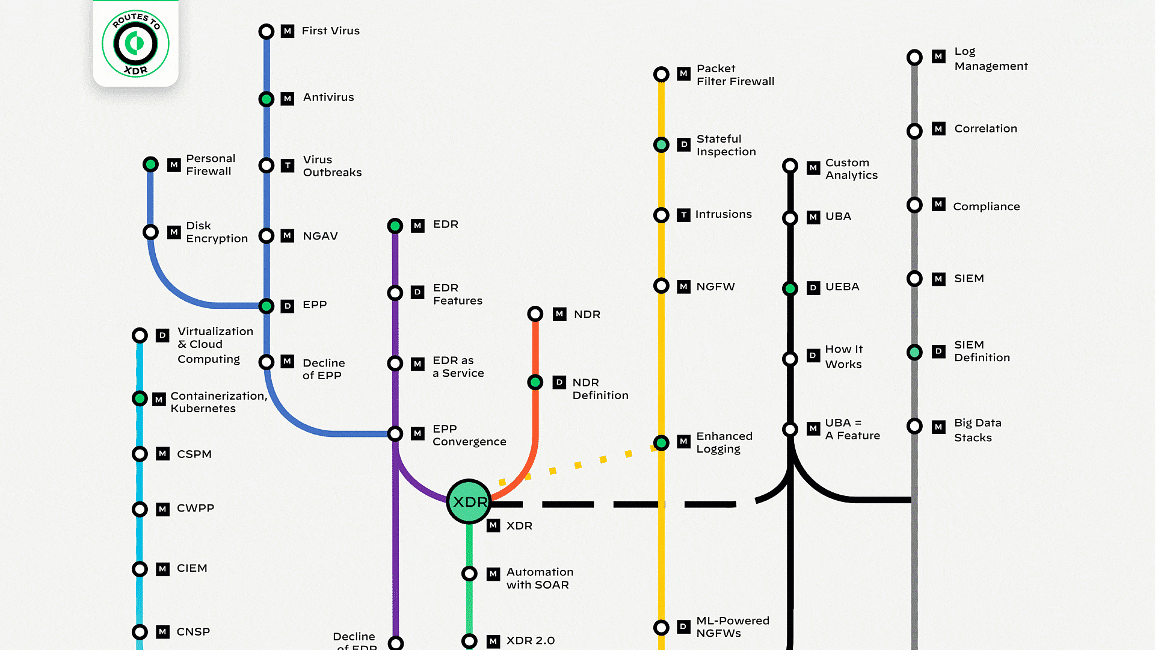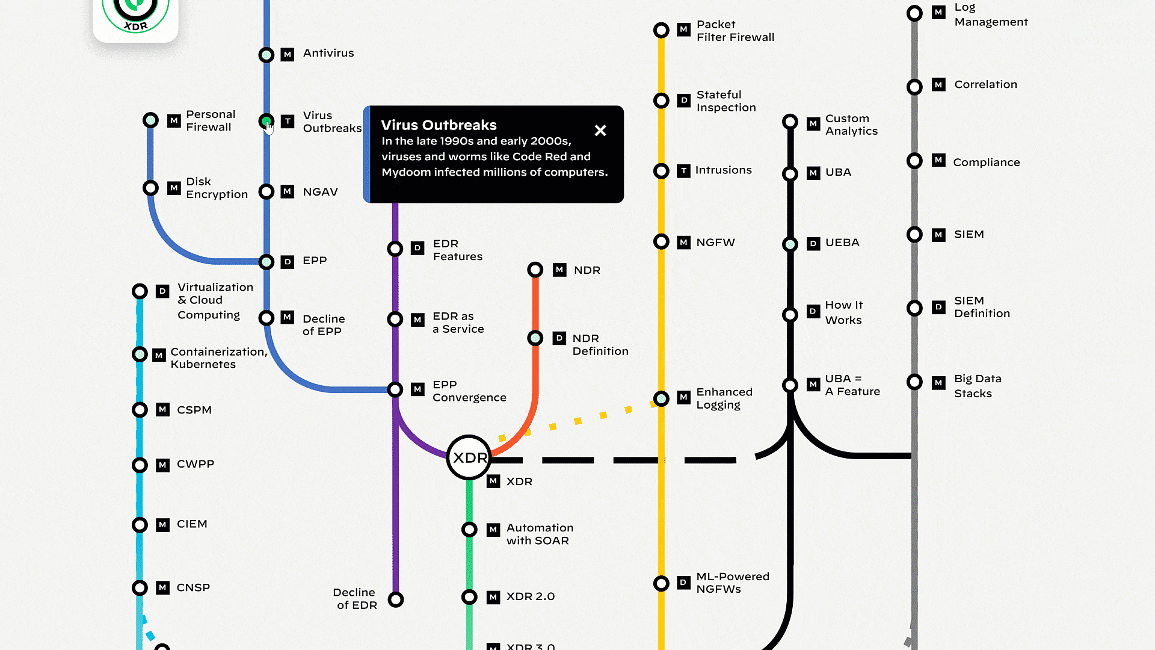
Endpoint Security in Flux
Nowhere is cybersecurity’s rapid evolution more apparent than in endpoint security. From the first prototypes of viruses in the 1970s to today, endpoints have constantly stayed in the crosshairs.
Not long after the term “computer virus” was coined in late 1983, the first antivirus products appeared on the scene. Antivirus evolved over time, slowly incorporating more features, such as host firewall and disk encryption, to become endpoint protection platforms.
No matter how much the technology advanced, it could never stop all attacks. This led Gartner to claim, "Endpoint protection platforms (EPP) no longer address the nature of modern threats as it is no longer practical to focus on achieving 100% prevention and protection."
Detection, Response and Analytics
While legacy antivirus morphed into an EPP and next-generation antivirus (NGAV), a separate category of tools emerged to detect and stop endpoint attacks. By 2013, Gartner named the category of endpoint tools, "primarily focused on detecting and investigating suspicious activities," as "Endpoint Threat Detection and Response." Two years later, the name evolved to Endpoint Detection and Response (EDR). But EDR products didn’t stop there. Over time, they added cloud-based delivery, endpoint protection and other enhancements to improve investigation and response.
Meanwhile, organizations faced an array of threats that EDR solutions couldn’t address. Security teams had limited visibility into cloud workloads, IoT and unmanaged devices. Advanced adversaries were even exploiting routers and load balancers and using them as an entry point into organizations’ networks. They were stealing credentials and moving laterally until they achieved their objectives. Malicious insiders were exploiting their existing privileges to access and steal sensitive data.
To combat these dangerous threats, security teams deployed a variety of nascent tools including network detection and response (NDR), cloud detection and response (CDR) and user behavior analytics (UBA or UEBA).
XDR: The Future of Detection and Response — Endpoint Security and More
Over the past decade, organizations armed their security teams with an ever-growing number of siloed tools. As a result, the average organization has 45 cybersecurity tools, with more tools associated with lower confidence in ability to respond to attacks, according to the Ponemon Institute. These tools are costly to manage and typically don’t work well together to stop attacks.
Because of all these disjointed tools, security analysts claim it takes them over 10 minutes to investigate each alert. They also face a deluge of alerts, with SOC teams receiving over 11,000+ alerts per day on average.
Palo Alto Networks CTO and co-founder, Nir Zuk, realized that security teams needed a new approach to detection, response and endpoint security. At our 2018 Ignite User Conference, Nir introduced the concept of XDR, and disrupted the cybersecurity status quo. Nir stated, “EDR as popular as it is right now, I predict, is dead. It just doesn't make any sense to do detection and response based on data coming just from endpoints.”
Since that date, XDR technology has taken security by storm. Now, the security community, including practitioners, industry analysts and other security vendors, have embraced the category. The Gartner® Market Guide for XDR and the Forrester New Wave™: Extended Detection and Response (XDR) both help validate this growing market category.
We believe XDR technology will subsume many siloed tools, including EPP, EDR, NDR, CDR and UBA. Because XDR applies analytics to integrated data, it delivers more accurate attack detection than siloed security. It also simplifies investigations by providing everything you need to investigate incidents in one place, including data from any source, so you can eliminate swivel chair syndrome.
Journey from Siloed Security to Extended Detection and Response
Explore our interactive map, The Journey from Siloed Security to XDR, to find out interesting facts and milestones in the evolution of cybersecurity. You’ll see how we got here and where we’re headed. Share this map with your peers and discuss your predictions for the future of detection and response. It’s been a wild ride so far!